WordPress powers over 40% of the public web, making its login surface one of the most continuously targeted authentication endpoints on the internet. According to WordPress security documentation, brute force and credential stuffing remain among the most common attack patterns against
wp-login.phpऔरxmlrpc.php(developer.wordpress.org).
This article focuses on realistic attack modeling, not exploitation for wrongdoing. Every technique discussed here is framed for defensive validation, red-team simulation, and security hardening.

Why WordPress Login Remains a High-Value Target
The WordPress login mechanism exposes several properties attractive to attackers:
- A predictable endpoint (
/wp-login.php) - A large installed base with inconsistent security posture
- Frequent reuse of weak or leaked credentials
- Optional legacy features like XML-RPC
Unlike zero-day exploitation, login attacks are low cost, high volume, and statistically effective. Large-scale botnets routinely probe WordPress login pages for weak credentials, often blending into normal traffic patterns.
WordPress itself acknowledges that brute force attacks are inevitable and must be mitigated through layered controls rather than obscurity (developer.wordpress.org).
Attack Surface Overview: wp-login.php and xmlrpc.php
Two endpoints dominate WordPress authentication abuse:
wp-login.php
This endpoint handles interactive logins and is heavily targeted by:
- Credential guessing
- Credential stuffing
- Username enumeration via response behavior
A typical login request looks like:
http
POST /wp-login.php HTTP/1.1 Content-Type: application/x-www-form-urlencoded log=admin&pwd=password123&wp-submit=Log+In
Attackers rely on automation rather than sophistication.
xmlrpc.php
XML-RPC enables remote publishing and API-style authentication. Its system.multicall feature historically allowed amplified brute force attempts in a single request.
Multiple advisories and incident reports have documented XML-RPC abuse as a force multiplier for password attacks (CERT).
Simulating WordPress Login Attacks with Kali Linux (Authorized Testing Only)
Kali Linux is widely used in professional penetration testing due to its curated tooling and controlled environment (kali.org).
WPScan: Enumeration and Credential Testing
WPScan is a WordPress-focused scanner maintained by Automattic security researchers (kali.org).
दे घुमा के
wpscan --url <https://target.example> --enumerate u
This command enumerates publicly discoverable usernames, which is often the first step in login attack modeling.
Credential testing (only with permission):
दे घुमा के
wpscan --url <https://target.example> \\ --usernames admin \\ --passwords wordlist.txt
WPScan respects rate limits and logs failed attempts, making it suitable for controlled testing.
Hydra: Form-Based Authentication Testing
Hydra is a general-purpose login testing tool capable of HTTP form simulation (en.wikipedia.org).
hydra -l admin -P rockyou.txt target.example http-post-form \\"/wp-login.php:log=^USER^&pwd=^PASS^&wp-submit=Log+In:Invalid username"
This simulates real-world credential guessing behavior and highlights the importance of rate limiting and anomaly detection.
Defense Example 1: Application-Level Login Rate Limiting
Rate limiting remains the most effective mitigation against brute force attacks.
A simplified WordPress-level control:
php
add_filter('authenticate', function($user, $username, $password) {
$ip = $*SERVER['REMOTE_ADDR'];*
*$attempts = get_transient('login_attempts*' . $ip) ?: 0;
if ($attempts > 5) {
wp_die('Too many login attempts.');
}
set_transient('login_attempts_' . $ip, $attempts + 1, 300);
return $user;
}, 30, 3);
This demonstrates the principle: stateful tracking + enforced delay.
Defense Example 2: Server-Level Protection of wp-login.php
Defense should not rely solely on application logic.
NGINX example:
nginx
location = /wp-login.php {limit_req zone=login burst=5 nodelay; }
Server-level controls significantly reduce attack throughput before PHP execution.
CVE Context: Why Login Security Is Not Theoretical
While brute force attacks do not always map directly to CVEs, WordPress authentication weaknesses frequently appear in vulnerability databases due to plugin behavior or logic flaws.
For example:
- CVE-2023-2745 involved authentication bypass conditions in WordPress plugins handling user roles improperly (nvd.nist.gov).
- Multiple XML-RPC related incidents have resulted in credential compromise without exploiting WordPress core vulnerabilities.
These cases reinforce a key lesson: most WordPress compromises begin with authentication failure, not memory corruption.
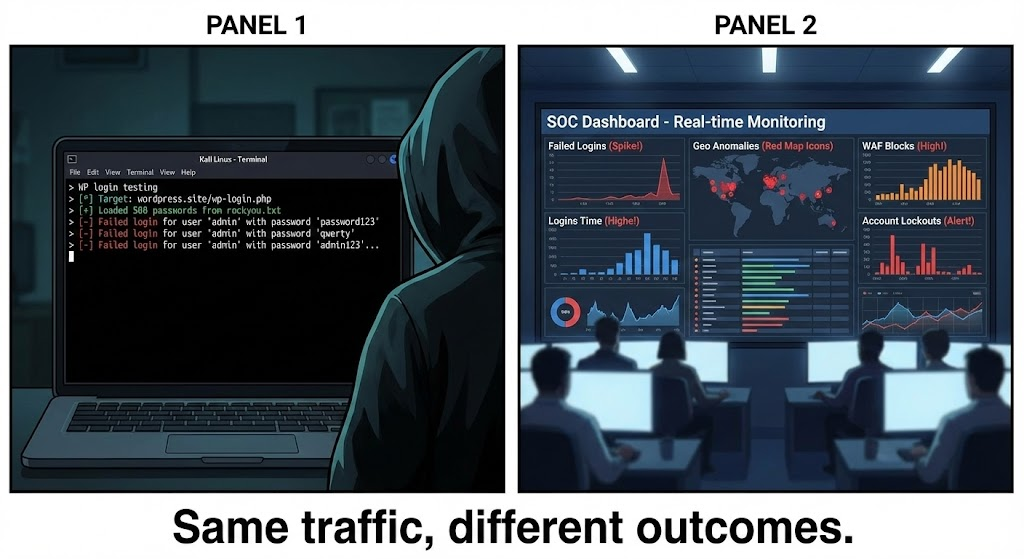
Operational Signals and Detection
Security teams should monitor for:
- Repeated failed logins from rotating IPs
- Excessive XML-RPC requests
- Login attempts outside normal geographic or temporal patterns
These indicators are often more reliable than signature-based alerts.
Where Automation and AI Fit
Manual testing validates assumptions, but scale requires automation. AI-driven penetration testing platforms such as पेनलिजेंट focus on correlating authentication attack paths, runtime behavior, and defensive gaps across environments.
Rather than replacing tools like WPScan, such platforms aim to orchestrate attack simulation and prioritization, helping teams focus remediation on login paths that present real risk.
This approach aligns with modern AppSec practices where continuous validation replaces periodic testing.
Conclusion: From “Hack” to Measurable Security Posture
Searching for wordpress login kali linux hack reflects a practical concern: how fragile is my authentication layer under realistic attack pressure?
By modeling attacks responsibly, validating defenses with Kali Linux, and enforcing layered controls at both application and infrastructure levels, organizations can significantly reduce WordPress compromise risk.
The goal is not to stop all login attempts—but to make successful compromise statistically improbable.