مقدمة: API - "كعب أخيل" العمارة الحديثة - "كعب أخيل" العمارة الحديثة
في عصر الخدمات المصغرة والبنية التحتية السحابية الأصلية والترابط بين الأجهزة المحمولة، لم تعد واجهات برمجة التطبيقات مجرد أنابيب للبيانات، بل أصبحت تشكل الجهاز العصبي الرقمي للمؤسسة. ومع ذلك، فإن انفتاحها وتوحيدها المتأصل يجعلها أيضًا هدفًا أساسيًا للمهاجمين.
على عكس الاختبار التقليدي لواجهة المستخدم، الذي يتحقق مما إذا كانت "الأبواب والنوافذ مغلقة"، فإن اختبار أمان واجهة برمجة التطبيقات يتحقق من "الأساس والجدران الحاملة". وقد توقعت شركة Gartner أن تصبح انتهاكات واجهة برمجة التطبيقات أكثر ناقلات الهجمات التي تؤدي إلى اختراق بيانات المؤسسات. لذلك، لا يمكن أن يتوقف اختبار واجهة برمجة التطبيقات عند الصواب الوظيفييجب أن تتحقق بدقة من المرونة و قابلية الدفاع.
تشمل التحديات الرئيسية ما يلي:
- ثغرات التفويض: كيف نكتشف العيوب العميقة على مستوى الكائن ومستوى الوظيفة؟
- أصول الظل: كيف نكتشف "واجهات برمجة التطبيقات الزومبي" غير المُدارة قبل أن يكتشفها المهاجمون؟
- إساءة استخدام المنطق كيف يمكننا محاكاة المهاجمين الذين يستغلون الميزات المشروعة للاحتيال؟
تصنيف الاختبارات: إطار متعدد الأبعاد
اختبار واجهة برمجة التطبيقات ليس متجانساً. لفهم النطاق، نصنف الاختبار إلى ثلاثة أرباع أساسية:
| اختبار البُعد | التركيز الأساسي | نقاط الضعف النموذجية | الأدوات والأساليب |
|---|---|---|---|
| وظيفي | منطق الأعمال، وتنسيق البيانات، وأمانة العقود | استجابات JSON مشوهة، انتهاكات المخطط | بوستمان، جي يونيت، اختبارات العقود |
| الأمن | AuthZ/AuthN، التحقق من صحة المدخلات، إساءة استخدام المنطق | بولا (IDOR)، الحقن، التعيين الشامل | حزمة تجشؤ، OWASP ZAP، تشويش الحزمة |
| الموثوقية والامتثال | حدود الأداء، ومعالجة الأخطاء، وخصوصية البيانات | أعطال الحد من المعدلات، وتسريبات معلومات التعريف الشخصية، ووقت التعطل | الماسحات الضوئية JMeter، K6، PII |
ملاحظة: في برنامج ناضج، تتداخل هذه الطبقات. على سبيل المثال، قد يكشف اختبار الموثوقية الذي يفرض خطأ في الخادم 500 عن خلل أمني عبر تسرب تتبع المكدس.
تقنيات الهجوم الأساسية: ما وراء الماسح الضوئي
يجب أن يتبنى مهندسو الأمن "عقلية المهاجمين". لا يكفي التحقق من ماهية واجهة برمجة التطبيقات يمكن القيام به؛ يجب عليك التحقق مما لا يمكن افعل.
اختبار التخويل العميق (AuthZ Deep Dive)
غالبًا ما تفوت الماسحات الضوئية القياسية عيوب التفويض المنطقي.
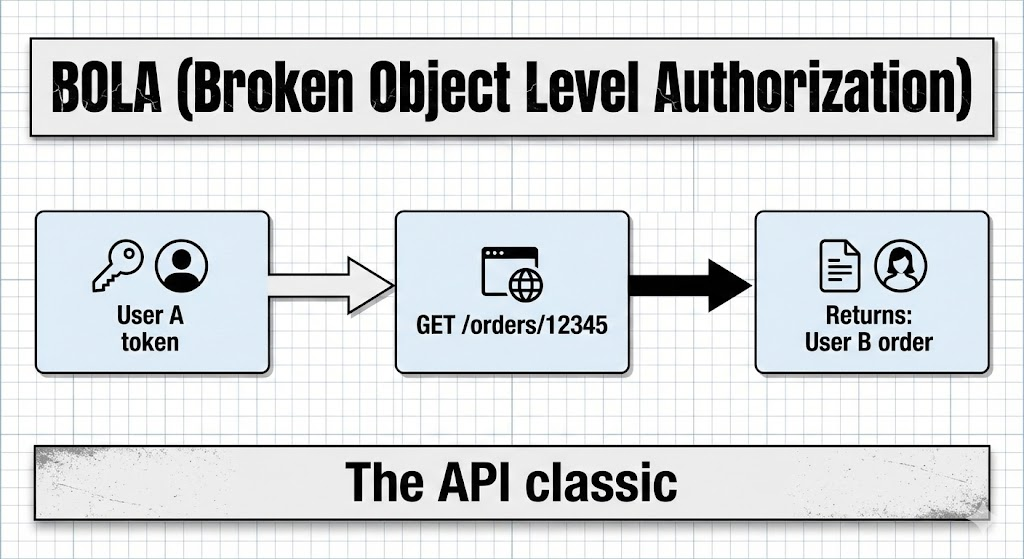
- BOLA (ترخيص مستوى الكائن المكسور): تهديد واجهة برمجة التطبيقات #1. يتطلب الاختبار تعداد المعرفات. إذا كنت المستخدم A، قم بالتكرار من خلال المعرفات (الأعداد الصحيحة، UUIDs) لمحاولة الوصول إلى
/API/الأوامر/{User_B_Order_ID}. - BFLA (تفويض مستوى الوظيفة المكسور): محاولة تبديل أساليب HTTP (على سبيل المثال، تغيير
احصل علىإلىحذف) أو الوصول إلى المسارات المميزة مثل/المشرف/المستخدمونأوداخلي/داخلي/مقاييسباستخدام رمز مستخدم قياسي.
منطق الأعمال وتدفق البيانات
- التعيين الجماعي (الربط التلقائي): اختبر ما إذا كانت واجهة برمجة التطبيقات تربط مدخلات العميل مباشرةً بكائنات التعليمات البرمجية الداخلية دون تصفية.
- هجوم: في تحديث الملف الشخصي، احقن
"is_admin": صوابأو"رصيد_المحفظة": 99999في هيئة JSON لمعرفة ما إذا كانت الواجهة الخلفية تستمر في ذلك.
- هجوم: في تحديث الملف الشخصي، احقن
- إساءة استخدام البيانات المهيكلة: استخدم هجمات الكيانات الخارجية ل XML (XXE) أو كائنات JSON المتداخلة بعمق (JSON DoS) لاستنفاد ذاكرة الخادم ووحدة المعالجة المركزية.
التشويش الذكي
يعثر التشويش على "المجهول المجهول". تجنب الضوضاء العشوائية؛ استخدم التشويش الذكي:
- طفرة الحدود: إرسال أعداد صحيحة تتسبب في حدوث تجاوزات أو أرقام سالبة أو بايتات فارغة.
- ارتباك في النوع: إرسال مصفوفة حيث من المتوقع وجود عدد صحيح (على سبيل المثال,
المعرف[]= 1بدلاً منالمعرف = 1) لتشغيل الاستثناءات غير المعالجة في الواجهة الخلفية.
أمثلة عملية على البرمجة البرمجية: التحقق من أمن البرمجة البرمجية
فيما يلي أمثلة ملموسة لكيفية برمجة التحقق الآلي من متجهات هجوم محددة.
مثال 1: خوارزمية JWT "بلا" وهجوم التوقيع الضعيف (Python)
غالبًا ما يحاول المهاجمون تجريد التوقيع أو ضبط الخوارزمية على لا شيء لتجاوز التحقق.
بايثون
'استيراد طلبات الاستيراد استيراد jwt # PyJWT مكتبة PyJWT استيراد json استيراد base64
محاكاة هجوم: إنشاء رمز مميز باستخدام 'alg': 'لا شيء'
def gener_unsigned_token(payload): # إنشاء رأس وحمولة يدويًا بدون توقيع header = {"alg": "لا شيء"، "نوع": "JWT"}
مساعد # لتشفير base64url
def b64_url(data):
إرجاع base64.urlsafe_b64encode(json.dumps(data).encode()).decode().rstrip("=")
header_b64 = b64_url(header)
الحمولة_ب64 = b64_url(الحمولة)
# إرجاع الرمز المميز بنقطة زائدة ولكن بدون توقيع
return f"{header_b64}.{payload_b64}."
API_URL = "https://api.example.com/v1/admin/resource“
محاولة تصعيد الامتيازات
الرمز المميز الخبيث = توليد_رمز_غير_موقع({"user_id": 1، "الدور": "admin"})
الاستجابة = requests.get(API_URL, headers={"authorization": f"bearer {malicious_token}"})
إذا كان رمز_حالة_الاستجابة == 200: اطبع(f"[CRITICAL] تم قبول واجهة برمجة التطبيقات غير الموقعة/وحدة-رمز JWT! البيانات: {response.text}") غير ذلك: اطبع(f"[SAFE] تم رفض طلب واجهة برمجة التطبيقات. الحالة: {response.status_code}")
مثال 2: اختبار حالة السباق / اختبار التزامن (Bash/Curl)
اختبار ما إذا كانت واجهة برمجة التطبيقات تتعامل بشكل صحيح مع الطلبات المتزامنة (على سبيل المثال، الإنفاق المزدوج للقسيمة).
باش
'#!/bin/bash
إرسال 20 طلبًا متزامنًا لمحاولة استرداد نفس القسيمة ذات الاستخدام الواحد
target_url="https://api.example.com/v1/coupon/redeem" auth_token="Bearer eyJhbGci..." payload='{"coupon_token":"DISCOUNT2024″}
صدى "بدء هجوم حالة السباق..."
بالنسبة إلى i في {1...20}؛ افعل # يضع "&" العملية في الخلفية، وينفذها في وقت واحد تقريبًا curl -X POST -s -o / div / null -w "%{http_code}\n" \ -H "تخويل: $auth_token" \ -H "Content-Type: application/json" \ -d "$P4Tpayload" "$arget_url" \ تم
انتظر صدى "اكتمل الهجوم. تحقق من سجلات الواجهة الخلفية بحثًا عن عمليات استرداد متعددة ناجحة."``
منظومة الأدوات: بناء سلسلة أدوات DevSecOps
تتطلب استراتيجية حديثة لاختبار واجهة برمجة التطبيقات (API) سلسلة أدوات مركبة.
- اختبار المواصفات أولاً/الاختبار التعاقدي:
- المخططات: أداة Python قوية تقرأ مواصفات OpenAPI/Swagger الخاصة بك وتنشئ حالات اختبار لتعطيل واجهة برمجة التطبيقات من خلال انتهاك المخطط.
- طيفية: أداة تبطين ل JSON/YAML لضمان استيفاء تعريفات واجهة برمجة التطبيقات لمعايير الأمان (على سبيل المثال، ضمان تعريف المصادقة لجميع نقاط النهاية).
- ديناميكية وتفاعلية (DAST/IAST):
- جناح التجشؤ الاحترافي: المعيار الذهبي للاختبار الخماسي اليدوي. الإضافات مثل مصفوفة المصادقة ضرورية لتصور جداول الأذونات المعقدة.
- OWASP ZAP: رائع لخطوط الأنابيب المؤتمتة وعمليات الفحص الأساسية.
- ماسحات ضوئية خاصة بواجهة برمجة التطبيقات:
- أدوات مثل APIsec أو ستاك هوك التركيز بشكل خاص على المنطق والهيكل، وفهم العلاقة بين نقاط النهاية بدلاً من فحصها بمعزل عن بعضها البعض.
المستقبل: الذكاء الاصطناعي والماجستير في أمن واجهة برمجة التطبيقات
إن التشويش التقليدي "أعمى"، لكن الذكاء الاصطناعي يجعله "دلالياً".
- توليد الحمولة الواعية بالسياق: يمكن لنماذج LLMs (مثل GPT-4 أو نماذج Llama المحلية) استيعاب وثائق واجهة برمجة التطبيقات وإنشاء حمولات صحيحة من الناحية النحوية ولكنها خبيثة من الناحية المنطقية. (على سبيل المثال, "توليد 10 حمولات JSON التي تحاول تعيين تاريخ التسليم إلى الماضي.")
- كشف حالات الشذوذ في حركة المرور: في الإنتاج، تنشئ نماذج الذكاء الاصطناعي "خط أساس للوضع الطبيعي". إذا كانت نقطة النهاية تُرجع عادةً 2 كيلوبايت من البيانات، ولكنها تُرجع فجأة 2 ميغابايت لمستخدم معين، يمكن أن تحظرها RASP (الحماية الذاتية للتطبيق في وقت التشغيل) باعتبارها عملية تسريب محتملة لبيانات BOLA.
- المعالجة الآلية: لا تكتفي أدوات الجيل التالي بالعثور على الخلل فحسب، بل تقترح إصلاح الكود الدقيق لوحدة التحكم أو البرنامج الوسيط بناءً على إطار العمل الذي تستخدمه.
الخاتمة: بناء برنامج واجهة برمجة تطبيقات مرن
إن اختبار أمان واجهة برمجة التطبيقات (API) ليس تمريناً في خانة الاختيار، بل هو نظام هندسي مستمر.
يجب على المؤسسات أن تتبنى استراتيجية "التحول إلى اليسار + الحماية إلى اليمين":
- انقل إلى اليسار ادمج التحقق من صحة المخططات ومخططات الأمان في خط أنابيب CI/CD لاكتشاف العيوب قبل دمج التعليمات البرمجية.
- الدرع الأيمن: نشر RASP والمراقبة في الوقت الحقيقي في الإنتاج للكشف عن إساءة الاستخدام التي تتجاوز الاختبار.
من خلال الجمع بين الأتمتة الصارمة والاختبارات المنطقية العميقة وسير العمل المعزز بالذكاء الاصطناعي، يمكن للمهندسين تأمين الواجهات المهمة التي تدعم الاقتصاد الرقمي الحديث.