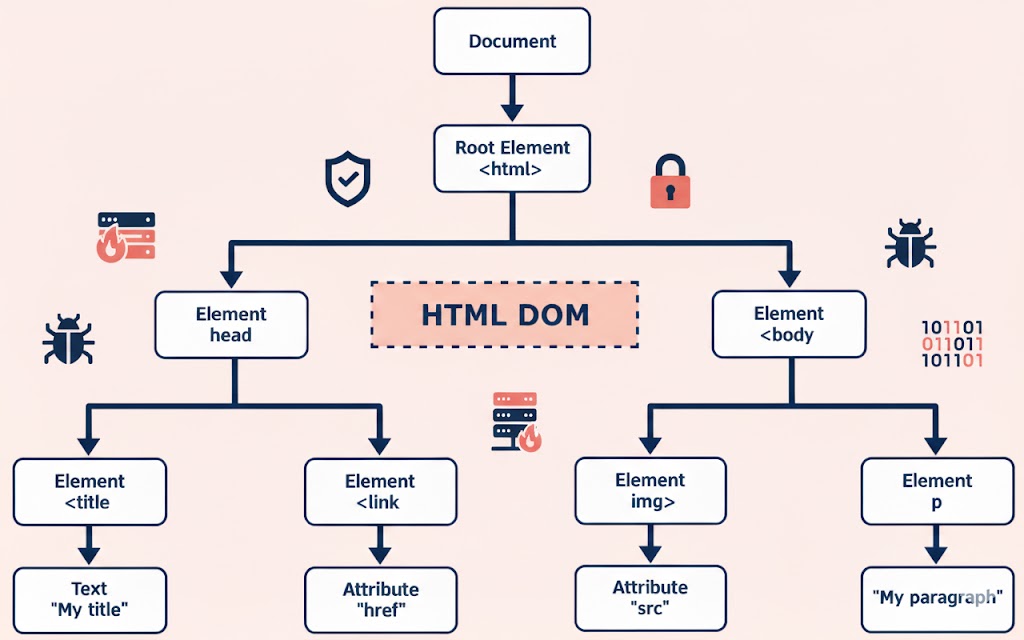
In the modern web ecosystem, the DOM (Document Object Model) plays a pivotal role in enabling interactive and dynamic user experiences. Think of the DOM as a map or blueprint that a web browser creates when it loads a webpage. Every element you see — headings, paragraphs, buttons, images — is represented as a node within this hierarchical structure. Developers can use JavaScript to navigate this map, change elements, add new ones, or respond to user actions like clicks and form submissions. For example, clicking a “Show More” button might trigger a script that modifies the DOM to display hidden text. Because the DOM is interactive and constantly updated, it acts as the interface between the static HTML code and the dynamic behavior users experience, driving the interactive features we take for granted.
However, this same interactivity can open the door to vulnerabilities that are uniquely tied to client-side code. For security professionals — whether penetration testers or engineers tasked with defending corporate assets — understanding DOM vulnerabilities is essential not only for exploitation but also for prevention.

The DOM in a Security Context
In secure coding, it’s crucial to monitor how data flows inside the DOM. An attacker-controlled source — such as a URL parameter (מיקום.חיפוש), a cookie (document.cookie), or referrer information (document.referrer) — can become dangerous when injected into an insecure sink, like innerHTML או eval(). The chain from source to sink is what enables DOM-based vulnerabilities.
Common DOM Vulnerabilities
| סוג הפגיעות | Example Sink | תיאור | Potential Impact |
|---|---|---|---|
| XSS מבוסס DOM | document.write()element.innerHTML | Injecting attacker-controlled data into HTML without sanitization allows arbitrary JavaScript execution. | Theft of cookies, session hijacking, malicious content injection. |
| Open Redirection | window.location | Improper URL handling lets attackers redirect users to malicious sites. | Phishing attacks, malware distribution, brand trust damage. |
| Cookie Manipulation | document.cookie | Attacker can overwrite or steal session cookies via unsafe JavaScript code. | Account takeover, session hijacking, impersonation. |
| JavaScript Injection | eval() | Executes attacker-provided string as JavaScript code. | Full client-side compromise, data exfiltration. |
| Document-domain Manipulation | document.domain | Changing domain to bypass same-origin restrictions. | Cross-domain data leaks, privilege escalation. |
| WebSocket URL Poisoning | WebSocket() | Supplying malicious endpoints for WebSocket connections. | Interception of data streams, unauthorized actions. |
| Link Manipulation | element.src | Attacker modifies resource links to load malicious code or steal data. | Malware injection, tracking, phishing landing pages. |
| Web Message Manipulation | postMessage() | Sending crafted messages to manipulate target frame/window. | Data leakage, cross-origin attacks. |
| Ajax Request-header Manipulation | setRequestHeader() | Attacker controls HTTP request headers in client-side code. | API misuse, CSRF-like exploitation. |
| Local File-path Manipulation | FileReader.readAsText() | Reading local files through client-side JS without proper restrictions. | Leakage of sensitive local data. |
| Client-side SQL Injection | ExecuteSql() | Passing unsanitized data to client-side DB queries. | Data theft, DB manipulation. |
| HTML5 Storage Manipulation | sessionStorage.setItem() / localStorage.setItem() | Storing malicious payloads in browser storage for later execution. | Persistent XSS, unauthorized client data access. |
| Client-side XPath Injection | document.evaluate() | Injection into XPath queries can give attacker access to XML data. | Data leaks, manipulation of XML-based app logic. |
| Client-side JSON Injection | JSON.parse() | Parsing tampered JSON from untrusted sources allows arbitrary object injection. | Data overwrite, logic manipulation. |
| DOM-data Manipulation | element.setAttribute() | Setting attributes with untrusted data can trigger malicious behaviors. | XSS, clickjacking, logic bypass. |
| Denial of Service (DoS) | RegExp() | Large or malicious regex patterns freeze the browser. | Application downtime, degraded performance. |
How DOM Vulnerabilities Are Found
Security teams typically employ a blend of strategies.
- Active scanning, using tools such as Burp Suite or OWASP ZAP, allows testers to simulate and observe unsafe DOM interactions.
- Passive discovery involves trawling resources like Shodan, ZoomEye, and PublicWWW, or even historical snapshots in the Wayback Machine, to uncover sensitive data hidden in the DOM layer.
- Automated Regex & AI Analysis, combines pattern matching for known credentials with AI-driven analysis that maps Source → Sink flows, dramatically shortening the time between detection and remediation.
Defending Against DOM Vulnerabilities
Strong defenses begin with disciplined input validation — ideally through a whitelist — to ensure only trusted data reaches the DOM.
Encoding strategies must be tailored to context: HTML encoding for page output, JavaScript escaping for script injection points, and URL encoding for link construction.
API keys, when they absolutely must appear in front-end code, should be locked down using referrer and origin checks, IP restrictions, and rate limits.
Teams should conduct a DOM review just before deployment, removing secrets and unsafe code, and revoking any credentials that have ever been exposed, even in archived snapshots.
Elevating DOM Security with Penligent
Traditionally, running a thorough DOM security audit required stitching together numerous tools — Nmap for discovery, Burp Suite for injection testing, SQLmap for exploitation — and then manually reviewing each finding for accuracy.
Penligent changes this by allowing testers to describe their goal in plain English. A request like “scan this website for DOM vulnerabilities” triggers an intelligent workflow: the AI integrates more than two hundred security tools, including Nmap, Burp Suite, SQLmap, etc., to conduct targeted scans on potential Source → Sink chains, validate each finding to eliminate false positives, rank them by severity. For both seasoned security experts and newcomers, this transforms DOM audits from multi-day manual marathons into streamlined, highly-accurate processes completed in hours or even minutes.