In der hyperbeschleunigten KI-Landschaft von Anfang 2026 hat sich die Sicherheitstechnik weitgehend gespalten. Auf der einen Seite verstärken die Teams die RAG-Pipelines von Unternehmen gegen prompte Einschleusung. Auf der anderen Seite sperren sie Cloud-VPCs ab. Ein großer blinder Fleck bleibt jedoch in der "Schatteninfrastruktur": die Edge Nodes und Home Labs, in denen Prototypmodelle entstehen.
Die Offenlegung von CVE-2025-64113 (CVSS-Score 9.8, Kritisch) eine katastrophale Schwachstelle in Emby Servereine beliebte Medien-Hosting-Lösung. Obwohl Emby eine Verbrauchersoftware ist, überschneidet sich sein Einsatzbereich stark mit der "Local LLM"-Community. Ingenieure betreiben Emby häufig neben Ollama, vLLM, oder Stabile Diffusion Workloads auf hochspezialisierten Bare-Metal-Servern (ausgestattet mit RTX 4090 oder A6000), um die Hardwareauslastung zu maximieren.
Für den AI-Sicherheitsingenieur ist CVE-2025-64113 kein Fehler im Medienserver, sondern ein passwortlose Root-Bridge für Ihren GPU-Compute-Cluster. In diesem Artikel wird die Schwachstelle als Bedrohung für kritische Infrastrukturen analysiert. Dabei werden der C#-Logikfehler, die Eskalation zur Remote Code Execution (RCE) und die Schutzmaßnahmen für Ihr Silizium detailliert beschrieben.
Vulnerability Intelligence Card
| Metrisch | Intelligenz Detail |
|---|---|
| CVE-Bezeichner | CVE-2025-64113 |
| Zielkomponente | Emby Server (MediaBrowser.Server.Core / Benutzerdienst) |
| Betroffene Versionen | Vor 4.9.1.81 (Beta & Stabil) |
| Klasse der Anfälligkeit | Umgehung der Authentifizierung (CWE-287) / Logikfehler |
| CVSS v3.1 Bewertung | 9.8 (Kritisch) (AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H) |
| Angriffsvektor | Netzwerk (Remote), Null-Interaktion |
Technische Vertiefung: Die Logik des "Skeleton Key"
Emby Server basiert auf dem .NET (C#) Stapel. Die Schwachstelle beruht auf einem grundlegenden Fehler in der Logik des "Password Reset Providers", insbesondere in Bezug auf die Art und Weise, wie der Server physische Dateisystem-Tokens gegenüber API-Anfragen validiert.
1. Der architektonische Makel
Der Mechanismus zum Zurücksetzen von Passwörtern bei Emby basiert auf einem "Proof of Access"-Modell.
- Geplanter Arbeitsablauf: Ein Benutzer fordert einen Reset an. Der Server schreibt eine Datei namens
passwortzurücksetzen.txtin das Konfigurationsverzeichnis. Der Benutzer muss diese Datei theoretisch lesen (was voraussetzt, dass er SSH/RDP-Zugang hat), um fortfahren zu können. - Die Verwundbarkeit: Der API-Endpunkt, der die Bestätigung der Rückstellung (
/Benutzer/VergessenesPasswort/Pin) versäumt es, streng darauf zu achten, dass der Nutzer kennt der Inhalt der Datei oder dass die Sitzung, die die Anfrage initiiert hat, mit der Sitzung übereinstimmt, die sie abschließt.
In anfälligen Versionen wirkt das Vorhandensein der Datei wie ein globales boolesches Flag: IsResetMode = True. Jeder nicht authentifizierte Benutzer, der während dieses Fensters auf die API zugreift (oder das Fenster selbst auslöst), kann das Administratorkonto übernehmen.
2. Forensische Code-Rekonstruktion (Hypothetischer C#)
Anhand der Patch-Differenzen und des Verhaltens können wir den anfälligen Logikfluss in der ConnectService oder UserService.
C#
`// VULNERABLE LOGIC PATTERN public async Task
// FATAL FLAW: Der Code prüft, ob die Datei existiert,
// impliziert aber Vertrauen, ohne eine sichere Token-Nutzlast innerhalb der Anfrage zu validieren.
if (_fileSystem.FileExists(tokenPath))
{
var user = _userManager.GetUserByName(request.UserName);
// Der Angreifer gibt ein neues Kennwort ein, und da die Datei existiert,
// lässt der Server das Überschreiben zu.
await _userManager.ChangePassword(user, request.NewPassword);
// Aufräumen
_fileSystem.DeleteFile(tokenPath);
return new { Erfolg = true };
}
throw new ResourceNotFoundException("Reset token not found on disk.");
}`
Dies ist ein Klassiker Zeitpunkt der Überprüfung zum Zeitpunkt der Verwendung (TOCTOU) Logikfehler in Kombination mit unzureichender Authentifizierungstiefe.

3. Die Exploit-Kill-Kette
- Auslöser: Angreifer sendet
POST /Benutzer/ForgotPasswortmit dem Ziel-Benutzernamen (z. B. "admin"). Emby erstelltpasswortzurücksetzen.txt. - Rennen/Bypass: Der Angreifer sendet sofort die Bestätigungsanfrage mit einem neuen Kennwort. Da die Datei auf der Festplatte existiert, ist die Bedingung
FileExistsgibt true zurück. - Übernahme: Der Server aktualisiert das Admin-Kennwort. Der Angreifer meldet sich an.
- Eskalation (RCE):
- Plugin installieren: Emby ermöglicht Administratoren die Installation von Plugins (DLLs).
- FFmpeg-Haken: Administratoren können benutzerdefinierte Vor- und Nachverarbeitungsskripte für die Medientranscodierung definieren.
- Ergebnis: Der Angreifer führt einen Reverse-Shell-Befehl über den Emby-Prozess aus (der oft als Root in Docker oder SYSTEM in Windows läuft).
Die Bedrohung der KI-Infrastruktur: Warum der Kontext wichtig ist
Sicherheitstechniker stufen Medienserver oft als "niedrige Priorität" ein. Im Zusammenhang mit der KI-Entwicklung ist dies ein fataler Fehler.
1. Der "Co-Located"-Angriffsvektor
KI-Ingenieure bauen in der Regel "All-in-One"-Rechenserver. Eine einzelne Ubuntu-Box mit zwei RTX 4090 hostet oft:
- Anschluss 11434: Ollama (LLM Inferenz)
- Anschluss 6333: Qdrant (Vektor-DB)
- Anschluss 8888: JupyterLab
- Anschluss 8096: Emby (Medien/persönliche Nutzung)
Da diese Dienste auf demselben Kernel laufen und dieselben Dateisystem-Mounts nutzen (z. B., /mnt/data), ermöglicht es dem Angreifer, Emby über CVE-2025-64113 zu kompromittieren und lokal zu drehen (localhost).
2. Exfiltration von Vermögenswerten von hohem Wert
Sobald sich der Angreifer im Emby-Container/Prozess befindet, kann er über Volume-Mounts auf diesen zugreifen:
- Modell Gewichte: Proprietäre LoRA-Adapter oder feinabgestimmte
.safetensorsDateien im Wert von Tausenden von Rechenstunden. - RAG-Datensätze: Unverschlüsselte Vektorspeicher mit privaten Wissensdatenbanken des Unternehmens.
- Umgebungsvariablen:
.envDateien, die häufig zwischen Docker-Containern ausgetauscht werden und OpenAI-API-Schlüssel oder HuggingFace-Tokens enthalten.
3. Compute Hijacking (Kryptojacking)
Die unmittelbarste Auswirkung ist oft die Verweigerung von Ressourcen. Angreifer setzen Stille Bergleute (wie XMRig), die an bestimmte CUDA-Kerne gebunden sind und 30-50% der GPU-Kapazität abschöpfen. Dies verschlechtert die Inferenzlatenz für legitime KI-Workloads und führt zu einer Überhitzung der Hardware, während es gleichzeitig subtil genug ist, um eine grundlegende CPU-Überwachung zu umgehen.
KI-gesteuerte Verteidigung: Der sträfliche Vorteil
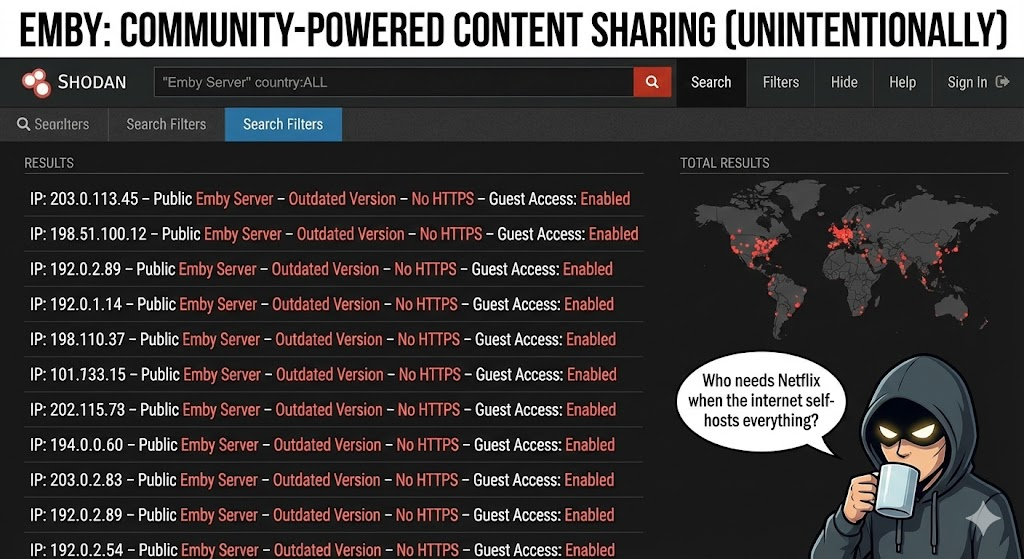
Die Erkennung von CVE-2025-64113 in einer verteilten, Ad-hoc-KI-Umgebung ist eine Herausforderung. Herkömmliche Scanner (Nessus/Qualys) erfordern Scans mit Zugangsberechtigung, um Dateisysteme zu sehen, und übersehen häufig nicht standardisierte Ports.
Dies ist der Ort, an dem Penligent.ai definiert die offensive Sicherheitsposition neu.
- Entdeckung von Schattenanlagen (Die "Unbekannten")
Die KI-Agenten von Penligent nutzen passive Datenverkehrsanalyse und aktives Sondieren, um "Schattendienste" zu identifizieren. Er erkennt, dass ein hochwertiger GPU-Knoten den Port 8096 freigibt, identifiziert den Dienst als Emby und korreliert ihn automatisch mit der kritischen CVE-2025-64113-Information. Er kontextualisiert das Risiko: "Media Server ausgesetzt auf kritischem KI-Knoten".
- Zerstörungsfreie Logiküberprüfung
Anstatt zu versuchen, das Administratorkennwort zurückzusetzen (was eine Dienstverweigerung zur Folge hätte), führt Penligent eine Safe Logic Probe durch.
- Er leitet den Handshake ein, um die
passwortzurücksetzen.txtErstellungsmechanismus (falls sicher). - Er analysiert das API-Antwort-Timing und die Fehlercodes, um festzustellen, ob der Bypass-Vektor aktiv ist.
- Es bestätigt die Schwachstelle mit nahezu null Fehlalarmen und liefert eine verifizierte "kritische" Warnung, ohne den Techniker bei seinem Samstagabendfilm oder seinem LLM-Trainingslauf zu stören.
Handbuch zur Wiederherstellung und Härtung
Wenn Sie eine KI-Infrastruktur verwalten, zu der auch Emby gehört, ist sofortiges Handeln erforderlich.
1. Patchen (Die einzige Lösung)
Upgrade auf Emby Server 4.9.1.81 sofort. In dieser Version wird die Logik zum Zurücksetzen des Passworts grundlegend umgeschrieben, sodass ein Token erforderlich ist, das nicht über die API-Interaktion erraten werden kann.
2. Unveränderliche Dateisystem-Sperre (der "Kill Switch")
Wenn Sie nicht sofort patchen können (z. B. aufgrund von Abhängigkeitsfehlern), können Sie den Exploit kastrieren, indem Sie die Erstellung des Reset-Tokens verhindern.
Für Linux (Docker/Bare Metal):
Bash
# Wechseln Sie in das Emby-Konfigurationsverzeichnis cd /var/lib/emby/config
Erstellen einer Dummy-Datei
touch passwortzurücksetzen.txt
Unveränderbar machen (selbst root kann sie nicht schreiben/löschen)
sudo chattr +i passwortzurücksetzen.txt`
Wirkung: Die API-Anfrage des Angreifers an Kennwort vergessen scheitert, weil der Server nicht in die Datei schreiben kann, wodurch die logische Kette unterbrochen wird.
Für Windows:
Klicken Sie mit der rechten Maustaste auf den Ordner config -> Eigenschaften -> Sicherheit -> Erweitert. Fügen Sie eine "Deny Write"-Regel für das Benutzerkonto hinzu, unter dem der Emby-Dienst läuft.
3. Netzsegmentierung (Zero Trust)
- Management-Ports isolieren: Geben Sie den Port 8096/8920 niemals für das öffentliche Internet frei.
- Tunnel verwenden: Zugang zu den Diensten über Heckwaage, Cloudflare-Tunneloder ein VPN.
- Container-Isolierung: Stellen Sie sicher, dass der Emby-Docker-Container nicht als
-privilegiertund mountet nur die spezifischen Medienverzeichnisse, die er benötigt (Read-Only, wo möglich), nicht den gesamten/mnt/Wurzel.
Schlussfolgerung
CVE-2025-64113 ist eine Erinnerung daran, dass die Angriffsfläche eines KI-Systems weit über das Modell selbst hinausgeht. Im Zeitalter der konvergenten Infrastruktur kann eine Schwachstelle in einer Freizeitmedienanwendung die fortschrittlichsten künstlichen Intelligenz-Workloads gefährden.
Bei der Sicherheitstechnik geht es um den Schutz der gesamte Stapel. Durch rigoroses Patching, Netzwerksegmentierung und den Einsatz von KI-gesteuerten Tools zur Erkennung von Assets wie Penligent können Unternehmen diese Hintertüren schließen, bevor sie zu einem katastrophalen Verlust von Rechenleistung oder geistigem Eigentum führen.