In the current landscape of cloud-native security, “alert fatigue” is no longer just a buzzword; it is the primary operational bottleneck for sophisticated security engineering teams. Traditional Cloud Security Posture Management (CSPM) tools act like hypersensitive car alarms—generating thousands of “Critical” alerts daily based on static configurations, yet failing to indicate which specific alert represents an active, traversable breach path.
This is the precise operational context for the ascent of Upwind Security. As one of the most closely watched cloud security platforms going into 2026 (following significant Series B funding), Upwind is not merely another acronym in the crowded CNAPP market. It represents a fundamental paradigm shift from “static API scanning” to “runtime context and execution truth.”
This article strips away marketing hyperbole to provide a rigorous technical dissection of Upwind Security for hardcore AI and cloud security engineers. We will analyze its eBPF-driven architecture, its application against sophisticated modern threats, and how to construct a closed-loop defense by weaponizing it alongside active AI penetration testing platforms like بنليجنت.
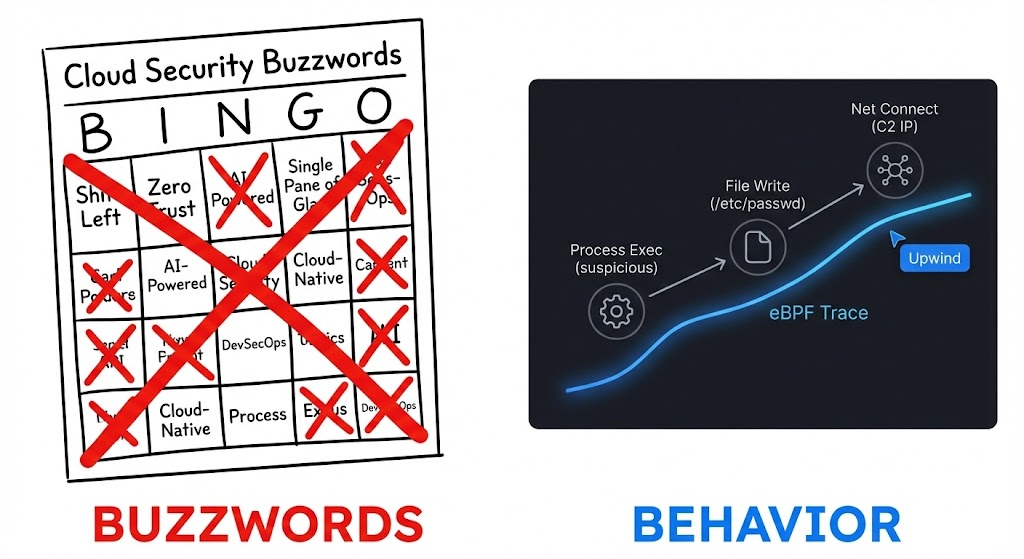
The Twilight of Static Scanning and the Reality Gap
The legacy security model—underpinning first-generation CSPMs and early agentless solutions—relies heavily on cloud API snapshots و disk side-scanning. These tools interrogate cloud provider APIs (e.g., AWS DescribeInstances) or mount snapshots of running workloads to scan filesystems for vulnerabilities.
While fast to deploy and excellent for high-level compliance governance, this approach suffers from a fatal logical flaw in high-threat environments: “Presence” does not equal “Exploitability.”
A container image containing a Java library with a critical Log4j vulnerability is terrifying on paper. However, if that library is never loaded into memory by the running process, or if the container’s effective Network Policy completely isolates it from ingress and egress traffic, its actual runtime risk approaches zero. Yet, in a static CSPM report, it remains a screaming red “Critical.” This reality gap is where security engineering hours go to die.
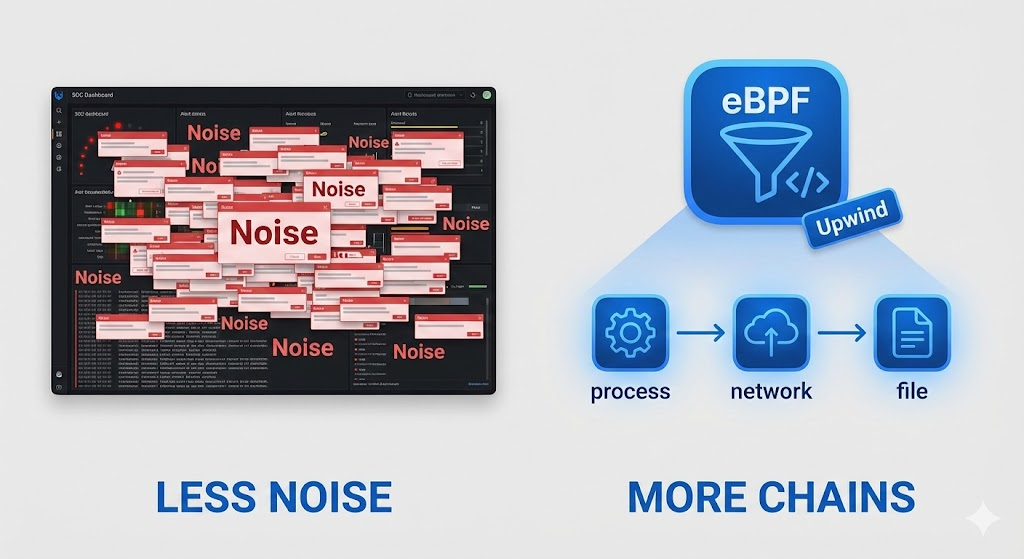
The Upwind Differentiator: The eBPF Lens
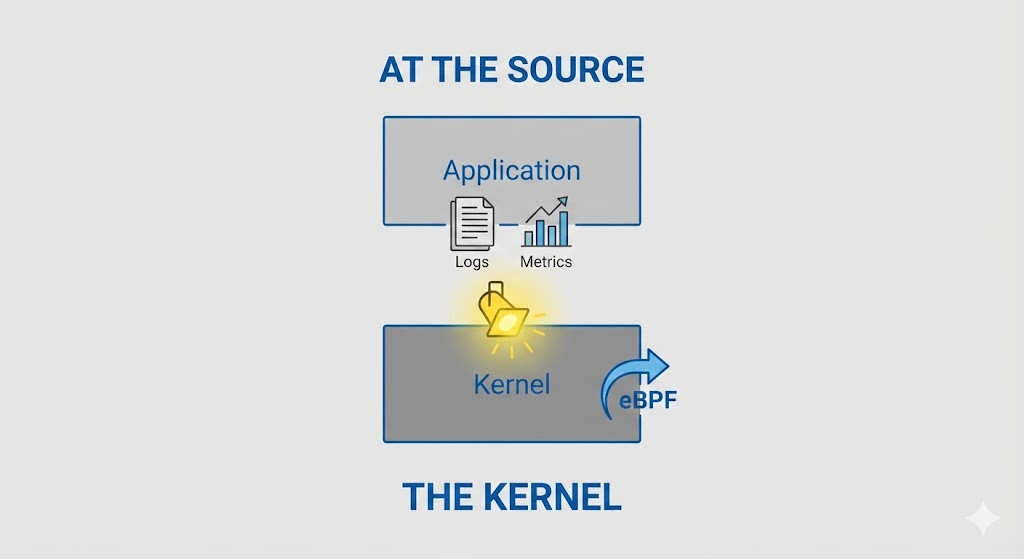
Upwind Security’s core architectural bet is placed firmly on eBPF (Extended Berkeley Packet Filter). eBPF is a revolutionary Linux kernel technology that allows engineers to run sandboxed, high-performance programs within the kernel space without modifying kernel source code or loading fragile kernel modules.
By leveraging eBPF, Upwind achieves “God-mode” observability into Kubernetes and host environments that user-space agents cannot match:
- Syscall Interception at Source: It does not rely on parsing logs. It hooks directly into kernel tracepoints to see every
execve,connect,accept4أوopenatcall as it happens. - L7 Network Transparency: Even within encrypted Service Meshes (like Istio mTLS), eBPF can attach to kernel socket functions (e.g.,
tcp_sendmsg) to reconstruct HTTP/gRPC payloads before encryption or after decryption, providing true application-layer visibility without bulky sidecars. - Memory-Level Executive Context: It can determine not just if a vulnerable package resides on disk, but if its shared object file (
.so) has been mapped into the active memory segment of a running process.
This capability transitions security teams from a state of “Guessing Risk” based on static configurations to “Knowing Risk” based on execution reality. Upwind’s claims of massive noise reduction are rooted in the mathematical certainty of runtime reachability analysis.
Technical Deep Dive: Anatomy of the Upwind eBPF Engine
For engineering teams, trust is built on understanding the mechanism of action. Upwind’s lightweight sensors are typically deployed as a Kubernetes DaemonSet, gaining the necessary privileges to hook into the host kernel’s kprobes and tracepoints to harvest telemetry.
The Kernel Logic Perspective
To visualize the difference, consider monitoring for a suspicious shell execution—a standard precursor to many container breakout scenarios. A traditional HIDS might rely on complex, brittle regex rules parsing audit logs. An eBPF-based approach operates at the metal.
The following is a simplified C-style pseudo-code representation of how an eBPF probe functions at the kernel level to detect execution events:
C
`/*
- Simplified Pseudo-code illustrating eBPF hook concept
- Not actual Upwind source code. */
// Hook into the kernel tracepoint for the execve system call entrance SEC(“tracepoint/syscalls/sys_enter_execve”) int trace_execve_entry(struct trace_event_raw_sys_enter *ctx) { u64 id = bpf_get_current_pid_tgid(); u32 pid = id >> 32; // Extract Process ID
// 1. Gather low-level execution context
char comm[TASK_COMM_LEN];
bpf_get_current_comm(&comm, sizeof(comm)); // e.g., "nginx", "java"
// Read the filename argument being executed from user space memory
char filename[MAX_FILENAME_LEN];
bpf_probe_read_user_str(filename, sizeof(filename), (const char *)ctx->args[0]);
/*
* The Upwind "Magic": Correlation Layer
* The raw BPF data is enriched instantly with Kubernetes metadata maps.
*/
struct k8s_metadata *meta = bpf_map_lookup_elem(&pod_map, &pid);
if (!meta) return 0;
/*
* Runtime Policy Evaluation logic
* If a frontend web pod suddenly tries to spawn /bin/bash, flag it.
*/
if (meta->is_public_facing && is_shell_binary(filename)) {
// Send high-fidelity event to userspace agent for alerting/blocking
send_security_event(pid, meta->pod_uid, filename, EVENT_TYPE_SHELL_SPAWN);
}
return 0;
}`
The immense power of Upwind’s implementation is not just running the BPF hook—anyone can run Falco. The proprietary value lies in the immediate, low-overhead correlation of that raw kernel pid with rich Kubernetes metadata (Pod Name, Namespace, Service Account, Labels) in real-time, creating an actionable security event rather than a raw kernel log.
The Dynamic Runtime Topology
Unlike static architecture diagrams derived from Terraform files, Upwind generates a dynamic topology based on proven TCP/UDP flows.
- The Static View (e.g., Wiz): Reports, “This S3 bucket is configured as public and is mounted by an EC2 instance with admin role.”
- The Upwind Runtime View: Reports, “This S3 bucket is configured as public, BUT in the last 30 days, the only actual read/write operations came from the internal IP
10.0.5.20via thebackend-serviceServiceAccount. Zero external IPs have accessed it.”
This distinction is critical. It determines whether an engineer gets paged at 3 AM for an immediate remediation or whether a Jira ticket is created for Monday morning architectural cleanup.
Combat Scenario: Defending Container Escape CVEs
To validate the necessity of runtime protection, we must examine threats that bypass static analysis. Modern container escapes often rely on race conditions or specific runtime configurations that static scanners cannot see.
Consider a sophisticated vulnerability scenario similar to high-impact runc escapes (like CVE-2019-5736 or more recent analogs). These exploits often involve attackers tricking the container runtime into overwriting host runc binaries or leveraging improper mount configurations to access the host filesystem.
The Static Blind Spot
A traditional image scanner looking at a registry only sees package versions. If an attacker manages to deploy a malicious Pod manifest (kubectl apply -f evil.yaml) that utilizes dangerous hostPath mounts, or exploits a kernel vulnerability to elevate privileges after the container starts, the static scanner is completely blind to the active attack.
The Upwind Runtime Interdiction
In the Upwind console (or leveraged via its advanced AI analysis interface), the kill chain of such an attack is visible and interruptible:
- Exploit Sequence Detection: The eBPF sensors capture a sequence of anomalous syscalls—perhaps an unusual
openaton/proc/self/exefollowed by an attempt to write to a file descriptor associated with the host’s container runtime binary. - Contextual Anomaly Correlation: The system identifies that the process initiating these privileged calls belongs to a standard
node-js-backendPod. According to the learned behavioral baseline for this workload, it has absolutely no business performing these actions or requiringCAP_SYS_ADMIN. - Automated Response (Kill Switch): Based on defined blocking policies, Upwind can move beyond alerting. It can instruct the kernel to immediately send a
SIGKILLto the offending process chain or interface with the Kubernetes API to cordon the node and terminate the Pod, stopping the escape before it achieves host persistence.
Table: The Efficacy Gap – Traditional vs. Runtime Security
| Feature Vector | Traditional CSPM / Static Agentless | Upwind Security (eBPF Runtime) |
|---|---|---|
| Primary Data Source | Cloud APIs, Disk Snapshots, Manifest files | Kernel Tracepoints, Syscalls, L7 Socket Data, Memory maps |
| Detection Latency | Pre-deployment or Periodic periodic scans (often 12-24h cycles) | Real-time (Nanosecond/Microsecond resolution via kernel) |
| Complex Exploits (e.g., Kernel Race Conditions) | Invisible (Cannot model runtime race states) | Detects & Blocks based on anomalous execution behavior |
| المعدل الإيجابي الكاذب | High (Cannot confirm actual usage/reachability) | Very Low (Alerts based on executed code and actual flows) |
| Performance Overhead | Low on workload (API heavy) | Negligible on host (eBPF is JIT compiled, typically <1% CPU) |
The CNAPP Landscape: Nuanced Positioning
For security architects, choosing the right tooling stack is critical. Upwind does not exist in a vacuum, and its relationship with incumbents like Wiz and Orca is nuanced.
- Wiz: Remains the undisputed king of broad visibility and graph-based querying. Its agentless graph is incredibly fast at answering inventory questions like “Show me all internet-facing VMs with critical vulnerabilities and high-privilege IAM roles.” It is the gold standard for asset inventory and compliance posture.
- Upwind Security: The defining characteristic is “deep execution context.” Upwind posits that true security requires proximity to where the code executes. While it requires deploying sensors (friction compared to pure API solutions), it trades that friction for forensic-level depth that static tools cannot provide.
The Verdict for Engineers: If your primary mandate is compliance governance and high-level asset inventory across multi-cloud, Wiz is essential. However, if you are a hardcore security engineering team tasked with detecting and stopping sophisticated 0-days, webshell implants, memory-resident malware, and advanced lateral movement in highly dynamic Kubernetes environments, Upwind is a mandatory runtime layer that fills the critical gaps left by static analysis.
Validation via Offense: Integrating Penligent.ai
A defense is only as good as its ability to withstand a real attack. Having deployed Upwind and configured eBPF-based blocking rules, the critical engineering question remains: How do we empirically validate its effectiveness without waiting for a real breach?
Relying solely on built-in “reachability analysis” tools is insufficient. They may validate network port openness, but they cannot model complex business logic vulnerabilities or multi-stage AI agent attack chains. This is the precise scenario for integrating offensive AI platforms like Penligent.ai.
The Penligent & Upwind Closed-Loop Architecture
بنليجنت is an advanced, AI-driven automated penetration testing platform designed to simulate the reasoning path and adaptability of a human attacker. By coupling Penligent’s offensive capabilities with Upwind’s defensive telemetry, organizations can build a rigorous, closed-loop DevSecOps validation environment:
Automated adversarial Emulation:
- Red Team (Penligent): Operators launch an AI Agent tasked with exploiting a service protected by Upwind. The agent might attempt a sophisticated SQL Injection, explore an IDOR (Insecure Direct Object Reference) vulnerability, or attempt to leverage a known CVE. Penligent’s AI does not just replay static payloads; it analyzes responses (WAF blocks, error messages) and adapts its attack strategy dynamically to bypass perimeter defenses.
- Blue Team (Upwind): At the runtime layer, Upwind’s eBPF probes should be the ultimate source of truth. They should detect the anomalous database query structures (resulting from a successful SQLi bypass of the WAF) or suspicious file read attempts (LFI) triggered by Penligent’s deep probing.
Proving the “Unreachable” False Negative:
- A common issue with static tools is false positives. Upwind helps reduce this by marking vulnerabilities as “Unreachable.” But can you trust that verdict 100%?
- Security engineers can task بنليجنت to specifically target a service Upwind deems unreachable. If Penligent’s AI agent successfully finds a pathway to exploit that vulnerability, it provides irrefutable evidence of a False Negative in the reachability model (perhaps due to a misconfigured micro-segmentation policy), allowing the team to close a critical gap that looked safe on a dashboard.
Integrating active AI-driven penetration testing (Penligent) with deep kernel-level runtime visibility (Upwind) moves an organization from “hope-based security” to “evidence-based security.”
Conclusion: The Shift to Truth-Based Security
Cloud security has matured beyond checking compliance boxes. In an era where attacks are increasingly automated and sophisticated, defensive teams must operate with higher fidelity data than their adversaries.
Upwind Security represents the necessary evolution of cloud defense: moving from static probabilistic models to runtime deterministic facts. By utilizing eBPF to pierce the abstraction layers of modern containerized environments, it reveals process-level truth. However, even this truth must be constantly challenged. By employing offensive AI tools like بنليجنت to relentlessly test these defenses, security engineers can ensure their runtime protection is not just a theoretical construct, but a battle-hardened reality.
Internal & Authoritative References
For further technical exploration, please refer to these primary sources and related analysis:
- eBPF Foundation: What is eBPF? A Technical Introduction – The definitive guide to the kernel technology powering Upwind.
- Kubernetes Documentation: Linux Kernel Security Capabilities – Understanding the baseline restrictions eBPF monitors against.
- Upwind Engineering: Technical Blog on eBPF Implementation – (Reference for architectural concepts utilized).
- Penligent AI: The Necessity of Automated AI Red Teaming in Cloud Native – Exploring the offensive validation methodology.
- CVE Mitre: Container Runtime Vulnerability Records – Database of historical escape techniques mentioned in combat scenarios.


