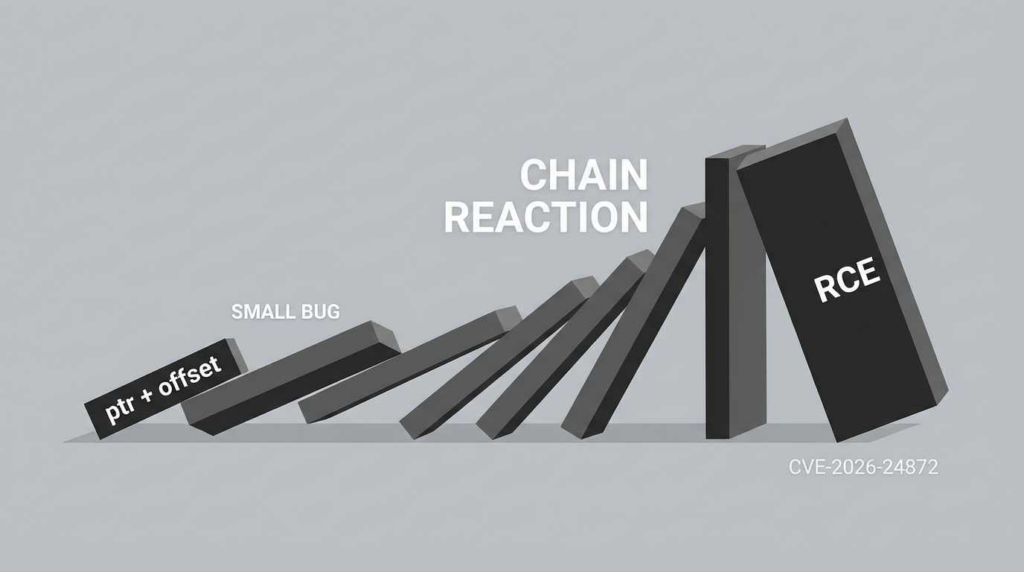
La divulgación de CVE-2026-24872 on January 28, 2026, sent ripples through the decentralized world-building community. Affecting ProjectSkyfire’s SkyFire_548 component, this vulnerability represents a “Critical” (CVSS 9.8) failure in low-level memory handling. At its core, it is a Pointer Arithmetic Error (CWE-468) that enables unauthenticated remote attackers to achieve full system compromise without any user interaction.
Architectural Context: The SkyFire_548 Processing Pipeline
ProjectSkyfire is an open-source engine designed for high-concurrency virtual environments. To maintain real-time performance, SkyFire_548 utilizes custom memory allocators and high-speed packet parsing logic written in C++.
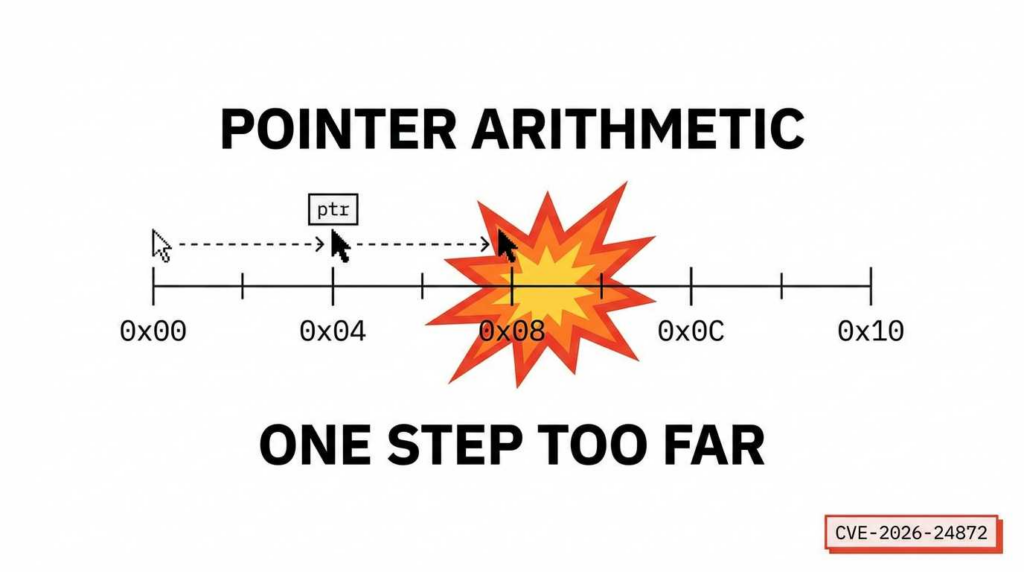
The engine processes binary streams using a “sliding window” parser. When a packet arrives, the engine calculates the location of the next data segment by adding an offset (extracted from the packet header) to the current base pointer.
The Root Cause: Unchecked Offset Addition
La vulnerabilidad reside en la WorldSession::HandleBufferUpdate function. In versions prior to 5.4.8-stable5, the engine trusts the segment_length y next_offset fields provided in the incoming UDP/TCP stream.
Detailed Code Analysis
Let’s look at the assembly-level logic often found in the vulnerable module:
C++
`// Decompiled representation of the vulnerable routine in SkyFire_548 void WorldSession::HandleBufferUpdate(Packet& packet) { uint8_t* base_ptr = this->internal_buffer; uint32_t header_offset = packet.ReadUInt32(); // Attacker-controlled uint32_t payload_size = packet.ReadUInt32(); // Attacker-controlled
/* * CRITICAL FAILURE:
* The engine fails to verify if (header_offset + payload_size)
* exceeds the bounds of internal_buffer_size.
*/
uint8_t* write_target = base_ptr + header_offset;
// This results in an Out-of-Bounds (OOB) Write
memcpy(write_target, packet.GetPayload(), payload_size);
}`
By providing a header_offset that pushes the write_target beyond the internal_buffer, an attacker can selectively overwrite adjacent memory structures. In a 64-bit environment, this is often used to target:
- Function Pointers: Overwriting pointers in the Global Offset Table (GOT).
- Stack Canaries/Return Addresses: Hijacking the control flow during the function epilogue.
- Heap Metadata: Corrupting chunk headers to trigger an exploit during subsequent
mallocofreecalls.
Comparative Vulnerability Landscape (2025-2026)
To understand the severity, we must compare CVE-2026-24872 to other “Titan” vulnerabilities that share similar memory corruption primitives:
| ID CVE | Impacted System | Causa raíz | CVSS |
|---|---|---|---|
| CVE-2026-24872 | ProjectSkyfire | Pointer Arithmetic / OOB Write | 9.8 |
| CVE-2026-21962 | Linux Kernel | Integer Overflow in create_elf_tables | 10.0 |
| CVE-2025-49201 | OpenSSL | Side-channel in RSA key parsing | 7.5 |
| CVE-2026-24830 | Commander-Genius | Buffer Overflow in SDL2 processing | 8.8 |
The “Zero-Click” nature of CVE-2026-24872 puts it in a rare category of vulnerabilities, similar to the “Stagefright” or “Heartbleed” eras, where simply being reachable on the network is sufficient for compromise.
Exploitation Strategy: From Memory Corruption to RCE
For a security engineer, the path to an exploit (PoC) involves bypasses for modern mitigations like ASLR (Address Space Layout Randomization) y DEP/NX (Data Execution Prevention).
- Information Leak: The attacker first uses a secondary vulnerability (or a variation of the same pointer error) to read memory, leaking the base address of the engine’s executable.
- Pointer Pivot: Using the OOB write in CVE-2026-24872, the attacker overwrites a specific object’s VTable.
- ROP Chain Execution: The next time the engine calls a virtual method on that object, the instruction pointer (
RIP) is redirected to a Programación orientada al retorno (ROP) chain crafted by the attacker, leading to the execution of a reverse shell or malware stager.
Advanced Mitigation: The Shift to AI-Native Pentesting
The discovery of CVE-2026-24872 highlights a significant gap in traditional security tooling. Static Analysis (SAST) often misses these arithmetic errors due to complex data-flow paths, and Fuzzing (DAST) can take weeks of compute time to find the exact “magic” packet structure.
Enter Penligent.ai: The Agentic Advantage
This is where the industry is pivoting. Penligent.ai represents the next generation of “Agentic Hacker” platforms. Unlike standard scanners, Penligent utilizes an AI-native reasoning engine to understand the semántica of the ProjectSkyfire protocol.
- Logic-Aware Fuzzing: Instead of brute-forcing, Penligent’s AI agents analyze the engine’s source code or binary and reason that the
header_offsetis a potential point of failure. - Autonomous Chain Construction: Once a memory corruption primitive is found, the platform doesn’t just report a “crash.” It autonomously attempts to chain the vulnerability with other environmental factors to prove RCE, providing engineers with a full, validated exploit path.
- Privacy-First Deployment: For teams handling sensitive infrastructure, Penligent can be deployed in a “Private Agent” mode—similar to the M4 Mac Mini setups discussed by the community—ensuring that the vulnerability data and exploit logic never leave the internal network.
Integración de Penligent.ai into the CI/CD pipeline ensures that deep-seated logic flaws like CVE-2026-24872 are caught during the build phase, rather than discovered by threat actors in production.
Remediation and Hardening Guidelines
If you are running any ProjectSkyfire-based instances, follow this priority list:
- Immediate Upgrade: Move to SkyFire_548 Version 5.4.8-stable5 or higher. This patch introduces strict
bounds_checkmacros on all pointer arithmetic operations. - Kernel Hardening: Asegúrese
kptr_restrictyperf_event_paranoidare set to their most restrictive levels to prevent easy information leaks. - Segmentación de la red: Isolate virtual world management ports behind a VPN or Zero-Trust Gateway to minimize the exposure of the “Zero-Click” attack surface.
- Continuous Testing: Use agentic AI platforms to perform regular, deep-logic audits of custom engine modules.
Referencias
- NVD CVE-2026-24872 Detail – The official government record.
- MITRE CVE-2026-24872 – The industry-standard vulnerability identifier.
- ProjectSkyfire GitHub Advisory – Direct patch notes and security analysis from the maintainers.
- CWE-468: Pointer Arithmetic Issues – Deep dive into the underlying software weakness.
- Penligent.ai Blog: The Future of Agentic Pentesting – How AI is automating the discovery of memory safety flaws.