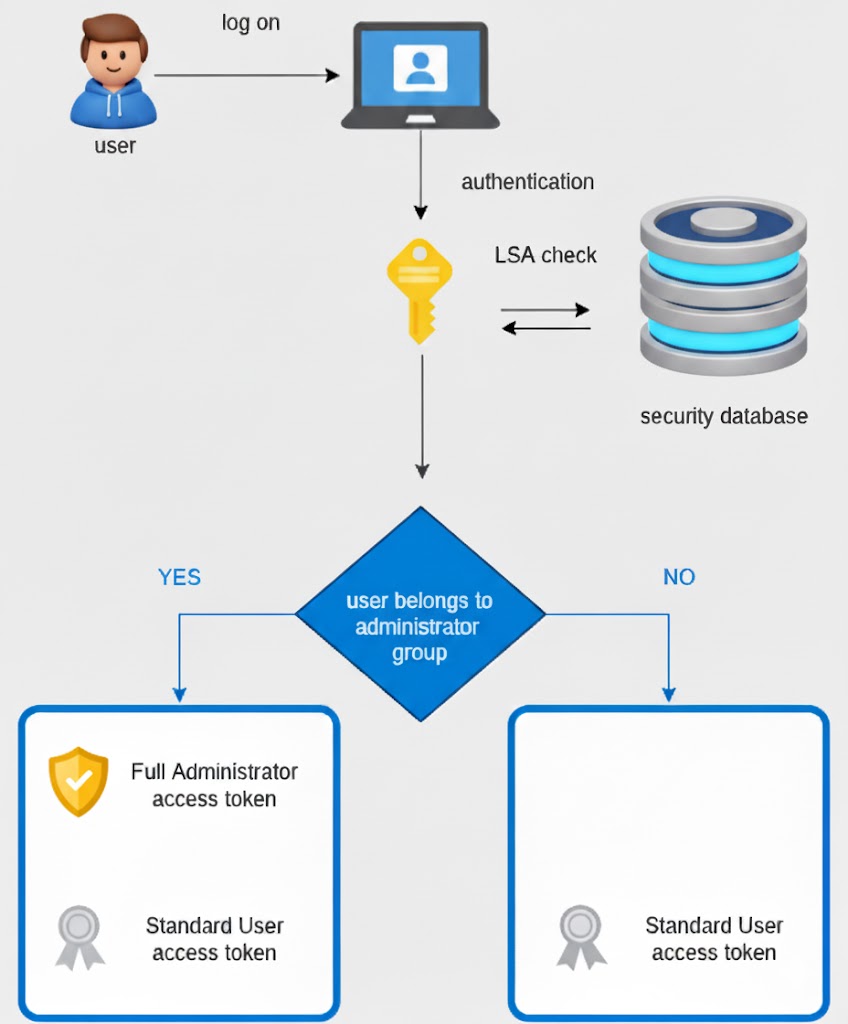
Bu Kimlik Doğrulama Jeton Manipülasyon Hatası genellikle şu durumlarda ortaya çıkar Linux kullanıcıları gibi komutları kullanarak parolaları değiştirmeye çalışın passwd. Basit bir operasyonel aksaklık gibi görünse de, güvenlik araştırmacıları ve DevSecOps mühendisleri için bu hata genellikle kimlik doğrulama iş akışlarında yanlış yapılandırılmış sistemlerden istismar edilebilir güvenlik açıklarına kadar daha derin sorunların bir işaretidir. Bunu ihmal etmek, ortamınızı ayrıcalık yükseltme, oturum ele geçirme ve hassas veri sızıntılarına maruz bırakabilir.

Sistem ve Otomasyon Ortamlarında Kimlik Doğrulama Simgesi Manipülasyonu Hata Nedenleri
| Neden Kategorisi | Spesifik Neden | Tipik Senaryo Örneği |
|---|---|---|
| Sistem Seviyesi | Yanlış yapılandırılmış PAM modülü ayarları | /etc/pam.d/common-password misconfig token güncellemesini engelleme |
Yanlış /etc/shadow izinler | İzinler 0640 olarak ayarlanmamış | |
| Kök bölüm salt okunur olarak bağlandı | Kritik kimlik doğrulama dosyalarına yazılamıyor | |
| Disk alanı dolu | Dosya yazma işlemleri başarısız | |
| Dosya sistemi hataları | Küçük yolsuzluk gerektiren fsck ONARIM | |
| Otomasyon/CI/CD | Boru hattı yeterli ayrıcalıklar olmadan çalışır | Konteynerler eksik --ayrıcalıklı bayrak |
| Bağımlı işler bitmeden önce belirteçleri temizleyen geçici ortamlar | Belirteç işlem ortasında kaldırıldı | |
| Yapılarda doğrudan işletim sistemi düzeyinde şifre manipülasyonu | Güvenli belirteç işleme ilkelerini ihlal eder |
Kimlik Doğrulama Simgesi Manipülasyon Hatası Güvenlik Riskleri
Yinelenen token manipülasyon hataları, kimlik doğrulama tasarımındaki sistemik zayıflıklar için kırmızı bayrak olabilir. CI/CD işlem hatlarında yanlış yönetilen belirteçler, MITM saldırıları yoluyla ele geçirilebilir veya derleme günlüklerinde ifşa edilebilirken, aşağıdaki gibi hassas dosyalarda uygunsuz izinler /etc/shadow saldırganların parola karmalarını çalmasına ve çevrimdışı kırma girişiminde bulunmasına izin verebilir.
Operasyonlar ve Güvenlik İyileştirmesi
Adresleme Kimlik Doğrulama Simgesi Manipülasyon Hatası etkili bir şekilde, temel nedenin ortadan kaldırıldığından emin olmak için her düzeltmenin doğrulama ile uygulandığı metodik bir süreç gerektirir. Geçici kilitlenmelerden veya durmuş kimlik doğrulama oturumlarından şüpheleniliyorsa, kontrollü bir yeniden başlatma bu geçici durumları temizleyebilir:
sudo yeniden başlat
Yanlış yapılandırılmış PAM (Takılabilir Kimlik Doğrulama Modülü) yığınları muhtemelen token güncellemelerini engelliyorsa, bunları yükseltilmiş ayrıcalıklarla yeniden yapılandırmak düzgün token kullanımını sağlar:
sudo pam-auth-update
Kök bölümün beklenmedik bir şekilde salt okunur modda bağlandığı durumlarda, yazma izinleriyle yeniden bağlama güncelleme özelliğini geri yükler:
sudo mount -o remount,rw /
Şunu doğrulayın /etc/shadow güvenli izinlere sahiptir (0640), meşru erişim ile yetkisiz maruz kalmaya karşı koruma arasında denge kurar:
sudo chmod 0640 /etc/shadow
Gibi araçlarla aşırı disk kullanımını temizleyin BleachBit veya FSlint yazma hatalarını önlemek için. Son olarak, dosya sistemi bozulmasından şüpheleniliyorsa, etkilenen birimin bağlantısını kaldırın, aşağıdakileri kullanarak onarın fsck, kritik verileri yedekleyin ve üretim kullanımı için yeniden bağlayın:
# Etkilenen birimlerin bağlantısını kaldırudo umount /dev/sdXn
# Dosya sistemi kontrolünü ve onarımını çalıştırudo fsck -f /dev/sdXn
# Kritik verileri yedekleyinudo tar -cvzf /mnt/backup/critical-data.tar.gz /mnt/production-data
# Üretim kullanımları için yeniden bağlaudo mount /dev/sdXn /mnt/production
Token Güvenliği için DevSecOps En İyi Uygulamaları
Tekrarlamasını önlemek için Kimlik Doğrulama Simgesi Manipülasyon HatasıDevSecOps iş akışlarının tüm aşamalarına güvenli token yönetimini yerleştirin. Statik kimlik bilgilerini HashiCorp Vault veya AWS Secrets Manager gibi sistemlerde yönetilen gizli dizilerle değiştirin, kısa ömürlü kapsam belirteçlerini uygulayın, işlem hatlarında doğrudan işletim sistemi düzeyinde parola manipülasyonundan kaçının ve yürütmeden önce otomatik ortam kontrolleri gerçekleştirin. Güvensiz uygulamaları tespit etmek için statik kod analizini, aktif riskleri belirlemek için dinamik çalışma zamanı taramasıyla birleştirerek sürekli token güvenliği sağlayın.
Kimlik Doğrulama Simgesi Manipülasyon Hatasını Tespit ve İstismar Etme
Ne zaman Kimlik Doğrulama Simgesi Manipülasyon Hataları Kimlik doğrulama akışlarında daha derin kusurlar olduğunu öne süren Penligent, tespit ve düzeltme işlemlerini kolaylaştırır. Nmap, Burp Suite veya SQLmap gibi araçları manuel olarak zincirlemek yerine sade dil - Örneğin, "Belirteç manipülasyonu için tara". Penligent, 200'den fazla entegre araç arasından seçim yapacak, hedefli testler gerçekleştirecek, gerçek güvenlik açıklarını doğrulayacak ve önceliklendirilmiş bir iyileştirme raporu oluşturmadan önce yanlış pozitifleri filtreleyecektir.
Sonuç
Bu Kimlik Doğrulama Simgesi Manipülasyon Hatası kimlik doğrulamada hızla ele alınması gereken potansiyel kusurlara işaret eder. Penligent gibi araçlarla güvenli token uygulamalarını ve otomatik güvenlik kontrollerini entegre etmek, esnek kimlik doğrulama sağlar ve ihlal riskini azaltır.