The latest research into Fluent Bit should make any cloud or AI infrastructure engineer a little uncomfortable. Five new CVEs in the popular logging and metrics agent can be chained to bypass authentication, write arbitrary files via path traversal, overflow a stack buffer, and silently manipulate tags on the wire. In the right conditions, that moves you all the way from unauthenticated log injection to remote code execution and full telemetry hijacking. (The Hacker News)
This is not a niche component. Fluent Bit is embedded in billions of containers and has been deployed more than 15 billion times, with millions of downloads every week. It sits on Kubernetes nodes, on managed Kubernetes offerings from hyperscalers, and in AI clusters that ship GPU node logs back to centralized systems. (Oligo Security)
If you care about penetration testing, automated security validation, or AI infrastructure safety, you now have to treat Fluent Bit as part of your attack surface, not just plumbing.
What Fluent Bit Actually Does and Why That’s a Problem
Fluent Bit is a compact telemetry agent for collecting, processing, and forwarding logs and metrics. It accepts data from inputs such as in_tail, in_http, in_splunk, in_elasticsearch, in_docker, and in_forward, transforms the data, then routes it to outputs like file, forward, elasticsearch, kafka, or cloud vendor endpoints.
Two properties make Fluent Bit attractive to attackers:
- It runs everywhere. SecurityWeek, CSO Online, and others highlight that Fluent Bit is now a default component in many managed Kubernetes stacks and cloud platforms—if you deploy containers at scale, you probably have it, often many times over. (eSecurity Planet)
- It often runs with broad privileges. To read host logs and container logs efficiently, it is frequently deployed as a DaemonSet with hostPath mounts and access to sensitive directories. In legacy or misconfigured environments it may even run as root.
That combination—omnipresent and privileged—means that a logic bug in the logging layer can quickly become a control point for the whole cluster.
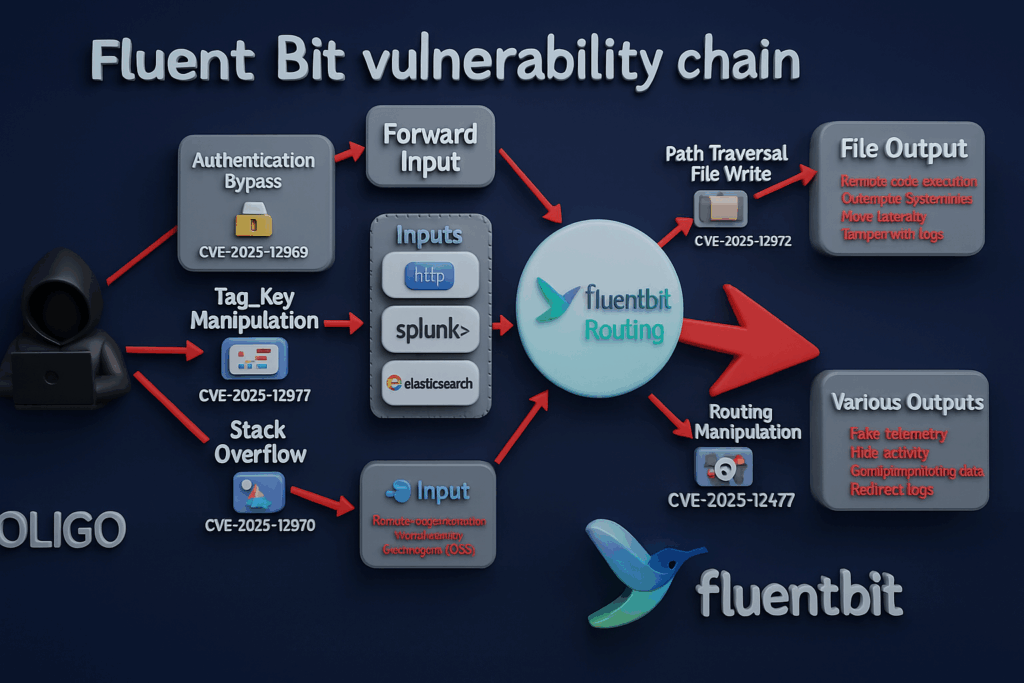
The Current Fluent Bit Vulnerability Chain
Researchers at Oligo Security and CERT/CC disclosed a chain of five vulnerabilities affecting Fluent Bit, now tracked in VU#761751 and multiple CVE records. (Oligo Security)
Summary of the Five CVEs
| CVE | Component | Core flaw | Primary impact |
|---|---|---|---|
| CVE-2025-12972 | out_file plugin | Uses unsanitized tag values to derive output filenames; when File is omitted, path traversal sequences like ../ in tags are honored | Arbitrary file write/overwrite outside intended directory; log tampering and potential RCE when combined with executable or config paths (CVE) |
| CVE-2025-12970 | in_docker input | extract_name() copies container names into a fixed-size stack buffer without length checks | Stack buffer overflow; attacker who can create or name containers can crash the agent or execute code on the host (Oligo Security) |
| CVE-2025-12969 | in_forward input | security.users authentication is not consistently enforced under certain configs | Authentication bypass: remote attacker with network access can send unauthenticated data over Forward, injecting forged logs and flooding systems (NVD) |
| CVE-2025-12977 | tag derivation | Improper validation of tags derived from user-controlled fields; allows newlines, traversal sequences, control characters | Corrupts downstream logs and parsing; can help disguise activity or break analytics pipelines (CERT Coordination Center) |
| CVE-2025-12978 | in_http, in_splunk, in_elasticsearch inputs | tag_key validation fails to enforce exact key-length matching; accepts tag prefixes as matches | Tag spoofing and routing manipulation: crafted inputs can reroute records to unintended destinations (NVD) |
Security articles from eSecurity Planet, CSO Online, and others all emphasize the same theme: these are data-plane vulnerabilities that attack the way Fluent Bit handles tags, filenames, and input authentication, not just its management surface. (eSecurity Planet)
How an Attacker Actually Chains These Bugs
Step 1 – Get a Foot in the Telemetry Plane
Most scenarios assume the attacker has network access to a Fluent Bit input (e.g., Forward, HTTP, Splunk, or Elasticsearch ingress), or the ability to influence container names via a CI/CD pipeline or compromised registry. CERT/CC explicitly warns that many of these flaws require “network access to the Fluent Bit instance,” which in cloud-native environments often means “anything in the VPC or cluster that can speak to the logging DaemonSet.” (CERT Coordination Center)
Step 2 – Turn Tags into a Write-What-Where Primitive (CVE-2025-12972)
The path traversal bug in out_file is arguably the most dangerous. By default, many operators configure the output with a Path but omit File, letting Fluent Bit synthesize filenames from tags. Because tag values are not sanitized when constructing the filename, an attacker who can control tags can inject ../ sequences to walk up directories and write logs into arbitrary locations. (CVE)
Once you can write arbitrary files and partially control their contents, you can:
- Overwrite shell scripts, cron jobs, or systemd unit files.
- Drop web shells or config fragments in directories that are later loaded by other services.
- Tamper with existing logs to erase traces of the intrusion.
Several analyses point out that in realistic deployments this goes beyond integrity issues and can lead to full remote code execution if those overwritten files are executed. (The Register)
Step 3 – Grab Code Execution on the Agent (CVE-2025-12970)
The stack overflow in in_docker gives attackers who can influence container names a more direct route. The extract_name() helper copies container names into a fixed 256-byte stack buffer without bounds checking; a name longer than 256 bytes overflows the buffer. (eSecurity Planet)
From an exploitation standpoint, you get a primitive on the same host where Fluent Bit runs—which is usually the node where multiple workloads are scheduled. Oligo and CSO both note that taking over the logging agent lets attackers hide their activity, plant backdoors, and pivot deeper into the cluster. (Oligo Security)
Step 4 – Hide in Plain Sight with Tag Manipulation (CVE-2025-12977 & 12978)
With the file-write and overflow primitives in place, the tag-related CVEs provide stealth:
- CVE-2025-12978 allows tag spoofing by treating a prefix as a full match in
tag_keyvalidation. That lets a malicious record masquerade as if it came from a trusted component. (NVD) - CVE-2025-12977 lets attackers inject control characters and newlines into tags derived from user-controlled fields, confusing downstream parsers and fusing multiple log events. (Malware Analysis, News and Indicators)
Combine these and you have the ability to reroute, reshape, and selectively corrupt the logs that defenders rely on.
Step 5 – Exploit Forward Authentication Gaps (CVE-2025-12969)
Finally, CVE-2025-12969 cuts a hole in the perimeter. When in_forward is configured with security.users in certain ways, the plugin fails to actually enforce authentication. From the outside it looks locked down; in practice, anyone with network access to the Forward port can send logs. (NVD)
That makes it trivial to inject forged events, flood alerting systems, or send benign “everything is OK” heartbeats while a real attack runs elsewhere.

Why This Matters Specifically for AI and Cloud-Native Stacks
If you run AI workloads, especially GPU-heavy LLM and inference clusters, Fluent Bit is often scraping logs from nodes that also host model servers, vector DBs, or agent runtimes. A compromised logging agent close to those workloads is a natural jumping-off point.
These new flaws also follow on from older issues such as CVE-2024-4323 “Linguistic Lumberjack”, a bug in Fluent Bit’s HTTP server that enabled denial of service and potential information disclosure. Multiple vendors have started to characterize Fluent Bit’s plugin and tag handling as a recurring weak spot rather than a one-off mistake. (Botcrawl)
In other words, if your threat model already includes supply-chain and lateral movement against your LLM infrastructure, Fluent Bit now belongs in the same “high-value” bucket as your ingress controller or service mesh.
Detection and Triage: Where to Start
Inventory Your Fluent Bit Footprint
In Kubernetes, you can quickly identify all pods running Fluent Bit and then query their versions:
# List pods and container images containing 'fluent-bit'
kubectl get pods -A -o jsonpath='{range .items[*]}{.metadata.namespace}{" "}{.metadata.name}{" "}{.spec.containers[*].image}{"\\n"}{end}' \\
| grep -i 'fluent-bit'
# Check version inside a specific pod
kubectl exec -n logging fluent-bit-abc123 -- fluent-bit --version
Compare what you find against your distribution’s release notes and the versions that contain fixes. CERT/CC and JPCERT both reference 4.1.0+ as including remediations for the five-CVE chain; many vendors are standardizing on 4.1.1. (CERT Coordination Center)
Look for Behavioral Signals
Even before patching, you can scan for:
- Unexpected Fluent Bit crashes or restart storms (possible overflow or malformed input).
- Sudden changes in
fileoutput locations or the appearance of log files in unusual directories. - Tags containing
../, newlines, or non-printable characters. - Forward connections from unusual IP ranges or unauthenticated peers.
These are weak signals by themselves, but stacked together they tell you whether the logging plane is already under pressure.
Remediation and Hardening: Not Just a Version Bump
Patch to Safe Versions
The non-negotiable step is to upgrade to vendor builds that incorporate fixes for CVE-2025-12969, 12970, 12972, 12977, and 12978—typically Fluent Bit 4.1.1 or later. Check your cloud provider’s release notes or the upstream Fluent Bit GitHub releases to confirm. (CERT Coordination Center)
Rollouts should be staged just like any other critical infrastructure component: start with a non-prod cluster, validate that log routing and volume look sane, then push across environments.
Fix Risky Configuration Patterns
Patching fixes the immediate bugs, but secure configuration is what prevents the next round from turning into the same story.
- Stop deriving filenames from tags. Use explicit
Filenames and a tightly controlledPathforout_file. - Turn on TLS and authentication for network inputs following Fluent Bit’s transport security guidance.
- Mount configs as read-only. Avoid giving Fluent Bit write access to directories that hold scripts, unit files, or binaries.
- Constrain tag sources. Don’t feed user-supplied strings directly into tags or
tag_keyfields without length and character whitelists.
A safer file output might look like this:
[OUTPUT]
Name file
Match kube.*
Path /var/log/fluentbit/out
File kube.log # explicit, not derived from tag
Format json_lines
Rotate_Wait 60
Bringing Fluent Bit into Automated Pentesting with Penligent
For a human-in-the-loop agentic pentest platform like Penligent, Fluent Bit is exactly the kind of asset that should be modeled explicitly in the attack graph rather than treated as background noise.
In a typical Penligent engagement against a Kubernetes or AI cluster, the workflow could look like this:
Discovery and Exposure Mapping
Agents first enumerate Fluent Bit instances, versions, and plugin configurations. Using CVE and CERT feeds, they flag nodes where in_forward, in_docker, or out_file are present in versions affected by the five-CVE chain or older issues like CVE-2024-4323. (CERT Coordination Center)
Controlled Exploitation in an Isolated Replica
Rather than firing exploit traffic at production, Penligent can clone representative logging nodes into a sandbox environment. There, agents exercise:
- Tag-based path traversal against
out_file. - Overlong container names targeting
in_docker. - Spoofed Forward traffic without credentials.
Outputs such as agent crashes, changed file paths, and log corruption are captured as evidence, not just theoretical findings.
Evidence-First Reporting and Hardening Playbooks
Finally, Penligent aggregates everything into a report your SRE and platform teams can act on: which clusters are exposed, which configs are dangerous, how far an attacker can get today, and what the system looks like after upgrading images and tightening config. That shifts the conversation from “Fluent Bit has CVEs” to “Here is exactly how Fluent Bit can be abused in our environment, and here is what we’ve done to close those paths.”
Key Takeaways
Fluent Bit is no longer a background detail. With CVE-2025-12969, 12970, 12972, 12977, and 12978, the logging agent itself becomes a viable entry point for remote attackers, and a powerful tool for hiding their tracks once they’re in. (CERT Coordination Center)
For engineers working on cloud-native or AI platforms, the message is simple:
- Inventory and patch your Fluent Bit deployments.
- Treat telemetry agents as tier-1 assets in your threat model.
- Use automated, evidence-driven testing—whether with Penligent or your own tooling—to validate that fixes and hardening steps actually work.
The logs are no longer just observers. In 2025, the logging layer is part of the battlefield.


