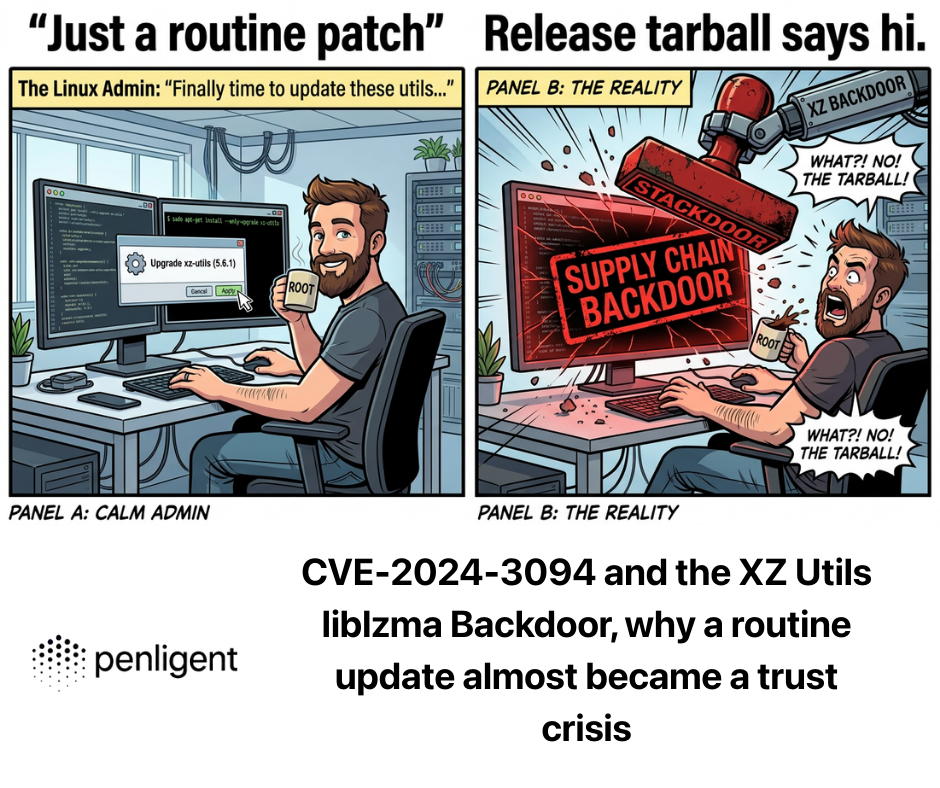
ゼロデイ・エクスプロイトとは何か?
A ゼロデイ攻撃 とは、公に公表されていないソフトウェアの欠陥を武器化するために使われる手法である。 ゼロデイ というのは、守備陣が 修正期間ゼロ日.
典型的なゼロデイ・シークエンスには以下のようなものがある:
- 未知の脆弱性
- 攻撃者が発見
- 攻撃者が悪用コードを開発
- パッチが存在する前に悪用される
このような欠陥は、しばしば可能にする:
- リモートコード実行(RCE)
- 特権の昇格
- データ盗難
- マルウェアの埋め込み
- 広範な妥協
脆弱性が未知であるため、従来のセキュリティツール(アンチウイルス、シグネチャーIDS、パッチ適用サイクル)は本質的に効果がない。
ハッカーがゼロデイ脆弱性を発見する方法
洗練された攻撃者(国家、高度犯罪集団、エクスプロイト・ブローカー)は、公表されていない脆弱性を見つけるために複数のテクニックを駆使する。
高度なファジング(技術と安全な例)
AFL++、Honggfuzz、libFuzzerなどの最新のファザーは、ターゲットアプリに予期せぬ動作をさせるために入力を変異させる。
以下はその一例である。 安全で教育的なPythonファジングの例 コアコンセプトの説明
パイソン
インポート・サブプロセス、ランダム
def mutate(seed):
i = random.randint(0, len(seed)-1)
return seed[:i] + bytes([random.randint(0,255)])+ seed[i+1:]
シード = b "A "*64
for _ in range(3000):
data = mutate(seed)
process = subprocess.Popen(["./test_binary"])、
stdin=subprocess.PIPE、
stdout=subprocess.PIPE、
stderr=subprocess.PIPE)
out, err = process.communication(データ)
process.returncodeが(0, None)でない場合:
print("クラッシュを確認 - 手動で調査")
これは、武器化せずにファジングのワークフローを模倣するものだ。
IDAまたはGhidraによるリバースエンジニアリング
アナリストたち
- バイナリのデコンパイル
- 機能フローの追跡
- メモリの境界を特定する
- 安全でない呼び出しを見つける(例.
strcpy,スプリント) - ロジックの欠陥を検出する
リバース・エンジニアリングによって、攻撃者はプログラムがどのように入力を処理し、どのようにそれを破るかを完全に知ることができる。
ゼロデーのライフサイクル
ゼロデイ攻撃は通常、このような段階を経て進行する:
- 発見 未知の脆弱性
- 開発 エクスプロイト(トリガー+ペイロード)
- 武器化する 文書、ウェブページ、フィッシング・ファイルなどに埋め込む。
- 届ける エクスプロイト
- 実行する コードとマルウェアのインストール
- 持続する 横方向の動きを行う
- エクスプロイト・スプレッド パッチを当てるまで
例メモリ破壊の安全なデモンストレーション
以下はその一例である。 開発不可能リスクを実証するための例示的なオーバーフロー:
c
void 脆弱(char *input) { {.
char buf[32];
// 安全でない:デモンストレーションのみ
strcpy(buf, input);
}
このコードは、単純な見落としがいかにセキュリティ上の弱点につながるかを示している。
本当のエクスプロイトには、DEP、ASLR、スタッククッキー、CFGなどを回避する必要があり、単純なスニペットをはるかに超える。
例概念的なペイロード・デリバリー・チェーン
現実的な(しかし非武装の)攻撃には、次のようなものがある:
- 悪意のあるPDF → ゼロデイを誘発
- シェルコードスタブ → セカンドステージをロード
- ローダー → 暗号化されたペイロードをダウンロード
- ペイロード → 信頼されたプロセスに注入
- 永続性 → スケジュールされたタスク / レジストリ・イベント
説明のための概念的なシェルコードのスタブ(機能しない):
アセンブリ
概念的で実行不可能な例
mov rax, [target_socket]
コール establish_connection
call read_encrypted_payload
jmp 実行スタブ
これは機能性ではなく構造を示している。
ゼロデイ・エクスプロイトが危険な理由
ゼロデイが危険なのは
- パッチは存在しない
- 従来のツールでは検出できない
- 高い特権アクセスを提供する
- 高度な脅威行為者によって利用されている
- 迅速かつ広範な侵害を可能にする
事例研究(Stuxnet、SolarWinds、iOSエクスプロイトなど)は、ゼロデイ攻撃が地政学的、経済的に与える影響の大きさを示している。

ゼロデイ・エクスプロイトを検出する方法
ゼロデイ検出は 署名ではなく行動.
Sysmonルールの例:疑わしいDLLのロード
xml
。
署名なし。
temp。
</ImageLoad>
といった悪用行為を早期に発見するのに役立つ:
- 不審なDLLのサイドロード
- 中空加工
- ファイルレスマルウェアのロード
スリカータ・ルールの例(安全、非特定)
ヤムル
alert http any any -> any any (
msg: "Potential exploit behavior"(悪用される可能性のある動作);
flow:established,to_server;
content:"|00 00 ff ff|";
http_header;
)
これは、エクスプロイト開発中にしばしば生成される不正なパターンを検出する。
Pythonの軽量サンドボックス
パイソン
インポート・サブプロセス
def run_safely(file):
subprocess.run(["firejail", "--private", file])
不審な文書やバイナリを分析する際には、封じ込めが鍵となる。
ゼロデイ脅威から身を守る方法
ゼロデイの回復力には以下が必要である:
- ディフェンス・イン・デプス
- 攻撃面の減少
- 厳格なアクセス制御
- ネットワーク・セグメンテーション
- 行動ベースのEDR
- エクスプロイト緩和フレームワーク(CFG、ASLR、DEP)
- 迅速なパッチサイクルと仮想パッチ
例異常入力をブロックするWAFロジック
パイソン
def waf_filter(req):
if len(req.headers.get("User-Agent", ""))> 400:
偽を返す
if "{{$" in req.text:
偽を返す
真を返す
これは、特定のペイロードではなく、攻撃のクラスをブロックする。
例RASP SQLインジェクション・ガード
パイソン
def protect_sql(query):
dangerous = ["--", ";", "/*", "*/", "DROP", "UNION"].
if any(x in query.upper() for x in dangerous):
raise Exception("不審なSQL動作をブロックしました。")
リターンクエリ
ランタイム保護はエクスプロイトファミリー全体を無力化する。
ペンリジェントAIによるゼロデイ耐性
Penligentは、ゼロデイ脅威から組織を強化します:
- AIによるファジング
- 自律的脆弱性発見
- メモリ異常検知
- APIレスポンスの意味的拡散
- MLベースの悪用可能性スコアリング
- 自動横移動検出
Penligentのゼロデイ・シミュレーション・エンジン(疑似ワークフロー)
疑似
ループだ:
input = AI.generate_mutation(種)
レスポンス = target.run(入力)
response.crashまたはhangの場合:
report.possible_zero_day(入力)
if response.behavior_shift > threshold:
alert.behavior_anomaly()
これにより、攻撃者がゼロデイタイプの弱点を見つける前に、プロアクティブに特定することができる。
ペルリゲント・エクスプロイタビリティ分析
疑似
analyze(memory_dump):
if control_flow_corrupted:
レーティング="高"
elif heap_structures_modified:
レーティング="中"
そうでなければ
評価="低い"
これにより、誤検知が減り、実用的な洞察が得られる。
結論ゼロデイ防衛には積極的な戦略が必要
特にAIを活用したサイバー犯罪の加速に伴い、ゼロデイ攻撃は今後も増加し続けるだろう。防御者は、次のような対策にシフトしなければならない。 シグネチャーベース への 行動、異常駆動、予測 のアプローチだ。
Penligentは、攻撃者に弱点を突かれる前に弱点を発見することで、組織がこうした脅威に先手を打てるよう特別に設計されています。