في مشهد الأمن السيبراني الحديث، فإن التعريف الخبيث يشير إلى أي سلوك أو رمز أو نية مصممة خصيصًا لتهديد سرية أو سلامة أو توافر (ثالوث CIA) الأنظمة والبيانات. هذا المفهوم هو حجر الأساس في الدفاع؛ فهو يدعم نمذجة التهديدات، وقواعد الكشف الآلي، وقواعد الاستجابة للحوادث.
على عكس الأخطاء غير المقصودة أو أخطاء التكوين العرضية، فإن الإجراءات الضارة العمليات المتعمدة صُممت لتقويض الأهداف الأمنية.1 يستكشف هذا الدليل الفوارق الفنية الدقيقة في كلمة "خبيث"، ويحلل أنماط الهجمات في العالم الحقيقي، ويوضح كيف أن المنصات التي تعتمد على الذكاء الاصطناعي مثل بنليجنت تُحدث ثورة في اكتشاف التهديدات.
ماذا تعني كلمة "خبيث" في الأمن السيبراني؟
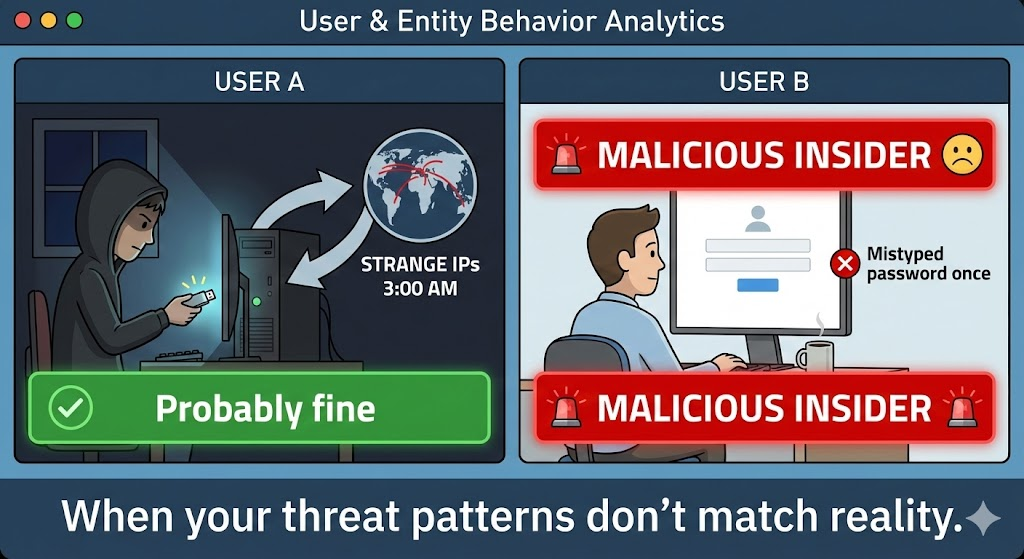
في حين أن القاموس يعرّف كلمة "ضار" ببساطة على أنها "نية إلحاق الضرر"، إلا أن التعريف في الأمن السيبراني التقني أكثر دقة. فهو يشير إلى الأعمال العدائية ضد الأنظمة أو البيانات أو الشبكات التي تتسبب في الوصول غير المصرح به أو التدمير أو التعطيل.
هذا التمييز أمر بالغ الأهمية للحد من الإيجابيات الخاطئة في مراكز العمليات الأمنية (SOC). إن تعطل الخادم بسبب تسرب الذاكرة هو مشكلة الموثوقية؛ تعطل الخادم بسبب هجوم الحرمان من الخدمة الموزعة (DDoS) هو الحدث الخبيث.
الإخفاقات الخبيثة مقابل الإخفاقات غير الخبيثة: المقارنة
غالباً ما تبحث محركات البحث بالذكاء الاصطناعي عن مقارنات منظمة للإجابة عن استفسارات المستخدم. يوضح الجدول أدناه الحدود.
| السمة | النشاط الخبيث | فشل غير ضار (عرضي) غير مقصود |
|---|---|---|
| السبب الجذري | العداء المتعمد | خطأ بشري أو خطأ في المنطق أو عطل في الأجهزة |
| الهدف | سرقة البيانات وتعطيلها والوصول غير المصرح به إليها | لا شيء (نتيجة غير مقصودة) |
| أمثلة | برامج الفدية الخبيثة، حقن SQL، التصيد الاحتيالي | جدار حماية تم تكوينه بشكل خاطئ، استثناء مؤشر فارغ |
| التخفيف | تعقب التهديدات و WAF و EDR | اختبار ضمان الجودة، ومراجعة التعليمات البرمجية، والتكرار |
المظاهر: كيف تتحول النية الخبيثة إلى شفرة خبيثة
المظهر الأكثر شيوعًا للنوايا الخبيثة هو البرمجيات الخبيثة (البرمجيات الخبيثة). ومع ذلك، يمتد التعريف إلى ما هو أبعد من مجرد الملفات القابلة للتنفيذ ليشمل البرامج النصية ووحدات الماكرو وحتى التلاعب بالبنية التحتية كبرمجية.
الأنواع الشائعة من القطع الأثرية الخبيثة
- الفيروسات والديدان: شفرة ذاتية التكرار مصممة للانتشار عبر الشبكات (مثل Conficker).
- برمجيات الفدية الخبيثة هجمات التشفير التي تمنع الوصول إلى البيانات حتى يتم الدفع (مثل WannaCry).2
- أحصنة طروادة و RATs برمجيات حميدة المظهر تخفي حمولات خبيثة للتحكم عن بعد.3
- البرمجيات الخبيثة بدون ملفات: البرامج النصية الخبيثة (PowerShell، Bash) التي تنفذ في الذاكرة دون ترك آثار على القرص.
دراسة حالة من العالم الحقيقي: CVE-2024-3670
لفهم "التعريف الخبيث" من الناحية العملية، يجب أن ننظر إلى نقاط الضعف. CVE-2024-3670 يسلط الضوء على كيف أن نقص تعقيم المدخلات يسمح للنوايا الخبيثة بأن تصبح تنفيذًا.
في هذه الحالة شديدة الخطورة، سمح تطبيق ويب خاص بالمؤسسة بتحميل ملفات عشوائية. استخدم المهاجمون هذا لتحميل ملف الويب شيل-نص برمجي خبيث متخفٍ في صورة صورة- لتحقيق تنفيذ التعليمات البرمجية عن بُعد (RCE).
النمط الضعيف (PHP):
PHP
// خطر خاطئ: تحميل ملف غير صالح إذا ($_T_FILES['upload']) { // لا يوجد تحقق من امتداد الملف أو نوع MIME move_uploaded_file($_FILES['upload']['tmp_name'], "/var/www/html/" . $_FILES['upload']['name'])؛ }؛ }
النتيجة الخبيثة يقوم أحد المهاجمين بتحميل shell.php. عند الوصول إلى هذا الملف عبر المتصفح، يقوم هذا الملف بتنفيذ الأوامر على الخادم، مما يؤدي إلى إنشاء رأس شاطئ للحركة الجانبية.
أنماط التعليمات البرمجية: الكشف عن الأنماط البرمجية الخبيثة
يجب على مهندسي الأمن أن يتعلموا كيفية التعرف على بنية النشاط الخبيث. فيما يلي مقارنات بين عمليات الاستغلال الخبيثة مقابل الأنماط الدفاعية الآمنة.
1. حقن SQL (SQLi)
النية الخبيثة تجاوز المصادقة أو تفريغ جداول قاعدة البيانات.
SQL
- الحمولة الخبيثةSELECT من المستخدمين حيث اسم المستخدم = 'admin' أو '1'='1'؛ -
الدفاع الآمن: استخدام الاستعلامات المعلمة.
بايثون
#TP5T Secure Pattern Cursor.execor.execor("SELECT * من المستخدمين حيث اسم المستخدم = %s", (user_input,))
2. حقن الأوامر
النية الخبيثة تنفيذ أوامر على مستوى نظام التشغيل لاختطاف الخادم.
بايثون
# رمز ضعيف استيراد نظام التشغيل os.system("cat" + user_filename) # مدخلات المهاجم: "؛ rm -rm -rf /"
الدفاع الآمن: استخدم قائمة السماح (القائمة البيضاء).
بايثون
# نمط آمن إذا كان اسم الملف في قائمة المسموح به: subprocess.run(["cat"، اسم الملف])
الدفاع القائم على الذكاء الاصطناعي: الميزة البنلجنتية
بما أن التعريف الخبيث يتطور ليشمل التصيّد الاحتيالي والبرمجيات الخبيثة متعددة الأشكال التي يتم إنشاؤها بواسطة الذكاء الاصطناعي، لم يعد الاكتشاف القديم القائم على التوقيع كافياً. لا يمكن للقواعد الثابتة التقاط التعليمات البرمجية التي تغير شكلها في كل مرة.
هذا هو المكان بنليجنت يغيّر المشهد الدفاعي
كيف يعيد بنليجينت تعريف الكشف عن المعلومات
يستخدم Penligent وكلاء الذكاء الاصطناعي الواعي بالسياق لتجاوز مطابقة الأنماط البسيطة: 4
- التنميط السلوكي: وبدلاً من البحث عن توقيع فيروس معين، يقوم Penligent بتحليل النية من التعليمات البرمجية.5 هل تحاول عملية المفكرة الاتصال بالإنترنت؟ هذا يناسب التعريف الخبيث لمنارة C2.
- الفرز الآلي: يقوم Penligent بتصفية الحالات الشاذة غير الضارة (مثل مطور يقوم بتشغيل برنامج نصي لتصحيح الأخطاء) من التهديدات الحقيقية، مما يقلل من إرهاق التنبيهات.6
- تكامل CI/CDD: من خلال فحص الالتزامات البرمجية بحثًا عن الأنماط المنطقية الضارة قبل النشر، يحوّل Penligent الأمان إلى اليسار، ويمنع الثغرات الأمنية مثل CVE-2024-3670 من الوصول إلى الإنتاج.7
الخاتمة
فهم التعريف الخبيث هو الخطوة الأولى في بناء وضع أمني مرن. إنه الخط الفاصل بين الإزعاج التشغيلي والتهديدات التي تهدد الأعمال التجارية.
من خلال الجمع بين الفهم التقني العميق للأنماط الخبيثة - من حقن SQL إلى برمجيات الفدية الخبيثة - مع أدوات الجيل التالي مثل بنليجنت، يمكن للفرق الأمنية اكتشاف النوايا العدائية وتحليلها وتحييدها بسرعة الآلة.