Modern applications rely on APIs more than ever — from mobile apps to microservices and cloud platforms — making api testing a cornerstone of functional quality and security assurance. API testing isn’t just about correctness; it’s about resilience under malicious pressure, compliance with security policies, and readiness for real-world exploitation attempts.
This comprehensive guide, grounded in authoritative sources and practical experience, is designed for security engineers, penetration testers, and AI-accelerated automation teams who need to understand api testing deeply — how it works, why attackers target it, what tools and methodologies exist, and how AI can elevate testing and detection workflows.

What Is API Testing and Why It Matters
API testing is the process of examining application programming interfaces to verify functional behavior, performance, compliance, and especially security correctness. Because APIs act as core communication layers between services and clients, failures at this layer can lead to severe breaches, downtime, and business disruption.
According to IBM’s API Testing overview, API tests ensure that backend logic behaves appropriately under various inputs, protects data securely, and delivers consistent responses across scenarios.
Unlike GUI or UI testing, API testing interacts directly with the endpoints, which enables teams to:
- Validate correctness of outputs and data formatting
- Test authorization and session management flows
- Simulate edge cases and unexpected inputs
- Discover vulnerabilities like injection flaws, BOLA/BFLA, and logical misuse
Given that APIs have become the de facto backbone of distributed systems and microservices, skipping rigorous security and functional testing is no longer an option — it’s a business risk.
API Testing Taxonomy: Functional, Security, and Beyond
API testing encompasses multiple layers. Below is a high-level classification:
| Category | Purpose | Security Focus |
|---|---|---|
| Functional Testing | Match expected output to input | Minimal security depth |
| Integration Testing | Verify inter-service communication | Can reveal logic misuse |
| Regression Testing | Ensure changes don’t break behavior | Baseline security checks |
| Performance & Load Testing | Verify performance under stress | Detect DoS thresholds |
| Security Testing | Detect vulnerabilities and misuse | Critical vulnerability discovery |
Security testing, specifically, tries to emulate real attack behavior rather than just expected inputs. This includes authentication/authorization abuse, parameter manipulation, session hijacking, and dangerous payload injection.
API Security Testing: Core Techniques Engineers Must Know
Security-focused API testing goes beyond expected behaviors; it tries to replicate how a real world attacker probes and abuses endpoints. Here are essential techniques referenced by authorities in API security:
Authentication & Authorization Testing
APIs commonly use OAuth2, JWT, API keys, and custom auth logic. Testing must examine:
- Weak token issuance and replay
- Broken Object Level Authorization (BOLA)
- Broken Function Level Authorization (BFLA)
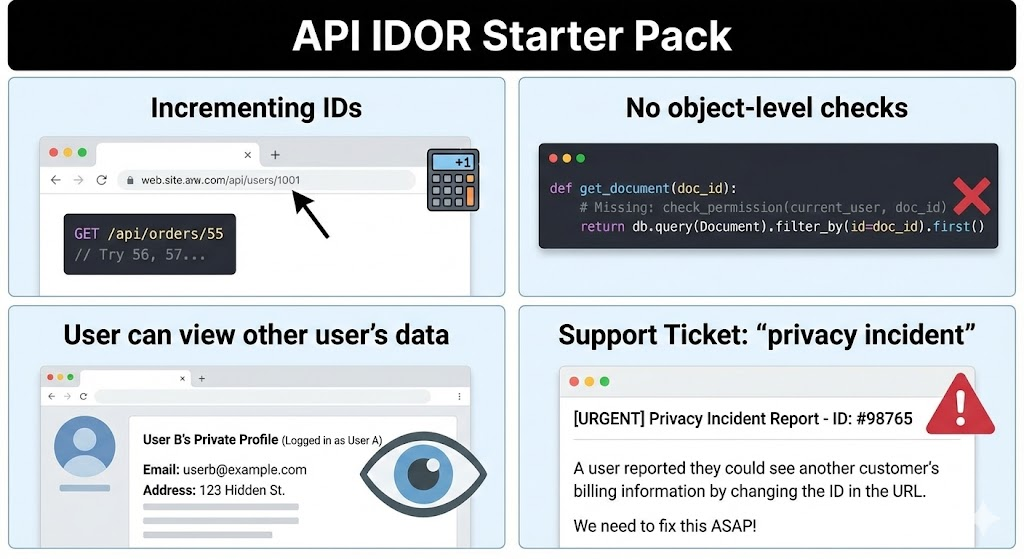
BOLA vulnerabilities often allow malicious actors to access other users’ data simply by changing IDs in requests (e.g., /api/users/123 → /api/users/456).
- Input & Data Flow Testing
APIs must be robust against malformed, oversized, or unexpected parameters. Techniques here include:
- Fuzzing: Sending random or semi-structured malformed inputs
- Parameter tampering and schema violation tests
- JSON and XML structure abuses
Fuzz testing helps surface coding errors or logic flaws that static analysis might miss.
Dynamic & Runtime Testing
Dynamic Application Security Testing (DAST) interacts with running API services to mimic attacker behaviors, uncovering authentication flaws, injection risks, and security misconfigurations.
Endpoint Discovery & Inventory
Attackers first enumerate API surface before launching targeted attacks. Using discovery tools to find shadow or zombie APIs ensures unknown endpoints are included in security tests.
Continuous Monitoring and RASP
Runtime Application Self-Protection (RASP) watches live traffic and detects harmful behaviors during execution, enabling anomaly detection beyond pre-deployment testing.
Compliance & Standards
Align API security testing with frameworks such as the OWASP API Security Top 10 and leverage resources like the OWASP API Security Testing Framework for standardized coverage.
Automated API Testing Tools Landscape
Automating API testing helps shift left in CI/CD, enabling collaboration between development, security, and DevOps teams. Below are categories of tools commonly used:
Static or Spec-Driven Scanners
Tools that scan OpenAPI/Swagger or documentation to identify schema mismatches, insecure definitions, or missing controls.
Dynamic & Fuzzing Tools
- JMeter — Offers load and fuzzing capabilities for REST/HTTP APIs. Useful for stress and injection boundary tests.
APIsec, StackHawk, Schemathesis — Tools that generate test cases from API definitions and execute in CI/CD.
Manual & Interactive Security Tools
- Burp Suite and OWASP ZAP — Useful for interactive pentesting and crafting tailored attack flows.
- Custom Postman Collections integrated with security fuzz payloads
Specialized Security Scanners
Tools that focus exclusively on API vulnerabilities, deep logic testing, and runtime behavioral analysis.
The right mix often involves combining automated scans with manual penetration efforts for coverage against both low-hanging vulnerabilities and deep logic abuse cases.
Real-World API Vulnerabilities & Security Lessons
While API testing itself isn’t a vulnerability, it’s crucial for uncovering flaws that expose data, logic, or infrastructure. A common category of API weaknesses includes Broken Function Level Authorization and BOLA — often exploited when APIs don’t validate resource access properly.
Another attack surface comes from injection abuses when input validation is lax, leading to cases where attackers manipulate data to escalate privileges or leak sensitive information.
In dynamic environments (microservices, third-party integrations), API endpoints can also introduce configuration drift, where evolving features break previously assumed security invariants — reinforcing why continuous testing is essential.
Practical Code Examples for API Security Testing
Below are concrete examples showing how engineers can script API tests for security validation.
Example 1: JWT Authorization Abuse Test (Python/Requests)
python
import requests
API_URL = "<https://api.example.com/v1/resource>"
invalid_jwt = "eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.invalidsignature"
response = requests.get(API_URL, headers={"Authorization": f"Bearer {invalid_jwt}"})
print(response.status_code, response.json())
Goal: verify invalid or manipulated tokens shouldn’t grant access.
Example 2: Fuzzing an Endpoint
bash
#!/bin/bashURL="<https://api.example.com/v1/update>" for payload in '{"id":-1}' '{"id":"A"}' '{"id":9999999999}'; do curl -X POST -H "Content-Type: application/json" \\ -d "$payload" "$URL"done
Purpose: simulate malformed input to observe error responses.
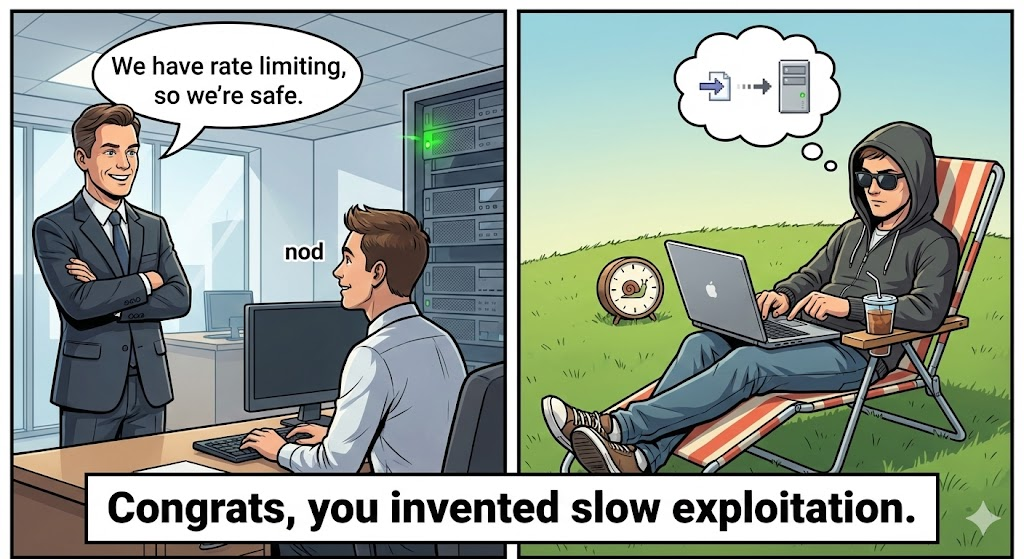
Example 3: Rate Limiting & Brute Force Simulation (Node.js)
javascript
const axios = require("axios");
async function bruteForceLogin() {
for (let i = 0; i < 20; i++) {
try {
await axios.post("<https://api.login.com/auth>", { username: "admin", password: "wrong" });
} catch (e) {
console.error(Attempt ${i} – HTTP ${e.response.status});
}
}
}
bruteForceLogin();
Check: does the API enforce rate limits or account lockout?
Automating API Testing in CI/CD Environments
To maximize impact, API tests should be integrated into CI/CD pipelines so every commit triggers automated functional and security checks. This “shift left” approach catches logic and security flaws early, reducing remediation cost and cycle time.
Common strategies include:
- Gate merge/pull requests based on API security scan results
- Use test definitions as living documentation (e.g., OpenAPI)
- Combine SAST/DAST with API fuzzing and manual pentest workflows
- Correlate test outputs with runtime logs to prioritize real risks
Continuous testing helps match the rapid delivery cycles of modern software without exposing unsecured APIs to production.
AI & Automated API Testing: Beyond Simple Scans
AI can significantly enhance API testing by:
- Generating intelligent test inputs that cover edge cases
- Classifying unexpected patterns that static rules miss
- Detecting logic misuse patterns via behavior profiling
- Automating de-templating and fuzz orchestration across microservices
Recent research suggests AI and LLMs can assist input partitioning and test generation, increasing coverage and detecting otherwise overlooked vulnerabilities.
Integrating AI models into API security testing frameworks enables testing that mirrors attacker exploration behaviors, not just textbook cases.
Summary: Building a Modern API Security Testing Program
API testing is now a core component of secure development and delivery. It validates not only correctness but also security posture against known and evolving threats. An effective API testing strategy should include:
- Functional validation and contract testing
- Security-oriented testing (auth, data abuse, injection)
- Fuzzing and dynamic scanning
- CI/CD integration for automated and continuous testing
- AI-accelerated test generation and runtime analysis
As APIs proliferate and digital transformation accelerates, a mature api testing practice isn’t merely best practice — it’s essential for safeguarding data, protecting users, and maintaining operational continuity.