サイバーセキュリティ評価と侵入テストのワークフローの中で、ブラウザベースのセキュリティメカニズムは常に焦点となっており、その中でも、Cross-Origin Resource Sharing(CORS)は、APIと最新のウェブアプリケーションの両方のセキュリティに広範囲な影響を及ぼすポリシーとして際立っています。テスト者が リクエストされたリソースに「access-control-allow-origin」ヘッダーが存在しない。 むしろ、バックエンドのクロスオリジン・コンフィギュレーションにおける過失や見落とし、あるいは、セキュリティ設計の一部として意図的に設けられた制限を知らせているのかもしれません。以下の節では、このメッセージを、以下の観点から分析します。 侵入テスト の観点から、その技術的な意味と潜在的なリスクを解き明かし、現実世界のシナリオを通じてその防衛上の意義を探り、Penligentのようなツールがいかに効率的でより正確な評価を可能にするかを示す。
何なのか? access-control-allow-origin」ヘッダを使用しない。 エラー
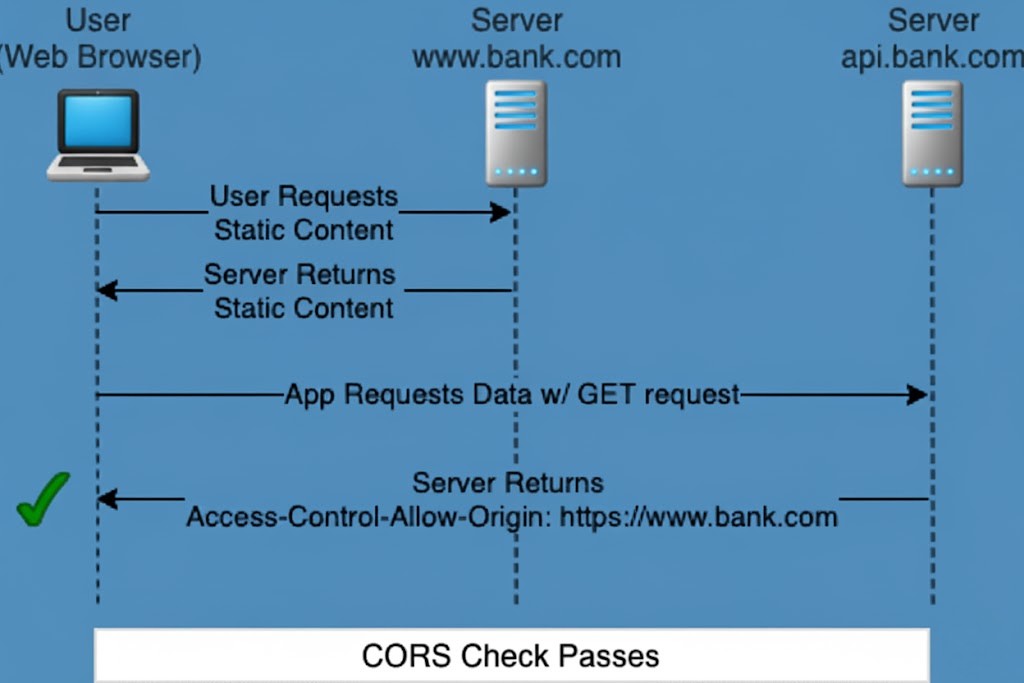
その中核となるCORSは、ブラウザによって実装されるクロスオリジンセキュリティルールのセットであり、ドメイン名、ポート番号、またはプロトコルの違いをカバーする、同一オリジンの範囲外のリソースを要求しようとするときに、ウェブページが持つ可能性のあるアクセスレベルを制限する。サーバーのレスポンスに アクセス制御-許可-オリジン HTTPヘッダは、ブラウザが、基礎となるネットワーク・リクエストが技術的には完了しているにもかかわらず、クライアント側のコードにレスポンスを読ませることを拒否し、代わりに access-control-allow-origin」ヘッダを使用しない。 エラー。
この動作は、攻撃者がブラウザのスクリプトを使用して、適切な権限なしに機密性の高いクロスオリジンデータを取得しようとした場合、その制限が効果的にそれをブロックすることを意味します。しかし、セキュリティテスト実施者にとって、このメッセージは、ターゲットシステムのクロスオリジンポリシーが十分に設定されていないか、適用されていないことを示すかもしれません。
セキュリティテスト者が、ブラウザのコンソールで次のようなクロスオリジン・リクエストのテストスクリプトを実行すると想像してください:
fetch("")
.then(response => response.json())
.then(data => console.log(データ))
.catch(error => console.error(エラー));
このリクエストに対するサーバーのレスポンスに アクセス制御-許可-オリジン ヘッダーの場合、HTTPレスポンスは次のようになる:
HTTP/1.1 200 OK
Content-Type: application/json
// ❌ Access-Control-Allow-Originの欠落
このような場合、基礎となるネットワーク・リクエストが技術的に成功したかどうかにかかわらず、ブラウザの開発者ツールは以下のようなエラーを表示する:
オリジン''から'<https://api.example.com/data'へのフェッチへのアクセスは、CORSポリシーによってブロックされています:要求されたリソースに'Access-Control-Allow-Origin'ヘッダが存在しません。
テスト者はこのことから、APIのクロスオリジンアクセスが制限されているか、クロスオリジンポリシーが欠落していると判断できる。
Penligentの活用によるクロスオリジンセキュリティリスクの検出と検証
従来の侵入テストでは、クロスオリジン・ポリシーのセキュリティを評価するためには、通常、テスト担当者がブラウザ開発者ツールを使って手作業で作業する必要があった、 カール スクリプト、またはBurp Suiteのようなツールのプロキシ・キャプチャ機能を使って、HTTPレスポンス・ヘッダを1つ1つ調べて、以下のようなことが可能かどうかを判断する。 アクセス制御-許可-オリジン を適切に設定する必要がある。このプロセスは時間がかかるだけでなく、特に大規模なAPIテストシナリオを扱う場合、見落としや判断ミスが起こりやすい。
Penligentのようなインテリジェントな侵入テスト・アシスタントを導入することで、評価のワークフローを根本的に変えることができます。Penligentの シンプルな自然言語コマンド たとえば "このドメイン配下のすべてのAPIがクロスオリジン・ポリシー・リスクを持っているかどうかをチェックする"Penligentは、NmapやNucleiを含む複数のツールをオーケストレーションし、レスポンスヘッダーを一括してキャプチャ、分析します。その後、検出された問題を検証して誤検出を除外し、深刻度と悪用可能性に基づいて優先順位を付け、最終的に脆弱性の詳細、影響評価、改善勧告を含む包括的なレポートを作成します。このアプローチは、評価の深さを維持しながら、テストサイクルを劇的に短縮し、重大なリスクを見逃す可能性を大幅に低減します。
クロスオリジン・リクエストのブロックがセキュリティに与える主な影響
ペネトレーション・テスターやセキュリティ監査人にとっては access-control-allow-origin」ヘッダを使用しない。 このエラーは単なる機能的なバグとして片付けるべきではありません。むしろ、クロスオリジンアクセス制御に関するサーバーの意図を示す具体的な指標となります。APIが意図的にこのHTTPヘッダをレスポンスから除外する場合、未知の、あるいは潜在的に悪意のあるオリジンがブラウザのスクリプトを使ってドメインを越えて機密データを取得することを防ぐため、より厳格な分離を実施するという防御的な姿勢を意味することがよくあります。
例えば、開発者が環境間でAPIを移行する際に(ステージング環境から本番環境への移行など)、必要なクロスオリジン設定を行わなかったために、正当なビジネスコールがブラウザによってブロックされてしまうような場合です。さらに微妙なことですが、一貫性のないクロスオリジン設定は、攻撃者に悪用可能なエンドポイントの "パーミッションマップ "を提供し、攻撃者をオープンまたは弱体化されたインターフェースに誘導する可能性があります。したがって、意図的にクロスオリジンアクセスをブロックしているリソースと、不注意にサポートが欠如しているリソースを区別することは、セキュリ ティテストプロセスの重要な部分になります。
Access-Control-Allow-Originの誤設定に対する効果的な修正方法
検証の結果、API のクロスオリジン構成がセキュリティリスクをもたらすか、正当なビジネスフローを混乱させることが確認された場合、セキュリティの強化を図りつつ、運用の可用性を維持することを目的として是正を行うべきである。よく採用される低リスクのアプローチは、例えば、機密性の高いインターフェイスに対して許可されるオリジンを正確に指定するサーバー側のホワイトリストを実装することである:
アクセス制御-許可-オリジン
ワイルドカードの使用を避ける * というのも、クロスオリジンアクセスの問題はすぐに解決できるかもしれないが、不注意にも攻撃対象が広がってしまうからだ。これを アクセス制御許可メソッド を使用して許可されるHTTPメソッドを制限し、強固な認証とセッション管理戦略とともに、クロスオリジンアクセスが許可されたユーザーにのみ許可されることをさらに確実にすることができる。
複数のフロントエンドとバックエンドのサービスを含む複雑なシステムでは、その場しのぎの修正に頼るのではなく、アーキテクチャの計画段階でクロスオリジン・ポリシーに対処し、将来の拡張やメンテナンス時に脆弱性が再導入されるのを防ぐべきである。
結論
結論として access-control-allow-origin」ヘッダを使用しない。 このメッセージは、単にフロントエンド開発者がよく遭遇するクロスオリジンエラーではなく、侵入テスト実施者がシステムインタフェースのセキュリ ティ体制を評価するときに見落としてはならない戦略的なシグナルでもあります。このメッセージは、防御設計における意図的な注意と思慮深さを示すかもしれませんし、潜在的な設定ギャップを指し示すかもしれません。
APIやウェブアプリケーションの定期的なセキュリティ監査、特にクロスオリジンポリシーの問題を含む幅広いリスクを効率的に検出する必要がある場合、テストアシスタントとしてPenligentの採用をご検討ください。ターゲットを定義した瞬間から、自動化されたリスク発見プロセスが開始され、熟練した侵入テスト実施者の専門知識によって修復ガイダンスが提供されるため、クロスオリジン監査が時間のかかる課題から迅速かつ正確なルーチンタスクに変わります。