يتم استهداف مواقع ووردبريس بلا هوادة في طبقة تسجيل الدخول. السبب بسيط: المصادقة هي نقطة اختناق عالمية، و wp-login.php يمكن التنبؤ به عبر ملايين عمليات النشر. عندما يقوم المهاجمون بالتشغيل الآلي على نطاق واسع - حشو بيانات الاعتماد، ورش كلمات المرور، والتخمين الموزّع - فإن السؤال ليس ما إذا كان موقعك سيتعرض للاختراق، ولكن ما إذا كانت دفاعاتك مصممة للصمود تحت ضغط حقيقي.
تم تصميم هذا الدليل من أجل التحقق الأمني المصرح به و الهندسة الدفاعية. يركز على كيفية نمذجة سلوك المهاجمين الواقعي بأمان، وكيفية قياس المرونة، وكيفية تقوية مصادقة WordPress بطريقة فعالة وقابلة للملاحظة ومستدامة من الناحية التشغيلية.
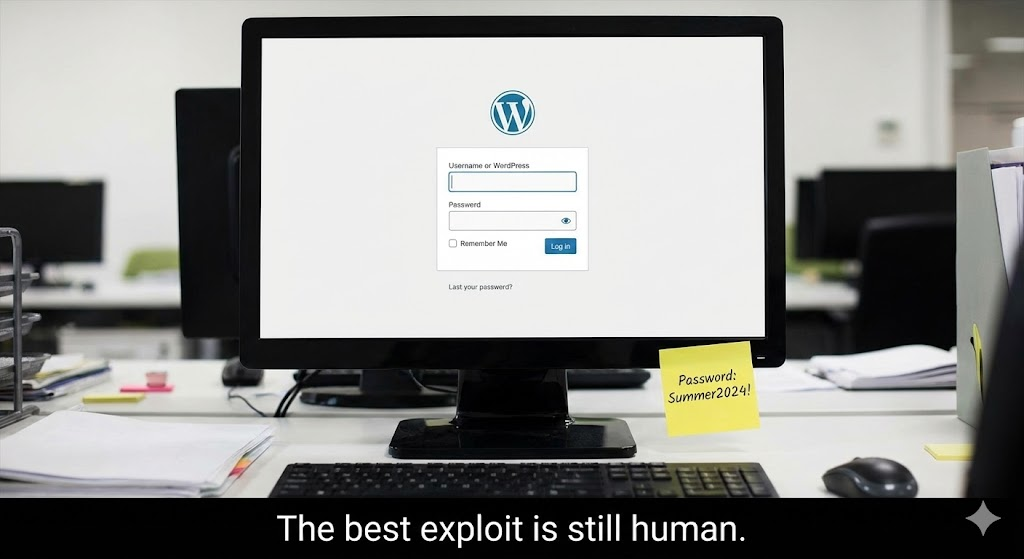
كيف تبدو "الهجمات الواقعية لتسجيل الدخول إلى ووردبريس" في البرية
معظم عمليات اختراق WordPress التي تبدأ عند تسجيل الدخول لا تعتمد على ثغرات غريبة. فهي تعتمد على الاقتصاد:
حشو أوراق الاعتماد يعيد المهاجمون تشغيل أزواج اسم المستخدم/كلمة المرور المسرّبة من اختراقات سابقة، مراهنين على إعادة استخدام كلمات المرور.
رش كلمة المرور: يجرب المهاجمون مجموعة صغيرة من كلمات المرور المشتركة عبر العديد من الحسابات لتجنب عمليات الإغلاق.
التخمين الموزع: تنتشر المحاولات عبر العديد من عناوين IP والنوافذ الزمنية لتجاوز حدود المعدل الأساسية.
ضغط التوفر: قد يكون هدف المهاجم هو التوقف عن العمل، وليس استنفاد عمال PHP أو اتصالات قاعدة البيانات.
الفكرة الأكثر أهمية: "القوة الغاشمة الصاخبة" من عنوان IP واحد ليست التهديد الأكثر واقعية. فالحملات الحقيقية غالبًا ما تكون منخفضة المعدل وموزعة ومستمرة.
سطح هجوم مصادقة ووردبريس للمصادقة: wp-login.php و xmlrpc.php
wp-login.php هي نقطة النهاية التفاعلية الأساسية لتسجيل الدخول التفاعلي. وهي مستهدفة لكل من الاستيلاء على الحساب والضغط بأسلوب DoS.
xmlrpc.php موجودة لعمليات التكامل القديمة والنشر عن بُعد. إذا تُركت مفتوحة، يمكنها توسيع طرق تفاعل الروبوتات مع المصادقة ويمكن إساءة استخدامها كقناة أتمتة إضافية.
إذا لم يكن موقعك في حاجة ماسة إلى XML-RPC، فإن إزالته أو تشديده بإحكام هو أحد أعلى معدلات التخفيضات في التعرض.
المحاكاة الآمنة والمصرح بها: ما يجب اختباره دون الإضرار بالإنتاج
يتم تعريف المحاكاة الواقعية بثلاث خصائص:
محدود: للاختبارات حدود قصوى للأسعار، ونوافذ زمنية، وشروط إيقاف.
قابلة للقياس: تقوم بتسجيل كتل الحافة، وتحميل الأصل، ومعدلات الخطأ، وزمن الاستجابة، وأحداث المصادقة.
الممثل: تمثّل السيناريوهات كلاً من الأنماط "السريعة/الصاخبة" و"البطيئة/الموزعة".
الهدف ليس "الاقتحام". الهدف هو التحقق من هذه البيانات بالأدلة:
- يتم حظر معظم حركة المرور المعادية أو اختناقها قبل أن تصل إلى PHP.
- لا يزال بإمكان المستخدمين الشرعيين تسجيل الدخول أثناء الضغط.
- تلتقط السجلات سياقاً كافياً للتحقيق والاستجابة.
- لا يوجد سوء تهيئة واحد (مكون إضافي، نقطة نهاية، تجاوز WAF) يؤدي إلى انهيار الدفاع بأكمله.
يُستخدم Kali Linux بشكل شائع كمحطة عمل أمنية لتشغيل عمليات الاختبار المصرح بها، لكن نظام التشغيل ليس هو نظام الدفاع والهندسة والقياس.
بناء بيئة اختبار تعكس المخاطر الحقيقية
يتطلب الاختبار الهادف وجود كومة تشبه الإنتاج:
- نفس نموذج الاستضافة (NGINX/Apache، وسلوك PHP-FPM، والتخزين المؤقت)
- طبقة الحافة نفسها (قواعد CDN/WAF/البوتات)
- نفس الإضافات الهامة ومسارات القوالب التي تؤثر على المصادقة
- نفس تكوين المصادقة (المصادقة التلقائية (MFA)، والتأمين، وأدوار المستخدم، ومسارات المسؤول)
الاستخدام حسابات الاختبار فقطبأدوار واقعية
- مستخدم اختبار المسؤول
- محرر اختبار المستخدم
- مستخدم اختبار المشترك
يسمح لك هذا بالتحقق من صحة كل من ضوابط الأمان ونصف قطر الانفجار.
الأجهزة أولاً: القياس عن بُعد الذي يجعل النتائج جديرة بالثقة
قبل إجراء أي محاكاة، تأكد من وجود مصادر القياس عن بُعد هذه:
القياس عن بُعد Edge/CDN/WAF
- طلب الحجم حسب المسار (
/wp-login.php,/xmlrpc.php) - إجراءات الحظر/التحدي والأسباب
- أهم مصادر عناوين IP/شبكات الأمان والبلدان
- درجة الروبوت أو توزيع السمعة (إذا كانت متوفرة)
القياس عن بُعد المنشأ
- رموز الاستجابة (200/302/403/403/429/529/5xx)
- زمن التأخير وزمن التأخير (ص95/ص99)
- استخدام عامل PHP وإشباعه
- ضغط اتصال قاعدة البيانات (إذا كان ذلك مناسباً)
قياس التطبيق عن بُعد
- حالات الفشل/النجاح في تسجيل الدخول مع الطابع الزمني، ومحاولة اسم المستخدم، وعنوان IP/عنوان IP المعاد توجيهه، ووكيل المستخدم
- أحداث الإغلاق ومحفزات التحدي
- تغييرات غير متوقعة في الأدوار أو إنشاء مستخدم إداري جديد
وبدون هذه الرؤية، يصبح "اختبار الأمان" سرداً للقصص بدلاً من الهندسة.
خطة اختبار واقعية: سيناريوهات تعكس سلوك المهاجمين
تعتمد خطة التحقق القوية على السيناريوهات وليس على الأدوات.
السيناريو (أ): خط الأساس الصحي
سجل زمن الوصول العادي لتسجيل الدخول واستخدام الموارد في ظل السلوك المشروع. هذه هي نقطتك المرجعية.
السيناريو ب: موجة الروبوتات الصاخبة (إجهاد التوفر)
محاكاة موجة قصيرة من حركة مرور تسجيل الدخول المرتفعة. معايير النجاح:
- ترتفع الكتل/التحديات الحافة بشكل حاد
- يظل الحمل الأصلي مستقرًا
- لا توجد أخطاء 5xx مستمرة
- يظل تسجيل الدخول الشرعي ممكنًا
السيناريو (ج): الضغط الموزع المنخفض والبطيء
محاكاة محاولات متواصلة ومتواضعة المعدل موزعة على مدار الوقت. معايير النجاح:
- الحد من المعدل/التراجع عن المشاركة دون الإضرار بالمستخدمين الحقيقيين
- تظهر سجلات المصادقة بوضوح النمط
- يتم تشغيل التنبيهات عند خطوط الأساس غير الطبيعية لفشل تسجيل الدخول، وليس فقط عند "الارتفاعات المفاجئة"
السيناريو (د): تجربة المستخدم تحت الهجوم
أثناء الضغط النشط، قم بتشغيل عمليات تسجيل الدخول المشروعة وإعادة تعيين كلمة المرور. معايير النجاح:
- يمكن للمستخدمين الحقيقيين المصادقة
- لا تُنشئ سياسات الإغلاق الذاتي للتشويش الذاتي
- تظهر التحديات بشكل انتقائي (للروبوتات)، وليس عالميًا
الهندسة الدفاعية: ضوابط متعددة الطبقات تنجو من الهجمات الحقيقية
الدفاع الفعال لتسجيل الدخول إلى ووردبريس متعدد الطبقات. كل طبقة لها وظيفة مختلفة، ويجب عليك قياس كل واحدة منها.
الطبقة 1: تصلب الهوية (تقليل فرصة نجاح أي محاولة)
المصادقة متعددة العوامل (MFA) لجميع المستخدمين المميزين هو أقوى عنصر تحكم ضد إعادة استخدام بيانات الاعتماد. إذا تم اختراق كلمة مرور، فإن المصادقة المصادقة المصغرة MFA تمنع غالبية محاولات الاستيلاء على "كلمة المرور فقط" من أن تصبح حوادث.
ضوابط إضافية للهوية:
- تقليل عدد حسابات المسؤولين
- إزالة الحسابات القديمة
- فرض كلمات مرور قوية وفريدة من نوعها (سياسات إدارة كلمات المرور)
- تطبيق أقل الامتيازات (المحررون ليسوا مشرفين؛ والمشرفون ليسوا في كل مكان)
الطبقة 2: ضوابط التطبيق (إبطاء الروبوتات وتقليل ردود فعل المهاجمين)
يجب أن تقلل طبقة التطبيق من الإنتاجية الآلية مع الحفاظ على سهولة الاستخدام:
- استخدام أخطاء تسجيل الدخول المتسقة التي لا تكشف ما إذا كان اسم المستخدم موجودًا أم لا
- تفضيل التراجع التدريجي والخنق المؤقت على الإغلاق الطويل والقاسي
- قم بتشغيل التحديات (تحديات CAPTCHA/تحديات الروبوت) بشكل مشروط عندما تظهر حركة المرور تلقائيًا
- إدارة تدفقات إعادة تعيين كلمات المرور بعناية بحيث لا يمكن إساءة استخدامها في التعداد أو الرسائل غير المرغوب فيها
الطبقة 3: تصغير السطح (xmlrpc.php والتعرضات الأخرى غير الضرورية)
إذا لم تكن هناك حاجة إلى XML-RPC، قم بتعطيله.
إذا كانت هناك حاجة إلى بوابتها:
- السماح للمصادر الموثوقة فقط عند الإمكان
- حد المعدل بقوة
- مراقبة خط الأساس لطلبها بشكل منفصل عن
wp-login.php
الحد من السطح ليس "الأمن عن طريق الغموض". إنه إزالة مسارات الهجوم غير الضرورية.
الطبقة 4: ضوابط البنية التحتية (حماية PHP وقاعدة البيانات)
يجب أن تمنع أرخص طبقة لديك معظم حركة المرور.
- إدارة CDN/WAF/البوتات لحظر الأتمتة أو تحدي الأتمتة على الحافة
- الحد من معدل خادم الويب الأصلي لمنع استنفاد عامل PHP
- التخزين المؤقت وضبط الاتصال للحفاظ على استقرار التوفر تحت الضغط
أحد أنماط الفشل الشائعة هو السماح لحركة المرور المعادية بالوصول إلى PHP، ثم محاولة "إصلاحها" باستخدام إضافات WordPress وحدها. هذا مكلف وهش على نطاق واسع.
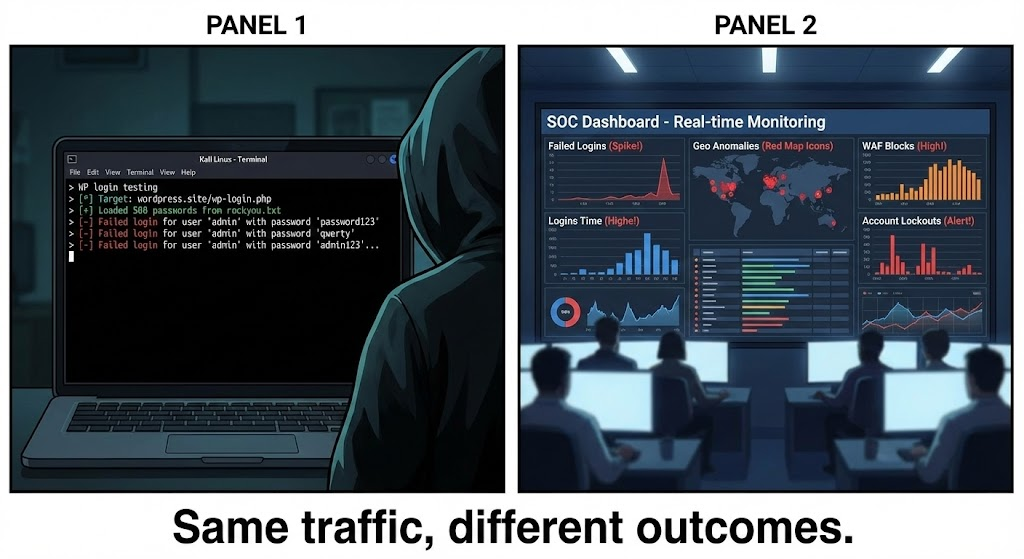
تحديد المعدل من جانب الخادم: شبكة أمان التوفر
حتى مع حماية الحافة، يعد الحد من معدل الأصل أمرًا ضروريًا لأنه يمنع سيناريوهات التجاوز من التحول إلى تعطل.
ليس الهدف الصحيح هو "حجب كل شيء"، ولكن الهدف الصحيح هو
- وضع حد أقصى لمعدلات الطلبات غير الطبيعية لنقاط نهاية المصادقة
- حماية تجمعات العاملين PHP-FPM
- تجنب الإضرار بالمستخدمين الشرعيين
تحديد المعدل الجيد له ثلاث خصائص:
- تم ضبطه على خط الأساس الخاص بك
- يحتوي على قواعد منفصلة ل
/wp-login.phpو/xmlrpc.php - يمكن ملاحظته (يمكنك معرفة متى ولماذا يتم تشغيله)
إشارات الكشف التي تتفوق في أدائها على التفكير بالتوقيع فقط
غالبًا ما يظهر هجوم تسجيل الدخول في أنماط وليس في أحداث فردية.
تشمل المؤشرات عالية الإشارة ما يلي:
- الزيادات المستمرة في عمليات تسجيل الدخول الفاشلة مقارنة بخط الأساس
- المحاولات المنتشرة عبر العديد من الحسابات ذات السمات السلوكية المشتركة
- انحرافات جغرافية/انحرافات جغرافية غير طبيعية
- تحديات الحافة المرتفعة لنقاط نهاية المصادقة
- زيادة زمن انتقال الذيل وتشبع عامل PHP أثناء ضغط المصادقة
نادرًا ما يكون حظر عنوان IP واحد كافيًا. الارتباط هو الفرق بين الضوضاء والذكاء.
الاستجابة للحوادث: ماذا تفعل عندما يتحول الضغط إلى حدث
عند اكتشاف ضغط المصادقة، يجب أن تكون الاستجابة متسقة وسريعة:
- تأكيد صحة المنشأ (زمن الوصول، ومعدلات الخطأ، وتشبع العامل).
- تشديد ضوابط الحافة لنقاط نهاية المصادقة (رفع عتبات التحدي وحدود المعدل).
- فرض قيود أصلية أكثر صرامة إذا لزم الأمر لحماية PHP.
- في حالة الاشتباه في حدوث اختراق
- تدقيق حسابات المستخدمين الإداريين والأدوار
- تدوير بيانات الاعتماد وفرض MFA
- مراجعة تغييرات المكون الإضافي/القالب
- التحقق من وجود اتصالات صادرة غير متوقعة أو تغييرات في الملفات
- مراجعة ما بعد الحادث: تحديث العتبات والقواعد وحقول التسجيل بناءً على الأدلة.
الهدف ليس مجرد التعافي - بل تحسين النظام بحيث يكون التعامل مع نفس النمط أرخص في المرة القادمة.
كيفية الإبلاغ عن النتائج مثل أدلة المهندس على الرأي
يتضمن التقرير المفيد ما يلي:
- السيناريوهات المنفذة والمدة الزمنية
- شكل حركة المرور (حركة المرور (دفعة واحدة مقابل متواصلة، مصدر واحد مقابل موزعة)
- نتائج الحافة: معدل الحظر/التحدي، أهم نقاط النهاية المستهدفة، الأسباب
- النتائج الأصلية: زمن الوصول (p95/p99)، استخدام العامل، معدل الخطأ
- نتائج التطبيق: حالات فشل/نجاح المصادقة/فشل المصادقة، سلوك الإغلاق
- نتائج تجربة المستخدم: ما إذا كانت عمليات تسجيل الدخول المشروعة لا تزال سلسة
- الثغرات: أين وصلت حركة المرور، وما الذي لم يتم تشغيله، وما الذي يجب ضبطه
إذا تم إيقاف معظم حركة المرور المعادية قبل PHP، وظل الأصل مستقرًا، وتمكن المستخدمون الشرعيون من تسجيل الدخول، يكون النظام مرنًا. إذا كان ضغط المصادقة يمكن أن يشبع العاملين أو ينتج عنه أخطاء 5xx، فإن التوافر يكون في خطر حتى لو لم يتم اختراق أي حساب.
الخاتمة
دفاع تسجيل الدخول إلى ووردبريس ليس إضافة واحدة أو قاعدة واحدة. إنه نظام متعدد الطبقات مصمم لمقاومة الأتمتة، والحفاظ على قابلية الاستخدام، وحماية التوافر، وتوفير رؤية واضحة عند حدوث ضغط.
تثبت المحاكاة الواقعية ما إذا كان نظامك صامدًا في ظل اقتصاديات المهاجمين الحقيقية: حركة المرور الموزعة، والمحاولات المنخفضة والبطيئة، والتحري المستمر. ثم تحول الهندسة الدفاعية هذه النتائج إلى ضوابط ملموسة: MFA للمستخدمين ذوي الامتيازات، والاختناق الدقيق والتحديات، وتقليل التعرض السطحي (خاصةً XML-RPC عندما لا يكون ضرورياً)، والحماية القوية للحافة، والحد من معدل المصدر، والقياس عن بُعد القابل للتنفيذ.
عندما تعمل هذه الطبقات معًا، تصبح مصادقة ووردبريس أصعب بكثير في اختراقها ويصبح من غير المرجح أن تصبح مصدرًا للتوقف عن العمل.