Introduction
In today’s cybersecurity landscape, with zero-day vulnerabilities emerging constantly and AI-driven attack models iterating at machine speed, TLS encryption (Transport Layer Security) remains the often-overlooked guardian—the cryptographic backbone for all secure communications.
TLS is not just a protocol; it is the cryptographic weave underpinning the entire internet trust model. Every secure HTTPS session, encrypted API call, and protected IoT handshake relies on it.
Entering 2025, with quantum threats on the horizon and AI systems widely deployed in attack and defense, precision in TLS implementation is more critical than ever.
For penetration testers, red teamers, and AI security engineers, understanding TLS is no longer optional—it’s the “ticket in” to modern vulnerability detection, encrypted configuration audits, and automated security testing frameworks.
What is TLS Encryption?
TLS (Transport Layer Security) is the successor to SSL, used to establish encrypted channels between two endpoints—typically a client and a server. It ensures the three core pillars of network security:
| Security Pillar | TLS Function | Outcome |
|---|---|---|
| Confidentiality | Protects transmitted data via symmetric encryption | Prevents eavesdropping |
| Integrity | Uses message authentication codes (MAC) to detect tampering | Prevents data modification |
| Authentifizierung | Verifies server identity through digital certificates | Prevents man-in-the-middle attacks |
Although the protocol is conceptually straightforward, real-world failures almost always come from implementation details: legacy cipher suites, misconfigured certificates, or systems still running TLS 1.0/1.1. Even seasoned engineers can encounter handshake failures due to version mismatches or expired intermediate certificates.
TLS 1.3: A Leap in Speed and Security
TLS 1.3 represents the most significant evolution of the protocol since its inception. Introduced in 2018, it streamlines the handshake process and removes insecure cryptographic algorithms such as RC4, SHA-1, and static RSA key exchanges.
| Merkmal | TLS 1.2 | TLS 1.3 |
|---|---|---|
| Round-trips for handshake | 2–3 | 1 (or 0, supporting 0-RTT) |
| Deprecated ciphers | Partial | All removed |
| Forward secrecy | Optional | Mandatory |
| 0-RTT data | Not supported | Supported (replay risk exists) |
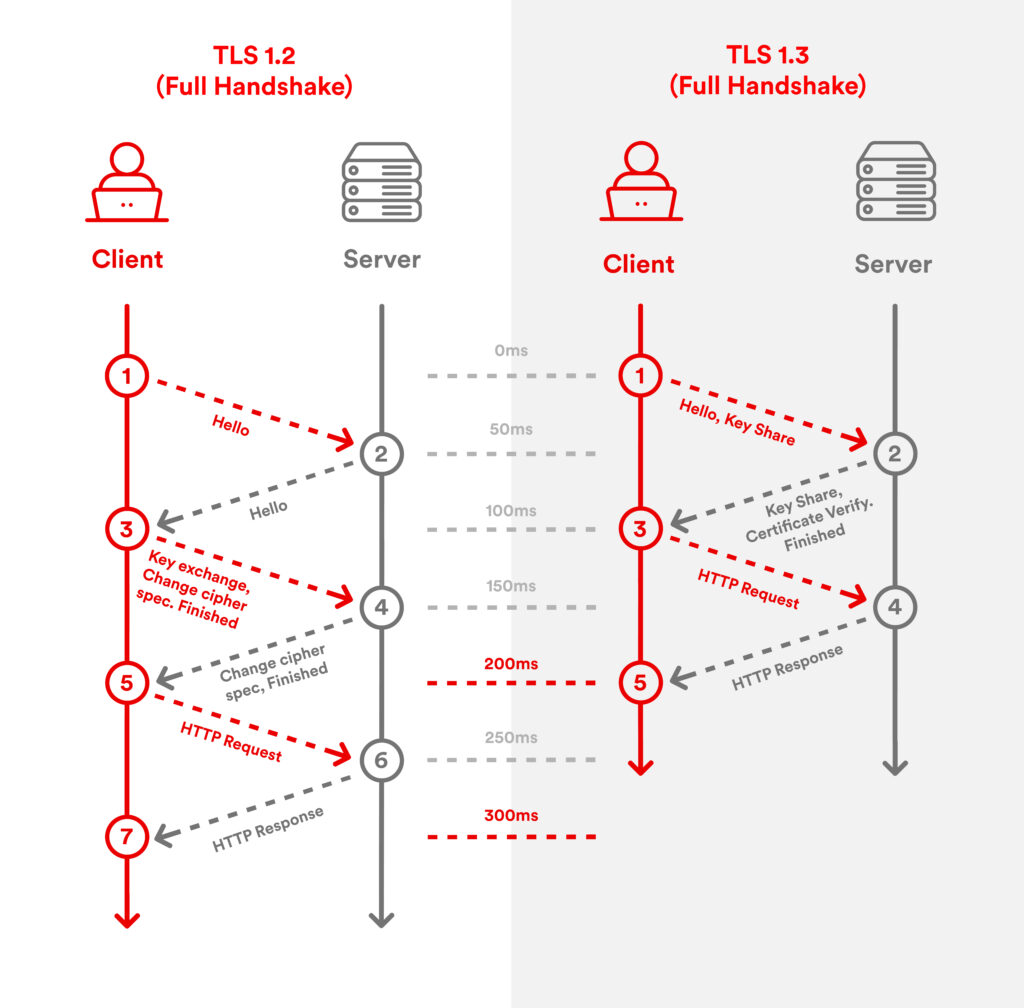
TLS 1.3 balances performance and privacy, which is crucial for high-frequency API calls, IoT systems, and AI-driven security systems needing thousands of encrypted connections in milliseconds.
However, 0-RTT carries replay risks, reminding us that security and convenience are always a balancing act.
TLS Handshake Deep Dive: How Encryption is Negotiated
At the heart of TLS is the handshake—a sequence of messages that establishes a shared secret, negotiates cipher suites, and authenticates the server (and optionally the client).
During a typical TLS 1.3 handshake:
- ClientHello: The client sends supported TLS versions, cipher suites, and a random nonce.
- ServerHello: Server selects TLS version, cipher suite, and provides its certificate.
- Key Exchange & Finished: Both parties compute shared secret, exchange Finished messages with HMAC verification.
Optional 0-RTT allows the client to send data immediately after ClientHello, using previously negotiated keys, improving latency at the risk of replay attacks.
Common TLS Misconfigurations and Failures
Even experienced engineers can misconfigure TLS, leading to serious vulnerabilities or handshake failures. Common issues include:
| Misconfiguration | Impact | Detection |
|---|---|---|
| Expired/Invalid Certificates | Browser/API rejects connection | Certificate inspection or OpenSSL s_client |
| Weak Cipher Suites | Vulnerable to downgrade attacks | nmap/sslyze scans |
| Mixed Content | Insecure HTTP resources on HTTPS page | Browser console, automated crawler |
| Missing HSTS | Susceptible to MITM via strip attacks | Security headers analysis |
| Reverse Proxy / Load Balancer Misalignment | TLS terminated at proxy, backend misconfigured | Endpoint testing |
Tools such as OpenSSL, nmap, sslyze, and automated CI/CD security checks are indispensable to catch these errors early.
Penetration Testing & Automation
For AI security engineers or penetration testers, TLS misconfigurations are high-value targets. Automating TLS audits can save hundreds of man-hours.
Automation Workflow Example (Python + OpenSSL):
import subprocess
hosts = ['example.com', 'api.example.com']
for host in hosts:
result = subprocess.run(['openssl', 's_client', '-connect', f'{host}:443'], capture_output=True, text=True)
if "Verify return code: 0 (ok)" in result.stdout:
print(f"{host} TLS OK")
else:
print(f"{host} TLS ERROR")
This simple snippet checks certificate validity and basic handshake success across multiple endpoints.
AI-Driven Detection of TLS Weaknesses
Modern security platforms, such as Penligent.ai, leverage AI to detect TLS anomalies across enterprise networks.
Key features include:
- Automated scanning for weak cipher suites, expired certs, and handshake anomalies.
- AI-based anomaly detection in repeated handshake patterns to detect MITM or downgrade attacks.
- CI/CD pipeline integration for continuous monitoring of TLS endpoints.
By combining ML-based anomaly detection with rule-based validation, Penligent.ai enables security teams to proactively remediate TLS misconfigurations before they are exploited.
TLS in AI-Driven Security Pipelines
AI-driven security systems increasingly rely on TLS for encrypted data flows between microservices, cloud APIs, and IoT endpoints.
Automated scanning, anomaly detection, and penetration testing now integrate TLS checks at scale:
- Automated certificate validation: Continuous verification of validity, expiration, and revocation status.
- Cipher suite auditing: Detect deprecated or weak ciphers, including fallback vulnerabilities.
- Handshake pattern analysis: AI identifies abnormal handshake behaviors indicating potential MITM attacks.
Penligent.ai Applied to TLS Audits
Penligent.ai can be directly applied to large-scale TLS assessments. Security engineers can deploy it to scan hundreds of endpoints, automatically classify misconfigurations, and generate actionable remediation reports.
Example Workflow:
- Penligent.ai crawls all API endpoints, collecting handshake metadata.
- AI engine analyzes TLS versions, cipher suites, certificate chains, and handshake timings.
- Automated reports highlight endpoints with deprecated TLS, weak ciphers, expired certs, or handshake anomalies.
This automation allows security teams to prioritize remediation based on real risk exposure rather than anecdotal errors.
Preparing for Post-Quantum TLS
Quantum computing introduces potential threats to traditional public-key cryptography, particularly RSA and ECDSA, which underpin TLS today.
Post-quantum TLS aims to integrate quantum-resistant algorithms such as CRYSTALS-Kyber or Dilithium to protect key exchanges and signatures.
Security engineers should:
- Monitor emerging post-quantum standards (NIST PQC competition outputs).
- Implement hybrid TLS (classical + post-quantum) in test environments.
- Continuously validate cryptographic agility in automation pipelines to adapt to future algorithm deprecations.
Engineering Best Practices: TLS Checklist
| Kategorie | Recommendation |
|---|---|
| Certificate Management | Use automated renewal, monitor revocation, enforce HSTS |
| Cipher Suites | Disable weak ciphers, prefer AEAD algorithms (AES-GCM, ChaCha20-Poly1305) |
| Handshake & Session | Enforce TLS 1.2+, forward secrecy, validate resumption securely |
| Proxy & Load Balancer | Ensure end-to-end encryption, forward headers, maintain certificate trust |
| Automation & Monitoring | Integrate AI-driven detection, log handshake anomalies, alert on expired certs |
Schlussfolgerung
TLS encryption is the foundation of secure digital communication. AI security engineers, penetration testers, and DevOps teams must understand not just TLS theory but real-world implementation, automated testing, and potential misconfigurations.
Platforms like Penligent.ai allow teams to scale detection, classify risks. By combining cryptographic best practices, AI-assisted testing, and post-quantum preparedness, organizations can ensure secure communications while staying ahead of evolving threats.


