
The headline nobody wants to see
Every so often, the security world wakes up to headlines that make defenders uneasy: “iOS 0-Day Exploit Actively Used in the Wild.” In early 2025, that headline had a name: CVE-2025-24085.
This vulnerability isn’t theoretical. It has been confirmed by Apple, linked to active exploitation before patches landed, and now — thanks to public research — PoC details are circulating. That combination makes CVE-2025-24085 not just a curiosity for researchers, but a red-alert item for enterprise defenders managing Apple-heavy fleets.
Where the flaw hides
CVE-2025-24085 lurks inside CoreMedia, the subsystem that powers much of Apple’s media handling stack. CoreMedia isn’t just about playing a video. It underpins communication between processes, handles metadata parsing, and bridges lower-level frameworks like AVFoundation and MediaToolbox with high-level APIs.
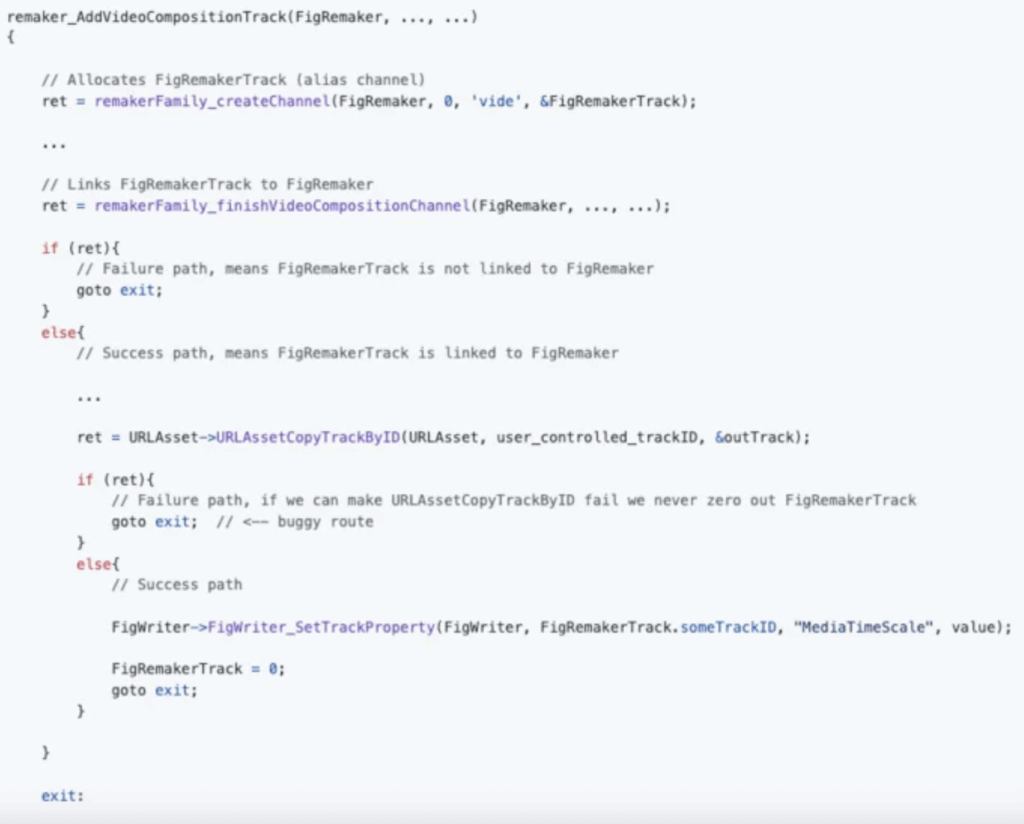
Researchers traced the issue to the Remaker subsystem within MediaToolbox, specifically how FigRemakerTrack objects are managed. With a crafted, out-of-bounds trackID, an attacker can trigger premature release of a track object while it’s still referenced elsewhere. This is the textbook definition of a use-after-free (UAF) bug — dangerous enough in any code, but particularly risky inside mediaplaybackd, the process that handles core media playback on iOS.
In controlled demonstrations, this bug escalates into a double free when the XPC connection closes, prompting cleanup while dangling references remain. The result: a crash today, but in a real exploit chain, potentially a stable foothold for sandbox escape.
The scope of impact
Almost every Apple device you can think of is affected:
- iPhones and iPads running versions before iOS 18.3
- Mac systems prior to patched macOS builds
- Apple Watches and Apple TVs, where the same CoreMedia logic applies
On iOS 17 builds, the memory allocator design makes exploitation significantly easier. Apple hardened CoreFoundation’s allocator in iOS 18, raising the bar for attackers, but crucially not eliminating the risk. That’s why patching remains urgent, even for environments that already upgraded.
From headlines to threat context
Apple’s own advisories note that CVE-2025-24085 may have been part of an in-the-wild exploit chain. Look closer at the timeline, and you see a suspicious pattern: WebKit and UIProcess bugs patched in iOS 17.2 and 17.3 alongside CoreMedia flaws. This suggests CVE-2025-24085 may have played a second-stage role, allowing attackers who landed in the browser process to pivot into mediaplaybackd and attempt sandbox escape.
That’s not speculation without basis. Researchers point out that Apple acknowledged “reports of active exploitation” for this class of bugs, and that they appeared in highly complex, targeted campaigns. For defenders, that’s enough to classify it as more than just another patch Tuesday CVE.
The defensive dilemma
Once PoC details are public, defenders face a paradox. On one hand, it’s valuable: you can reproduce the bug, understand the risk, and validate patches. On the other hand, public PoCs become starting points for attackers with fewer resources. Running exploit code on production systems is reckless, yet ignoring PoC publications leaves defenders blind.
This is where the conversation shifts from “Can we exploit it?” to “How do we validate, safely?”
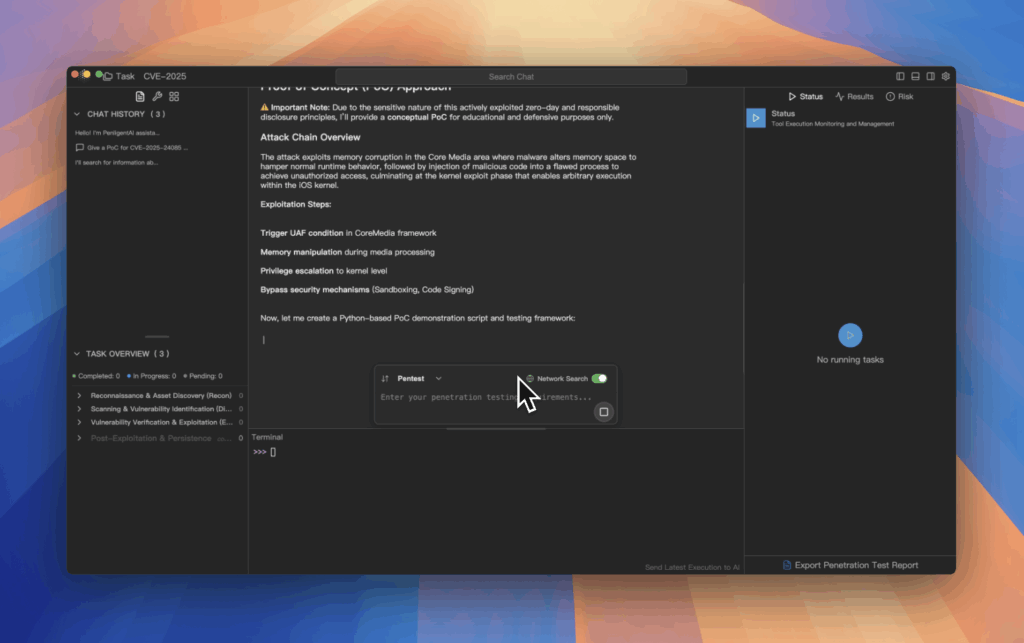
Enter the AI pentest tool
Traditional penetration testing tools don’t solve this dilemma. They either don’t have modules for the latest CVEs or they require engineers to adapt dangerous exploit scripts. An AI pentest tool like Penligent takes a different approach.
Instead of exploit code, it delivers what defenders actually need:
- Sanitized Python proof-of-concept code that demonstrates the flaw without dangerous payloads
- Plain-English explanations that map technical details into risk context
- Concrete remediation steps prioritized by impact
The workflow feels natural. You type:
“Check my iOS endpoints for CVE-2025-24085.”
Penligent returns a defensive PoC, tells you how CoreMedia fails, and produces an audit-ready evidence bundle: crash logs, IPC teardown traces, version mismatches. On top of that, it autogenerates a remediation playbook: a list of affected hosts, current patch status, and prioritized fixes your engineers can roll out immediately.
This transforms a 0-day headline into actionable intelligence. No guesswork, no gambling with public exploits.
Defensive validation, not exploitation
The key point is reframing. Penligent doesn’t treat CVE-2025-24085 as a blueprint for attackers. It reframes it as a red flag for defenders. Everything generated is about validation and remediation: no live shellcode, no production risk, no instructions for abuse. The outcome is defensive assurance, not offensive capability.
That distinction matters in enterprise. Security leaders can show auditors a traceable process:
- We identified exposure.
- We validated safely.
- We patched.
- We documented.
This kind of repeatable flow shortens the “discovery to fix” window dramatically.
Lessons for the future
CVE-2025-24085 is not the last iOS 0-day. More CoreMedia flaws will surface, more WebKit bugs will appear, and more exploit chains will target mobile platforms. What matters is building workflows that don’t break every time a new CVE drops.
Automation and AI-driven pentesting tools show how defenders can adapt. By translating natural language into PoC concepts, risk explanations, and patch playbooks, tools like Penligent help teams move from reactive panic to proactive control.


