Para engenheiros de segurança de IA e profissionais de DevSecOps que gerenciam fluxos de trabalho automatizados, CVE-2025-68668 representa uma falha crítica nas camadas de isolamento da orquestração moderna de IA.
Como as organizações dependem cada vez mais de n8n Para unir LLMs (Large Language Models), bancos de dados vetoriais e APIs internas, a integridade do ambiente de execução do fluxo de trabalho torna-se fundamental. Essa vulnerabilidade, um desvio crítico de sandbox no n8n Python Code Node, demonstra exatamente por que o "sandboxing" em ambientes interpretados é notoriamente difícil de proteger.
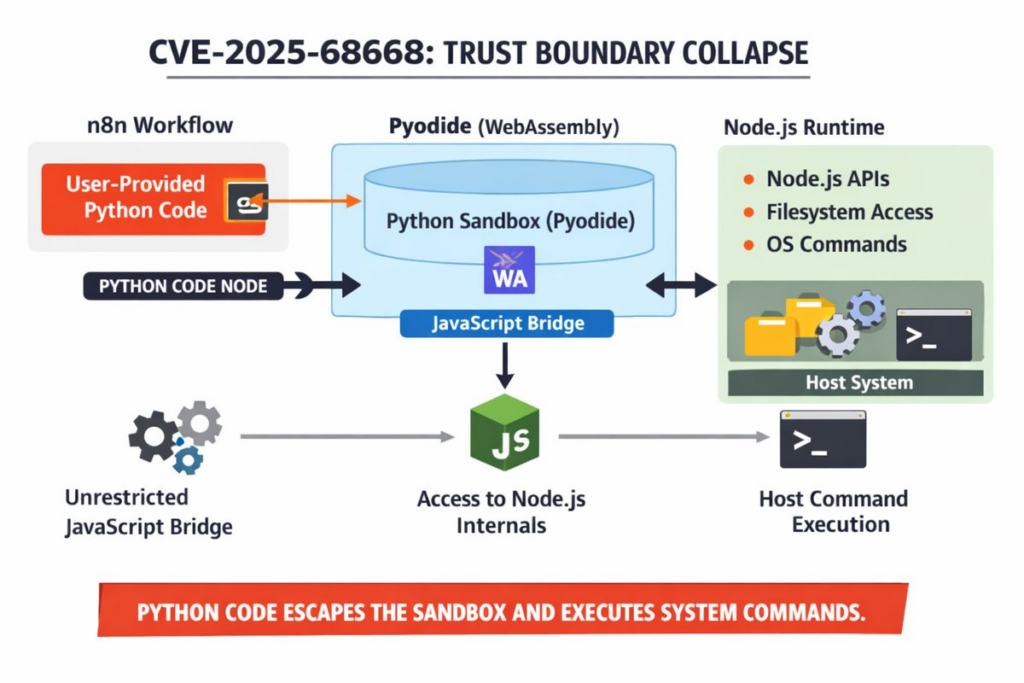
A anatomia do CVE-2025-68668
Em sua essência, o CVE-2025-68668 (CVSS 9.9) é um Falha no mecanismo de proteção afetando as versões do n8n a partir de 1.0.0 até 2.0.0. Ele tem como alvo específico a implementação do Python Code Node que depende de Piodetouma porta do CPython para WebAssembly/Emscripten.
Embora o Pyodide tenha sido projetado para executar o Python com segurança em ambientes restritos, a implementação no backend do n8n não conseguiu impor rigorosamente os limites de isolamento.
O mecanismo de desvio técnico
A vulnerabilidade permite que um usuário autenticado (com privilégios de criação/modificação de fluxo de trabalho) para sair do ambiente Pyodide. Em uma configuração segura padrão, o nó de código Python deve restringir o acesso às bibliotecas padrão do host, especificamente os, subprocessoe sistema.
No entanto, em versões vulneráveis, o mecanismo de importação permite que os invasores acessem o shell do sistema host subjacente. Ao criar uma carga útil Python específica dentro do editor de fluxo de trabalho, um invasor pode executar comandos arbitrários com os mesmos privilégios do próprio processo n8n (geralmente raiz em ambientes Dockerizados).
Perfil de vulnerabilidade:
| Recurso | Detalhes |
|---|---|
| ID DO CVE | CVE-2025-68668 |
| Componente de destino | n8n Nó de código Python (Pyodide) |
| Tipo de vulnerabilidade | Contorno de sandbox / RCE |
| Pontuação CVSS | 9,9 (Crítico) |
| Vetor | Rede (autenticada) |
| Impacto | Comprometimento total do host |
Análise de código: Conceituando a exploração
Observação: o bloco de código a seguir é para análise educacional e defensiva. Não o utilize em sistemas que não sejam de sua propriedade.
A exploração aproveita a capacidade de acessar o sistema de arquivos do host ou o tratamento de processos, apesar do invólucro do Pyodide. Uma lógica de desvio típica envolve a reimportação de módulos restritos ou a utilização do js (se exposta) para fazer a ponte de volta ao contexto do host do Node.js.
Python
`# Representação conceitual da lógica de escape do Sandbox
Em uma instância vulnerável do n8n, o isolamento não consegue bloquear chamadas específicas do sistema.
try: # Tentativa de acessar as variáveis de ambiente do host ou o sistema de arquivos import os import subprocess
# Se o sandbox fosse eficaz, isso geraria um PermissionError ou ImportError
# No CVE-2025-68668, isso é executado com êxito no host.
output = subprocess.check_output(['whoami'])
print(f "Sandbox Broken. Usuário: {output.decode('utf-8')}")
# Os invasores podem, então, fazer o dump dos arquivos .env que contêm as chaves do OpenAI/AWS
# malicious_payload = subprocess.check_output(['cat', '/home/node/.n8n/config'])
exceto Exception as e: print("Environment Secure or Patched.")`
Por que isso é importante para os engenheiros de segurança de IA
Essa não é apenas uma vulnerabilidade padrão da Web; é uma risco da cadeia de suprimentos para agentes de IA.
- Coleta de credenciais: Os fluxos de trabalho da n8n são tesouros de segredos de alto valor: Chaves de API da OpenAI, credenciais do Pinecone vector DB e tokens de acesso ao AWS. Uma exploração bem-sucedida concede acesso imediato a essas variáveis de ambiente.
- Envenenamento por modelo: Um invasor com RCE pode interceptar os dados que fluem para seus pipelines RAG (Retrieval-Augmented Generation), envenenando a janela de contexto ou alterando a saída do modelo antes que ele chegue ao usuário final.
- Movimento lateral: Como o n8n geralmente fica dentro da VPC para acessar bancos de dados internos, um nó comprometido atua como um ponto de articulação ideal para o movimento lateral na rede interna.
Validação da ameaça com pentesting automatizado
A detecção do CVE-2025-68668 representa um desafio para os scanners de vulnerabilidade tradicionais. As ferramentas DAST (Dynamic Application Security Testing) padrão geralmente procuram cabeçalhos de versão ou códigos de erro HTTP simples. Elas não têm a lógica para autenticar, criar um fluxo de trabalho, injetar um trecho de Python e validar se o código foi executado no host.
É aqui que Teste de penetração orientado por IA torna-se essencial.
Penligente utiliza agentes autônomos de IA que imitam o comportamento de um engenheiro de segurança humano. Em vez de depender de assinaturas estáticas, os agentes da Penligent podem:
- Contextualizar: Entenda que o alvo é uma instância do n8n.
- Autenticar: Use as credenciais fornecidas para acessar o editor de fluxo de trabalho.
- Sintetizar cargas úteis: Gerar dinamicamente código Python destinado a testar os limites da área restrita com segurança (por exemplo, tentar ler um arquivo temporário não sensível).
- Verificar: Analise a saída da execução para confirmar se a sandbox foi realmente contornada, eliminando falsos positivos comuns em scanners legados.
Ao integrar a Penligent ao seu CI/CD ou às auditorias de segurança regulares, você garante que vulnerabilidades lógicas como a CVE-2025-68668 sejam detectadas antes que possam ser exploradas na produção.
Estratégias de remediação e mitigação
Para proteger sua infraestrutura de automação de IA contra o CVE-2025-68668, é necessário agir imediatamente.
1. Faça o upgrade imediatamente
A principal correção é atualizar o n8n para a versão 2.0.0 ou superior. A equipe do n8n refatorou completamente o modelo de execução do Python na versão 2.0 para fornecer um executor python nativo seguro por padrão.
2. Desativar nós de código Python (temporário)
Se a atualização não for viável imediatamente, você poderá reduzir o risco desativando o tipo de nó vulnerável por meio de variáveis de ambiente:
Bash
# Desative o suporte a Python no nó Code export N8N_PYTHON_ENABLED=false
3. Restringir permissões de fluxo de trabalho
Como essa é uma vulnerabilidade autenticada, aplique o Princípio do Menor Privilégio (PoLP). Certifique-se de que somente engenheiros confiáveis tenham permissões de "Criador de fluxo de trabalho". Audite sua lista de usuários imediatamente.
Conclusão
O CVE-2025-68668 serve como um lembrete claro de que, à medida que abstraímos a complexidade com ferramentas de IA de baixo código, introduzimos novas camadas de risco. A natureza de "caixa preta" da execução de código em sandbox exige uma validação rigorosa e contínua.
Para o engenheiro de segurança moderno, confiar no gerenciamento de patches é necessário, mas insuficiente. Adotar plataformas automatizadas de segurança ofensiva como Penligent.ai permite que as organizações testem continuamente a resiliência dessas integrações complexas, garantindo que seus agentes de IA permaneçam servidores, e não sabotadores em potencial.


