Why this Firefox “0-day” matters even if you don’t run Nightly
This incident is a rare gift to defenders: a real-world browser RCE chain rooted in a single character—& typed where | was intended—that we can study end-to-end with public artifacts. It landed in Firefox 149 Nightly, was caught and fixed quickly, और did not ship to stable releases. (Cyber Security News)
So why should a security team care?
Because the failure mode is not exotic. It is the kind of bug you can produce in any high-performance runtime that uses:
- pointer tagging (low-bit markers),
- multiple layouts for the “same” logical object,
- moving GC + JIT cooperation,
- and “obvious” bitwise code that reviewers read past.
This write-up focuses on operationally useful facts: what broke, why it broke, how to verify you’re not exposed, and how to prevent the pattern in your own codebases—without publishing weaponized exploitation steps.
The verified timeline
The public researcher write-up and the Firefox repo commits line up on the core sequence: the buggy change was introduced, independently found, and then fixed by a minimal diff that also added an assertion to lock the invariant in place. (Kqx)
| Event | Date | प्रमाण |
|---|---|---|
| Bug introduced in Firefox source | 2026-01-19 | Commit fcc2f20e35ec message and diff context (GitHub) |
| Researcher analysis published | 2026-02-04 | “How a single typo led to RCE in Firefox” (Kqx) |
| Fix landed | 2026-02-09 | Commit 05ffcde… changes & 1 → ` |
| Reported impact | Firefox 149 Nightly only (not release) | Stated in public reporting and write-up (Cyber Security News) |
Two Bugzilla reports are referenced, but they are access-restricted (security-sensitive). We can still verify the engineering facts via the public GitHub mirror commits and the public technical write-up. (Bugzilla)
What actually broke: a pointer-tagging invariant collapsed
At the center is one line in js/src/wasm/WasmGcObject.cpp inside the WebAssembly GC array relocation path.
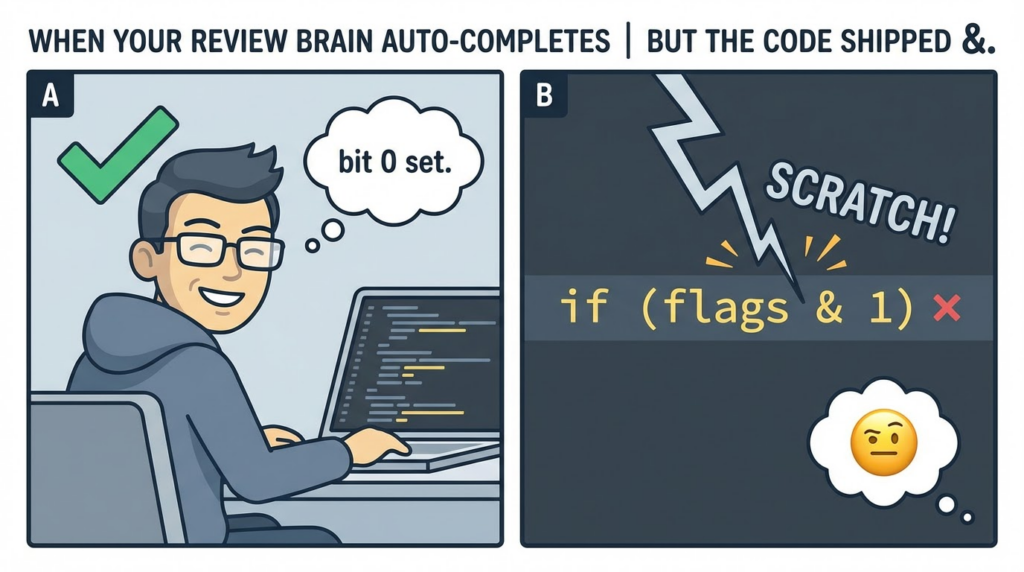
The intent, per the comment, was to store a forwarding pointer with bit 0 set—a common trick to distinguish “this word is a tagged pointer” from “this word is a normal header value.” The vulnerable commit stored:
// Store the forwarding word, with bit 0 set.
oolHeaderOld->word = uintptr_t(oolHeaderNew) & 1;
But for aligned pointers, ptr & 1 is almost always 0, meaning the code wrote zero, not “pointer | 1”. This is described both in the public write-up and the security news summary. (Kqx)
The fix is explicit and source-verifiable:
- adds
MOZ_ASSERT((uintptr_t(oolHeaderNew) & 1) == 0); - changes to
oolHeaderOld->word = uintptr_t(oolHeaderNew) | 1;(GitHub)
That assertion is a quiet admission of what matters: the entire safety of the downstream logic depends on the least significant bit being a reliable marker.
Inline vs Out-of-line: why bit 0 decides “what kind of object this is”
The public write-up explains the two layouts for Wasm GC arrays:
- Inline (IL) arrays: data lives directly after the object.
- Out-of-line (OOL) arrays: object points to a separately allocated block with a header word, then the data payload. (Kqx)
To quickly decide which case it is, the engine reads the word before the data pointer and checks bit 0:
uintptr_t headerWord = header->word;
return (headerWord & 1) == 0;
If your “forwarding pointer marker” mistakenly becomes 0, the system starts treating an OOL case as IL. That mismatch matters because the JIT and GC cooperate to update references when objects move. If the JIT updates the wrong thing (or doesn’t update at all), you’re suddenly in use-after-free territory—which is precisely how modern browser renderer compromises tend to start. (Kqx)
Why this class of bug slips through: the review trap
This is not a “missing bounds check” that static analyzers scream about. It’s the kind of bug that survives because:
- The comment agrees with the reviewer’s brain. The comment says “bit 0 set,” so the eye reads “
| 1” even when the code says “& 1।” - Unit tests can’t easily force the exact moving-GC + optimizing-JIT path. Nightly codepaths, new Wasm GC features, and compiler tiering mean you can miss the “right” state combinations.
- Bitwise operations are low-signal during review. People learn to skim them—until they become security boundaries.
The best proof is the minimal fix: a one-character operator swap plus an assertion. (GitHub)
Impact reality check for defenders
Public reporting states this affected Firefox 149 Nightly and did not ship to stable releases. That matters because the default enterprise fleet is usually on Stable या ESR, not Nightly. (Cyber Security News)
But don’t stop there. There are three practical reasons to still treat it as actionable:
- Developer endpoints sometimes run Nightly or Developer Edition for testing.
- CI environments sometimes embed browser builds (E2E tests, automation rigs).
- A “Nightly-only” bug can still teach you what to monitor: crashes in content processes, unusual Wasm usage patterns, or sudden JIT instability.

What to do now
1) Prove you don’t have Nightly in scope
Start with inventory. Your goal is not “find Firefox,” it’s “find non-standard channels.”
- Detect Firefox channel (Stable/ESR/Nightly) via package metadata, install paths, or update URLs.
- Flag unmanaged browser installs on dev workstations.
If you use device management, enforce policy and make it visible. Mozilla’s enterprise policy documentation is the official starting point. (Mozilla Support)
2) If you must harden aggressively, restrict WebAssembly
In high-security environments, disabling Wasm is sometimes used as a coarse kill-switch. In Firefox, the widely referenced control is javascript.options.wasm in about:config. That’s documented across multiple reputable technical discussions and references. (Information Security Stack Exchange)
Important trade-off: disabling Wasm breaks some legitimate apps (streaming, graphics, heavy web apps). Even Mozilla support threads note real sites failing when Wasm is disabled. (Mozilla Support)
So treat Wasm restriction as:
- short-term containment for a subset of endpoints, or
- a policy for hardened browsing profiles / high-risk roles, not as a default for everyone.
3) Verify the fix is present
If you compile Firefox (or audit a fork), you can verify whether the fix commit is included.
This isn’t about “trust the version string.” It’s about “trust the diff.”
CI and code review hardening: catching & vs | class bugs early
A practical pattern: “bit-tag write must have a symmetric read”
When a system uses bit tagging:
- Writers should use a clear helper:
TagPtr(ptr)rather thanptr | 1. - Readers should use
IsTagged(word)rather thanword & 1.
If you can’t refactor immediately, add a rule that alerts when code does something that looks like:
uintptr_t(ptr) & 1assigned into a “header word”- or “bit 0 set” comment near
& 1
Example: Semgrep rule (C/C++)
rules:
- id: suspicious-pointer-tag-and
message: "Suspicious pointer tagging: '& 1' used where '| 1' is typical. Verify intent."
severity: WARNING
languages: [cpp]
patterns:
- pattern: $X = (uintptr_t)$P & 1;
This does not prove vulnerability; it proves “review this line like it’s a security boundary.”
Example: git grep guardrail
git grep -nE "uintptr_t\\\\([^\\\\)]*\\\\)\\\\s*&\\\\s*1" -- js/src/wasm js/src/jit
Add it as a CI “warning gate” for low-level runtime code.
Threat-model context: this is why Wasm/JIT bugs stay high-leverage
Browser exploitation economics reward memory corruption primitives inside renderer processes. Even when sandboxes exist, renderer compromise is the first domino.
Mozilla’s advisories regularly include “memory safety” and engine issues that are considered potentially exploitable with enough effort—this is not new, and it’s why mature teams treat browser patching as an identity-tier control. (Mozilla)
For additional context on how JIT bugs are operationalized in real competitions, ZDI’s analysis of an IonMonkey renderer compromise is a good reference point for “why the renderer is the battleground.” (Zero Day Initiative)
And for a recent Wasm-GC-adjacent example that did impact release channels, public reporting around CVE-2025-13016 shows how a subtle error in the WebAssembly GC area can sit in production for months—reinforcing why you should invest in guardrails, not just emergency patching. (TechRepublic)
Non-weaponized verification playbook
Evidence you want to collect
| परत | What you check | Output you can show auditors |
|---|---|---|
| Asset coverage | Which endpoints run Firefox; which channel (Stable/ESR/Nightly) | Inventory report + exceptions list |
| Patch / code lineage | If you build/ship a fork: is 05ffcde… included? | Build provenance + commit inclusion proof (GitHub) |
| Control posture | Wasm allowed? JIT settings? policy enforcement? | policies.json / GPO proof + screenshots of about:policies (Mozilla Support) |
| Runtime signals | Crash telemetry, content process crashes, unusual Wasm-heavy sites | SIEM dashboard + incident notes |
Example: enterprise policy enforcement workflow
Mozilla’s official documentation explains how to enforce policies for Firefox in enterprise environments. Use that as your “source of truth” rather than random blog snippets. (Mozilla Support)
If you’re treating “browser + client attack surface” as part of your offensive/defensive validation, this incident maps cleanly to a workflow problem:
- Most orgs can patch stable browsers.
- Fewer orgs can prove they have no unmanaged Nightly/dev builds.
- Even fewer can produce a single report showing asset coverage + policy posture + behavioral evidence.
That’s exactly the gap an AI-assisted pentest and verification platform can close: not “exploit the bug,” but validate exposure, enforce posture, and generate audit-grade evidence across fleets and environments.
Two related Penligent pieces that align with this “prove, don’t promise” posture:
- Your Chrome zero-day operations framing (what to verify after patching) (पेनलिजेंट)
- Your VirusTotal incident-response workflow (how to pivot without leaking data) (पेनलिजेंट)
Practical “don’t repeat this mistake” checklist for runtime teams
- Wrap pointer tagging in named helpers (TagPtr/UntagPtr/IsTagged).
- Assert invariants at the write site (like the added
MOZ_ASSERTin the fix). (GitHub) - Add lint rules for suspicious bit-ops in sensitive directories.
- Gate risky refactors behind extra review for JIT/GC/Wasm code.
- Fuzz the state machine, not just inputs: moving GC + optimizing tiers + Wasm features.
- Treat “Nightly-only” as a policy violation on production endpoints unless explicitly approved.
References
- Firefox vulnerable introduction commit
fcc2f20e35ec(GitHub mirror) (GitHub) - Firefox fix commit
05ffcde…showing& 1→| 1+ assertion (GitHub) - Researcher technical write-up “How a single typo led to RCE in Firefox” (Kqx)
- Mozilla enterprise policy enforcement overview (Mozilla Support)
- Mozilla policy templates index (Mozilla GitHub Pages)
- ZDI blog: IonMonkey renderer compromise context (Zero Day Initiative)
- Mozilla advisory example (engine/memory safety context) (Mozilla)
- https://www.penligent.ai/hackinglabs/cve-2026-2441-the-chrome-css-zero-day-that-demands-proof-not-promises/ (पेनलिजेंट)
- https://www.penligent.ai/hackinglabs/cve-2026-2441-the-chrome-css-zero-day-that-starts-inside-the-sandbox-and-rarely-ends-there/ (पेनलिजेंट)
- https://www.penligent.ai/hackinglabs/virustotal-in-incident-response-how-to-identify-malware-fast-and-pivot-without-leaking-data/ (पेनलिजेंट)