In the hierarchy of PHP vulnerabilities, Dependency Injection (DI) Container Injection sits at the very top—complex to detect, elegant to exploit, and devastating in impact.
The disclosure of CVE-2025-32432 targeting Craft CMS (and by extension, the underlying Yii2 Framework) serves as a brutal reminder: when user input controls class instantiation, the application belongs to the attacker.
While many security scanners flagged this as a “Configuration Issue,” elite security engineers recognize it for what it truly is: Remote Code Execution (RCE) via insecure object deserialization. This article performs a technical autopsy of the vulnerability, reconstructing the gadget chain and demonstrating how AI-driven analysis is the only way to catch these logic flaws at scale.
The Architecture of Failure: Inside the Yii2 Container
To understand CVE-2025-32432, you must understand the heart of Yii2: the yii\\di\\Container.
Craft CMS relies on Yii2’s DI container to manage class dependencies. The container allows developers to configure objects using arrays. For example:
PHP
// Legitimate usage $object = Yii::createObject([ 'class' => 'app\\models\\User', 'name' => 'Admin', ]);
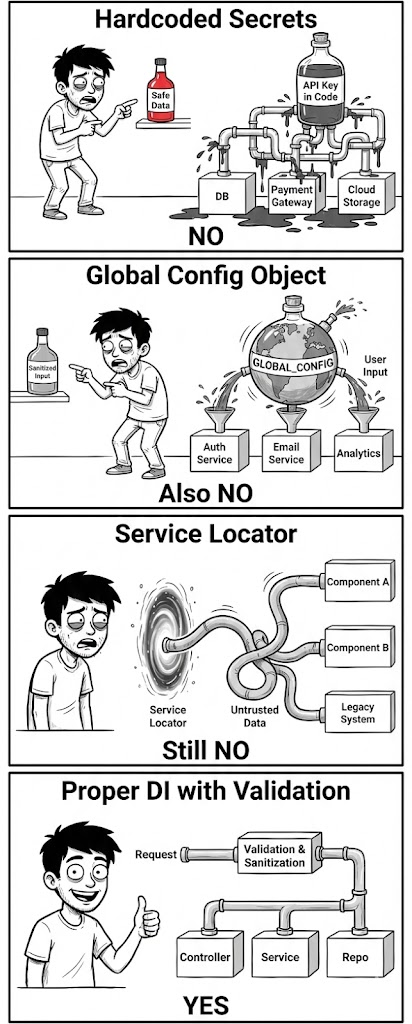
The vulnerability arises when an attacker can influence this configuration array. If a controller action takes raw JSON input and passes it blindly to Yii::createObject() or Yii::$container->set(), the attacker can force the application to instantiate any class available in the autoload path, with any property values.
The Attack Surface
The flaw typically resides in Craft CMS controllers handling API requests or plugin configurations where input sanitization focuses on XSS (HTML tags) rather than logic (Class definitions).
- Source: User-supplied JSON (e.g.,
POST /actions/vulnerable-plugin/save-config). - Sink:
Yii::createObject($userInput).
Constructing the Kill Chain: The PoC
Exploitation requires finding a Gadget—a class that performs dangerous operations (like file writing or command execution) in its lifecycle methods (__construct, init, __destruct, or __wakeup).
In the context of CVE-2025-32432, we leverage a common gadget chain found in the Yii2 ecosystem involving yii\\rest\\IndexAction or similar callback-heavy classes.
The Concept
We want to instantiate a class that allows us to execute a PHP callback function (like system or exec) on a supplied argument.
Weaponized JSON Payload
Below is a conceptual Proof of Concept (PoC) demonstrating how to trigger RCE by injecting a malicious class definition.
JSON
{ "rce_trigger": { "class": "yii\\\\rest\\\\IndexAction", "checkAccess": "system", "id": "rce", "controller": { "class": "yii\\\\web\\\\Controller", "id": "dummy" }, "modelClass": "yii\\\\base\\\\Model", "run": "id; uname -a" } }
Breakdown of the Payload:
class: We instruct the DI container to instantiateyii\\rest\\IndexAction.checkAccess: This is our dangerous property. In this specific gadget, thecheckAccessproperty is designed to hold a callable. We set it tosystem.- Triggering the Execution: When the application processes this object (often during the
run()method execution or property validation), it invokes the callback stored incheckAccesswith arguments supplied by the context (or attacker). - Result: The server executes
system('id; uname -a').
Note: In a hardened environment, attackers might chain this with yii\\caching\\FileCache to write a PHP web shell to the web/ directory.
Why Traditional Scanners Miss This
Detecting CVE-2025-32432 is notoriously difficult for legacy DAST tools.
- No Signature: The payload is valid JSON. It doesn’t contain SQL injection syntax (
' OR 1=1) or XSS tags (<script>). - Context Dependent: The vulnerability isn’t in the input itself, but in how the framework interprets the
classkey. A standard scanner does not understand thatclassmaps toYii::createObject.
AI-Driven Detection: The Penligent Advantage
This is where Penligent.ai changes the paradigm. Penligent utilizes Context-Aware AI Agents that understand framework-specific logic.
- Framework Recognition: Penligent’s agents identify that the target is running Craft CMS / Yii2. It knows the “Dangerous Sinks” specific to this framework (e.g.,
Yii::createObject). - Logic Inference: Instead of blind fuzzing, the AI analyzes the API schema. If it sees a JSON object accepting configuration-like parameters, it intelligently injects “Probing Payloads”—such as attempting to instantiate a benign class like
yii\\helpers\\VarDumper—to test if the container is reachable. - Automated Verification: If the probe succeeds (e.g., the application behaves differently or returns a specific error indicating class instantiation), Penligent flags the endpoint as vulnerable to Container Injection and generates the specific RCE payload for remediation validation.
Remediation and Defense
To secure Craft CMS against CVE-2025-32432 and similar DI attacks:
- Strict Type Checking: Never pass raw user input arrays to
Yii::createObject. Always validate that theclasskey is either absent (hardcoded in backend) or strictly allow-listed. - Update Craft CMS: Apply the latest patches immediately. The vendor has likely tightened the
actionprocessing logic to reject arbitrary class definitions. - Disable Dangerous Functions: In your
php.ini, usedisable_functionsto blocksystem,exec,passthru, andproc_opento mitigate the impact of RCE.
Conclusion
CVE-2025-32432 is a stark reminder that modern PHP frameworks, while powerful, introduce complex attack surfaces. Container Injection is the “SQL Injection of the 2020s”—a logic flaw that grants total control.
For security engineers, the lesson is clear: If you let users define the objects, they will define your destruction. Validating the “Shape” of data is no longer enough; you must validate the “Type.”


