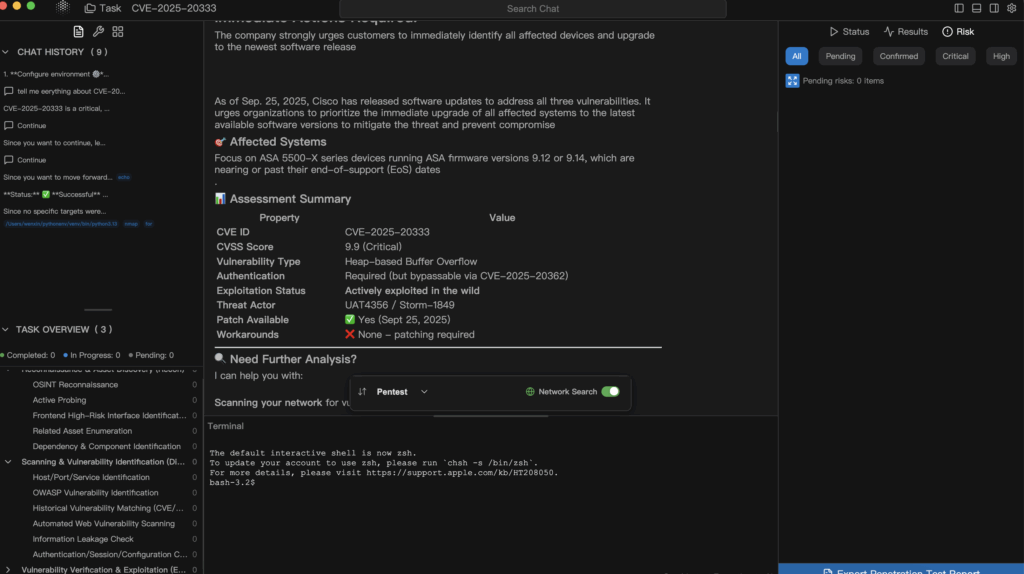
لم يبدأ الأمر بعنوان رئيسي؛ بل بدأ بسطري سجل غير ملحوظ وإعادة تحميل غير متوقعة. شاهدنا أثناء الاتصال بعض طلبات HTTPS كبيرة الحجم تصل إلى بوابة WebVPN، ثم عاد الصندوق للعمل دون سابق إنذار. لم يقل أحد "0 يوم". قمنا بسحب الأدلة: لقطات الحزم، وبصمات الخدمة، وسلاسل الإصدارات، وجرد التعرض. في غضون دقائق أشار اللغز إلى استشارة Cisco: CVE-2025-2025-20333 على خادم الويب الخاص بالشبكة الافتراضية الخاصة (بوابة WebVPN/AnyConnect) في جدار حماية Cisco Secure Firewall ASA/FTDA. يصف ما كتبه البائع تنفيذ التعليمات البرمجية عن بُعد يمكن تحقيقه بواسطة مهاجم عن بعد ببيانات اعتماد VPN صالحة عبر طلبات HTTPS المصممة خصيصًا، وتذكر التحديثات التالية متغير الهجوم الجديد وتقارير عمليات إعادة التحميل/التشويش غير المتوقعة. في الواجهة التي تعرضها العديد من المؤسسات عن قصد للوصول عن بُعد، تُترجم هذه الكلمات إلى توجيه بسيط: تصرف الآن. تعامل مع استشارة Ciscoفإن سجل NVDو Cisco's استمرار الهجمات كمرتكزاتك الأساسية؛ فهي المصادر التي تستشهد بها للإدارة وتلك التي يجب أن تدور حولها تذاكر التغيير.
نادرًا ما يكون الجزء الصعب هو "ما مدى رعب هذا الأمر بشكل مجرد". الجزء الصعب هو اختصار ساعة من متوسط الوقت اللازم لاحتواء المشكلة دون إشعال النار في أي شيء. في الممارسة العملية تلك الساعة هي التي تفوز فيها: تقلص التعرض، وتجمع الأدلة المقبولة، وترتب الرقع، وتتحقق من الانحدارات، وتبقي الأضواء مضاءة. ما تبقى من هذه القطعة يسير معك على هذا الخط.
لماذا هذه ليست حالة "تصحيح في عطلة نهاية الأسبوع"
إن بوابة SSL WebVPN/AnyConnect ذات طبقة المقابس الآمنة مكشوف عمدًا في العديد من الشبكات؛ فهو باب للعمل عن بُعد، والبائعين، والمتعاقدين المؤقتين. CVE-2025-2025-20333 يجلس مباشرة على هذا السطح، ويجمع بين إمكانية وصول عالية مع سياق عالي القيمة. يشير تحديث Cisco اللاحق إلى متغير جديد و عمليات إعادة التحميل غير المتوقعة، مما يعني أن البوابة غير المصححة ليست مجرد موطئ قدم - بل هي أيضًا انقطاع قابل للتشغيل عن بُعد في انتظار أسوأ ساعة عمل ممكنة. لا ينبغي أن يتوقف تحديد الأولويات على ما إذا كانت السلسلة المسلحة بالكامل عامة، بل يجب أن يتوقف على ما إذا كانت بوابتك مكشوفة ومدى خطورة هذا الانكشاف. نعم، أنت بحاجة إلى تصحيحات. قبل التصحيحات، تحتاج إلى سحب التعرض للخلف و التقط شكل الصندوق الآن.
ما الذي يتأثر وكيفية إغلاق الحلقة بشكل حقيقي
دعك من غرفة صدى المدونة وامنح نفسك ورقة واحدة تجيب على الأسئلة الوحيدة التي تهم طرحك.
| السؤال الذي تريد الإجابة عليه بالفعل | استنتاج عملي |
|---|---|
| أين الخلل بالضبط؟ | إن بوابة WebVPN / AnyConnect في ASA/FTDA التي تعالج طلبات HTTP(S) أثناء الجلسة. هذا هو سطح الوصول عن بُعد المنشور. تحقق من ذلك في مقابل إرشادات Cisco وسجل NVD. |
| الشروط المسبقة مقابل الشائعات | تنص شركة Cisco على ما يلي مصادق عليه الاستغلال؛ يناقش الباحثون التسلسل مع CVE-2025-2025-20362 لتخفيف الشروط المسبقة في إعدادات معينة. استخدام السلاسل لنمذجة التهديدات، وليس لاستبدال الثابت الأول المصفوفة. |
| لماذا تقارير إعادة التحميل/التعطيل؟ | تستدعي تحديثات Cisco متغير جديد الإشارات والتقارير الميدانية عن عمليات إعادة التحميل غير الطبيعية. وهذا بالضبط هو السبب في أن تقليل التعرض يوفر لك الوقت - فالمتغيرات لا تهتم بنافذة الصيانة. |
| هل تستحق عمليات التخفيف من المخاطر؟ | نعم، كمكابح. يؤدي تعطيل WebVPN بدون عميل ومراجعة خدمات عميل IKEv2 إلى تقليل نصف قطر الانفجار أثناء إعداد التصحيحات. عمليات التخفيف ليست إصلاحات. |
| كيف نثبت الإصلاح؟ | استخدم مدقق برامج سيسكو للتعرف على قطارك الثابت الأول الإصدارات. تعامل مع البصمات قبل/بعد البصمات وسلاسل الإصدارات على أنها قطع أثرية للتدقيق، وليس حواشي. |
ما فعلناه بالفعل في تلك الساعة الأولى
لقد قمنا بتقسيم الاستجابة إلى ثلاث حركات تهدف إلى التداول بأقل وقت مقابل أكبر قدر من المخاطر.
تقييد التعرض. ضمن نافذة التغيير وبموافقة العمل، قللنا أو عطلنا مؤقتًا نقاط دخول WebVPN وسيرنا خدمات عميل IKEv2 عبر الواجهات. الأمر ليس مثيرًا، لكن الأسطر القليلة التي تضيفها إلى تذكرة التغيير هي الفرق بين "لقد حالفنا الحظ" و "جعلنا أنفسنا أقل استهدافًا".
تكوين المحطة الطرفية
لا webvpn ! قم بتعطيل WebVPN بدون عميل في الوقت الحالي (اتبع إرشادات Cisco لقطارك)
تم تمكين crypto ikev2 خارجي ! مراجعة/تعديل التعرض والسياسة لكل واجهة
الخروج
كتابة الذاكرة
تصوير الحاضر. لا تنتظر حتى يتم التصحيح قبل أن توثق خط الأساس. اسحب اللافتات والعناوين وأول 30 سطرًا من صفحة البوابة بحيث يكون لديك مجموعة "قبل" مع الطوابع الزمنية. بعد التصحيح، اسحب نفس القطع الأثرية مرة أخرى؛ تميل الحجج إلى الموت في مواجهة الحقائق المختلفة.
# تحديد المنافذ وإصدارات الخدمة
nmap -sV -p 443,8443,9443,9443
# جلب مسارات بوابة يمكن التعرف عليها (تختلف المسارات؛ هذه توضيحية)
curl -k -k -I https:// </+webvpn+/index.html
curl -k -k https:// <>/+webvpn+/index.html | head -n 30
جعل الترقيع قابلاً للتدقيق. حملت تذكرتنا أربع مجموعات من الإثباتات: البصمات قبل/بعد، وسلاسل الإصدارات الدقيقة وأسماء الصور، ونافذة التغيير والموافقات، وبيان تأثير الأعمال الموقّع. عندما يهبط المتغير التالي، ستحتاج إلى هذا الإثبات أكثر مما تريد منشور مدونة آخر.
كيفية التفكير في مسارات الهجوم وكيفية التحقق من صحتها في المختبر
في المختبر، ابدأ بـ حساب اختبار صالح وجلسة WebVPN حقيقية حتى تعيش في السياق الصحيح. من هناك، قم بقيادة المدخلات المصممة في نقاط نهاية البوابة وراقب عمليات إعادة التحميل غير الطبيعية، أو أخطاء في الامتيازات، أو ارتباك في جهاز الدولة. نظرًا لاختلاف الأجهزة والقطارات الحقيقية، فإن قولك "يبدو أنه يعمل" يحتاج إلى التوفيق بين مصفوفة الإصدار الثابت من Cisco؛ الادعاءات القوية الوحيدة هي تلك التي يمكنك ربطها بصورة ثابتة.
بالنسبة للأدوات، ثلاثي نصوص HTTP، وPCAP، وسجلات وحدة التحكم يحكي القصة بوضوح. المقتطف أدناه ليس استغلالاً؛ إنه هيكل عظمي يوضح الطلبات المرتبطة بالجلسة. ستصمم نقاط النهاية والمعلمات حسب الهدف المصرح به.
طلبات الاستيراد
القاعدة = "https://"
s = طلبات.Session()
s.check = False # مختبر # فقط؛
# افترض أنك قمت بالمصادقة والتقاط ملف تعريف ارتباط الجلسة
s.cookies.set("webvpnCookie", "")
الحمولة = {"kw": "A" * 8192، "redir": "/+CSCOE+/portal.html"} # حقول توضيحية فقط
r = s.post(s.post(f"{base}/+webvpn+/index.html"، البيانات=payload، المهلة=10)
طباعة (r.status_code, r.headers.get("X-Device-Id"))
طباعة(r.text[:2000])
إذا كنت ترغب في استكشاف التسلسل محاكاة واقعية CVE-2025-2025-20362 أولاً للحصول على موطئ قدم غير متوقع ثم حاول 20333. ولكن أبقِ علاجك مستندًا إلى الثابت الأول الصور؛ تعمل السلاسل القائمة على البحث على توسيع نموذجك، ولا تحل محل خط الأساس للبائع.
تحويل حادثة واحدة إلى عضلة قابلة للتكرار
كل حادثة هي فرصة لجعل الحادثة التالية مملة. لقد قمنا بتوصيل الاكتشاف ← المحفز ← الدافع ← الدليل ← الانحدار ← التقرير في مسار واحد. أثناء عمليات المسح المحيطية نقوم بتمييز نقاط نهاية WebVPN المرشحة؛ وأثناء التحقق من الصحة نرسل مدخلات متعددة الترميز و إعادة تشغيل الآلات الآلية الحكومية؛ عندما تظهر الحالات الشاذة نجمع تلقائيًا نصوص HTTP، و PCAPs، وأحداث التعطل/إعادة التحميل، وسجلات وحدة التحكم؛ بعد التصحيح نقوم بتشغيل انحدار أ/ب. والنتيجة ليست بطولات؛ إنها حلقة هادئة يمكن الاعتماد عليها في كل مرة يقول لك أحدهم "هل هذا البديل جديد؟
إذا كنت تستخدم Penligent، فاحرص على إبقاء الإنسان في الحلقة والأدلة أولاً
لا يطلب منك Penligent التخلي عن سلسلة أدواتك. إنه ببساطة يلصق الأتمتة القائمة على الأدلة أولاً بالطريقة التي تعمل بها بالفعل. يقوم الوكلاء بتعداد المعلمات وتغييرها داخل الجلسات المصادق عليها؛ ويقوم المهندسون بالفصل في السلوك المشبوه في الوقت الفعلي؛ وتصبح المسارات الناجحة على مستوى المؤسسة اختبارات الانحدار التي يتم تشغيلها تلقائيًا في المرة التالية التي تقوم فيها بترقية ASA/التحديثات المحدودة. وعندما تحتاج إلى إقناع لوحة التغيير، فإنك تقوم بالارتباط بـ استشارة Ciscoفإن سجل NVDو استمرار الهجمات الصفحة - نفس المصادر التي يجب أن تستشهد بها اليوم.
الروابط الموثوقة
- إرشادات سيسكو الأمنية - cisco-sa-ASA-ASAFTD-webvpn-z5xP8EUB: https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-asaftd-webvpn-z5xP8EUB
- NVD - CVE-2025-2025-20333: https://nvd.nist.gov/vuln/detail/CVE-2025-20333
- سيسكو - الهجمات المستمرة ضد جدران حماية سيسكو: https://sec.cloudapps.cisco.com/security/center/resources/continued-attacks-cisco-firewalls
كيفية استغلال CVE


