Arkadaşlık Uygulamaları Neden Yüksek Riskli Platformlardır?
Son yıllarda çevrimiçi flört, niş bir etkinlikten modern sosyal yaşamın günlük bir parçası haline geldi ve araştırmalar her üç kişiden birinin potansiyel partnerlerle tanışmak için flört uygulamalarına başvurduğunu gösteriyor. Ancak, kolaylıklarına ve kültürel yaygınlıklarına rağmen, bu platformların siber güvenlik duruşu endişe verici derecede zayıf kalmaktadır. Business Digital Index'in son raporuna göre, en yaygın kullanılan arkadaşlık uygulamalarının 75%'si hala temel güvenlik standartlarını karşılayamıyor ve milyonlarca kullanıcının en mahrem bilgilerini - cinsel yönelim ve kişisel fotoğraflardan hassas GPS konumlarına, özel sohbet geçmişlerine ve hatta ödeme kartı verilerine kadar - önemli risk altında bırakıyor.
Bu teorik bir endişe olmaktan çok uzaktır. Tarih, bu sektördeki güvenlik hatalarının ne kadar zarar verici olabileceğini defalarca göstermiştir. 2015 yılında Ashley Madison ihlali otuz milyon kişinin kişisel verilerini açığa çıkarmış, boşanmaları, şantaj girişimlerini ve birkaç doğrulanmış intihar vakasını tetiklemiştir. Bir yıl sonra, AdultFriendFinder tarihin en büyük ihlallerinden birine maruz kaldı ve açık cinsel tercih verileri de dahil olmak üzere dört yüz milyon kayıt çevrimiçi olarak sızdırıldı. Ve 2020'de Zoosk, ShinyHunters grubu tarafından ele geçirildi ve gelir, doğum tarihleri ve siyasi görüşler gibi son derece kişisel ayrıntıları içeren yirmi dört milyon kaydın çalınmasıyla sonuçlandı.
Bu olaylar birlikte ele alındığında net ve rahatsız edici bir tablo ortaya çıkıyor: arkadaşlık uygulamaları siber suçlular için birincil hedef olmaya devam ediyor ve güvenlikleri başarısız olduğunda, sonuçlar son derece kişisel olabilir ve genellikle dijital alanın çok ötesine geçerek kullanıcılarının gerçek yaşamlarında kalıcı zararlara yol açabilir.

Arkadaşlık Uygulamaları Güvenlik Açığı Analizi
| Kategori | Spesifik Güvenlik Açığı | Örnek Etki |
|---|---|---|
| Harici | Zayıf E-posta Kimlik Doğrulaması (eksik SPF, DMARC, DKIM) | Kimlik avı ve marka sahteciliği kampanyalarını etkinleştirir |
| Yamalanmamış Yazılım Açıkları | Uzaktan kod çalıştırmaya, kolay istismara izin verir | |
| Zayıf TLS/Şifreleme Yapılandırması | MITM saldırılarını ve veri müdahalesini kolaylaştırır | |
| Dahili | Kimlikle bağlantılı verilerin sızması (işyeri, okul isimleri) | Sosyal mühendislik, hedefli taciz |
| Veri İletimi Sırasında SSL/TLS Eksikliği | Verilerin ele geçirilmesi ve manipülasyonu | |
| Sertifika Doğrulama Hatası | MITM saldırılarına karşı duyarlı | |
| Kötü Token Yönetimi | Mesajlara ve fotoğraflara yetkisiz erişim |
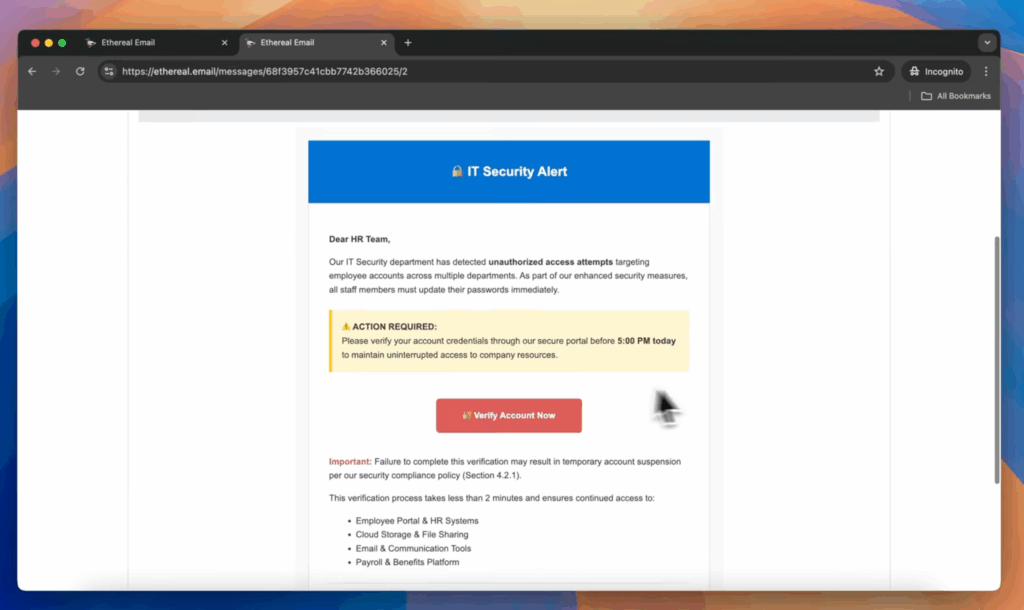
Arkadaşlık Uygulamaları için Sızma Testi - Penligent'ı Kullanma Kimlik Avı Simülasyonu
Güvenlik araştırmacıları ve sızma test uzmanları için, flört uygulamalarının dayanıklılığını değerlendirmek genel güvenlik açığı taramasından daha fazlasını gerektirir - hedeflenen teknik araştırmayı sosyal mühendisliğin insan güvenini nasıl istismar ettiğine dair derin bir anlayışla harmanlayan çok katmanlı bir yaklaşım gerektirir. Saldırganlar genellikle kimlik avı, gözetleme veya veri sızdırma kampanyaları yürütmek için konum tabanlı eşleştirme, profil meta verileri ve uygulama içi mesajlaşma gibi flört ekosistemlerine özgü özelliklerden yararlanır.
Veri Sızıntısı için API Fuzzing
Kişisel verileri veya konum verilerini sızdırabilecek zayıf girdi doğrulamasını, eksik erişim denetimlerini veya yanlış yapılandırılmış yanıt başlıklarını belirlemek için mobil ve web API uç noktalarına karşı yapılandırılmış bulanıklaştırma gerçekleştirin.
Profil, mesajlaşma ve coğrafi konum hizmetleriyle ilgili uç noktaları hedef alın, çünkü bunlar genellikle kritik gizlilik verilerine sahiptir.
# Örnek: API bulanıklaştırma için OWASP ZAP kullanma
zap-cli başlat
zap-cli open-url
zap-cli fuzz --context "DatingAppAPI" --payloads payloads/location-data.txt
zap-cli report --output report_api_fuzz.html
zap-cli durdurma
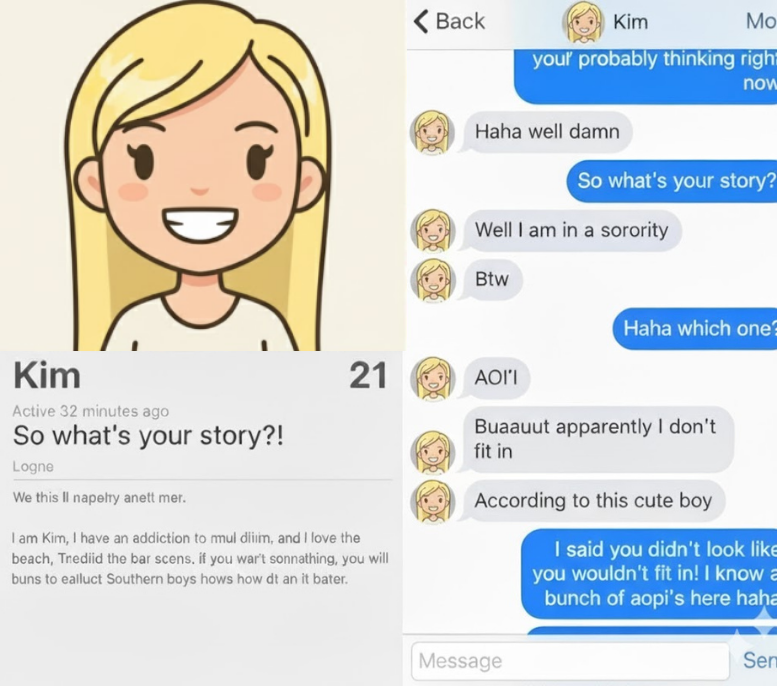
Romantik Dolandırıcılıkları Önlemek için E-posta Kimlik Doğrulama Denetimleri
Doğrulama veya eşleşme bildirimleri göndermek için kullanılan etki alanları için SPF, DKIM ve DMARC yapılandırmalarını inceleyin.
Zayıf veya eksik kayıtlar, saldırganların flört uygulaması e-postalarını taklit etmesine ve kullanıcıları kimlik avı sayfalarına çekmesine olanak tanır.
# SPF, DKIM, DMARC kayıtlarını kontrol edin
dig datingapp.com TXT | grep spf
dig datingapp.com TXT | grep dmarc
# DKIM'i kullanarak doğrulayın
opendkim-testkey -d datingapp.com -s default -k /etc/opendkim/keys/default.txt
TLS Yapılandırması ve MITM Saldırılarının Önlenmesi
TLS/SSL uygulamalarının gücünü test edin ve mobil uygulamanın sertifika sabitlemeyi zorunlu kıldığından emin olun.
Eski şifre paketleri veya eksik sabitleme, özel sohbetlerin veya konum güncellemelerinin ele geçirilmesini sağlar.
# Örnek: SSLyze'ı Kullanma
sslyze --regular datingapp.com
# Mobil uygulama TLS sabitleme kontrolü
frida -U -f com.datingapp.mobile --no-pause -l check_tls_pinning.js
Belirteçler ve Ortamlar için Depolama ve Erişim Kontrolünün Denetlenmesi
Kimlik doğrulama belirteçlerinin, özel fotoğrafların ve sohbet geçmişlerinin cihazlarda ve arka uç sistemlerde nasıl saklandığını inceleyin.
Belirteçlerin beklemede şifrelendiğinden, erişim kontrollü olduğundan ve doğrudan API yanıtlarına veya günlüklerine gömülmediğinden emin olun.
Penligent Ne Yapabilir?
- Doğal Dil Arayüzü: Sadece "Bu tanışma uygulaması giriş sisteminde kimlik avı simülasyonu yapın" yazın - Penligent doğru araçlarla yürütür.
- Gerçekçi Kimlik Avı Simülasyonu: Yem mesajlarından kimlik bilgilerinin ele geçirilmesine kadar flört uygulaması kullanıcılarını hedef alan kimlik avı zincirlerini yeniden oluşturabilir.
- Otomatik Doğrulama ve Önceliklendirme: Gerçek riskleri yanlış pozitiflerden ayırır.
- Anında Raporlama ve Ekip İşbirliği: Gerçek zamanlı analist işbirliği ile PDF/HTML rapor oluşturma.
Arkadaşlık Uygulamaları Kullanıcıları için Kişisel Güvenlik İpuçları
Arkadaşlık uygulamalarında kişisel güvenliğin korunması söz konusu olduğunda, proaktif önlemler önemli bir fark yaratır. Kullanıcılar özel bir e-posta adresiyle kaydolmalı ve kimlik bilgilerinin yeniden kullanılmasını önlemek için güçlü, benzersiz bir şifre kullanmalıdır. Kesin konum paylaşımının devre dışı bırakılması, takip edilme tehdidini önemli ölçüde azaltabilirken, sosyal hesap girişlerinin kullanılmasından kaçınılması, bir ihlal durumunda platformlar arası maruz kalma olasılığını en aza indirir. Son olarak, işyeri veya okul bilgilerinin herkese açık profillerden çıkarılması, hedefli taciz veya kimlik takibinin önlenmesine yardımcı olabilir.