Scripting Nedir ve Siber Güvenlikte Neden Önemlidir?
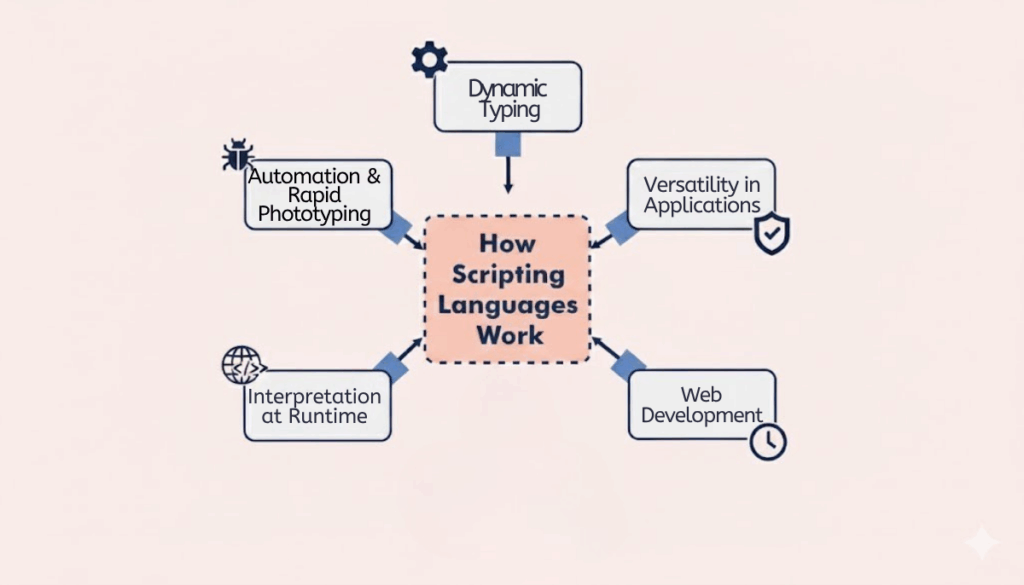
Günümüzün siber güvenlik ortamında tehditlerin sürekli evrim geçirmesi, savunucuların giderek daha dar zaman dilimleri içinde tepki vermesi gerektiği anlamına geliyor. Saldırılar, özellikle kritik sistemleri hedef alan sıfır gün istismarlarından, haftalar hatta aylara yayılan titizlikle planlanmış, çok aşamalı izinsiz giriş kampanyalarına kadar değişebilir ve güvenlik ekiplerine tespit edildikten sonra yanıt vermek için yalnızca dakikalar veya saniyeler bırakabilir. Bu baskı ortamında, Komut Dosyası Yazma artık çevresel bir teknik beceri değil, tüm disiplinlerde güvenlik alanında çalışan profesyoneller için temel bir yetkinlik olarak ortaya çıkmıştır.
Komut dosyası oluşturma, adım adım insan müdahalesine dayanmak yerine bilgisayarların önceden tanımlanmış görevleri otomatik olarak tamamlamasını sağlayan yürütülebilir talimat setleri yazmak için komut dosyası oluşturma dillerini kullanma uygulamasını ifade eder. Komut dosyası yazmanın değeri çok yönlüdür: tekrarlayan süreçleri yürütmek için gereken süreyi önemli ölçüde azaltır, potansiyel olarak maliyetli insan hatalarını en aza indirir ve yetenekli analistlerin zamanlarını stratejik risk değerlendirmeleri, karmaşık adli tıp ve işbirliğine dayalı olay müdahale çabaları gibi daha yüksek değerli faaliyetlere ayırmalarını sağlar. Sızma testi, izinsiz giriş tespiti, tehdit avcılığı ve hızlı olay müdahalesinde komut dosyası oluşturma, savunma ve saldırı operasyonlarının neredeyse her aşamasına dahil olmuştur.

Yaygın Betik Dilleri
Farklı komut dosyası dilleri farklı güçlü yönlere sahiptir ve bu da onları farklı güvenlik hedefleri için uygun hale getirir. Bazıları hızlı keşifte üstünlük sağlarken, diğerleri büyük veri kümelerini işlemede eşsizdir; bazı diller ise belirli güvenlik çerçevelerine derinlemesine entegre edilerek sektörün vazgeçilmezleri haline gelir. Aşağıdaki tabloda siber güvenlikte en yaygın kullanılan altı betik dili listelenmekte, temel özellikleri, uygulanabilirlik yelpazeleri ve gerçek dünyayla ilgilerini gösteren çalıştırılabilir kod örnekleri özetlenmektedir.
| Dil | Özellikler | Güvenlikte Örnek Kullanım |
|---|---|---|
| Python | Güçlü yeteneklere sahip basit, okunabilir sözdizimi; Scapy, Requests ve Volatility gibi kapsamlı güvenlik kütüphaneleri ve araçları ekosistemi; güvenlik açığı taraması, günlük analizi ve ağ trafiği izleme için ideal | Otomatik Günlük Ayrıştırma ve Uyarı "`pythonimport redef parse_logs(file_path):with open(file_path, 'r') as file:for line in file:if re.search(r"(Failed login |
| Bash | Unix benzeri sistemlerde komutları hızlı bir şekilde birbirine zincirlemek için son derece verimli; keşif, sistem bakımı ve ilk sızma testi keşfi için mükemmel | Ağ Taramasıbash<br>#!/bin/bash<br>if ! command -v nmap &> /dev/null; then<br> echo "Hata: Nmap yüklü değil."<br> Çıkış 1<br>fi<br>nmap -sP 192.168.1.0/24 |
| PowerShell | Windows ortamlarıyla derin entegrasyon için tasarlanmıştır; yama yönetimi, yapılandırma denetimi ve otomatik olay müdahale iş akışlarında mükemmeldir | Eksik Yama Tespiti "`powershellImport-Module PSWindowsUpdateGet-WindowsUpdate |
| JavaScript | İstemci tarafı güvenlik testlerinin ve kötü amaçlı kod analizinin merkezinde yer alır; Siteler Arası Komut Dosyası Oluşturma (XSS) gibi güvenlik açıklarını simüle etmek ve tespit etmek için yaygın olarak kullanılır | Web Sayfalarında XSS Testi (kontrollü ortamlar için)javascript<br>let payload = "<script>alert('XSS');<\\/script>";<br>document.querySelectorAll('input').forEach(input => {<br> input.value = payload;<br>});<br>alert("Payload injected for testing"); |
| Yakut | Son derece esnek ve bakımı kolay; Metasploit gibi çerçevelere yakından bağlı, bu da onu istismar modülleri yazmak veya özelleştirmek için ideal hale getiriyor | Metasploit'te Güvenlik Açığı TaramasıYAKUT<br># Metasploit konsolunun içinde çalıştırın<br>use auxiliary/scanner/http/title<br>set RHOSTS 192.168.1.0/24<br>koşmak |
| Perl | Metin ayrıştırma ve toplu veri analizi için olağanüstü; büyük hacimli günlükleri veya tarama sonuçlarını işlerken verimli | Anahtar Kelime Uyarıları için Günlükleri Aramaperl<br>#!/usr/bin/perl<br>katı kullanın;<br>kullanım uyarıları;<br>open(my $log, "<", "system.log") or die $!;<br>while(<$log>){<br> if(/Başarısız giriş/){<br> print "ALERT: $_";<br> }<br>}<br>close($log); |
Sunucu tarafı komut dosyaları genellikle arka uç sistemlerde çalıştırılır, kullanıcı görünümünden gizlenir, bu da onları daha güvenli ve hassas verileri işlemek veya güvenlik açığı doğrulaması yapmak için daha uygun hale getirir. Bunun aksine, istemci tarafı komut dosyaları kullanıcının tarayıcısında veya yerel ortamında çalışır ve daha hızlı yanıt süreleri sunar, ancak görünürlükleri ve değiştirilme kolaylıkları nedeniyle, güçlü girdi doğrulama ve gizleme mekanizmalarıyla eşleştirilmedikleri sürece doğal olarak daha az güvenlidirler.
Komut Dosyasının Avantajları ve Sınırlamaları
Derlenmiş dillerle karşılaştırıldığında, betik dillerinin açıklığı ve uyarlanabilirliği, güvenlik ekiplerinin yeni araçlara hızla uyum sağlamasına, ortaya çıkan güvenlik açıklarına yanıt vermesine ve uzun derleme süreçleri olmadan yeni geliştirilen metodolojileri entegre etmesine olanak tanır. Bu çeviklik, aktif tehditleri azaltırken veya yeni tespit stratejileri uygularken paha biçilmezdir. Ek olarak, betik dilleri genellikle çapraz platformludur, yaygın olarak belgelenmiştir ve acemi dostudur, bu da hem deneyimli sızma testi uzmanları hem de alana yeni başlayanlar tarafından hızlı bir şekilde benimsenmesini sağlar.
Öte yandan, komut dosyaları genellikle çalışma zamanında yorumlandığından, derlenmiş ikili dosyalara göre daha yavaş çalışırlar ve derlenmiş kodda mümkün olan sağlam optimizasyondan yoksundurlar. Bu durum, büyük veri kümelerinin milisaniyeler içinde işlenmesi gibi yüksek performansın kritik önem taşıdığı senaryolarda zorluklara yol açabilir ve genellikle komut dosyası ile derlenmiş bileşenleri harmanlayan hibrit yaklaşımlar gerektirir.
Siber Güvenlikte Temsili Komut Dosyası Uygulamaları
Komut dosyası oluşturma tüm güvenlik iş akışına nüfuz eder. Keşif aşamasında, komut dosyaları bir ağdaki ana bilgisayarları hızlı bir şekilde numaralandırabilir, açık bağlantı noktalarını belirleyebilir ve çalışan hizmetleri tespit edebilir. Güvenlik açığı doğrulama aşamalarında, otomatik sızma testleri yürütebilir, sonuçları CVE veritabanlarıve iyileştirme çabalarını önceliklendirir. Olay işleme sırasında, komut dosyaları güvenliği ihlal edilmiş ana bilgisayarları izole edebilir, analiz için adli verileri çekebilir ve hatta belirli algılama modelleri tarafından tetiklenen önceden tanımlanmış sınırlama eylemlerini başlatabilir. Güvenlik ekipleri, komut dosyasını her operasyonel aşamaya dahil ederek daha hızlı, daha tutarlı ve daha tekrarlanabilir sonuçlar elde eder.
Bash Komut Dosyaları: Güvenlik Görevleri için Hızlı Yürütme
Bash komut dosyaları özellikle ağ düzeyinde toplu işlemlere uygundur. Yerel sistem komutlarını harici araçlarla bir araya getirme yetenekleri, toplu ana bilgisayar keşif taramaları yapmak gibi tekrarlayan yönetim görevlerini verimli bir şekilde yerine getirebilecekleri anlamına gelir, liman maruziyetini denetleme dağıtılmış ortamlarda dosya bütünlüğünü doğrulama ve olası kötüye kullanım için kullanıcı etkinliğini izleme. Bu özellik, devam eden operasyonel güvenlik ile planlı saldırı testlerini dengelemek zorunda olan ekipler için özellikle değerlidir.
Python Komut Dosyası: Orta ve İleri Düzey Beceriler
Python'un çok yönlülüğü - geniş kütüphane ortamıyla birleştiğinde - onu incelikli güvenlik iş akışlarını idare etmek için bir güç merkezi haline getirir. BeautifulSoup ve Requests ile entegrasyonlar, büyük web sitelerinde otomatik tarama ve güvenlik açığı taraması sağlar; Scapy hassas paket yakalama ve protokol analizi sağlar; Volatility ve YARA hem statik hem de dinamik kötü amaçlı yazılım analizini otomatikleştirebilir; Selenium karmaşık web uygulamalarında fuzz testini kolaylaştırır. Bu özellikler, güvenlik uzmanlarının yalnızca tehditleri tespit etmelerine değil, aynı zamanda taktiklerini gelişen düşman tekniklerine göre uyarlamalarına da olanak tanır.
Saldırganlar İzinsiz Giriş İçin Komut Dosyalarından Nasıl Yararlanıyor?
Saldırganlar, izinsiz giriş çabalarını ölçeklendirmek ve otomatikleştirmek için komut dosyalarından yararlanma konusunda da aynı derecede ustadır. Kötü niyetli PowerShell komut dosyaları, uç nokta savunmalarını atlamak ve yükleri doğrudan bellekte çalıştırmak için sıklıkla kullanılır; PDF'lere gömülü JavaScript veya web sayfaları tetikleyebilir siteler arası saldırılar ve gizli indirmeler; ve HTA dosyaları gibi modası geçmiş mekanizmalar hala oltalama kampanyaları saldırgana komut dosyası düzeyinde kontrol sağlayarak. Savunmacılar bu saldırı yeteneklerini anlayarak bunları daha iyi tahmin edebilir, tespit edebilir ve etkisiz hale getirebilir.
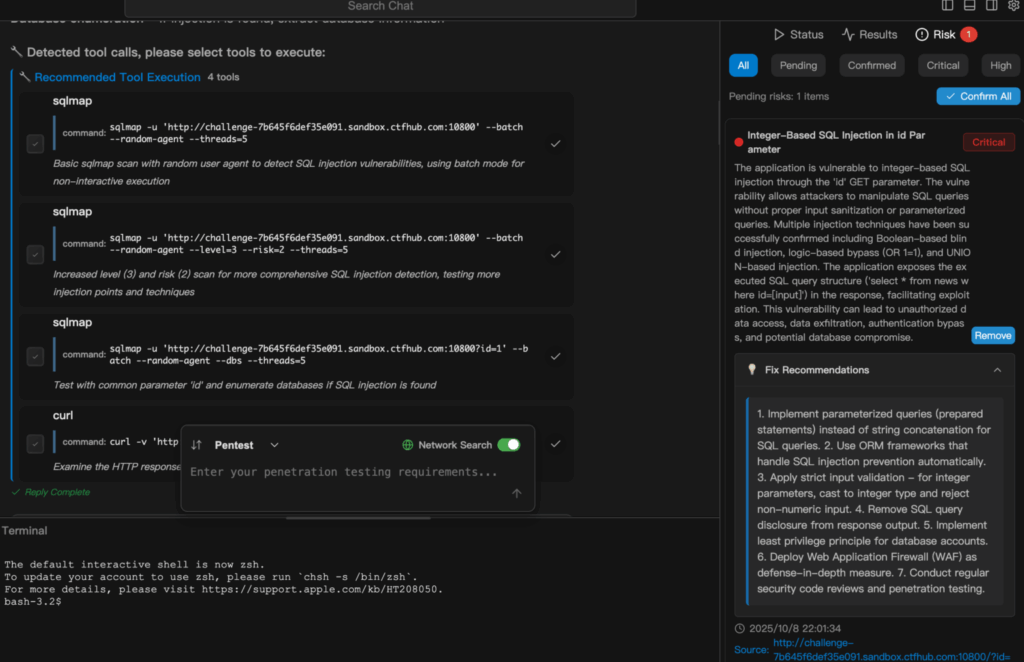
Yapay Zeka Destekli Komut Dosyası Yazma: Penligent'ın Akıllı Sızma Testine Yaklaşımı
Geleneksel sızma testi iş akışında, güvenlik uzmanları veya etik bilgisayar korsanları komut dosyalarının nasıl yazılacağını ve çalıştırılacağını bilmeli, Nmap, Burp Suite gibi araçları manuel olarak çalıştırmalıdır, SQLmapve Metasploit'i çalıştırabilir ve ardından nihai bir rapor oluşturmadan önce gürültü ve yanlış pozitifleri ortadan kaldırmak için kapsamlı çıktıları eleyebilirsiniz. Bu süreç yalnızca yüksek düzeyde komut dosyası uzmanlığı gerektirmekle kalmaz, aynı zamanda günlerce değerli zamanınızı da tüketebilir.
Penligent bu paradigmayı tamamen değiştirerek komut dosyalarını kendiniz yazma zorunluluğunu ortadan kaldırır. Python veya Bash kodu hazırlamak yerine, amacınızı basit, doğal bir dille ifade edersiniz, "Bu web sitesini SQL enjeksiyon açıkları için kontrol edin" veya "Şirket ağında kapsamlı bir port taraması yapın". Penligent AI Agent talebinizi yorumlar, 200'den fazla entegre güvenlik aracından oluşan bir kütüphaneden en uygun araçları otomatik olarak seçer, gerekli taramaları gerçekleştirir, gerçek olduklarından emin olmak için güvenlik açıklarını doğrular, risk ciddiyetine göre öncelik puanları atar ve hemen harekete geçmeye hazır net, profesyonel bir rapor oluşturur.