Why Automated Penetration Testing Tools Matter for Modern Cybersecurity
In the fast-paced and constantly shifting world of cybersecurity, organizations today face not only a greater number of attacks but also increasingly sophisticated and targeted threats. Every day, new vulnerabilities are discovered in operating systems, applications, and connected devices, placing security teams under a relentless burden to identify, assess, and remediate weaknesses before they can be exploited. In such an environment, manual penetration testing—though thorough and valuable—often struggles to keep pace with the frequency and depth of modern risks. This is where Automated Penetration Testing Tools become indispensable, allowing businesses to maintain constant vigilance, test their systems at any time without weeks of scheduling, and respond to newly emerging threats in hours rather than days. For professionals and companies in the United States navigating the digital battlefield of 2025, adopting automation is not merely a way to save time—it is a necessary evolution to ensure resilience and security at scale.
What Is Automated Penetration Testing Tools?
An Automated Penetration Testing Tool is a software platform that simulates cyberattacks—identifying, exploiting, and reporting vulnerabilities—without constant human intervention. Unlike manual pentests, these tools:
- Scan assets and networks for security flaws
- Validate CVEs (Common Vulnerabilities and Exposures) automatically
- Launch realistic exploit scenarios
- Generate compliance-ready reports (ISO 27001, PCI-DSS, NIST)
Unlike traditional manual testing, which may require extensive scripting, specialist command-line skills, and a lengthy audit cycle, these tools incorporate scanning engines, exploit frameworks, and reporting modules into a unified workflow that operates with minimal human intervention. They are designed not only to identify technical weaknesses but also to bridge the gap between raw technical findings and actionable strategies for remediation, making advanced security testing accessible to teams of all sizes and varying expertise.
Key Advantages of Using Automated Penetration Testing Tools
For both seasoned security professionals and organizations just beginning to formalize their cybersecurity strategies, the advantages of Automated Penetration Testing Tools are multi-dimensional. They drastically reduce the time from vulnerability detection to remediation, enabling fixes to be applied in hours or days rather than weeks. This speed not only minimizes exposure time but also helps businesses keep pace with compliance frameworks, whether the requirement is ISO 27001, PCI-DSS, or NIST standards. Cost efficiency is another tangible benefit, as these tools remove the need for repeated manual test cycles with high consulting fees, making continuous security monitoring financially viable even for mid-sized enterprises. Furthermore, by running frequent, automated tests—perhaps weekly or daily—organizations can ensure that newly introduced code, infrastructure changes, or third-party integrations do not inadvertently open new security holes, creating a sustainable layer of defense across operational workflows.
Core Features Automated Penetration Testing Solution Should Have
When selecting an Automated Penetration Testing Tool in 2025, forward-thinking security teams should examine the depth of its automation capabilities.
Ideally, the platform should support a full-stack workflow beginning with asset discovery, continuing through dynamic vulnerability scanning, moving into verified exploitation and privilege escalation, and concluding with comprehensive reporting that maps directly to recognized security frameworks.
A multi-agent architecture—where specialized modules handle reconnaissance, exploitation, and lateral movement independently—can ensure higher precision and faster execution.
Natural language interaction, where complex tasks are launched through plain-English commands, allows non-specialists to initiate sophisticated tests without a steep learning curve.
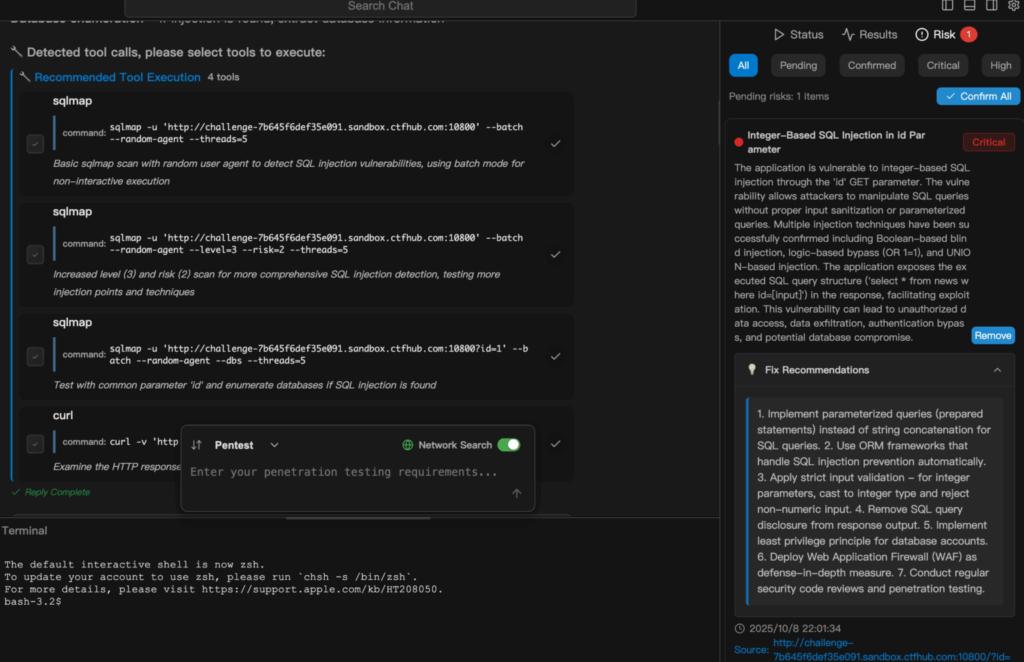
Finally, the inclusion of visual attack chain diagrams and ranked risk dashboards turns raw data into actionable insight, enabling the entire team to understand how one compromised asset could lead to another and how to prioritize defensive measures accordingly.
Penligent.ai: A Next-Generation Automated Penetration Testing Tool
Among the emerging solutions, Penligent.ai stands out as a next-generation Automated Penetration Testing Tool that integrates established security tools—such as nmap, Metasploit, and Burp Suite—into a cohesive, AI-powered workflow. Whether for a beginner exploring cybersecurity or a seasoned red-teamer executing custom payloads, Penligent.ai lowers the barrier to entry while maintaining sophisticated, professional-grade capabilities.
Key highlights include:
- Zero setup with AI-driven installation By eliminating traditional setup complexities, Penligent.ai enables instant testing right after deployment, with an intelligent installer tailored to detect the user’s operating system and configure necessary components automatically.
- Real-time CVE database updates The platform is powered by a real-time CVE vulnerability database containing more than 120,000 entries with tested exploit workflows. This ensures that your assessments are always based on the latest threat intelligence, making it possible to identify and validate vulnerabilities with both speed and precision.
- Interactive attack chain visualizations During testing, Penligent.ai delivers interactive attack‑chain visualizations that map out every stage from initial access to lateral movement. These diagrams not only provide clarity for technical teams but also make complex penetration scenarios understandable to non‑technical stakeholders, helping bridge the gap between raw data and strategic decision-making.
- One-click compliance reporting With its one‑click compliance report generation, Penligent.ai transforms technical results into ready‑to‑use documentation aligned with ISO 27001, PCI‑DSS, SOC 2, and NIST standards. This feature streamlines audits, reduces preparation time, and ensures that essential compliance deliverables are available instantly, whether for internal governance or external regulators.
Choosing the Right Tool: Buyer’s Checklist
Selecting the right Automated Penetration Testing Tool requires more than scanning a list of features; it demands an understanding of how well the tool fits into your existing ecosystem. Consider whether the platform supports all the operating systems in use across your infrastructure, whether its vulnerability database receives updates frequently enough to keep pace with newly discovered exploits, and whether it offers seamless integration with CI/CD pipelines for continuous testing. Evaluate the quality of vendor support, documentation, and community engagement, as these determine how quickly you can resolve issues or adapt the tool to unique scenarios. A thoughtful, informed choice will ensure that your investment scales alongside your growing security needs rather than becoming a bottleneck.
Conclusion
Cybersecurity is a race where standing still is the surest way to fall behind. Automated Penetration Testing Tools empower organizations to keep moving, testing, and strengthening their defenses at the speed of modern threats. If your goal in 2025 is to close the gap between vulnerability discovery and remediation, now is the time to explore platforms like Penligent.ai. By integrating automation into your security strategy, you not only gain efficiency but also the confidence that your defenses are as adaptable as the attacks they face.


