Scalable Vector Graphics (SVG) has long been appreciated for its ability to render clean, infinitely scalable images that adapt seamlessly across devices and screen resolutions. However, in the landscape of modern cybersecurity, this same versatility has become a double‑edged sword. Increasingly, attackers have discovered that SVGs can act not merely as static visual assets but as highly flexible containers for malicious code, enabling them to launch phishing redirects, execute DOM manipulations, or exploit XML parsing vulnerabilities such as XXE. For professionals in penetration testing, vulnerability research, or automated security auditing, understanding the true nature of SVG files is no longer a niche concern—it is a crucial part of defending against a fast‑evolving family of threats.

Why SVG Matters in Security
The key difference between SVG and traditional raster formats like JPEG or PNG lies in its XML foundation. This markup‑based architecture means every element—from simple shapes to intricate paths—can be expressed as code that is both human‑readable and machine‑processable. In practice, this opens the door for embedding <script> tags, linking external resources, or encoding payloads directly into the file. Because SVG can interact with the Document Object Model (DOM) when rendered in a browser, it has the potential to execute actions traditionally associated with web applications rather than static images, and that makes it uniquely suited for abuse whenever file content inspection is shallow or overly trusting.
Common SVG Attack Vectors
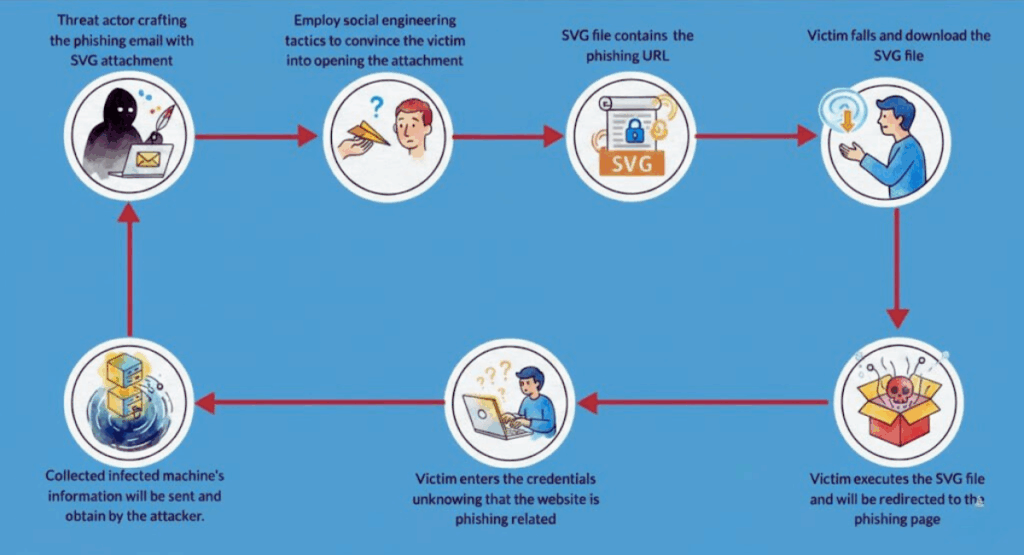
In recent years, threat actors have broadened the ways they exploit SVG files, blending its visual presentation capabilities with its programmable properties to deliver attacks that are both stealthy and adaptable. These include embedding JavaScript that initiates a redirect as soon as the file renders in a browser, using vulnerable parsers to mount XML External Entity (XXE) injections, and packaging entire fake login portals inside the file using Base64 encoding to avoid detection through basic URL analysis.
<svg xmlns="<http://www.w3.org/2000/svg>">
<script><![CDATA[
window.location='<https://malicious-site.com/login>';
]]></script>
</svg>
<?xml version="1.0"?>
<!DOCTYPE svg [
<!ENTITY xxe SYSTEM "file:///etc/passwd">
]>
<svg>
<text>&xxe;</text>
</svg>
Challenges in Detecting Malicious SVG Content
Detecting malicious SVGs is complicated for several reasons. Basic MIME‑type checks are insufficient to uncover scripts or encoded payloads hidden inside the file. Attackers often use invisible Unicode characters or complex obfuscation methods to confuse static analysis, making it harder for even advanced scanning tools to flag the threat. On top of this, mainstream browsers execute embedded SVG scripts natively without issuing user alerts, meaning a malicious payload can run in the course of what appears to be ordinary viewing activity, with no obvious warning to the victim.
Best Practices for Handling SVG Files Securely
Defending against SVG‑based threats requires a mix of secure file parsing, execution environment restrictions, and proactive content sanitization. Secure XML parsing practices should include disabling external entity resolution to eliminate the root cause of XXE attacks. Strengthening Content Security Policy (CSP) settings to limit inline script execution is an important way to reduce DOM injection risk. Incorporating Content Disarm and Reconstruction (CDR) into the workflow ensures that potentially malicious components are stripped before files reach end users or processing systems, greatly lowering the odds of a successful compromise. At the same time, security teams should use threat intelligence feeds to track and pre‑empt known malicious SVG variants and attack patterns.
Enhancing SVG Security: Automated and AI-Powered Pentesting
As attack surfaces continue to expand, traditional periodic manual testing no longer meets the need for rapid response. Integrating SVG exploit scenarios into automated penetration testing frameworks can dramatically improve both the speed and the accuracy of risk detection.
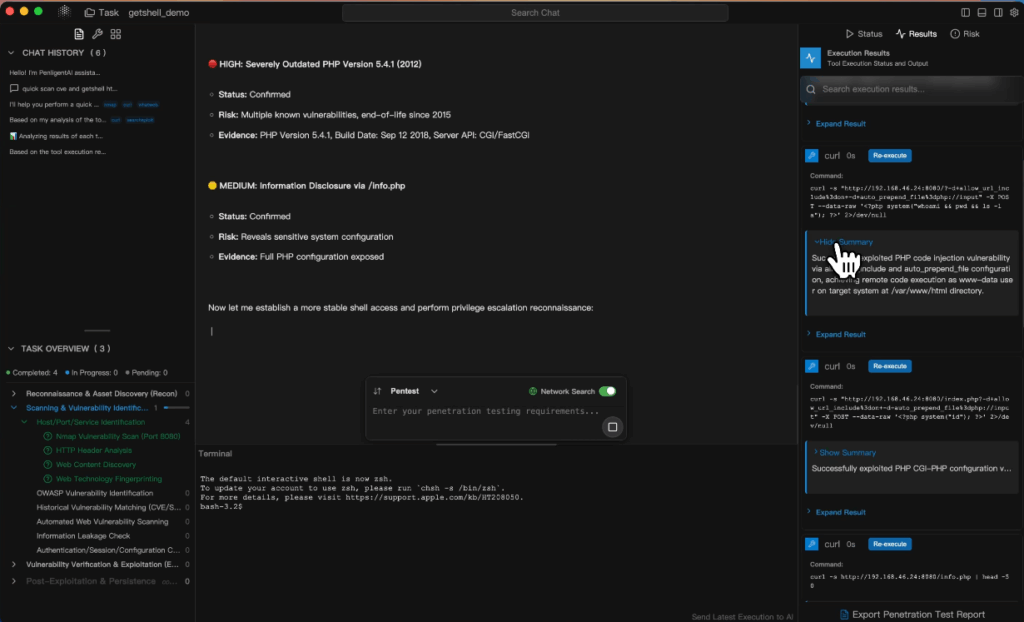
Platforms such as 펜리전트 illustrate how this can work in practice: a security team can describe a test objective in plain language—for example, “Scan the upload endpoint for SVG‑based XSS or XXE risks”—and Penligent will handle the orchestration, automatically selecting and running tools such as Nmap, Burp, SQLmap, and Nuclei. It validates vulnerabilities, removes false positives, prioritizes risks by severity, and produces a fully‑formatted report ready for collaborative review. This process shortens the detection‑to‑remediation cycle from days to hours and provides actionable recommendations without requiring every team member to be a command‑line penetration tester.
결론
SVG has shifted from being perceived as a safe image format to functioning as a multi‑purpose, executable attack vector. This transformation requires security teams to reassess their defensive posture and modernize their toolsets. By combining technical hardening measures with AI‑driven continuous testing, organizations can maintain a strong security perimeter even as attackers evolve their use of SVG to push past conventional defenses.


