In the AI security landscape of 2026, software-level defenses (like prompt filtering) are no longer the primary focus for advanced Red Teams. The real war is being fought in the darkest corner of the infrastructure: The Hardware Isolation Layer.
You are searching for izen bypass, which means you are targeting the core of modern AI infrastructure: the Isolation Zone Enforcement Node (IZEN). As the industry standard architecture for protecting Model Weights from being dumped on H200/B200 GPU clusters, IZEN is touted as the “unbreakable black box.”
But as with all complex security architectures, IZEN is not invincible. This guide skips the basics and goes straight to the hardcore engineering: how to utilize Voltage Glitching, Micro-architectural Side Channelsو Logical Race Conditions to achieve an IZEN Bypass and extract the billion-dollar asset—the model weights.
Anatomy of IZEN: Why is it Hard to Break?
Before dissecting the izen bypass, we must understand the defender’s logic. IZEN differs from traditional SGX or SEV; it is a TEE specifically designed for Tensor Processing Units (TPUs/NPUs).
- Secure Memory Encryption (SME): IZEN performs real-time AES-GCM-256 encryption on data in VRAM (HBM). Even if you physically probe the memory bus, you get entropy, not weights.
- Control Flow Integrity (CFI): The IZEN coprocessor monitors the Computation Graph’s execution path. Any unexpected jump (like a ROP chain) triggers an immediate NMI interrupt via PCI-e and wipes the keys instantly.
- Zero-Access Management: Even the
الجذرuser on the Host OS cannot access the Guest IZEN memory space.
CVE-2026-33910 The Ring-0 to Ring-3 Hammer
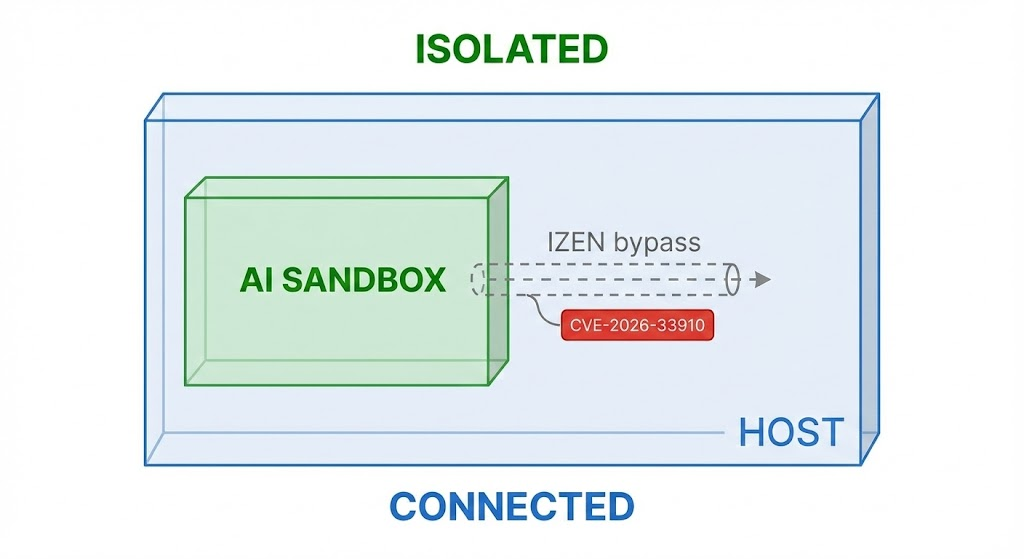
This is currently the most reliable izen bypass vector. CVE-2026-33910 does not exist in the IZEN hardware itself, but in the communication protocol between its driver and the User-mode library.
The Vulnerability:
The IZEN driver contains a وقت التحقق إلى وقت الاستخدام (TOCTOUU) race condition when handling the IOCTL_IZEN_MAP_TENSOR instruction.
The Exploit Chain:
- Memory Map: The attacker requests a shared memory region for tensor transfer.
- Race Trigger: One thread continuously calls
IOCTLto map this memory, while another thread aggressively usesmadviseto free and reallocate the memory (Page Flip). - Page Table Confusion: With low probability, the IZEN DMA engine fetches the wrong Physical Address, mapping a protected “Model Weight Page” into the attacker’s user-mode space.
- Extraction: The attacker reads the memory page, retrieving decrypted model weight fragments.
Concept PoC:
C
`// IZEN Bypass via TOCTOU (CVE-2026-33910 Concept) void race_thread() { while (!stop) { // Aggressively flip memory pages to confuse the IZEN DMA madvise(shared_buf, BUF_SIZE, MADV_DONTNEED); mmap(shared_buf, BUF_SIZE, PROT_READ|PROT_WRITE, …); } }
void trigger_thread() { struct izen_ioctl_args args = { .handle = shared_buf, .op = TENSOR_MAP }; while (!stop) { // Trigger the driver mapping, hoping for a page table mismatch ioctl(fd, IOCTL_IZEN_MAP_TENSOR, &args); if (check_if_weights_leaked(shared_buf)) { printf(“[+] IZEN Bypass Successful! Weights dumped.\n”); stop = 1; } } }`
Voltage Glitching (Physics vs. Logic)
If the software layer is patched, hardcore engineers turn to physics. The IZEN chip is extremely sensitive to voltage during “Key Derivation.”
The Attack:
By controlling the GPU’s VRM (Voltage Regulator Module), an attacker drops the voltage by 150mV for a single nanosecond during the specific Clock Cycle where IZEN executes the AES_DECRYPT instruction.
The Result:
This “glitch” causes the CPU pipeline to skip security checks (e.g., a JNZ instruction is misinterpreted as NOP) or causes the encryption engine to output a faulty intermediate state. Using Differential Fault Analysis (DFA), attackers can recover the IZEN Root Key in hours.
AI Logic Side Channels The “Silent” Leak
This is a non-root izen bypass technique specifically targeting LLM inference services.
The Theory:
While IZEN isolates memory, it cannot isolate Computation Time. Different model weight values cause microscopic differences in latency during floating-point operations.
The Implementation:
Attackers construct a series of specific Prompts (high-dimensional sparse matrix multiplications) and precisely measure the Time-to-First-Token (TTFT). By analyzing the timing distribution of millions of requests, attackers can train a “Shadow Model” to infer the core weight distribution of the protected model. This is known as “Contactless Weight Theft.”
Automated IZEN Pentesting: The Penligent Advantage
قد تسأل: “How do I know if my AI Cluster is vulnerable to these IZEN vectors?” Testing these manually (especially race conditions and side channels) requires immense cost and niche expertise.
هذا هو المكان Penligent.ai يغيّر اللعبة
Penligent is not just a web scanner; it is the industry’s first platform to support AI Hardware Isolation (AI-TEE) testing. For izen bypass risks, Penligent provides dedicated modules:
- TEE Fuzzing Agent: Penligent deploys a privileged agent on the host to perform high-coverage fuzzing against the IZEN driver interface. It uses AI to predict which IOCTL parameter combinations are most likely to trigger DMA race conditions like CVE-2026-33910.
- Side-Channel Analyzer: Penligent sends thousands of engineered mathematical probes to your inference endpoint, automatically collecting timing data and calculating if statistically significant side-channel leakage exists. If Penligent can guess your model’s layer count via API latency, it alerts you immediately.
- Compliance Audit: Automatically checks Host OS kernel parameters, BIOS settings, and IZEN Firmware versions to ensure
Secure BootوMemory Encryptionare strictly enforced.
Defense & Hardening
Once an izen bypass path is found, defenders must respond at the architectural level:
- Update Firmware: Ensure IZEN Firmware is updated to version 2026.01, which patches the known IOCTL race logic.
- Disable Vulnerable IOCTLs: If dynamic tensor mapping is not required, disable the
IOCTL_IZEN_MAP_TENSORfeature via kernel module parameters to reduce the attack surface. - Introduce Noise: Inject random microsecond-level delays (Jitter) into the inference service to destroy the temporal correlation required for side-channel attacks.
- Continuous Red Teaming: Use بنليجنت to stress-test your AI hardware environment regularly. The value of an AI model lies in its weights; the only way to protect them is to constantly try to steal them.
الخاتمة
إن izen bypass represents the highest level of adversarial AI. It is no longer about SQL Injection or XSS; it is about control over the essence of computation. As model weights become the core asset of the enterprise, attacks against isolation technologies like IZEN will become routine. Only by mastering these hardcore offensive techniques can security engineers hold the line in the Compute Wars of 2026.
المراجع
- Confidential Computing Consortium: Hardware-based Isolation Standards
- USENIX Security 2025: Breaking TEEs with Voltage Glitching: A Case Study on AI Accelerators
- CVE-2026-33910 Detail: NIST NVD – IZEN Driver Race Condition
- بنليجنت Automated AI-TEE Security Validation


