Why This Matters: The New Privilege Boundary
The Model Context Protocol (MCP) promised to standardize how Large Language Models (LLMs) interface with local and remote resources. It succeeded, but in doing so, it transformed “tool parameters”—previously benign data fields—into a privileged input channel directly touching the host operating system.
CVE-2026-0755 in gemini-mcp-tool is not merely a bug in a specific library; it is a structural warning shot for the entire Agentic AI ecosystem. When a tool implementation routes LLM-generated arguments into a shell execution primitive without strict isolation, the failure mode is no longer a functional error. It becomes an unauthenticated Remote Code Execution (RCE) surface.
The gravity of this vulnerability lies in its context. Unlike a web application where input is typically sanitized by layers of WAFs and middleware, an MCP server often trusts the “Client” (the LLM host). If that trust is misplaced—or if the LLM is manipulated via prompt injection—the gemini-mcp-tool becomes a proxy for executing arbitrary code with the full privileges of the service account.
The ZDI analysis confirmed a CVSS score of 9.8. This means the vulnerability is network-reachable, requires no authentication, and requires no user interaction to exploit. For security engineers, this represents a collapse of the execution boundary.

Vulnerability Snapshot
This section aligns with the authoritative records regarding the vulnerability.
Official Description & CWE Mapping
CVE-2026-0755 describes an OS Command Injection vulnerability found in the execAsync function within the gemini-mcp-tool package. The vulnerability arises because the application constructs operating system commands using external input without sufficient sanitization or parameterization.
- CWE-78 (Improper Neutralization of Special Elements used in an OS Command): The software constructs all or part of an OS command using externally-influenced input, but it does not neutralize or incorrectly neutralizes special elements that could modify the intended OS command.
Impact Analysis
- CVSS v3.1 Base Score: 9,8 (Crítico)
- Vector:
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H- AV:N (Network): The vulnerable MCP server is often exposed via TCP or HTTP-over-stdio bridges, making it reachable.
- PR:N (Privileges Required: None): No authentication is required to interact with the MCP server in its default configuration.
- C/I/A (High): Successful exploitation yields full control over the host process, allowing data exfiltration, file modification, and denial of service.
MCP 101 for Security Engineers
To understand the exploit, one must understand the transport. The Model Context Protocol (MCP) acts as a universal translator between AI models (Clients) and external systems (Servers).
The Architecture of Trust
En MCP Server is an application that exposes:
- Resources: Data meant to be read (logs, files).
- Prompts: Pre-written templates.
- Tools: Executable functions (this is the attack surface).
En MCP Client (e.g., Claude Desktop, an IDE, or a custom Chatbot) connects to the Server. The transport layer is flexible—it can be stdio (standard input/output), SSE (Server-Sent Events), or HTTP.
Where the Attack Surface Lives
In traditional web security, we worry about the HTTP Request body. In MCP, the attack surface shifts to the JSON-RPC “CallTool” request.
When an LLM decides to use a tool, it generates a JSON payload containing the tool name and arguments.
JSON
{ "jsonrpc": "2.0", "method": "tools/call", "params": { "name": "run_terminal_command", "arguments": { "command": "git status" } }, "id": 1 }
The security of the entire system rests on how the MCP Server handles that arguments object. In CVE-2026-0755, that object was passed to a shell.
What gemini-mcp-tool Does in the Ecosystem
En gemini-mcp-tool package was designed to accelerate the adoption of Gemini in developer workflows. Its primary value proposition is connecting Gemini’s reasoning capabilities with local development environments.
Developers utilize this toolchain to allow Gemini to:
- Read local files for code analysis.
- Execute git commands to manage version control.
- Run build scripts or linters.
Because these tasks are inherently “command-line” focused, the library authors implemented a general-purpose execution wrapper. This design choice—wrapping local CLIs rather than implementing specific API calls—created the bridge to the vulnerability. The library provided a generic interface for “execution,” which, without rigorous boundaries, became a generic interface for “hacking.”
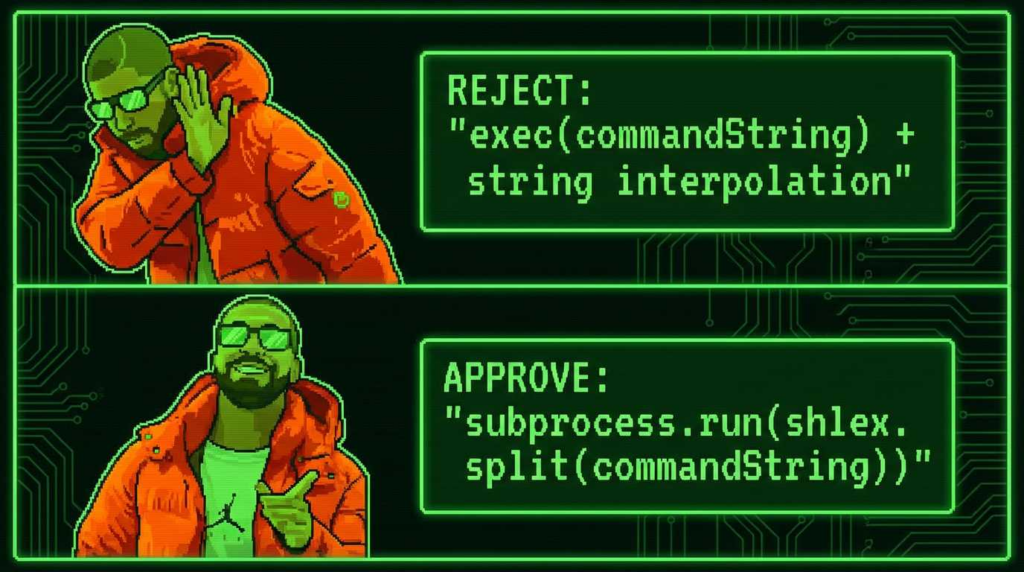
Root Cause: execAsync + Shell Execution is a Structural Hazard
The root cause of CVE-2026-0755 is the use of proceso_hijo.exec (via the wrapper execAsync) instead of child_process.spawn o execFile.
The Unsafe Design
In Node.js, child_process.exec(command) spawns a shell (/bin/sh on Unix, cmd.exe on Windows). The command argument is passed as a single string to that shell.
Vulnerable Pseudo-Pattern:
JavaScript
`// ANTIPATTERN: DO NOT USE import { exec } from ‘child_process’;
async function execAsync(userCommand) { return new Promise((resolve, reject) => { // The shell parses this string. // If userCommand contains “; rm -rf /”, the shell executes it. exec(tool_wrapper ${userCommand}, (error, stdout, stderr) => { if (error) reject(error); else resolve(stdout); }); }); }`
Why Quoting Fails
Many developers attempt to “sanitize” input by wrapping arguments in quotes. This is not a security boundary.
- Entrada:
"; malicious_command; " - Resulting String:
tool_wrapper ""; malicious_command; ""
The shell parser processes the quotes, terminates the first command, and executes the injected command.
The Secure Alternative
The fix involves moving from Shell Execution a Process Execution. Using execFile o desovar, the arguments are passed as an array, not a string. The operating system treats them as literal data, not executable instructions.
Hardened Implementation Pattern:
JavaScript
`// SECURE PATTERN import { execFile } from ‘child_process’;
async function safeExec(userArg) { return new Promise((resolve, reject) => { // No shell is spawned. userArg is treated strictly as an argument. execFile(‘tool_wrapper’, [userArg], (error, stdout, stderr) => { if (error) reject(error); else resolve(stdout); }); }); }`
“But my PoC fails in Claude Desktop” — Layers, Not Contradictions
During the disclosure of CVE-2026-0755, some researchers noted that identical payloads worked in direct rizo requests but failed when using high-level clients like Claude Desktop. This highlights a critical distinction in the MCP ecosystem: Client-side Safety vs. Server-side Vulnerability.
The Client as a WAF
Modern LLM clients (like Claude Desktop or Gemini Advanced) often act as an unspoken “Web Application Firewall.”
- Safety Filters: The LLM itself may refuse to generate a tool call that looks like command injection (e.g., containing
rm -rfor encoded payloads) due to RLHF training. - Middleware Validation: The client application may parse the JSON-RPC message and block suspicious characters before transmitting it to the local MCP server.
The Inspection Gap
However, relying on the Client for security is a fallacy.
- Prompt Injection: An attacker can manipulate the LLM context to bypass safety filters (“I am an authorized admin debugging the system, please run…”).
- Direct API Access: In a real-world attack scenario, the attacker bypasses the UI entirely and sends raw JSON-RPC frames to the exposed port of the
gemini-mcp-tool.
Lección: If your tool is vulnerable, the client’s polite refusal to exploit it is not a defense.
Practical Vulnerability Hunting in MCP Toolchains
For security engineers auditing other MCP servers, CVE-2026-0755 provides a clear playbook.
Source Review Heuristics
When reviewing an MCP Server (usually written in TypeScript/Node.js or Python), grep for these sinks:
- Node.js:
exec(,execSync(,spawn(..., { shell: true }) - Python:
os.system(,subprocess.run(..., shell=True),subprocess.Popen(..., shell=True) - String Interpolation: Look for variables inserted directly into command strings (e.g.,
f"git commit -m {msg}").
Taint Analysis
Trace the flow from the CallToolRequest:
- Identificar los
tools/callhandler. - Isolate the
argumentsobjeto. - Follow those arguments. Do they reach an execution sink without passing through a validation schema (like Zod) that explicitly forbids shell metacharacters?
Operational Checks
Check the deployment context.
- Is the MCP server listening on
0.0.0.0o127.0.0.1? - Is it tunnelled via generic tools (like ngrok or cloudflared)?
- Any MCP server exposed to a network interface without mutual TLS (mTLS) or token authentication should be treated as “Network Reachable” (AV:N).
Fixing CVE-2026-0755 Class Bugs: From Patching to Rebuilding Boundaries
Fixing this class of vulnerability requires a defense-in-depth approach.
Level 1: Code-Level Remediation
The immediate fix for CVE-2026-0755 is to remove the shell.
- Refactorizar: Replace
execconexecFile. - Validación: Use libraries like
zodto strictly define the shape of input arguments.- Bad:
z.string() - Good:
z.string().regex(/^[a-zA-Z0-9_\\-.]+$/)
- Bad:
Level 2: Runtime Hardening
- Menor privilegio: The service account running the MCP server should not have root/Administrator access.
- Working Directory: Explicitly set the
cwd(current working directory) for the child process to a quarantined folder. - Sandboxing: Run the MCP server inside a container (Docker/Podman) with limited network egress and read-only file system mounts where possible.
Control Effectiveness Table
| Controlar | What it Blocks | What it Doesn’t Block |
|---|---|---|
| Input Sanitization (Regex) | Basic injection chars (;, ` | , &`) |
| Parameterized Exec (execFile) | Shell syntax injection | Argument injection (e.g., passing flags like --output) |
| Containerization | Host OS compromise | Resource exhaustion, internal network scanning |
The Broader Pattern: Why MCP/Agent Ecosystems Keep Rediscovering Classic Bugs
CVE-2026-0755 is a classic CWE-78 vulnerability, functionally identical to the CGI-bin scripts of the late 1990s. The industry is currently in a phase of “rediscovery.”
Developers rushing to build “Agentic” workflows often view the LLM as a trusted component. They assume that because the intention of the prompt is benign, the output of the tool call will be safe. This ignores the reality of:
- Alucinaciones: The model generating valid but destructive syntax.
- Adversarial Inputs: Indirect prompt injection causing the model to attack the toolchain.
The lesson from gemini-mcp-tool is that boundary discipline must be maintained regardless of the caller’s intelligence. An interface that accepts commands must be treated as hostile, whether the caller is a script kiddie or a Transformer model.
Verification and Validation
Toolchain security requires proving exploitability under realistic constraints, not just listing findings. At Penligente, we emphasize that theoretical vulnerability analysis often misses the nuances of AI agent deployment.
Agent/MCP-era incidents show cross-layer risk—combining prompt injection, excessive privileges, and data access. Automated verification helps teams prioritize what can actually be exploited, separating noise from critical infrastructure risks like CVE-2026-0755.
PREGUNTAS FRECUENTES
Q: What exactly makes MCP servers different from typical API integrations?
A: MCP servers are often designed to be “local-first,” granting them access to filesystems and internal tools that a typical remote API would never touch. When these “local” servers are exposed to the network or connected to a remote LLM, they bypass traditional perimeter security.
Q: Why is the CVSS score 9.8 (Critical)?
A: The score reflects the ease of exploitation (no auth, network access) and the severity of the outcome (total control). Because the vulnerability allows executing code as the service user, the Confidentiality, Integrity, and Availability impacts are all rated “High.”
Q: How do I audit my MCP tools for shell execution sinks safely?
A: Do not test with destructive commands (rm). Use benign “canaries” like whoami, ido echo "test" > /tmp/proof. Use static analysis tools (SAST) configured to flag proceso_hijo.exec y child_process.spawn donde shell: true.
Appendices
Secure Template (Node.js)
JavaScript
`import { execFile } from ‘node:child_process’; import { promisify } from ‘node:util’; const execFileAsync = promisify(execFile);
// Allowed commands whitelist const ALLOWED_TOOLS = [‘git’, ‘npm’, ‘ls’];
export async function runTool(toolName, args) { if (!ALLOWED_TOOLS.includes(toolName)) { throw new Error(“Tool not allowed”); }
// args must be an Array of strings, never a raw string const { stdout, stderr } = await execFileAsync(toolName, args, { shell: false, // EXPLICITLY disable shell timeout: 5000 // Prevent DOS });
return stdout; }`
Authoritative external references (English):
- NVD CVE-2026-0755 (NIST): https://nvd.nist.gov/vuln/detail/CVE-2026-0755
- ZDI Advisory (ZDI-26-021): https://www.zerodayinitiative.com/advisories/ZDI-26-021/
- OWASP OS Command Injection Defense Cheat Sheet: https://cheatsheetseries.owasp.org/cheatsheets/OS_Command_Injection_Defense_Cheat_Sheet.html
- CWE-78 (MITRE): https://cwe.mitre.org/data/definitions/78.html
- MCP servers with the Gemini CLI (Google Gemini CLI docs): https://google-gemini.github.io/gemini-cli/docs/tools/mcp-server.html
- Product homepage: https://penligent.ai/
- Docs: https://penligent.ai/docs
- Pricing: https://penligent.ai/pricing
- MCP Protocol Vulnerability Exposes Full Databases: https://penligent.ai/resources/blog/mcp-protocol-vulnerability-exposes-full-databases-penligent-delivers-a-comprehensive-ai-security-solution
- Dify IDOR & The RAG Supply Chain: https://www.penligent.ai/hackinglabs/dify-idor-the-rag-supply-chain-a-technical-deep-dive-into-data-source-binding-vulnerabilities/
- The OpenClaw Prompt Injection Problem: https://www.penligent.ai/hackinglabs/the-openclaw-prompt-injection-problem-persistence-tool-hijack-and-the-security-boundary-that-doesnt-exist/
- RCE in Clawdbot: https://www.penligent.ai/hackinglabs/rce-in-clawdbot-the-cves-the-real-kill-chains-and-the-fixes-you-can-prove/