لماذا لا تزال ورقة غش xss أخرى مهمة
الأطر الحديثة ≠ خالية من XSS. يقلل الهروب التلقائي في React/Angular/Svelte من ثغرات النمذجة، ولكن لا تزال الأنظمة الحقيقية تشحن سوء استخدام واجهة برمجة DOM، وعناصر واجهة برمجة تطبيقات الطرف الثالث غير الآمنة، و Markdown/WYSIWYG المتساهلة, جافا سكريبت: معالجات عناوين URL، وSVG/MathML، وبقايا JSONP، والثقة الضمنية في الموقع/التجزئة/رسالة بعد الرسالة.
تتطور النظم البيئية الناقلة. يقوم PortSwigger بتعليق الحمولات باستمرار بواسطة حدث / علامة / سمة / متصفحمما يقلل بشكل كبير من "الذاكرة القبلية". هذا التنظيم هو الذهب عندما تحتاج إلى تغطية واسعة دون إعادة اختراع تصنيفات الحمولة.
التصفية وحدها ليست دفاعاً. لقد كررت OWASP هذا لأكثر من عقد من الزمان: تعتمد الصحة على سياق عرض البيانات. الجمع بين ترميز الإخراج المناسب, التعقيم (ل HTML من تأليف المستخدم), السياسة (CSP، الأنواع الموثوقة)، و نظافة الإطار غير قابل للتفاوض
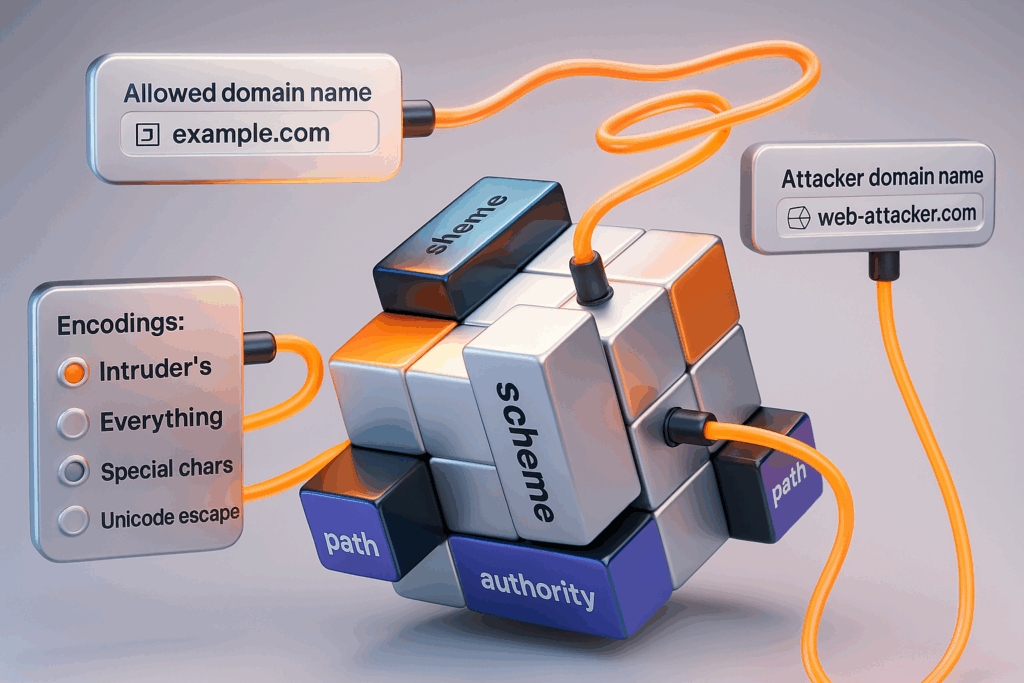
مصفوفة سطح الهجوم × مصفوفة السياق
استخدِم هذه المصفوفة كـ قائمة مراجعة التنفيذ عند برمجة عمليات التحقق من صحة Playwright/Burp/Nuclei أو عمليات التدقيق البرمجي. كل صف يربط بين كل عرض السياق إلى محفوفة بالمخاطر المغاسل، شائع الإدخالاتفإن الحركة الدفاعية الأولىو كيفية التحقق على نطاق واسع.
| السياق | أحواض محفوفة بالمخاطر (توضيحية) | نقاط الدخول النموذجية | الدفاع الأساسي | كيفية التحقق من الصحة على نطاق واسع |
|---|---|---|---|---|
| نص HTML | داخليHTML، تسلسل سلسلة القالب | البارامترات المنعكسة وخانات البحث وسير المستخدمين والتعليقات | ترميز إخراج HTML؛ لا تدفع أبدًا HTML غير موثوق به | تصيير بدون رأس + خطافات DOM-taint + خطافات DOM-taint؛ اختلاف DOM قبل/بعد |
| السمة | href/src/إجراءأي على* المعالج | جافا سكريبت: عناوين URL، وسمات SVG, البيانات: عناوين URL | ترميز السمة/عنوان URLحظر جافا سكريبت:; CSP | تشويش من حيث السمة؛ مراقبة المشغلات التلقائية والتنقل |
| جافا سكريبت | التقييم, الوظيفة, ضبط المهلة(سلسلة) | استدعاءات JSONP، تسلسل/تحليل نص ديناميكي للنصوص البرمجية | حظر التقييم الديناميكي؛ تسلسل المدخلات؛ وضع الحماية إذا لزم الأمر | الخطاف التقييم/الوظيفةجمع مكدسات الاستدعاء والوسائط |
| عنوان URL/الملاحة | الموقع, المستند.URL التسلسل | عمليات إعادة التوجيه المفتوحة، وحقن التجزئة/التجزئة المجزأة | التعميم؛ قوائم بدلات صارمة؛ عدم خياطة السلاسل الخام أبدًا | إعادة التشغيل الحقيقي - UA؛ تتبع سلسلة إعادة التوجيه |
| النمذجة/إس إس إس آر | الفلاتر/الأجزاء غير الآمنة | تقاطعات بيانات القالب من جانب الخادم | الهروب الصارم من القالب؛ القوائم البيضاء المتغيرة | اختبارات وحدة القالب + تشويش العناصر النائبة |
| محتوى غني | WYSIWYG/Markdown/SVG/MathML | لصق HTML/SVG خارجي؛ محتوى ملف تعريف المستخدم | تعقيم الوعاء (DOMPurify); CSPإسقاط العلامات الخطرة؛ إسقاط العلامات الخطرة | إعادة تشغيل الحمولة دفعة واحدة + تسجيل انتهاك CSP |
الحد الأدنى من الأمثلة القابلة للتكرار (MREs) التي يمكنك تشغيلها بالفعل
1) سياق السمة + مشغل التفاعل الصفري
<input autofocus onfocus="fetch('/beacon?xss=1')">
ما أهمية ذلك: أحداث التركيز التي يتم تشغيلها ذاتيًا عند التحميل في العديد من تدفقات تجربة المستخدم (حقول البحث، والمطالبات السريعة). استبدل بـ <svg onload=…> أو <img onerror="…"> لاختبار دلالات الزناد المختلفة.
2) حامل SVG + المراوغات في التعامل مع عناوين URL
<svg><a xlink:href="javascript:fetch('/beacon?svg')">x</a></svg>
ما أهمية ذلك: SVG هي مساحة اسم XML منفصلة مع تحليل سمات ملتوية تاريخيًا. غالبًا ما تنسى فرق العمل تعقيم SVG أو السماح به من خلال أدوات عرض Markdown.
3) XSS المستندة إلى DOM (المصدر → نسب الحوض)
<script>
const q = new URL(location).hash.slice(1);
document.getElementById('out').innerHTML = q; // sink
</script>
<div id="out"></div>
ما أهمية ذلك: النمط التقليدي "القراءة من عنوان URL، والكتابة إلى DOM" المضاد للنمط التقليدي. إنه موجود في كل مكان في المواقع القديمة والأدوات الداخلية. أصلحها باستخدام ترميز صحيح السياق وعدم الكتابة مباشرةً إلى أحواض HTML.
خط الأساس الدفاع (الهندسة أولاً، وليس الشعارات)
- ترميز الإخراج حسب السياق. ترميز ل HTML / سمة / عنوان URL / JS على التوالي. لا يغطي الإفلات التلقائي للإطار DOM ملفوفة يدوياً التحديثات.
- تعقيم الوعاء لـ HTML المستخدم. عندما يتطلب منطق العمل محتوى غنيًا (التعليقات، والسير الذاتية، وقواعد المعرفة)، استخدم DOMPurify (أو ما يعادله) بتكوينات محصنة؛ تجنب "تقطيع الكلمات" في القائمة السوداء.
- سياسة أمان المحتوى. ابدأ ب
البرنامج النصي المصدر 'ذاتي'+ كتلة مضمنة افتراضيًا؛ اضبطمصدر الكائن 'لا شيء'والقاعدة-وري 'لا شيء'. اعتماد الأنواع الموثوق بها في Chromium لفرض واجهات برمجة تطبيقات DOM الآمنة في وقت التجميع/وقت التشغيل. - تدقيق واجهة برمجة التطبيقات الخطرة. حظر أو بوابة
تقييم/وظيفة جديدة/إعداد المهلة(سلسلة)وتحويلات رمز JSON → الديناميكية. الفرض باستخدام قواعد ESLint أثناء الإنشاء وفشل CI عند ظهور انتهاكات. - اختبر وتحقق من ذلك كرمز. إعادة تشغيل الحمولة تلقائياً. الاقتران بـ الإبلاغ عن انتهاكات CSP و ارتباط البوابة/السجل لفصل "النوافذ المنبثقة القابلة للعرض التجريبي" عن قابل للاستغلال المسارات التي تهم العمل.
من ورقة غش إلى خط أنابيب: الأتمتة التي يتم شحنها
أقصر مسار من "مكتبة المتجهات" إلى "ضمان درجة الإنتاج" هو حلقة من خمس مراحل:
- اكتشاف السياق. عمليات المسح الثابتة (قواعد ESLint، وELSLint، وSimantic grep) + مسابر وقت التشغيل التي تحدد البالوعات المحتملة (
داخليHTMLومحددات السمات ونقاط التنقل). - جدولة المتجهات. قم بتعيين كل حوض/سياق إلى مجموعة منسقة من الحمولات (أحداث السمات، ومراوغات العلامات، ومعالجات عناوين URL)، والتصفية حسب المتصفح وعلامات الميزات.
- التدقيق بدون رأس تشغيل Playwright/Chromium لكل متجه. التقاط وحدة التحكم، الشبكة, انتهاكات CSPوطفرات DOM.
- ترابط الإشارات. انضم إلى النتائج مقطوعة الرأس مع بوابة واجهة برمجة التطبيقات و سجلات التطبيق لحصر "الضجيج مقابل الحقيقي". هذا يقتل الإيجابيات الخاطئة في اليوم الأول.
- إعداد التقارير القائمة على الأدلة أولاً. إرفاق لقطات شاشة وآثار HTTP و DOM قبل/بعد الاختلافات وانتهاكات السياسة تلقائيًا-ثم تسجيل الثقة حتى يعرف المهندسون من أين يبدأون
الحد الأدنى من إعادة تشغيل Playwright (مقتطفات منسدلة)
استورد { كروم } من { بلاي رايت
const vectors = [
'#\"><img src="x" onerror="fetch(\">',
'#<svg onload="fetch(\">'
];
(متزامن () => { {
const browser = await chromium.launch();
const page = await browser.newPage();
page.on('console', m => console.log('console:', m.text()));
page.on('pageerror', e => console.error('pageerror:',', e));
بالنسبة إلى (const v من المتجهات) {
انتظر page.goto('https://target.example/' + v);
انتظر page.screenshot({ path: 'evidence_${encodeURIComponent(v)}.png'});
}
انتظر المتصفح.close();
})();
إنتاجها: إضافة تسميات النسب المصدرية → النسب إلى كل عملية تشغيل، قم بتشغيل تقرير CSP فقط لجمع الانتهاكات، وتخزين فروق DOM لجعل الانحدارات واضحة في العلاقات العامة.
الحقائق الإطارية التي يجب أن تصمم من أجلها
- React/JSX. يساعدك الهروب التلقائي في الهروب التلقائي، ولكن بشكل خطيرSetSetInnerHTML وخام
ref.current.innerHTML = ...إعادة فتح الحوض. تعاملوا معها على أنها روائح كريهة؛ بوابة وراء مطهر وسياسة الأنواع الموثوقة. - الزاوي. المطهر لائق، ولكن BypassSecurityTrustHtml وما شابهها من واجهات برمجة التطبيقات المماثلة يمكن أن تحدث ثغرات؛ قم بتوثيق كل تجاوز وقصره على المصادر التي تم فحصها.
- التالي/التالي/التالي/التالي/التالي يجب أن يكون صدى الصفحات التي ينشئها الخادم صدى فقط مشفرة المحتوى. لا تعتمد أبدًا على أطر عمل العميل "لتنظيف" أخطاء الخادم.
- Markdown/MDX/WYSIWYG. تعامل معهم على أنهم استيعاب HTML المشاكل. قم بتقوية العارض الخاص بك، ووضع أدوات واجهة المستخدم غير الموثوق بها في وضع الحماية وإزالة سمات الحدث/معالجات عناوين URL.
- SVG/MathML. إذا كان لا بد من السماح بها، فقم بتغطية مجموعة الميزات وتشغيل معقم يفهم مساحات أسماء XML. إذا لم تكن حرجة، قم بالتحويل إلى النقطية الآمنة على الخادم.
عائلات الحمولة العملية التي ستحتاجها بالفعل
- المشغل التلقائي في الحدث:
ضبط تلقائي للصورة,التحميل,على خطأ,بدء التشغيل,أون فوكس,أون بوينترينتر. رائع لإثبات إمكانية الاستغلال دون نقرات المستخدم. - معالجات عناوين URL:
جافا سكريبت:,البيانات:وأحيانًاvbscript:(إرث). فرض القوائم المسموح بها. - تصادم القوالب: حيل التقسيم/التقسيم التي تتسلل من خلال المرشحات الساذجة (على سبيل المثال، الخروج من سياقات السمات ثم إعادة إدخال HTML).
- ضرب DOM الكتابة فوق المعرفات/الأسماء لإعادة توجيه مسارات التعليمات البرمجية والهبوط في الحوض.
- توقيت الطفرات والمراقب: المشغلات التي تستغل التحديثات الديناميكية بدلاً من التحميل الأولي.
CSP والأنواع الموثوق بها: من "لطيف أن يكون" إلى حاجز حماية
- CSP يمنحك لغة سياسة لتقييد مصادر البرامج النصية والتنفيذ المضمن. ابدأ بصرامة، ثم وسّعها فقط للحالات التي تم فحصها. اقترن بـ
تقرير-وري/تقرير إلىوالحصاد تقارير الانتهاكات في القياس عن بُعد - الأنواع الموثوق بها إجبار المطورين على تمرير السياسة الموضوعة في واجهات برمجة تطبيقات DOM التي تقبل السلاسل الأولية (
داخليHTML,outerHTML,إدراجAdjacentHTML,النطاق#createContextualFragment). هذا يزيل فئات كاملة من DOM XSS عن طريق البناء. - تلميح الطرح: تشغيل CSP في
تقرير فقطلسباقين؛ إصلاح الانتهاكات؛ ثم التنفيذ. تقديم سياسة الأنواع الموثوقة على مستوى التطبيق وإصدار HTML "مبارك" فقط عن طريق منشئين تم فحصهم.
كيفية إثبات قابلية الاستغلال للمهندسين
- نصوص النسخ: توفير سطر واحد (عنوان URL أو كيرل) وفرع Playwright لإعادة التشغيل.
- فرق DOM: إظهار العقدة التي تغيرت بالضبط والمسار (
#app > .Profile > .bio). - مكدسات المكالمات: بالنسبة لمصارف JS، قم بتضمين تتبعات المكدس من
التقييم/الوظيفةالخطافات. - أدلة CSP: إرفاق JSON الانتهاك JSON للاختراقات المضمنة/النصية src.
- سرد الأعمال: "يمكن لهذا أن يستخرج رموز جلسة العمل من
/الحسابعن طريق الحقن<img>منارة" تتفوق على "تنبيهات تنبيهية" في كل مرة.
تشغيل ورقة غش xss هذه داخل Penligent
إذا كنت تستخدم بالفعل بنليجنت كمنصة اختبار خماسي مؤتمتة، يمكنك تجميع ما سبق في قالب واحد قابل للتشغيل:
- قالب المهمة: "XSS Recon + التحقق من الصحة". يقوم الوكيل بإجراء الاستطلاع (نطاق فرعي/منفذ/بصمة إصبع)، وجدولة المتجهات حسب السياق المكتشف، وتنفيذ إعادة تشغيل بدون رأس، و يربط بين الإشارات مع جذوع الأشجار/البوابات لخفض الضوضاء.
- تصدير الأدلة أولاً. يتم شحن النتائج مع درجات الثقةوخطوات قابلة للتكرار، ولقطات شاشة، وسجلات انتهاكات CSP، وفرق DOM التي يمكن لمهندسيك الوثوق بها.
- حيث يساعدك أكثر. النطاقات الكبيرة ذات النطاقات الكبيرة التي تحتوي على حزم مختلطة من الأنظمة القديمة + SPA، أو الفرق التي تنتقل إلى نظام دعم البرامج/أنواع موثوق بها وتحتاج إلى الفرز القائم على الإثبات بدلاً من الحمولة التافهة.
المزالق الشائعة التي لا تزال تلاحق الفرق المتمرسة
- تعقيم المدخلات وليس المخرجات. إذا كان يجب عليك قبول HTML، فقم بتعقيم و لا يزال التشفير على الإخراج بناءً على سياق الوجهة؛ فالاثنان غير قابلين للتبادل.
- السماح بـ
جافا سكريبت:من أجل "المرونة". أوقفه بالكامل، وقم بإدراج بروتوكولات محددة فقط في القائمة البيضاء (https,البريد الإلكترونيربماالهاتف). - التعامل مع تخفيض السعر على أنه "نص آمن". إنه عارض-مكوناته الإضافية تقرر السلامة. التدقيق في العلامات/السمات المسموح بها؛ ضع في اعتبارك التنقيط من جانب الخادم لـ SVG غير الموثوق به.
- تجاهل السياقات غير HTML. يعد تسلسل عناوين URL و JSON → JS Evals من المخالفين المتكررين. تعزيز سياسة "عدم التسلسل في التعليمات البرمجية".
- الثقة في بيئة واحدة. قد تنجح XSS التي تفشل في الإصدارات مقطوعة الرأس على Chromium المحمول أو إصدارات سطح المكتب القديمة. احتفظ ب مصفوفة المتصفح للتطبيقات عالية القيمة.
قائمة مراجعة الإنتاج، قم بتثبيتها بجانب شارة CI الخاصة بك
- الوعي بالسياق الترميز الأدوات المساعدة مع اختبارات الوحدة ل HTML/Attr/URL/URL/JS
- DOMPurify (أو ما يعادله) مقفل على تهيئة محصنة لمسارات المحتوى الغني
- CSP مع
البرنامج النصي المصدر 'ذاتي'(لا يوجد خط غير آمن في السطر),مصدر الكائن 'لا شيء',القاعدة-وري 'لا شيء'جمع الانتهاكات الموصولة بالقياس عن بُعد - الأنواع الموثوق بها سياسة + قواعد الوبر في وقت الإنشاء لحظر مصارف السلسلة الخام
- حظر قواعد ESLint
تقييم/وظيفة جديدة/إعداد المهلة(سلسلة)(CI-enforced) - كاتب مسرحي مجموعة الإعادة مصنّفة مع ناقلات على غرار PortSwigger؛ لقطات شاشة لكل ناقل + اختلافات DOM
- مؤتمتة ارتباط الإشارة مع سجلات التطبيق / أحداث بوابة واجهة برمجة التطبيقات
- التقارير التي تستند إلى الأدلة أولاً مع درجات الثقة وملاحظات تأثير الأعمال
- سطور قالب العلاقات العامة: "يقدم أحواض HTML جديدة؟" "تجاوز المطهر؟" "تحديث سياسة TT؟"
- المراجعة المنتظمة لإعدادات أدوات الطرف الثالث/WYSIWYG/Markdown
الأسئلة الشائعة
س: إذا كنا نستخدم React/Angular بالفعل، هل ما زلنا بحاجة إلى هذا؟
ج: نعم. لا تراقب الأطر جميع كتابات DOM أو أدوات الطرف الثالث أو Markdown/SVG. ما زلت بحاجة إلى معقِّم + CSP + TT، ويجب عليك تجنب كتابة بيانات غير موثوق بها في مصارف DOM الخام.
سؤال: هل يجب أن نحظر جميع البرامج النصية المضمنة مع CSP؟
ج: نعم، بشكل افتراضي. استخدم nonces أو التجزئة فقط عند الضرورة القصوى ووثق الاستثناء. الهدف على المدى الطويل هو تجنب البرامج النصية المضمنة تمامًا.
س: هل التعقيم كافٍ؟
ج: لا. يقلل التعقيم من سطح الهجوم على استيعاب HTMLولكنك لا تزال بحاجة إلى تصحيح ترميز الإخراج وحواجز حماية السياسات. مشاكل مختلفة، وأدوات مختلفة.
سؤال: ما هي المتصفحات التي نختبرها؟
ج: كحد أدنى، أهم محركين لقاعدة المستخدمين لديك على سطح المكتب + الهاتف المحمول. احتفظ بمصفوفة صغيرة، فبعض المتجهات خاصة بالمتصفح أو ذات خصائص محددة.
مزيد من القراءة (موثوق)
- PortSwigger - ورقة الغش في البرمجة النصية عبر المواقع (XSS) - كتالوج حي للناقلات، ونقاط البيع، وملاحظات المتصفح.
- OWASP - ورقة غش للوقاية من XSS - استراتيجيات ترميز صارمة ومحددة السياق وجداول افعل/لا تفعل.
- OWASP - ورقة غش في منع XSS المستندة إلى DOM - المصدر → أنماط البالوعة والتخفيف في المتصفح.
- PortSwigger - ما هو XSS؟ - برنامج تعليمي منظم ومختبرات عملية لتدريب الموظفين الجدد.
الملحق: مرجع سريع للتعقيم والترميز
- عقد نص HTML النصية → الهروب
& " ' / - قيم السمات → ترميز سمة HTML-تشفير سمة HTML + عدم السماح بخصائص الحدث من البيانات غير الموثوق بها
- عناوين URL → ترميز المكوناتبروتوكولات القائمة المسموح بها؛ لا تكتب خامًا أبدًا
جافا سكريبت:/البيانات: - سلاسل JS → التسلسل بأمان؛ لا تمرر أبدًا بيانات المستخدم إلى واجهات برمجة التطبيقات التي تفسر التعليمات البرمجية
ملاحظة ختامية: مفيدة ورقة غش xss هو واحد يمكنك سلك في خط الأنابيب الخاص بكابدأ باكتشاف السياق، وجدولة المتجهات حسب السياق، وإعادة التشغيل بدون رأس، والربط مع السجلات، وشحن الأدلة مع درجات الثقة. سواء كنت تتبنى Penligent أو تقوم بتشغيل الحزام الخاص بك، قم بقيادة العملية باستخدام الأدلة والسماح للسياسة بفرض حواجز الحماية.


