In day-to-day database development, SUBSTRING is usually seen as a simple utility for extracting parts of a string—it’s efficient for handling email addresses, parsing URLs, or splitting composite keys directly at the SQL layer. However, security engineers know that this seemingly harmless function can become a hidden gateway for data leaks, privilege escalation, and cross-tenant breaches if used without strict validation. In environments such as multi-tenant SaaS platforms, financial systems, or healthcare record management, a single misuse can lead to catastrophic exposure of sensitive data.
When analyzing logs from production systems, patterns of frequent or unusual SUBSTRING calls can often signal attempts to exploit SQL injection vulnerabilities. Attackers combine it with other functions to slowly retrieve confidential information, bypassing restrictions that prevent full-field access in a single request. This guide explains why SQL substring acts as a double-edged sword, how to detect injection attempts effectively through log analysis, and how to integrate preventative strategies—including AI-driven automation—into your security workflow.
Why SQL Substring Becomes a Security Risk
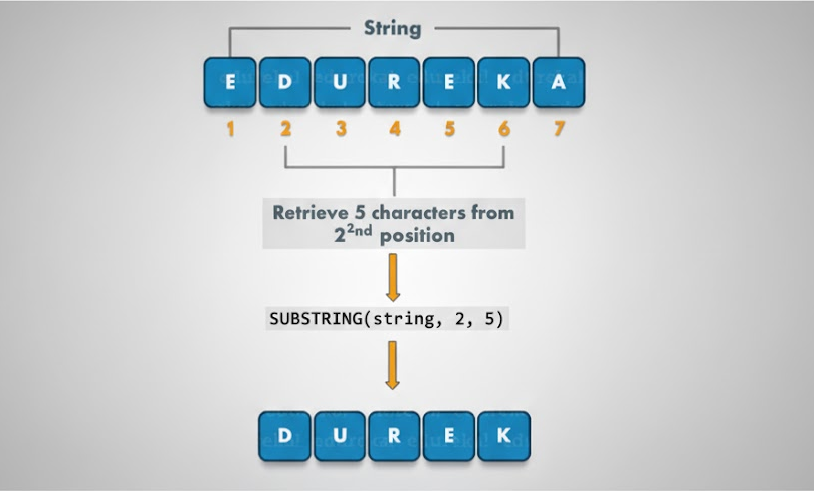
From a functional standpoint, SUBSTRING lets developers extract a portion of a string based on a starting position and length. This capability often replaces logic that would otherwise exist in the application layer, and while it may seem like an optimization, it also opens the door to abuse. An attacker can invoke SUBSTRING repeatedly to leak restricted data in small increments, bypassing constraints that would block complete outputs.
The risk escalates when SUBSTRING parameters—especially delimiters or lengths—are taken directly from user input without proper validation. In a multi-tenant system, a malicious actor might forge identifiers that, when parsed by SUBSTRING, point to another tenant’s data. At that moment, the isolation boundary meant to protect client segregation collapses.
-- Intended: Extract username from an emailSELECT SUBSTRING(email, 1, LOCATE('@', email)-1) AS username;
-- Malicious: Gradually read sensitive fieldsSELECT SUBSTRING(ssn, 1, 3) FROM users WHERE id=1;
How to Spot SQL Substring Exploitation in Database Logs?
An experienced analyst doesn’t just scan for SELECT या UPDATE keywords in logs—they look at behavior patterns. One of the most telling signs of potential compromise is an abnormal frequency of SUBSTRING calls, especially when combined with functions like ASCII या CHAR. This pairing is often used to translate specific characters from sensitive fields into numeric codes, allowing attackers to reconstruct full values piece by piece.
Another high-risk pattern is when the delimiter or length argument in SUBSTRING originates from external sources, such as GET parameters in a URL, POST body fields, or API payload data. Since these inputs can be manipulated, unvalidated usage effectively hands over slicing control to the attacker.
You should also be cautious when spotting JOIN statements in logs that depend on SUBSTRING to derive multi-tenant identifiers. For example, parsing a customer_ref into tenant IDs and order IDs on the fly might seem harmless, but a malformed input can easily trick the query into matching and returning rows belonging to the wrong tenant.

How to Identify Dangerous SQL SUBSTRING Usage
To combat SUBSTRING-based injection attempts, security teams should formalize both static and runtime detection mechanisms. The static side can be handled through SAST pipelines—configuring pattern-based rules to flag problematic SUBSTRING usage and fail pull requests if violations are found.
At runtime, database proxy layers or middleware can analyze query traffic in real-time, blocking any statement where SUBSTRING takes unvalidated dynamic input. Meanwhile, historical log analysis should use regular expressions to search for suspicious patterns, enabling security engineers to backtrack and identify potentially compromised datasets.
Example detection rule in a SAST configuration:
rules:
- id: sql-substring-dynamic-delimiter
languages: [sql]
message: Avoid SUBSTRING with unvalidated or dynamic delimiter/count.
severity: error
Simple Python regex detection for query logs:
import re
pattern = re.compile(r"SUBSTRING\\s*\\(.+?\\)", re.IGNORECASE)
with open('query.log') as log:
for line in log:
if pattern.search(line):
print("[ALERT] Possible risky SUBSTRING usage:", line.strip())
While these methods help you spot suspicious activity, they are even more effective when combined with proper development practices: validate all delimiters, enforce format constraints, keep parsing logic in the application layer, and never use SUBSTRING in security-critical join conditions.
AI Trends in SQL Injection Detection — Featuring Penligent
Artificial intelligence has been reshaping security monitoring by spotting anomalies that strict rule-based systems miss. In SQL injection detection, modern AI tools can correlate multiple signals across vast log datasets, learn from evolving attack patterns, and detect suspicious query construction in ways that go beyond static signature matching.
Penligent stands out in this space as the world’s first एजेंटिक एआई हैकर. Instead of requiring you to manually chain tools and write complex commands, Penligent allows you to initiate a full penetration testing process with plain English—for example, typing: “Detect SQL SUBSTRING injection risks”. The AI then autonomously orchestrates over 200 integrated security tools, including SQLmap, Burp Suite, Nmap, and Nuclei, to scan, validate, and analyze the target.
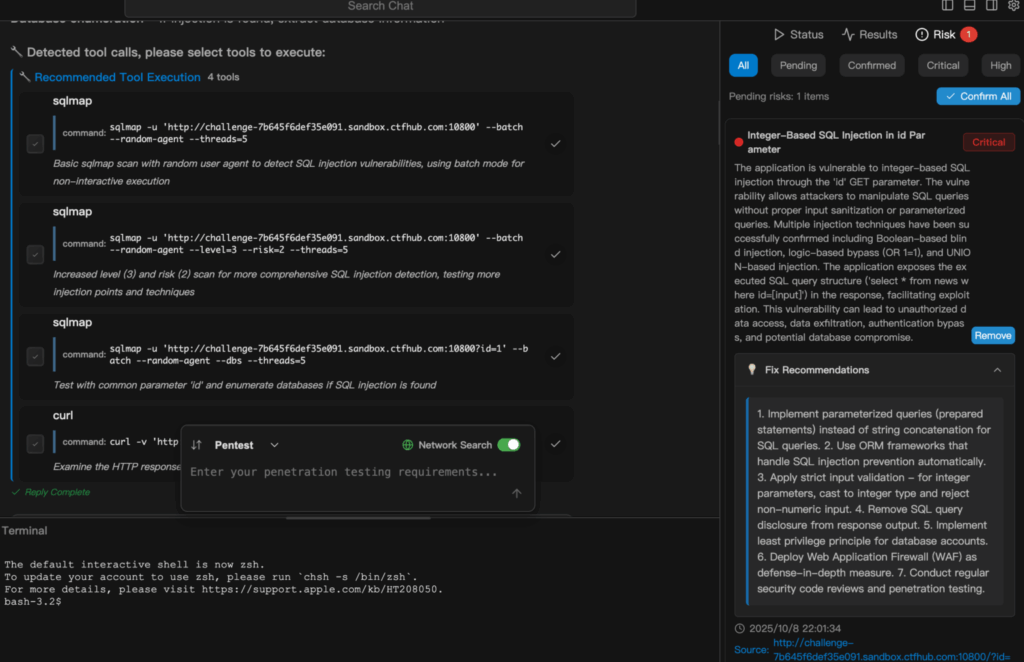
Penligent doesn’t just dump unfiltered results—it validates whether vulnerabilities are real, assigns priorities based on risk impact, and even blocks unsafe code from being deployed if integrated into your CI/CD pipeline. At the end of a test, it automatically generates a professional, shareable report, enabling your security team to act quickly while maintaining transparency into each decision and step the AI took. This means that what once took days of manual testing, verification, and reporting can now be accomplished in minutes—by both expert and non-expert users—without sacrificing accuracy.
निष्कर्ष
SQL SUBSTRING is far from a trivial string function when viewed through the lens of cybersecurity—it’s a potential attack vector that can quietly undermine your data boundaries if left unchecked. By embedding detection into your SAST pipelines, using runtime query interception, enforcing strict input validation, and leveraging AI-driven tools like Penligent, you gain not only visibility but also the speed to remediate threats before they turn into breaches.


