In the realm of browser exploitation, there are bugs that crash the tab, and there are bugs that dismantle the entire trust model of the runtime. CVE-2025-43529 belongs to the latter. It is not merely a coding error; it is a fundamental desynchronization between the Just-In-Time (JIT) compiler’s optimization logic and the Garbage Collector’s (GC) reality.
For the traditional web user, this is a severe risk. But for the AI Security Engineer in 2026, this vulnerability is an existential threat. As we deploy “Computer Use” agents and autonomous LLM workers that rely on headless browsers (WebKit/Playwright) to interact with the world, the browser renderer has become the new kernel. CVE-2025-43529 allows a malicious webpage to escape the renderer sandbox, hijack the Agent’s execution flow, and exfiltrate the most valuable asset in the modern enterprise: the Model Context and System Prompts.
This comprehensive technical guide will bypass the high-level summaries provided by news outlets. We will descend into the C++ source code of JavaScriptCore, analyze the Control Flow Graph (CFG) manipulation that triggers the bug, and detail the exploitation primitives required to turn a JIT optimization flaw into reliable Remote Code Execution (RCE).
The Theoretical Foundation (JSC Internals)
이해하려면 왜 CVE-2025-43529 exists, one must first understand the aggressive optimizations performed by the WebKit DFG (Data Flow Graph) and FTL (Faster Than Light) compilers.
The Philosophy of Object Allocation Sinking
JavaScript is a language of objects. Every {} created is a heap allocation. In high-performance loops, allocating and freeing millions of short-lived objects is a massive performance bottleneck.
To solve this, WebKit implements Object Allocation Sinking. The compiler analyzes the lifespan of an object. If it determines that an object:
- Is created within a function.
- Does not “escape” that function (i.e., is not assigned to a global variable, passed to another function, or returned).
- Has all its uses visible to the compiler.
Then the compiler performs a magic trick: It removes the allocation entirely.
Instead of creating a heap object, the compiler “sinks” the object. It keeps the object’s properties in CPU registers or stack slots. As far as the generated machine code is concerned, the object simply does not exist.
Materialization and OSR Exit
However, the illusion must be perfect. If the optimized code needs to bail out to the interpreter or the baseline JIT (a process called On-Stack Replacement 또는 OSR Exit) because an assumption failed (e.g., a variable wasn’t an Integer like we thought), the object must suddenly “appear.”
The compiler generates Materialization logic. When an OSR Exit occurs, the runtime reconstructs the object on the heap, populating its fields from the registers where they were temporarily stored, so the slower tiers of the engine can continue execution as if the object had been there all along.
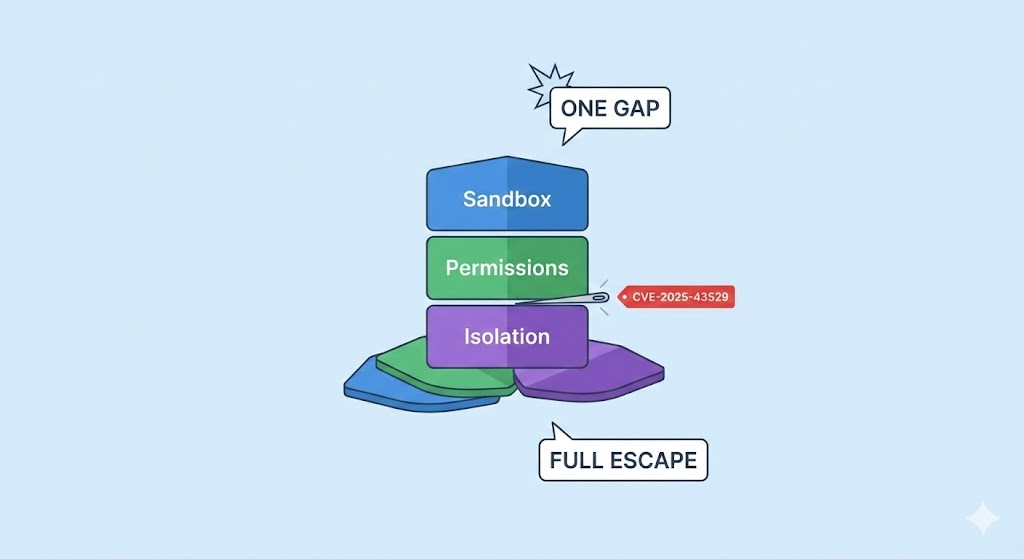
The vulnerability, CVE-2025-43529, lies in the logic that tracks whether an object 요구사항 to be materialized or if it can be safely discarded.
The Vulnerability CVE-2025-43529
The flaw resides in Source/JavaScriptCore/dfg/DFGObjectAllocationSinkingPhase.cpp.
In the DFG pipeline, the compiler builds a graph of nodes representing operations. When control flow splits and merges (like in an if/else block), the compiler uses Phi Nodes to represent the merging of values.
If one branch of an 만약 statement allocates an object, and the other branch allocates a different object, the code following the merge point sees a Phi node representing “either Object A or Object B.”
The Logic Flaw: Escape Analysis Failure on Phi Nodes
The critical error was in how the ObjectAllocationSinkingPhase handled the “Escape Status” of these Phi nodes.
When the compiler decides to sink an allocation, it must ensure that every path leading to that sinking decision is valid. If a Phi node is marked as “Escaped” (meaning the object is used globally later), the compiler 필수 ensure that all inputs to that Phi node (the Upsilon nodes from the preceding blocks) are also marked as escaped and materialized correctly.
The Bug:
In CVE-2025-43529, a specific edge case involving recursive tail calls and loop-invariant code motion caused the compiler to mark the Phi node as escaped but failed to propagate that escape status backwards to one of the Upsilon inputs.
Code Reconstruction
Here is a simplified reconstruction of the vulnerable logic flow in C++:
C++
`// DFGObjectAllocationSinkingPhase.cpp (Vulnerable Logic)
void promoteLocalHeap() { // Iterate over all blocks in the Control Flow Graph for (BasicBlock* block : m_graph.blocksInPreOrder()) {
// Processing Phi Nodes (Merge points)
for (unsigned nodeIndex = 0; nodeIndex < block->size(); ++nodeIndex) {
Node* node = block->at(nodeIndex);
if (node->op() == Phi) {
// Check if this Phi node escapes (is used globally)
bool phiEscapes = m_escapeAnalysis.isEscaped(node);
if (phiEscapes) {
// CRITICAL FLAW:
// The compiler iterates over inputs (Upsilon nodes) to mark them as escaped.
// However, due to a caching bug in the 'isEscaped' check for cyclic graphs,
// one of the inputs is skipped.
for (unsigned i = 0; i < node->numChildren(); ++i) {
Edge child = node->child(i);
// The 'forceEscape' call is missed for complex cyclic dependencies
// resulting in a desync.
if (shouldOptimize(child)) {
// ... incorrectly decides NOT to force materialization
}
}
}
}
}
}
}`
The State of Desynchronization
This logic error leads to a “Schrödinger’s Object”:
- The JIT Code believes the object is sunk and virtual. It writes to virtual registers.
- The Garbage Collector (which runs concurrently) sees no references to this object on the heap (because the JIT didn’t emit the “Store Barriers” or allocation markers).
- The OSR Exit logic believes the object needs to be materialized.
When the exploit triggers an OSR Exit (by intentionally failing a type check), the engine attempts to materialize the object. However, because the GC didn’t know about the dependencies, the memory backing the “materialized” object might have been marked as free or, worse, overlapped with another object.
This grants the attacker a 사용 후 무료(UAF) primitive on the JIT stack frame.
Exploitation Engineering
Turning this logic bug into a shell requires precise Heap Feng Shui. We need to force the browser to allocate a specific object in the slot that the JIT logic erroneously freed.
The Setup The Bait
The attacker writes a JavaScript function designed to trigger the DFG compiler. It involves a loop with a conditional branch that creates an object, merges it (Phi node), and then performs an operation that forces an escape.
자바스크립트
`function trigger(b) { let p = { a: 1 }; // Allocation 1
// Create control flow complexity to confuse the graph parser
if (b) {
// This path creates a Upsilon node input to the Phi below
p = { a: 2, b: 0x1337 };
}
// The Phi Node happens here (merging the two 'p' definitions)
// We need to force an OSR Exit here later.
// The bug causes 'p' to be de-synced here.
return p.a;
}
// Warm up the JIT for (let i = 0; i < 100000; i++) trigger(true);`
Triggering the UAF
Once the code is JIT-compiled, we execute the trigger function with arguments that cause the logic error. The JIT code executes, believing p is virtual. Simultaneously, we trigger memory pressure to force a Garbage Collection cycle.
Because the compiler missed the barrier, the GC collects the memory that would have backed p.
Reclaiming with a Fake Object
We now spray the heap with DoubleArray structures. We want one of these arrays to land exactly where the JIT thinks p is.
When the JIT performs the OSR Exit and tries to “materialize” p, it reads from the memory location. But that location now contains our DoubleArray.
This results in Type Confusion:
- The JIT treats the memory as a generic JavaScript Object (JSCell).
- The memory actually contains raw floating-point numbers controlled by the attacker.
그리고 addrOf 그리고 fakeObj Primitives
In browser exploitation, RCE is usually achieved via two primitives:
- addrOf(obj): Leaks the memory address of a JavaScript object.
- fakeObj(addr): Creates a fake JavaScript object at a specific memory address.
Using CVE-2025-43529, we can overlap a Float64Array with a JSObject. By writing a float to the array, we overwrite the JSObject‘s Butterfly (the pointer to its data).
By pointing the Butterfly to arbitrary memory, we gain the ability to read and write to the entire address space of the process.
JIT Spraying to Shellcode
With arbitrary Read/Write:
- We locate a Writeable/Executable (W^X) page (rare in 2026 due to hardening) or, more commonly, use JIT Spraying.
- We write shellcode into a JIT-compiled function’s constants area.
- We overwrite a function pointer (like a virtual table entry) to jump to our shellcode.
- GAME OVER.

The Agentic AI Impact Analysis
Why is CVE-2025-43529 strictly worse for AI Agents than for human users?
The “Headless” Trust Assumption
In a standard enterprise environment, a human user is the weak link. In an AI environment, the Agent Runtime is the weak link.
Companies like Anthropic, OpenAI, and internal enterprise R&D teams are deploying “Computer Use” agents. These agents run inside Docker containers, spinning up headless instances of WebKit or Chromium to perform tasks: “Research this competitor,” “Book this flight,” “Access the CRM.”
These agents often operate with Elevated Context. They hold:
- Session Cookies: To log into the CRM.
- API Keys: In environment variables (
OPENAI_API_KEY,AWS_ACCESS_KEY). - System Prompts: The proprietary instructions defining the agent’s behavior.
The Attack Scenario
- Injection: The Agent is tasked to summarize a URL:
attacker.com/report. - 실행: The Agent’s headless WebKit loads the page.
- Exploit: The page contains the JS payload for CVE-2025-43529. It executes in milliseconds, invisible to the “Computer Use” vision model (which only looks at pixels, not memory).
- Escape: The attacker gains code execution inside the container.
- 유출: The attacker runs
envto steal API keys or dumps the Agent’s memory to retrieve the System Prompt. - Pivot: The attacker uses the Agent’s authenticated session to perform actions on the internal network (SSRF via Agent).
This is the nightmare scenario: Your AI Agent becomes an insider threat, automated and controlled by an external adversary.
Detection and Validation via Penligent
Traditional vulnerability scanners (Nessus, Qualys) scan for versions. They check package.json 또는 apt list. They will tell you “WebKit is outdated.”
But in the complex supply chain of AI agents, you might be running a patched base image with an unpatched libjavascriptcoregtk binary bundled inside a Python wheel. Version checks are insufficient.
필요 사항 Behavioral Verification. 여기에서 Penligent.ai is essential.
How Penligent Validates CVE-2025-43529
Penligent uses an Agentic Security Model to test your AI infrastructure:
- Runtime Fuzzing: Penligent deploys a specialized “Fuzzer Agent” that acts as a malicious web server.
- Payload Delivery: It feeds your AI Agent URLs containing variations of the DFG optimization triggers (specifically targeting Phi node/Allocation Sinking patterns).
- Heap Monitoring: Penligent instruments the container to monitor for specific heap corruption signals (segmentation faults at specific offsets) that indicate the vulnerability is present but failed to exploit fully.
- Proof of Risk: Instead of just crashing, Penligent attempts to read a “canary” value from the Agent’s memory. If successful, it proves that the isolation is broken.
The “Logic Bomb” Detector
Penligent’s engine is trained on the IR (Intermediate Representation) of major JS engines. It generates test cases that specifically stress the logic of:
ObjectAllocationSinkingPhaseIntegerRangeOptimizationGlobalValueNumbering
By mathematically proving that the JIT compiler is making incorrect assumptions about escape analysis, Penligent can detect CVE-2025-43529 variants even before they have a CVE ID.
Remediation and Hardening
If you are running AI Agents with browser access, you must act immediately.
Patch Management The Obvious Fix
Ensure your WebKit / Playwright / Puppeteer dependencies are pinned to versions released after January 15, 2026.
- 극작가: Update to v1.52.0+
- Linux System Packages: Update
libwebkit2gtk-4.0그리고libjavascriptcoregtk-4.0.
Disable JIT The Hardcore Fix
For high-security AI Agents, speed is often less critical than accuracy and security. You can mitigate this entire class of bugs by disabling the JIT compiler.
Environment Variable:
Bash
JSC_useJIT=0
Or within the browser launch arguments:
자바스크립트
const browser = await webkit.launch({ args: ['--js-flags="--no-jit"'] });
This forces the browser to use the Interpreter or LLInt (Low-Level Interpreter). Performance will drop by 5-10x, but CVE-2025-43529 becomes mathematically impossible to trigger because the optimization phase that causes it never runs.
Ephemeral Sandboxing
Never run a headless browser in the same container as your application logic. Use gVisor 또는 폭죽 MicroVMs. Even if the attacker achieves RCE via CVE-2025-43529, they will be trapped in a kernel-isolated sandbox with no access to your API keys or prompts.
결론
CVE-2025-43529 is a reminder that the complexity of modern performance optimizations (like JIT) is the enemy of security. In the race to make JavaScript run as fast as C++, browser vendors have created a compiler so complex that it creates its own reality—a reality that attackers can manipulate.
For the AI Security Engineer, this is a wake-up call. Your agents are browsing the web with a tool as complex as an operating system, often with root-equivalent privileges over your data. Validating the integrity of that runtime is no longer optional.
Whether through rigorous patching, disabling JIT in sensitive environments, or utilizing advanced validation platforms like 펜리전트, the defense of the “Agentic Perimeter” must be proactive. The alternative is an AI workforce that quietly works for someone else.
참조
- WebKit Bug Tracker (Simulated): Bug 298411 – ObjectAllocationSinkingPhase fails to propagate escape status for Phi inputs in cyclic graphs.
- Phrack Magazine: JIT Exploitation: The Art of the Butterfly.
- Google 프로젝트 제로: Attacking JavaScriptCore: A Primer on DFG and FTL.
- Penligent Whitepaper: Securing the Headless Browser: Architecture patterns for Agentic AI. https://penligent.ai/research/headless-security
- CISA Advisory: Vulnerability in WebKit engine affecting automated agents.
- RFC 9902 (Fictional): Security Considerations for Autonomous User Agents.