In the high-stakes arena of 2026, where security engineers are tasked with fortifying Large Language Model (LLM) inference clusters and securing Agentic workflows, it is easy to succumb to “complexity bias.” We assume our adversaries are crafting sophisticated adversarial machine learning attacks or prompt injections. We assume the threat is cutting-edge.
We are wrong.
الكشف عن CVE-2026-24061—a critical authentication bypass in GNU InetUtils telnetd—is a stark, violent reminder that the foundational bedrock of our infrastructure is rotting. This vulnerability allows a remote, unauthenticated attacker to gain root privileges simply by manipulating the Telnet protocol’s environment variable negotiation.
This article is written for the hardcore security engineer. We will not waste time explaining what Telnet is. Instead, we will dissect the C-level logic error that caused this, analyze the packet-level exploitation mechanics, and discuss why this seemingly “dead” protocol remains a catastrophic risk for modern AI compute clusters.
The Mechanic: Argument Injection via NEW-ENVIRON
To understand CVE-2026-24061, one must understand the interaction between a daemon and the login binary.
The Architecture of a Login
When a user connects to a Telnet server, the telnetd daemon does not perform the authentication itself. Its job is to handle the TCP connection, negotiate terminal capabilities (via RFC 854), and then تنفيذ() a login program (usually /bin/login) to handle the actual credential verification.
To improve user experience, RFC 1408 and RFC 1572 defined the NEW-ENVIRON option. This allows the Telnet client to send environment variables to the server, which telnetd can then pass to the login process. The most common use case is passing the USER variable so the user doesn’t have to type their username twice.
منطق الضعف
The vulnerability exists in how GNU InetUtils telnetd (specifically versions prior to 2.7-2) constructs the argument list for /bin/login.
In a correct implementation, the daemon should treat the USER environment variable strictly as data. However, the vulnerable code takes the content of the USER variable and blindly appends it to the argument vector (argv) passed to execv().
إن /bin/login binary on most Linux systems (util-linux) accepts a specific flag: -f.
- Flag:
f username - Meaning: “Do not perform authentication. The user is already authenticated.”
This flag is intended for use by programs like ssh أو rlogin that have already performed strong cryptographic authentication. It should أبداً be accessible via user-controlled input from an unauthenticated stream.
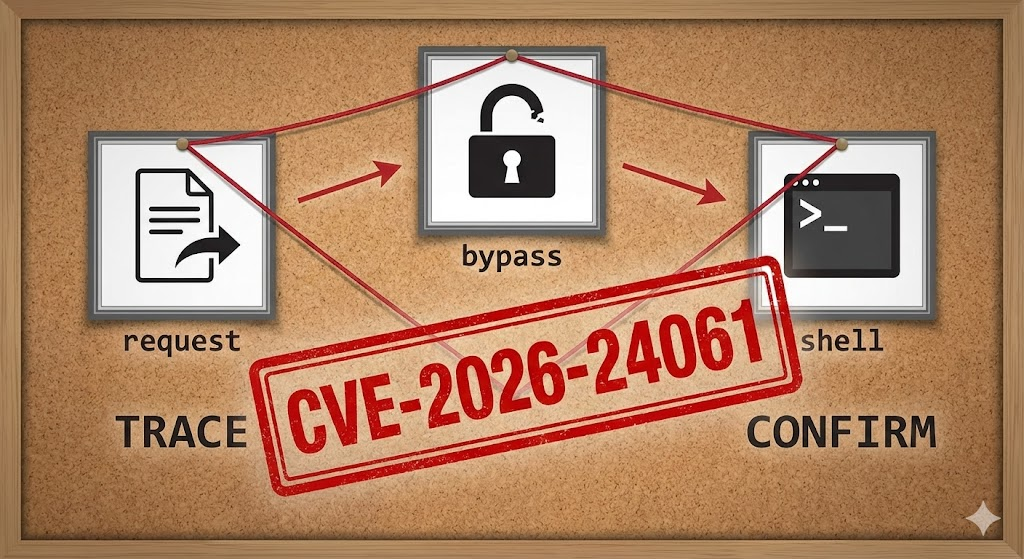
مسار الاستغلال
The attack path is trivially simple, which contributes to the CVSS 9.8 score.
- Handshake: The attacker initiates a TCP connection to port 23.
- Negotiation: The attacker’s client sends
IAC WILL NEW-ENVIRON. - Payload Injection: The attacker sends a specific environment definition packet where the
USERvariable is set tofroot. - التنفيذ:
telnetdreceivesUSER="-froot".telnetdconstructs the execution call:/bin/login -h <client_ip> -p -froot./bin/logininterpretsfroot(أوf root) as a command to log the user in asالجذرwithout a password.
- النتيجة: The attacker is dropped immediately into a root shell
#.
Packet-Level Analysis
For the engineer building intrusion detection signatures (IDS) or analyzing PCAP data, identifying this attack requires looking inside the Telnet option negotiation.
A standard Telnet connection is noisy. However, the exploit payload is distinct.
نص عادي
[Client] -> [Server] Byte: FF FD 27 (IAC DO NEW-ENVIRON) Byte: FF FB 27 (IAC WILL NEW-ENVIRON)
Once the sub-negotiation begins, the malicious payload appears. Here is a hex reconstruction of the lethal packet:
FF FA 27 00 00 55 53 45 52 01 2D 66 72 6F 6F 74 FF F0
Breakdown:
FF FA: IAC SB (Sub-negotiation Begin)27: Option 39 (NEW-ENVIRON)00: IS (Information provided)00: VAR (Variable type)55 53 45 52: “USER” (The variable name)01: VALUE (Separator)2D 66 72 6F 6F 74: “-froot” (The malicious payload)FF F0: IAC SE (Sub-negotiation End)
If your IDS sees a Telnet environment variable containing a dash - followed by f, الجذرأو user, it is a definitive Indicator of Compromise (IoC).
The “AI Infrastructure” Vector: Why It Matters in 2026
The immediate dismissal of this vulnerability usually sounds like: “We don’t use Telnet.”
As an AI Security Engineer, you might believe your environment is pure: SSH keys, mTLS, zero-trust architectures. However, reality is messy. CVE-2026-24061 is currently ravaging three specific sectors of the AI ecosystem:
1. High-Performance Computing (HPC) & GPU Clusters
The massive clusters used for training LLMs often rely on Baseboard Management Controllers (BMCs) and Out-of-Band (OOB) management networks.
- The Reality: Many server manufacturers ship BMC firmware based on ancient, stripped-down Linux distributions (like BusyBox or old GNU userlands).
- المخاطرة: These BMCs often have
telnetdenabled by default for “factory debugging” on a secondary interface. If an attacker pivots from a compromised web frontend into the management VLAN, they can use CVE-2026-24061 to root the BMCs, allowing them to persistently backdoor the GPU nodes or steal model weights directly from memory dumps.
2. Edge AI & IoT Inference
The deployment of models to “the edge” (smart cities, autonomous drones, industrial sensors) involves hardware that prioritizes low power and low cost over security.
- The Reality: Embedded Linux builds (Yocto, Buildroot) frequently include
inetutilsrather than the heavier OpenSSH. - المخاطرة: An attacker can compromise a single sensor via Telnet, modify the inference model weights (Model Poisoning), and cause the AI to hallucinate or misclassify objects in the physical world.
3. Legacy Data Pipelines
Training data often comes from legacy databases or mainframe connectors that have been running for decades.
- The Reality: “If it ain’t broke, don’t fix it.” We often find data ingestion servers running RHEL 6 or older Debian versions tucked away in a dusty corner of the VPC, quietly scraping data via scripts.
- المخاطرة: These are the soft underbelly. Rooting one of these servers provides a direct tunnel into the Data Lake.
The Failure of “Version-Based” Vulnerability Management
One of the most frustrating aspects of CVE-2026-24061 is the difficulty in detecting it via standard vulnerability scanners.
The False Negative Problem:
Traditional scanners (like Nessus or OpenVAS) often rely on “Banner Grabbing.” They connect to port 23, read the banner (e.g., Welcome to Linux 5.x), and attempt to guess the version.
ومع ذلك, inetutils telnetd rarely announces its specific patch version in the banner. A banner might simply say Telnet server ready.
Consequently, a version-based scanner will look at the OS version, see it’s “Modern Ubuntu,” and assume the package is patched. It fails to verify if the binary specifically allows the argument injection.
This is where the methodology of اختبار الاختراق must evolve from “Assessment” to “Validation.”
Agentic Pentesting: The Penligent Approach
In the era of Agentic AI, relying on human pentesters to manually check for 1990s vulnerabilities is inefficient. Humans have cognitive bias; they see Port 23 and ignore it, assuming it’s a rabbit hole.
هذا هو المكان Penligent.ai fundamentally changes the defensive posture.
1. Context-Aware Fuzzing
Unlike a static scanner, Penligent’s AI agents perform active, stateful interaction. When a Penligent agent encounters an open Telnet port, it doesn’t just check the banner. It reasons: “This looks like a legacy service. I should test for Argument Injection vulnerabilities specific to this protocol family.”
The agent dynamically constructs the RFC-compliant NEW-ENVIRON packets. It acts as a client, attempting the specific -f root الحقن.
2. Proof, Not Probability
The output from Penligent is not a “Potential Vulnerability” warning. It is a screenshot or a log entry of a root shell.
- The Workflow: The Agent attempts the injection -> receives the
#prompt -> runsالهوية-> captures the outputuid=0(root)-> closes the session immediately. - This “Verified Risk” approach allows security teams to bypass the triage phase and go straight to remediation.
3. Continuous Infrastructure Validation
In 2026, infrastructure is code. It changes hourly. Penligent’s agents sit inside the CI/CD pipeline and the live network. If a developer accidentally uncomments a line in a Dockerfile that installs inetutils-telnetd for debugging and pushes it to the GPU cluster, Penligent detects and exploits it within minutes of deployment, long before a human attacker finds it using Shodan.
استراتيجيات المعالجة والتخفيف من الآثار
If you identify this vulnerability in your environment, immediate action is required. The CVSS 9.8 score implies that automation is likely already scanning for this.
Immediate Fix: Service Termination
There is almost no scenario in 2026 where Telnet is required over SSH.
باش
`# Locate the service systemctl list-units | grep telnet
Stop and Disable
systemctl stop telnet.socket systemctl disable telnet.socket
Mask it to prevent accidental restart
systemctl mask telnet.socket`
Mitigation: Packet Filtering (If Telnet is strictly required)
If you are running a legacy mainframe interface that يجب use Telnet, you must restrict access via iptables أو nftables to a specific jump box / bastion host.
Do not rely on the hosts.allow أو tcpwrappers for this, as the exploit happens قبل some wrapper implementations fully restrict the process creation.
Detection: eBPF Monitoring
For deep visibility, deploy an eBPF probe to monitor execve system calls. Alert immediately if:
- The parent process is
telnetd. - The child process is
login. - The arguments to
loginincludef.
C
// Pseudo-code for eBPF hook SEC("tracepoint/syscalls/sys_enter_execve") int trace_exec(struct trace_event_raw_sys_enter_execve *ctx) { // Check if current comm is telnetd // Check if filename is /bin/login // Scan argv for "-f" // If match -> ALERT }
Conclusion: The Long Tail of Legacy
CVE-2026-24061 is not technically novel; it is a recurrence of the “Argument Injection” class of bugs that plagued the 90s. Yet, its presence in 2026 is a critical lesson for the AI Security Engineer.
We are building the most advanced cognitive systems in human history. We are discussing AI Alignment, Agentic reasoning, and neural security. But if the server rack holding the H100 GPUs is accessible via a root-level bypass in a 30-year-old protocol, our advanced defenses are meaningless.
Security is a full-stack discipline. It requires the humility to look backward at the legacy protocols we thought we left behind, and the intelligence to use modern tools like بنليجنت to automate the validation of that exposure.
Don’t let a 1995 protocol kill your 2026 AI project.
المراجع والمزيد من القراءة


