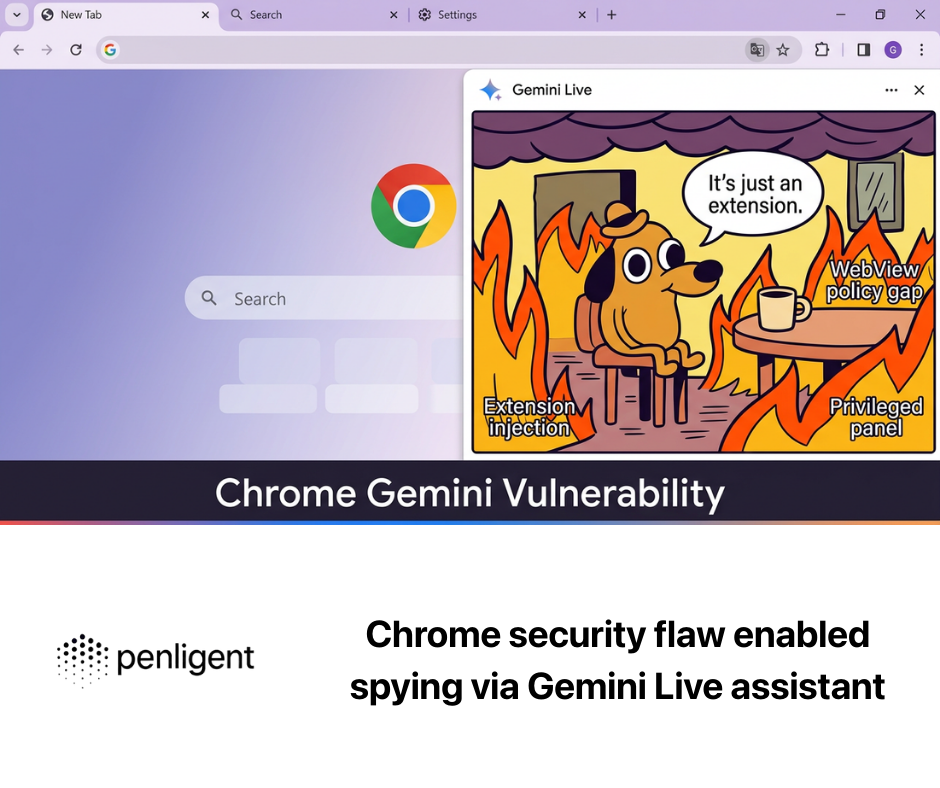
Introduction to OSINT and the OSINT Framework
Open Source Intelligence (OSINT) refers to the process of collecting and analyzing information from publicly available data sources to support decision-making in security, investigations, and research. The OSINT Framework is a curated, web-based directory of tools and resources designed to make this process more efficient and structured for analysts, digital investigators, cybersecurity professionals, and threat researchers.
Instead of being a single software product, the OSINT Framework serves as a centralized hub—organizing links to tools and services across categories like social media analysis, domain research, and geolocation. It’s widely used as an entry point to OSINT research.
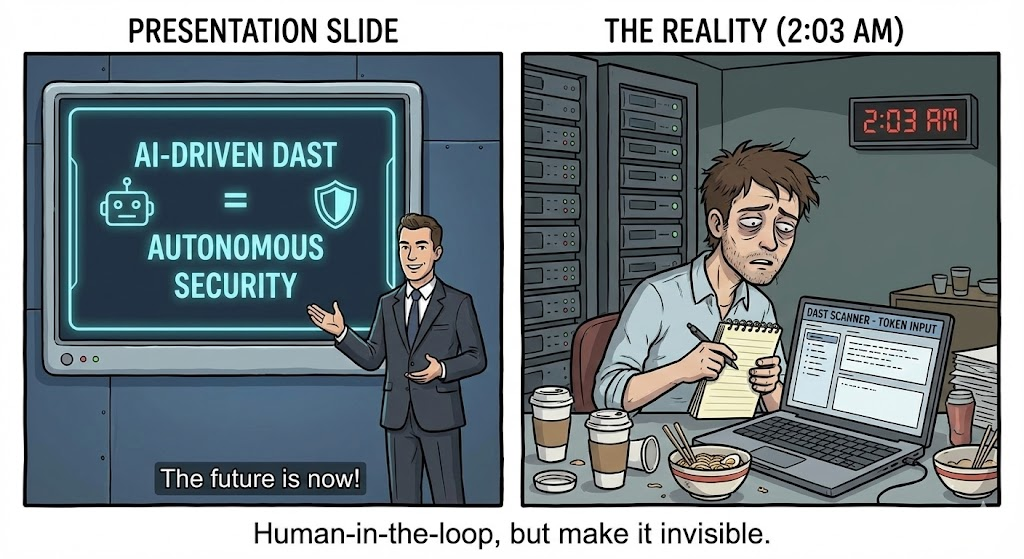
What Makes the OSINT Framework Valuable
At its core, the OSINT Framework offers:
- Comprehensive Categorization: Links and references to hundreds of free and paid intelligence tools.
- Easy Navigation: An interactive tree of resources that reduces the time needed to find relevant tools.
- Wide Domain Coverage: From metadata analysis to social media monitoring, email reconnaissance, and domain research.
By aggregating tools into easily navigable categories, the framework helps practitioners avoid the overhead of searching for tools individually and provides a structured starting point for OSINT investigations. Neotas
Key Categories and Tools in the OSINT Framework
Below are core categories frequently used in OSINT workflows, along with representative tools and examples of how they’re applied.
Search Engines & Domain Research
Search engines are foundational to OSINT. Analysts use advanced operators (like site:, intitle:, या filetype:) to uncover exposed pages, documents, or sensitive data in public repositories. Specialized search engines like Shodan and Censys show internet-connected devices and services, while Google Dorking can reveal unintentionally exposed content. Recorded Future+1
Social Media Intelligence (SOCMINT)
Social platforms offer a wealth of real-time information. Tools like social mention aggregators or keyword trackers provide insights into public sentiment, trending topics, and user networks. Analysts combine multiple sources to identify patterns or emerging threats. Recorded Future
Metadata & File Analysis
Documents and images contain embedded metadata that can leak information such as author names, software versions, GPS coordinates, or timestamps. Tools linked from the OSINT Framework help extract this data for investigative use.
Geolocation & Mapping
Geospatial OSINT tools support mapping coordinates from multimedia, tracking areas of interest through satellite imagery, and correlating physical locations with digital footprints. Knowlesys Software, Inc.
Dark Web Monitoring
For deep and hidden internet sources, tools like Tor browsers and specialized crawlers allow analysts to monitor darknet forums, marketplaces, and content not indexed by traditional search engines. Recorded Future
Threat Actor Profiling
Using aggregated OSINT data, analysts can develop profiles of cyber threat actors by examining their infrastructure, social profiles, or past activity patterns. This helps build actionable intelligence. Neotas
Why OSINT Matters in Modern Security and Intelligence
The OSINT Framework is widely used across multiple professional domains, including:
- Cybersecurity: Identifying exposed infrastructure, credentials, or vulnerabilities in publicly accessible data.
- Threat Intelligence: Monitoring threat actor communications or emerging attack tactics.
- Law Enforcement and Investigations: Corroborating evidence from public records and digital footprints.
- Corporate Risk and Competitive Intelligence: Analyzing market presence, corporate filings, and web footprints. Network Kings
Open source intelligence complements classified or proprietary data by providing broad visibility into external environments without requiring privileged access. Neotas
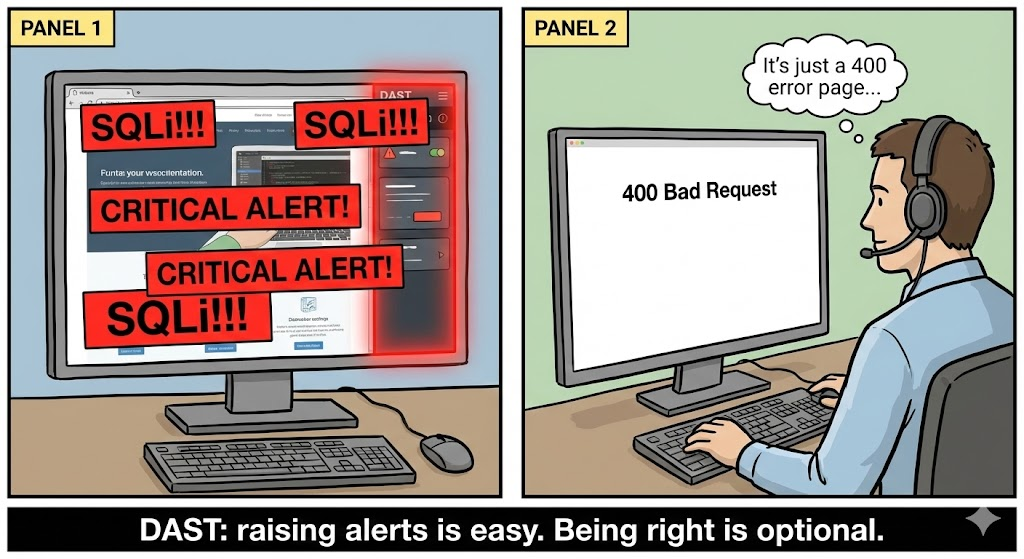
Best Practices for Using the OSINT Framework
Effective OSINT requires discipline, methodology, and ethical conduct:
- Define Clear Objectives: Before gathering data, specify what you’re trying to uncover—whether it’s asset discovery, threat profiling, or public sentiment analysis. Knowlesys Software, Inc.
- Validate and Corroborate Data: Multiple sources reduce false positives and increase confidence in conclusions. Rogue Signals
- Respect Ethical and Legal Boundaries: Always adhere to laws and organizational policies; misuse of OSINT can violate privacy or platform terms. Neotas
- Use Automation Where Appropriate: Tools and scripts help scale repetitive tasks like scheduled monitoring or data extraction. Rogue Signals
By integrating these practices, analysts can ensure intelligence outcomes are reliable and actionable.
Advanced OSINT Techniques with Code Examples
Below are two practical examples showing how OSINT practitioners extract and analyze open data.
Example 1: Automated Web Scraping for Targeted Data
Using Python’s requests और BeautifulSoup, analysts can collect and parse HTML content from public pages. This is commonly used to gather product listings, news mentions, or publicly indexed profiles.
अजगर
import requests
from bs4 import BeautifulSoup
url = "<https://example.com>"
response = requests.get(url)
soup = BeautifulSoup(response.text, "html.parser")
for link in soup.find_all("a"):
print(link.get("href"))
This script prints all hyperlinks on a given page and can be expanded to crawl and index multiple pages as part of reconnaissance or research.
Example 2: Reverse Image Metadata Extraction
Images often contain hidden metadata, which can expose camera, GPS, or timestamp data. Here’s how to extract EXIF metadata with the exifread library:
अजगर
import exifread
with open("photo.jpg", "rb") as image_file:
tags = exifread.process_file(image_file)
for tag in tags:
print(f"{tag}: {tags[tag]}")
This technique supports OSINT by enriching investigations with contextual metadata often overlooked in surface analysis.
Data Visualization and Analysis
High-volume OSINT investigations benefit from visualization tools that represent relationships and connections between entities.
| Category | Tool Example | उदाहरण |
|---|---|---|
| Link Analysis | Maltego | Visual mapping of connections (people, domains, IPs) wikipedia |
| Device Discovery | Shodan | Find exposed services and hardware on the internet wikipedia |
| Graph Analytics | Neo4j | Large dataset relationship mapping, pattern recognition |
| Public Records | Search Operators | Corroborate identity and filing records |
Visualization helps analysts spot relationships or anomalies that may be invisible in raw datasets.
Limitations and Ethical Considerations
While powerful, the OSINT Framework has limitations:
- Outdated or Broken Links: Because it is community-driven, not all links may remain current or functional. Reddit
- Data Overload: OSINT generates large datasets that can include noise or irrelevant information. Rogue Signals
- Legal Risks: Misuse—such as unauthorized automated scraping—can violate terms of service or data protection laws. Neotas
Practitioners should balance depth with ethical guidelines and ensure proper operational security measures are in place.
Conclusion: Practical OSINT with the OSINT Framework
The OSINT Framework remains a foundational resource for professionals seeking structured access to open-source tools and methodologies. It simplifies the discovery of relevant intelligence resources while providing a scaffold to organize research work.
Whether you are conducting threat research, supporting cybersecurity, or performing investigative analysis, combining the OSINT Framework with disciplined practice, ethical conduct, and analytical skills allows you to derive meaningful insights from public data sources.
By following structured workflows and leveraging diverse tools in an ethical and responsible manner, practitioners can maximize the value of open-source intelligence in modern investigations and security operations. Neotas