JSON Web İmzası (JWS) decoding is the process of parsing and verifying the components of a JWS token—header, payload, and signature—to extract the signed data and check its integrity. In security and penetration testing contexts, decoding a JWS helps analysts understand what claims are embedded, detect misconfigurations, and identify weak signing practices that can lead to vulnerabilities such as signature bypass or token forgery.
This article explains why JWS decoding matters, how to decode and verify signatures using real code, common pitfalls, security implications, and defense strategies you should know in 2025.
What Is JSON Web Signature (JWS)?
JSON Web İmzası (JWS) is a compact, URL-safe means of representing a signed message. It is defined in RFC 7515 and commonly used to ensure the authenticity and integrity of data transferred over REST APIs, single sign-on (SSO), and microservices authentication flows.
A typical JWS token looks like:
nginx
eyJhbGciOiJFUzI1NiIsInR5cCI6IkpXVCJ9. eyJzdWIiOiIxMjM0NTY3ODkwIiwibmFtZSI6IkpvZSJ9 . MEUCIQDh...
Each segment is Base64URL encoded:
- Başlık — describes the algorithm and token type
- Payload (Claims) — the signed data
- İmza — proof of integrity
Decoding a JWS without verifying the signature reveals claims, but only verification proves they came from a trusted source.
Authoritative standard: RFC 7515 — https://tools.ietf.org/html/rfc7515

Why Decode a JWS? Security & Testing Perspectives
Decoding a JWS serves several purposes:
- Understand embedded claims: Who is the user? What are permissions?
- Identify signing algorithm: Weak algorithms (e.g.,
HiçbiriveyaHS256with predictable keys) - Assess integrity: Detect tampered tokens
- Discover vulnerabilities: Signature bypass, algorithm downgrade attacks
From an offensive security angle, discovering weak JWS signing practices can lead to exploits where attackers forge tokens and escalate privileges.
Anatomy of a JWS Token
Here’s a breakdown of a typical token:
| Segment | Meaning | Örnek |
|---|---|---|
| Başlık | Algorithm & metadata | { “alg”: “RS256”, “typ”: “JWT” } |
| Yük | Claims | { “sub”: “12345”, “role”: “admin” } |
| İmza | Signed digest | Base64URL of encrypted header+payload |
A decoded JWS shows plain JSON for header and payload:
ini
HeaderJSON = base64url_decode(part1)PayloadJSON = base64url_decode(part2)
Decoding doesn’t prove authenticity — only signature verification does.
Simple JWS Decode (Without Verification)
In security triage, often the first step is seeing what’s inside:
Python Example (Decode Only)
python
import base64import json def base64url_decode(input_str): rem = len(input_str) % 4 input_str += "=" * (4 - rem)return base64.urlsafe_b64decode(input_str) token = "eyJhbGciOiJSUzI1NiIsInR5cCI6IkpXVCJ9.eyJzdWIiOiIxMjMifQ.SflKxw..."header, payload, signature = token.split('.') header_json = json.loads(base64url_decode(header)) payload_json = json.loads(base64url_decode(payload)) print("Header:", header_json)print("Payload:", payload_json)
This outputs readable JSON but doesn’t validate whether the signature is correct.
Verifying a JWS Signature (Security-Critical)
To be confident the token is legitimate, you must verify the signature using the expected algorithm and key. Here’s how:
JavaScript (Node.js) Example Using jose
javaScript
import { jwtVerify } from "jose"; const token = "eyJ..."; const publicKey = /* load appropriate public key, e.g., from JWKS endpoint */; async function verifyToken() {try {const { payload } = await jwtVerify(token, publicKey);console.log("Verified payload:", payload); } catch (e) {console.error("Verification failed:", e); } } verifyToken();
This ensures the token was signed by the correct private key corresponding to the public key.
Real-World Example: Decoding an OAuth Token
Many APIs issue JWS tokens for access control. Decoding reveals user and session info:
json
{ "iss": "<https://auth.example.com>", "sub": "alice", "exp": 1700000000, "scope": "read write" }
Security teams review decoded tokens to audit scopes and expiration times.
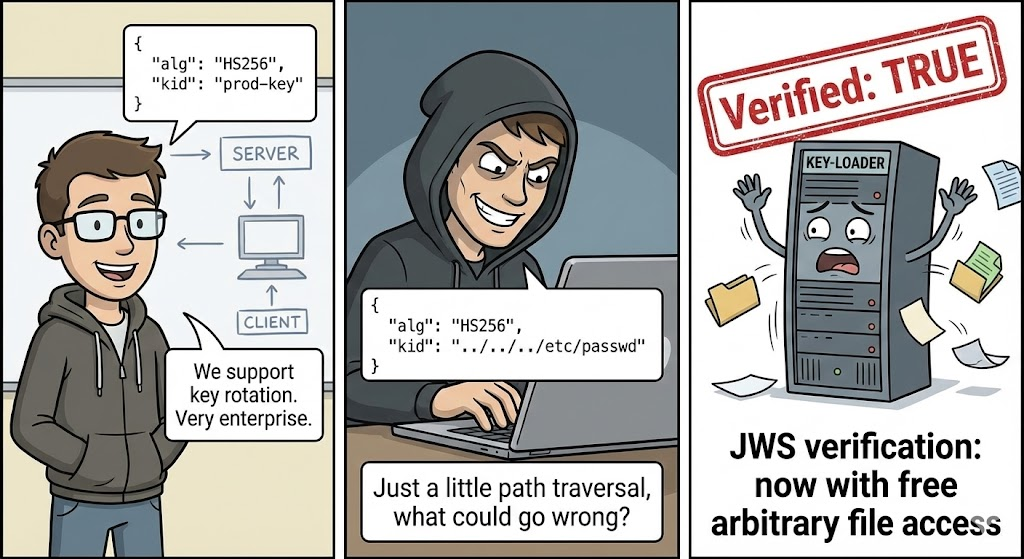
Common Vulnerabilities in JWS Implementations
Algorithm Downgrade
Some libraries incorrectly allow changing alg için Hiçbiri, enabling attackers to bypass verification.
Unsafe header example:
json
{"alg":"none","typ":"JWT"}
Attack defense: Always reject tokens with alg: none unless explicitly safe in context.
Weak Symmetric Keys (HS256)
Using weak or predictable symmetric keys allows attackers to guess the key and forge tokens.
Hafifletme:
- Use strong secret keys (≥ 256 bits)
- Prefer asymmetric algorithms (
RS256,ES256)
CLI Tools for Quick JWS Decoding
| Alet | Açıklama | Official |
|---|---|---|
| jwt.io Debugger | Web-based decode & verify | https://jwt.io |
| jose CLI | Node-based decode/verify | https://github.com/panva/jose |
| jwt-cli | Cross-platform CLI | https://github.com/mike-engel/jwt-cli |
Example CLI decode:
bash
jwt decode eyJhbGciOi...
Vulnerability Scenario: Forging a Token (Proof-of-Concept)
If a server incorrectly accepts alg: none, an attacker can forge:
css
Header: {"alg":"none","typ":"JWT"} Payload: {"sub":"attacker","role":"admin"} Signature: ""
Proof-of-Concept Script (Python):
python
import base64import json def b64url(x): return base64.urlsafe_b64encode(x).rstrip(b'=').decode() header = {"alg":"none","typ":"JWT"} payload = {"sub":"attacker","role":"admin"} token = f"{b64url(json.dumps(header).encode())}.{b64url(json.dumps(payload).encode())}."print("Forged token:", token)
Savunma:
- Reject tokens where
algisHiçbiriunless explicitly safe - Enforce algorithm whitelist
Why Signature Verification Matters in 2025
In modern microservices and distributed APIs, tokens drive access decisions. Improper verification can lead to:
- Ayrıcalık yükseltme
- Yetkisiz erişim
- Session hijacking
Penetration testers and defenders must be able to decode and validate tokens programmatically and at scale.
Detecting Broken Verification in APIs
Automated scanners can check if an API attempts to accept invalid JWS signatures.
Python Pseudocode (Security Check)
python
def test_broken_verification(api_url, forged_token): headers = {"Authorization": f"Bearer {forged_token}"} response = requests.get(api_url, headers=headers)return response.status_code bad_api = test_broken_verification("<https://api.example.com/data>", forged_token)if bad_api == 200:print("Potentially vulnerable to JWS forgery")
If the API responds with 200 OK, the token acceptance logic may be flawed.
Defensive Best Practices
| Defense | Açıklama |
|---|---|
| Use Asymmetric Keys | Prefer RS256, ES256 over symmetric keys |
| Enforce Algorithm Whitelisting | Reject unexpected alg values |
| Short Token Lifetimes | Minimize replay risk |
| Key Rotation | Update signing keys regularly |
| Audit Token Libraries | Keep dependencies up to date |
Integrating Token Decoding into CI/CD Security
In 2025, security pipelines often automatically validate JWS practices:
- Automated linting of JWT configurations
- CI test that rejects insecure libs
- Runtime monitoring for bad token acceptance
Example CI Script Snippet (Bash):
bash
#Reject if any code uses "alg: none"grep -R '"alg": *"none"' ./src && exit 1
Related Concepts: JWE vs JWS
| Term | Meaning |
|---|---|
| JWS | JSON Web Signature (signed only) |
| JWE | JSON Web Encryption (encrypted) |
JWE protects confidentiality; JWS protects integrity and authenticity. Many systems use both together.
Tools and Libraries (2025 Security Stack)
- Node.js
jose— JWT/JWS decode & verify - Python
python-jose— Flexible cryptography support - OpenSSL — Low-level crypto verification
- jwt.io — Quick web decoder


