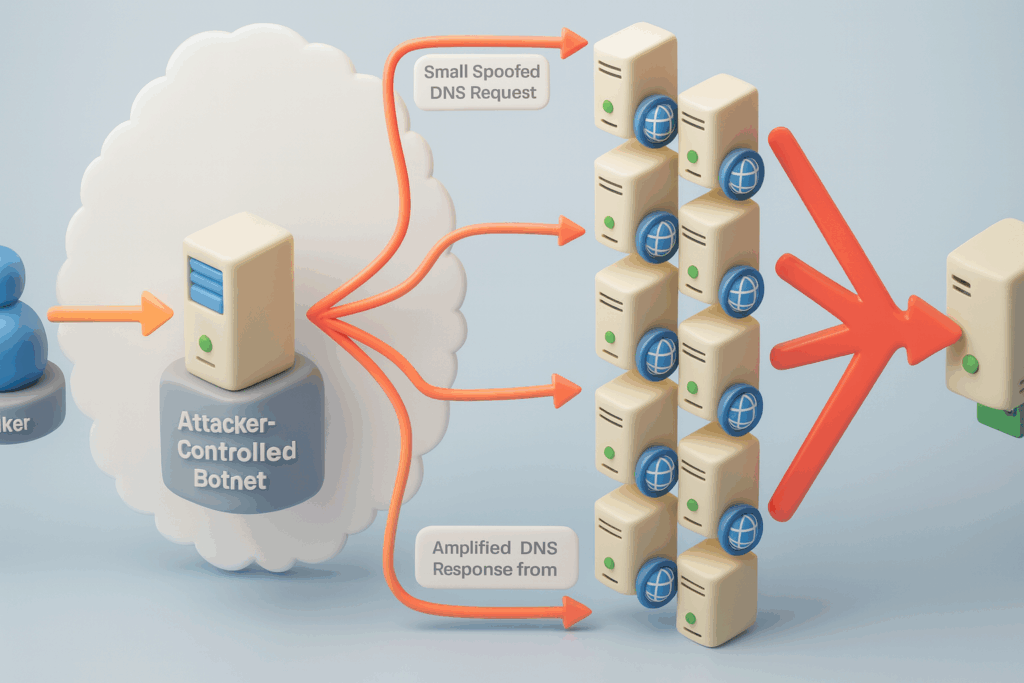
Une attaque par amplification DNS est un type d'attaque par déni de service distribué (DDoS) dans lequel un attaquant envoie une petite requête DNS usurpée à un serveur DNS ouvert, ce qui amène le serveur à renvoyer une réponse massivement plus importante à une victime qui ne se doute de rien. En d'autres termes, une requête minuscule déclenche une réponse énorme qui inonde la cible d'un trafic écrasant. Cette technique est dangereuse car elle ne nécessite qu'un minimum de ressources de la part de l'attaquant, elle est extrêmement difficile à tracer en raison de l'usurpation d'adresse IP et elle peut générer des centaines de fois plus de trafic que ce qui a été envoyé à l'origine, ce qui entraîne des pannes massives pour les entreprises, les fournisseurs d'accès à Internet et les services en ligne cruciaux.
Comprendre l'amplification du DNS et les attaques DDoS par réflexion
À la base, une attaque par amplification DNS s'appuie sur deux caractéristiques de longue date du système de noms de domaine : Le DNS utilise par défaut le protocole UDP, qui ne valide pas l'adresse IP source. Lorsqu'un attaquant falsifie l'adresse IP de la victime comme source d'une requête DNS, tout serveur DNS qui répondra enverra sans le savoir la réponse à la victime.
Les serveurs DNS sont donc des "réflecteurs" idéaux. L'attaquant n'a pas besoin de contacter directement la victime. Au contraire, les résolveurs ouverts et les serveurs DNS mal configurés deviennent des canons à trafic. Étant donné que les réponses DNS - en particulier ANY ou les réponses liées au DNSSEC - contiennent beaucoup plus de données que les requêtes initiales, l'attaquant bénéficie d'un effet d'amplification, multipliant son impact sans presque aucun effort supplémentaire.
Comment fonctionne l'amplification DNS : Un aperçu technique
Bien que l'attaque soit simple sur le plan conceptuel, les mécanismes du trafic sont élégants et malveillants. Une attaque typique se déroule en quatre étapes :
- L'attaquant usurpe l'adresse IP de la victime.
- L'attaquant envoie des milliers (ou des millions) de requêtes DNS à des résolveurs DNS ouverts.
- Ces résolveurs renvoient des réponses DNS volumineuses à l'adresse usurpée.
- Le flot de données non sollicitées submerge la victime.
Une requête falsifiée typique peut ressembler à ceci au niveau des paquets :
yaml
Source IP : Victime IP (spoofed)
IP de destination : 8.8.8.8
Protocole : UDP/53
Type de requête : ANY
Requête : example.com
L'attaquant peut n'envoyer qu'une requête de 60 octets, mais le résolveur DNS peut renvoyer plusieurs kilo-octets de données - parfois même des dizaines de milliers d'octets dans des formes avancées d'amplification.
C'est dans cet échange asymétrique que réside le véritable danger : l'attaquant n'investit presque rien, mais c'est la victime qui paie le prix.
Facteurs d'amplification : Pourquoi la méthode "Small In, Huge Out" est dévastatrice
Les différents types de requêtes DNS entraînent des niveaux d'amplification différents. La disparité peut être stupéfiante :
| Type de requête | Taille de la demande | Taille de la réponse | Facteur d'amplification |
|---|---|---|---|
| Un dossier | 60 octets | 512 octets | ~8.5x |
| ANY | 60 octets | 3 500 octets | ~58x |
| DNSSEC | 70 octets | 4 000+ octets | ~57x |
| NXNSAttack | 60 octets | 40 000+ octets | 600x+ |
Ce qui rend ce phénomène particulièrement menaçant, c'est l'échelle. Un réseau de zombies n'utilisant qu'une bande passante modeste - disons 100 Mbps - peut générer plusieurs Gbps de trafic de réponse DNS sortant pendant l'amplification. Cloudflare et CISA ont documenté plusieurs attaques DDoS réelles dépassant des centaines de Gbps par le seul biais de l'amplification DNS.
Simulation d'une attaque par amplification du DNS dans un laboratoire contrôlé
Pour comprendre comment les attaquants opèrent, les chercheurs et les testeurs de pénétration simulent souvent l'amplification DNS dans des environnements isolés et légalement autorisés. Une simple preuve de concept utilisant Python et Scapy illustre la facilité avec laquelle il est possible de déclencher une amplification :
python
from scapy.all import *
target = "192.168.1.10" # Victime (IP usurpée)
dns_server = "192.168.1.53" # Résolveur DNS ouvert
packet = IP(src=target, dst=dns_server)/UDP(dport=53)/DNS(rd=1, qd=DNSQR(qname="example.com", qtype="ANY"))
for i in range(1000) :
send(packet, verbose=0)
print("Simulation d'amplification DNS envoyée.")
Ce texte met l'accent sur deux dures réalités :
- L'attaquant ne contacte jamais directement la victime.
- Le serveur DNS devient le complice involontaire.
- Une bande passante minimale peut avoir un impact massif.
C'est un exemple frappant de l'asymétrie réelle de l'attaque.
Pourquoi l'amplification du DNS est-elle si dangereuse pour les organisations modernes ?
Le risque va bien au-delà des pics de trafic. L'amplification du DNS a des conséquences systémiques :
- Faible coût pour les attaquants: Aucune infrastructure à large bande n'est nécessaire.
- Attribution difficile: L'usurpation d'adresse IP masque l'identité de l'attaquant.
- Surface d'attaque globale: Des millions de résolveurs ouverts restent exposés.
- Dommages collatéraux: Les fournisseurs de DNS, les CDN, les plateformes en nuage et les FAI subissent des perturbations en aval.
Lors d'une attaque par amplification à grande échelle, les organisations signalent souvent :
| Métrique | Trafic normal | Pendant l'attaque |
|---|---|---|
| DNS QPS | 1,200 | 480,000 |
| Sortie Mbit/s | 40 Mbps | 2,9 Gbps |
| ANY Query Ratio | <1% | 86% |
| Principales adresses IP sources | Prévisible | Spoofed / Randomized |
Même les réseaux bien conçus peuvent s'effondrer sous ce volume.
Détection précoce de l'amplification DNS : Journaux, règles et modèles de trafic
Parce que le trafic semble "légitime" (réponses aux requêtes DNS), les pare-feu traditionnels passent souvent à côté des attaques par amplification. La détection nécessite une surveillance basée sur le comportement.
Règle de détection des suricates
Cette règle signale les hausses suspectes des requêtes ANY :
yaml
alert dns any any -> any any (
msg : "Possible DNS Amplification Attack" ;
dns_query_type == ANY ;
seuil:type both, track by_src, count 50, seconds 1 ;
sid:100001 ;
)
Analyse des journaux DNS avec SQL
Un SIEM permet de détecter instantanément les anomalies :
sql
SELECT source_ip, COUNT(*) as queries
FROM dns_logs
WHERE query_type = 'ANY'
GROUP BY source_ip
AYANT COUNT(*) > 5000 ;
Des pics soudains de requêtes ANY sont souvent le prélude à une attaque de grande envergure.
Défendre contre l'amplification DNS : Techniques pratiques et réalisables
Contrairement à certaines variantes de DDoS, l'amplification DNS peut être considérablement atténuée par une configuration adéquate.
Désactiver la récursivité ouverte dans BIND
lier
options {
récursion non ;
allow-query { trusted ; } ;
};
acl "trusted" {
192.168.1.0/24;
};
La restriction de la récursivité garantit que le serveur DNS ne peut pas être utilisé de manière abusive par l'internet public.
Activer la limitation du taux de réponse (RRL)
lier
limite de débit {
réponses par seconde 5 ;
fenêtre 5 ;
fiche 2 ;
};
Le RRL permet de limiter les réponses répétitives et de réduire considérablement le potentiel d'amplification.
Mise en œuvre de l'anti-spoofing IP (BCP 38) via iptables
bash
iptables -A INPUT -s 10.0.0.0/8 -j DROP
iptables -A INPUT -s 172.16.0.0/12 -j DROP
iptables -A INPUT -s 192.168.0.0/16 -j DROP
Cela permet d'éviter que des plages d'adresses privées falsifiées n'entrent dans le réseau - l'un des vecteurs d'usurpation d'identité les plus courants.
Surveiller les ratios ANY et DNSSEC
Une augmentation du nombre de requêtes ANY est rarement bénigne.
Test de pénétration et validation automatisée avec Penligent
Bien que l'audit manuel soit crucial, l'infrastructure DNS est aujourd'hui trop vaste et trop dynamique pour être testée une fois et oubliée. Des erreurs de configuration, même mineures, peuvent réintroduire un risque d'amplification.
C'est là que des plateformes comme Penligentun système intelligent de tests de pénétration automatisés, offrent une valeur significative :
Analyse de la mauvaise configuration du DNS
La négligence permet d'identifier automatiquement :
- Résolveurs ouverts exposés au public
- RRL manquant ou mal configuré
- Risques d'amplification des DNSSEC
- Politiques de récursivité permettant des abus
Menaces futures : De l'attaque NXNSA à la rotation du réflecteur
Des recherches récentes mettent en évidence une tendance inquiétante : les attaquants vont au-delà de l'amplification ANY classique. Des techniques telles que NXNSAttack exploitent les chaînes de référence pour générer une amplification extrême, tandis que la "rotation des réflecteurs" utilise de vastes pools de serveurs DNS pour éviter le filtrage et la mise sur liste noire.
La conclusion est claire : l'amplification évolue et les défenseurs doivent évoluer avec elle.
Conclusion
Une attaque par amplification DNS est l'une des formes les plus efficaces et les plus destructrices de DDoS, car elle utilise une infrastructure légitime contre des cibles innocentes. Elle transforme les serveurs DNS en amplificateurs, transforme les petites requêtes en inondations massives et dissimule l'attaquant derrière de fausses adresses IP. La combinaison d'un faible effort, d'un impact élevé et d'une évolutivité globale en fait une menace que les organisations modernes ne peuvent ignorer.
La bonne nouvelle, c'est qu'avec une configuration adéquate - désactivation de la récursivité ouverte, activation du RRL, application de l'anti-spoofing, surveillance des anomalies du trafic et tests réguliers de la posture DNS - les organisations peuvent réduire considérablement leur exposition. Pour les environnements où l'échelle DNS est importante ou en constante évolution, des plateformes automatisées comme Penligent peuvent aider à garantir que les vulnérabilités ne réapparaissent pas sans avoir été détectées.
Dans un monde où le temps de fonctionnement, la disponibilité et la confiance définissent le succès de l'entreprise, la sécurisation des DNS n'est pas facultative, elle est fondamentale.