In modern cybersecurity, malicious definition refers to any behavior, code, or intent designed to harm systems, networks, data, or users—purposefully violating integrity, confidentiality, or availability. This definition is foundational because it underpins everything from threat modeling to automated detection, response engineering, and adversarial playbooks in penetration testing. In simple terms, malicious actions aren’t accidental glitches—they are intentional operations crafted to undermine security goals. N2K CyberWire
This article explores how “malicious” is understood in technical contexts, how it plays out in real attacks, how defenders can classify and mitigate malicious patterns, and how AI-driven security tools such as पेनलिजेंट can help engineers detect and respond to malicious activity at scale.
What “Malicious” Really Means in Cybersecurity
The word “malicious” in plain English denotes ill-intentioned or harmful intent, but in cybersecurity, it specifically refers to actions that compromise the expected functioning or trust model of systems. According to a widely accepted industry glossary, malicious behavior relates to hostile actions against systems, data, or networks that cause harm, loss, or unauthorized access. N2K CyberWire
This definition separates malicious activity from accidental failures or benign errors. For example, a software bug that accidentally deletes logs is harmful but not malicious; malicious means there is a deliberate strategy to harm or exploit. That distinction is critical for building accurate threat models and deploying effective automation to catch real threats.
Malicious vs Non-Malicious Failures
| Category | विवरण | उदाहरण |
|---|---|---|
| Malicious | Intent to harm or exploit | Malware installation, data exfiltration |
| Unintentional error | Bug or configuration mistake | Accidental data loss due to logic error |
| Unknown anomaly | Behavior needing investigation | Unexpected spike in CPU usage |
By defining malicious behavior clearly, security teams can refine detection rules and reduce false positives.
Common Manifestations of Malicious Behavior
A primary expression of malicious intent in digital environment is malware, a contraction of “malicious software,” designed to disrupt systems, steal data, or provide unauthorized access. Malware functions as a class of threats that embody hostile intent and range from simple viruses to advanced persistent threats. eunetic.com
Types of Malicious Software and Attacks
| Threat Type | Malicious Function | उदाहरण |
|---|---|---|
| Virus | Self-replicates, infects host files | Classic file infector |
| Worm | Spreads across networks autonomously | Conficker |
| Trojan | Masquerades as benign software | RAT delivery |
| Ransomware | Encrypts data, demands ransom | WannaCry |
| Spyware | Steals data silently | Keylogging spyware |
| Botnet agent | Enables remote control | DDoS botnets |
Malicious behavior also appears in non-software threats like phishing (social engineering to deceive users), malicious URLs (designed to host or deliver malware), insider abuse, or distributed denial-of-service attacks intended to overwhelm systems.
How Malicious Actions Unfold: From Intent to Exploit
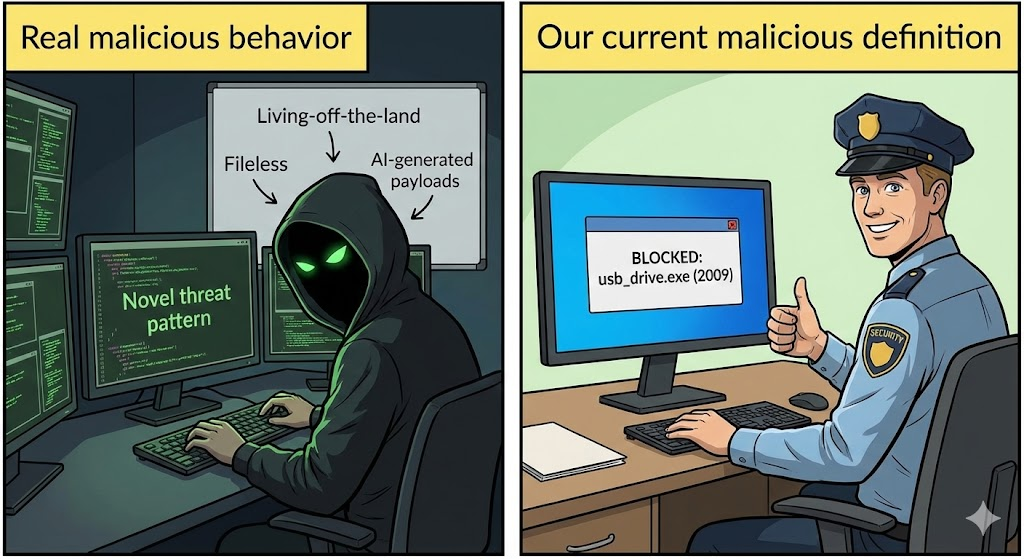
Understanding malicious intent is abstract; seeing how it unfolds in real attacks is concrete. Threat actors design malicious operations by combining various tactics, including exploitation of vulnerabilities, social engineering, and covert persistence. Modern malware often uses obfuscation, polymorphism, and anti-sandbox techniques to evade detection, making traditional defenses insufficient on their own. techtarget.com
CVE Case Study: CVE-2024-3670 (Example)
A recent high-severity vulnerability (CVE-2024-3670) in a major enterprise web application allowed attackers to deploy arbitrary file upload functionality without proper sanitization. Attackers could upload a web shell—a malicious script—leading to remote code execution. This malicious payload then enabled lateral movement and persistent access within the victim environment.
php
// Unsafe file upload (malicious exploit risk) if ($_FILES['upload']) {move_uploaded_file($_FILES['upload']['tmp_name'], "/var/www/html/" . $_FILES['upload']['name']); }
Defensive mitigation: Always validate file types, implement file scanning, and restrict upload paths.
Distinguishing Malicious Patterns from Normal Activity
Malicious intent is best captured not by single signals but by patterns. Security teams combine multiple indicators—unexpected network connections, unauthorized file changes, unusual process spawning, etc.—to detect true malicious activities.
Behavioral Indicators
- Unexpected outbound connections to known malicious domains
- Unusual file system changes (encrypted files, rogue executables)
- Privilege escalation patterns
- Persistence mechanisms (registry run keys, cron jobs, service installations)
Behavioral analysis tools use statistical or ML-based methods to separate benign anomalies from genuinely malicious patterns.
Attack & Defense Code Samples: Malicious Patterns
Below are practical examples illustrating malicious activity and secure defensive coding.
- SQL Injection Exploit
Malicious pattern:
sql
SELECT * FROM users WHERE username = '" + userInput + "';";
This allows attacker vectors such as ' OR '1'='1 to bypass authentication.
Secure defense (parameterized query):
अजगर
cur.execute("SELECT * FROM users WHERE username = %s", (userInput,) )
- Command Injection
Malicious pattern:
अजगर
import os os.system("cat " + filename) # Dangerous if filename crafted by user
Defensive pattern (whitelist):
अजगर
allowed_files = {"readme.txt", "config.json"}if filename in allowed_files: os.system(f"cat {filename}")
- क्रॉस-साइट स्क्रिप्टिंग (XSS)
Malicious:
एचटीएमएल
<script>alert('xss')</script>
Defense (escaping):
जावास्क्रिप्ट
res.send(escapeHtml(userInput));
- Arbitrary File Write
Malicious attempt:
जावास्क्रिप्ट
fs.writeFileSync("/etc/passwd", userControlledContent);
Defense:
जावास्क्रिप्ट
const safePath = path.join("/data/safe", path.basename(filename));
Detection Strategies for Malicious Activity
Modern detection uses layered approaches:
- Signature-based detection: Recognizes known malicious patterns.
- Behavioral detection: Monitors runtime anomalies.
- Sandbox analysis: Executes suspicious code in isolation to observe malicious behavior.
- Threat intelligence integration: Uses updated feeds to detect known IOCs.
These methods help catch both known and novel malicious tactics.
The Role of Automation and AI in Detecting Malicious Patterns
As threats have become more adaptive, relying solely on static signatures is no longer viable. AI and machine learning help detect zero-day and obfuscated malicious patterns by correlating unusual behavior across telemetry sources and learning typical benign vs malicious profiles.
For example, advanced Malware-as-Service campaigns increasingly hide payloads in encrypted channels and use AI-generated phishing lures to trick users, making proactive detection essential.
Penligent: AI-Powered Malicious Detection and Response
In environments where malicious threat surfaces are large and dynamic, manual analysis alone can’t keep pace. पेनलिजेंट leverages AI to automate and scale malicious activity detection and remediation workflows:
- Automated analysis of code paths for embedded malicious patterns.
- Behavioral profiling to spot deviations consistent with malicious intent.
- Prioritized alerts based on risk scoring and potential impact.
- Integration into CI/CD and DevSecOps pipelines to catch malicious patterns early.
By combining domain expertise with AI-driven heuristics, Penligent helps security teams stay ahead of threat actors and reduce mean time to detection and response.
In practical terms, this means a security engineer can focus on high-value investigations while the system sifts through billions of events to detect true threats using contextual analysis.
Building Defensive Posture Against Malicious Threats
Defending against malicious activity isn’t just about specific tools—it’s about architectural discipline:
- Network segmentation limits lateral movement.
- Least privilege reduces the blast radius of breaches.
- Continuous monitoring ensures early detection.
- Incident response playbooks reduce recovery time.
These measures work in concert with automated detection to defend against both opportunistic and targeted malicious activity.
Conclusion: Malicious Definition as Core Security Knowledge
Understanding the malicious definition in cybersecurity is not just academic—it’s practical and actionable. It guides threat modeling, detection heuristics, defensive coding, and incident response workflows. Differentiating malicious intent from error allows teams to allocate resources efficiently, prioritize genuine threats, and build robust mitigation strategies. Pairing this conceptual grounding with modern automation platforms like पेनलिजेंट arms security engineers with both breadth and depth in defending against evolving malicious threats.