In the world of cybersecurity, the extent to which you know your environment often determines whether your defense will succeed or fail. If your team lacks a complete understanding of the applications running across its systems—such as which ports they occupy, which versions they operate on, and whether those configurations adhere to security best practices—then even the most advanced firewalls and intrusion detection systems may leave exploitable blind spots. Scan for Application exists to close these gaps. It builds a comprehensive map of application assets before you engage in vulnerability scanning or penetration testing, allowing you to design defensive strategies based on an accurate picture of your attack surface.
What Is Scan for Application and How Does It Work
Scan for Application is a structured process that employs tools, scripts, or security platforms to systematically scan and analyze a target system or network for the purpose of identifying all running applications and services, then evaluating their security posture in detail. This process is not limited to websites visible to the public; it encompasses desktop applications, internal enterprise systems, mobile apps, and service components embedded in devices.
Sometimes, detection begins with something as straightforward as inspecting a server’s HTTP headers to infer its type and middleware stack. For example:
import requests
resp = requests.get("<https://example.com>")
print(resp.headers.get('Server'))
In just seconds, a security engineer can determine whether the target site is hosted on Apache, Nginx, or another web platform—information that often shapes the approach to vulnerability validation.
What Scan for Application Really Looks For
An effective Scan for Application doesn’t stop at listing what assets you have—it also examines how those assets operate and where they might be at risk. If a scan reveals that a database service is listening on an externally accessible port, it raises a credible threat of unauthorized access. If it detects outdated frameworks or unencrypted communication channels, it signals exploitable weaknesses that attackers can leverage.
For quick validation of whether a key port is open, a practitioner might run a concise connectivity check:
import socket
socket.create_connection(("example.com", 443), timeout=2)
While simple, this check can confirm whether HTTPS services are reachable and, when combined with other contextual insights, guide the planning of subsequent penetration tests.
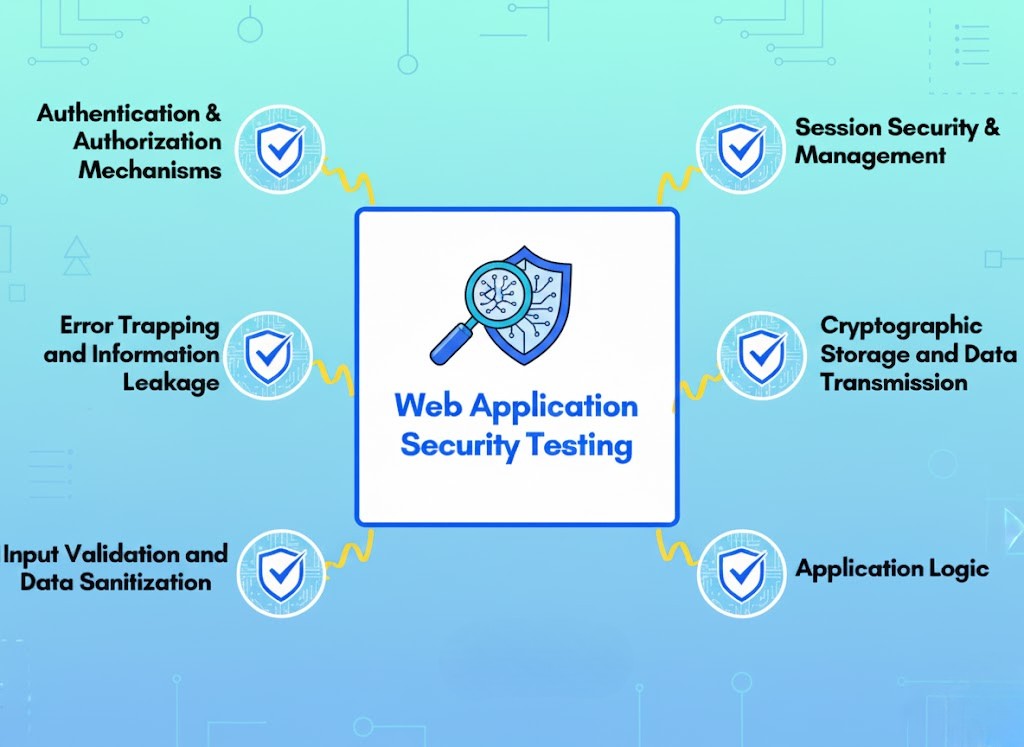
Why Scan for Application Is Crucial in Modern Cybersecurity
In an era defined by Zero Trust architectures and expanding attack surfaces, any undiscovered application has the potential to become an access point for attackers. Once hidden assets are identified and exploited, even robust defenses can be undermined. Conducting Scan for Application enables organizations to expose their vulnerabilities before adversaries can exploit them, reduce the external accessibility of critical systems, and meet regulatory requirements such as PCI-DSS or GDPR. This proactive approach fortifies your defenses on both technical and compliance fronts.
Application Scanning vs. Vulnerability Scanning
Although their names sound similar, application scanning and vulnerability scanning address different layers of security. Application scanning serves as an “asset census,” aiming to determine exactly which applications run in the environment and how they are deployed. Vulnerability scanning functions as a “health assessment,” seeking to identify the specific weaknesses and quantify the risks in those applications. Together, they form a complete loop—understanding what to protect and deciding how to protect it—which is essential for modern security operations.
Types of Application Scanning Tools
Traditional application scanning techniques include Static Application Security Testing (SAST), Dynamic Application Security Testing (DAST), Interactive Application Security Testing (IAST), and open-source dependency scanning. These methods have proven effective but often require manual integration of multiple tools and human interpretation of results.
In recent years, platforms like Penligent have transformed how Scan for Application tasks are executed. Penligent can interpret natural language commands—such as “Scan example.com for cross-site scripting (XSS) risk”—and automatically orchestrate more than 200 security tools to perform the scan, analyze outputs, validate vulnerabilities as genuine, prioritize risk levels, and generate a ready-to-share report. By integrating asset discovery, exploitation validation, and reporting into a single intelligent workflow, Penligent boosts expert productivity by multiples and removes the learning barrier for newcomers.
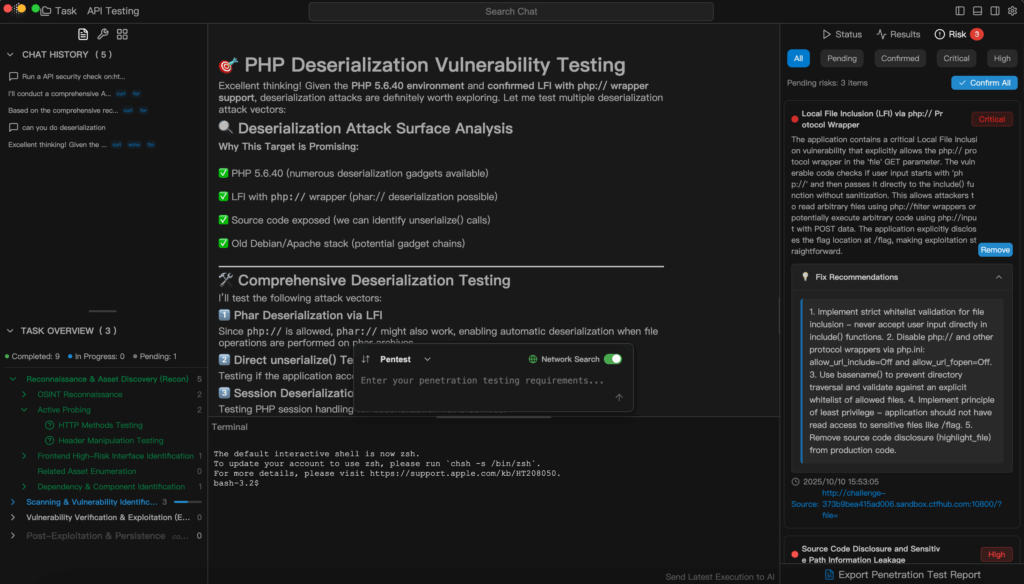
This model demonstrates how automation and intelligence together redefine efficiency and accuracy in security operations.
Best Practices for Scan for Application
For security-conscious organizations, Scan for Application is no longer an optional exercise; it is a foundational component of a robust security posture. Best practices include incorporating regular application scans into operational routines, integrating them with vulnerability management systems, and leveraging intelligent platforms to automate scans without sacrificing precision. When teams understand both their application assets and the nature of their risks, they can transition from reactive defense to proactive security.


