The Persistence of “Simple” Catastrophes
In January 2026, amidst the noise of quantum decryption fears and adversarial AI attacks, the cybersecurity community was pulled back to basics by CVE-2025-67968. This vulnerability, found in the Real Homes CRM plugin (versions ≤ 1.0.0), carries a devastating CVSS v3.1 score of 9.9.
It is an Unrestricted Upload of File with Dangerous Type (CWE-434), but to categorize it merely as “file upload” is to underestimate the architectural rot it represents. For the hardcore security engineer, CVE-2025-67968 is a case study in the failure of Implicit Trust. It demonstrates how a low-privileged user—a Subscriber intended only to view newsletters—can leverage a forgotten AJAX hook to dismantle an entire server infrastructure.
This article goes beyond the basic advisory. We will reverse-engineer the vulnerability, explore the specific PHP failures, construct a WAF-bypassing kill chain, and analyze why this class of vulnerability effectively renders traditional Static Application Security Testing (SAST) obsolete in favor of AI-driven, agentic verification.
The Architecture of Failure: WordPress AJAX Hooks
To understand the exploit, one must understand the battlefield. WordPress relies heavily on admin-ajax.php for dynamic interactivity. Developers register “actions” that map to PHP functions.
Crucially, these hooks come in two flavors:
wp_ajax_{action}: Fires for logged-in users.wp_ajax_nopriv_{action}: Fires for unauthenticated visitors.
The fatal assumption made by the developers of Real Homes CRM was treating “logged-in” as synonymous with “trusted.” They registered the action realhomes_upload_csv using the wp_ajax_ hook but failed to implement a Capability Check inside the function itself.
In the WordPress permission model, a “Subscriber” is technically logged in. Therefore, they have access to the same AJAX endpoints as an Administrator, unless the code explicitly forbids it. CVE-2025-67968 exists in this invisible gap between “Authenticated” and “Authorized.”
Code-Level Anatomy: Where Logic Breaks Down
Let’s simulate the vulnerable controller logic to pinpoint exactly where the defense collapsed. The following is a reconstruction based on the vulnerability disclosure patterns.
PHP
`/**
- SIMULATION OF VULNERABLE CONTROLLER
- Hook: wp_ajax_realhomes_upload_csv */ function realhomes_upload_handler() { // CRITICAL FAILURE #1: Missing Authorization // Proper code should have: if (!current_user_can(‘manage_options’)) die(); if (isset($_FILES[‘import_file’])) { $file = $_FILES[‘import_file’];
// CRITICAL FAILURE #2: Shallow Validation // The code relies on the 'type' sent by the browser/client. // This is user-controlled data. $allowed_types = ['text/csv', 'application/vnd.ms-excel']; if (in_array($file['type'], $allowed_types)) { $upload_dir = wp_upload_dir(); $target_path = $upload_dir['path'] . '/' . basename($file['name']); // CRITICAL FAILURE #3: Extension Preservation // The code accepts the filename as provided by the user. // If the user sends 'exploit.php', it saves as 'exploit.php'. if (move_uploaded_file($file['tmp_name'], $target_path)) { wp_send_json_success(['url' => $upload_dir['url'] . '/' . basename($file['name'])]); } }} wp_send_json_error(‘Upload failed’); }`
The Trifecta of Vulnerability:
- No ACL (Access Control List): The door is open to anyone with a login cookie.
- Client-Side Trust: Believing the
コンテンツタイプheader allows attackers to dress up a wolf as a sheep. - Filesystem Passthrough: Allowing the user to dictate the file extension (
.php) means the web server (Apache/Nginx/LiteSpeed) will execute it rather than serving it as text.
The Kill Chain: From Subscriber to Root
Exploiting CVE-2025-67968 is not a “spray and pray” operation. It requires a structured kill chain.
フェーズ1:偵察とアクセス
The attacker scans for the plugin signature, often found in the source code: /wp-content/plugins/realhomes-crm/. Once confirmed, the attacker needs a Subscriber account. On real estate platforms, this is trivial—registration is usually open for users to “save properties.”
Phase 2: Payload Construction (The Bypass)
A standard upload of shell.php might be caught by a basic firewall if it inspects extensions. However, the application logic checks the MIME type.
The “Chameleon” Request:
The attacker crafts a マルチパート/フォームデータ POST request.
- Filename:
config_backup.php(The server saves this exactly). - Content-Type:
text/csv(The server checks this and approves). - Content: The PHP payload.
To bypass heuristic scanners that might look at the first few bytes of the file (Magic Bytes), the attacker can create a Polyglot File.
- They add a valid CSV header:
ID,Name,Email,Status - Followed by the payload:
<?php system($_GET['cmd']); die; ?>
To the server’s weak inspection logic (if it uses finfo_file), it might look like text. To the PHP interpreter, everything before <?php is just ignored noise, and the code executes perfectly.
Phase 3: Execution & Persistence
Once move_uploaded_file executes, the shell resides at /wp-content/uploads/2026/01/config_backup.php.
The attacker accesses this URL. The web server sees the .php extension, hands it to the PHP-FPM processor, and the attacker achieves RCE. From here, they can:
- Dump
wp-config.phpto get database credentials. - Inject JavaScript into theme headers (SEO poisoning/Credit Card skimming).
- Lateral move to other sites hosted on the same server.
Advanced Evasion: Defeating the WAF
In 2026, most servers sit behind Cloudflare, AWS WAF, or Imperva. How does CVE-2025-67968 bypass these?
1. Chunked Transfer Encoding:
Attackers can split the payload into HTTP chunks. WAFs typically inspect the continuous stream. By breaking the <?php tag across chunks, the WAF pattern matcher might miss the signature, but the backend server reassembles it before processing.
2. Obfuscation Chains:
Instead of sending cleartext システム(), attackers use PHP’s dynamic features:
$_= "sys"."tem"; $_($_GET['x']);
This passes simple keyword filters used by generic WAF rulesets meant to block “file upload attacks.”
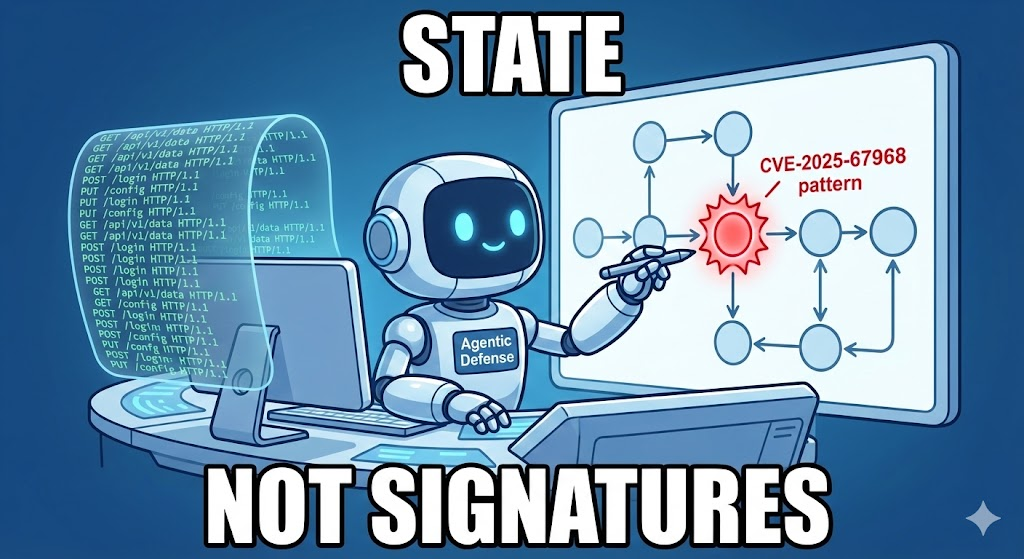
3. Statefulness (The WAF’s Weakness):
WAFs are stateless regarding user permissions. The WAF sees a “Subscriber” uploading a “CSV”. It doesn’t know that “Subscribers” shouldn’t be uploading CSVs to this specific endpoint. It assumes the application handles authorization. This logic gap is where the vulnerability thrives.
静的解析(SAST)の失敗
Why wasn’t this caught during development?
Context Blindness.
A SAST tool scanning the plugin source code sees move_uploaded_file. It checks if the function is reachable. It might flag “Unrestricted Upload,” but developers often mark this as “False Positive” because they point to the if ($file['type'] == 'text/csv') line.
The SAST tool cannot semantic understand that text/csv is a user-supplied lie. It cannot understand that the function is hooked to wp_ajax_ without a capability check. It lacks the semantic understanding of the WordPress permission model.
The Penligent Paradigm: Agentic AI Verification
This is the pivotal moment for AI-Driven Penetration Testing. The industry is moving away from “scanners” toward “agents.”
で ペンリジェント, we approach CVE-2025-67968 not as a pattern-matching problem, but as a logic puzzle. An AI Agent allows for Stateful Logic Verification.
The Agent’s Chain of Thought
When a Penligent Agent engages with a target running Real Homes CRM, its internal reasoning process looks like this:
- 忖度だ: “I have identified a WordPress installation. I see
realhomes-crmin the source.” - Role Simulation: “I have a valid credential set for a ‘Subscriber’. I will authenticate and extract my session cookies.”
- Attack Surface Mapping: “I am parsing the JS files. I found a reference to
action: realhomes_upload_csv. This looks like an administrative function.” - Hypothesis Generation: “If I am a Subscriber, I should ない be able to access this. However, the code might be missing an ACL. I will attempt to access it.”
- Payload Fuzzing (Smart): “The endpoint expects a CSV. I will try to upload a file named
test.phpbut declare it astext/csv. If that fails, I will trytest.csv.php. If that fails, I will try a Polyglot.” - 検証する: “The server responded ‘Success’. I will now attempt to HTTP GET the file I just uploaded. If I receive the output of my
echocommand, the vulnerability is confirmed.”
結果 The Agent generates a report that says, “I successfully achieved RCE as a Subscriber.” This is zero-false-positive validation. It proves the logic flaw exists in the running environment, bypassing the limitations of static code analysis.
Strategic Remediation: Beyond the Patch
Applying the vendor patch for CVE-2025-67968 is necessary but insufficient. You must harden the environment against the next logical flaw.
1. Defense in Depth: Directory Execution Prevention
The most effective mitigation for File Upload vulnerabilities is to castrate the uploads directory. Even if an attacker uploads a PHP shell, the web server should refuse to execute it.
For Nginx:
Nginx
location ^~ /wp-content/uploads/ { # Prevent PHP execution location ~ \\.php$ { return 403; } }
2. Immutable Infrastructure:
In containerized environments (Docker/Kubernetes), the code directory should be read-only. Uploads should be offloaded immediately to S3 or Azure Blob Storage, which cannot execute PHP code. This renders local file upload vulnerabilities inert.
3. Strict Logic Validation:
Developers must move away from “Blocklists” (banning .php) and “MIME checks” (trusting headers).
- Rename on Upload: Always rename files to a random hash (
md5(time())). - Re-encode Content: Use libraries like ImageMagick to re-process images, stripping metadata and webshells.
- Capability Gates: Every AJAX function must start with a permission check.
Conclusion: The Future of Logic Flaws
CVE-2025-67968 is a reminder that as we build higher walls around our networks, attackers are simply finding unlocked doors inside. The complexity of modern CMS ecosystems, combined with the pressure to ship features fast, guarantees that logic flaws will persist.
The era of “running a scan once a quarter” is over. Vulnerabilities like this—which require authentication, state manipulation, and logic bypassing—can only be detected by continuous, intelligent, and active probing. Whether through a dedicated Red Team or an automated AI platform like ペンリジェント, the mandate is clear: Verify the logic, not just the code.
In the battle between static defenses and dynamic attackers, only dynamic defenses stand a chance.
参考文献と権威あるリンク
- NVD: CVE-2025-67968 Detail
- CWE-434: Unrestricted Upload of File with Dangerous Type
- Penligent.ai: The Future of Automated Penetration Testing
- Penligent Blog: Why Logic Flaws Defeat Traditional Scanners
- OWASPファイルアップロードチートシート
- WordPress Developer Resources: Securing AJAX
- Wordfence: 2025 State of WordPress Security Report


