GHunt is an open-source OSINT tool designed to investigate and analyze Google accounts using publicly available data. Originally released by security researcher mxrch, GHunt has become a staple in OSINT investigations, penetration testing, and threat intelligence.
Unlike exploit frameworks, GHunt doesn’t hack into accounts. Instead, it leverages open Google services to gather digital footprints. With only a Gmail address, GHunt can reveal valuable intelligence.
What GHunt Can Do
- Gmail & Google ID Profiling: Collect metadata about the account, creation date, and linked services.
- Google Maps Reviews: Extract user-generated reviews and location check-ins.
- Google Photos & Albums: Detect publicly shared albums.
- Google Drive & Docs: Identify files that are accidentally shared with public access.
- YouTube & Calendar: Gather traces of video activity and shared calendars.
For penetration testers, this translates into actionable reconnaissance during the early stages of an engagement. For OSINT researchers, it’s a way to map an individual’s online exposure.
Security and Legal Considerations
GHunt is strictly an OSINT tool. It relies only on publicly available information and should never be used without proper authorization. Running GHunt against accounts you don’t own or don’t have permission to investigate may breach privacy laws.
Defenders, however, can use GHunt to audit their own Google accounts, making sure no information is exposed unintentionally.

Where GHunt Fits in Cybersecurity
- Red Team Reconnaissance: Collecting background before an engagement.
- Threat Intelligence: Tracking exposure of public data linked to specific email addresses.
- Digital Forensics: Correlating online behavior with compromised accounts.
Still, GHunt has its limitations: it’s specialized in Google services, requires technical knowledge, and doesn’t cover broader vulnerability validation.
From GHunt to Automated Pentesting with AI
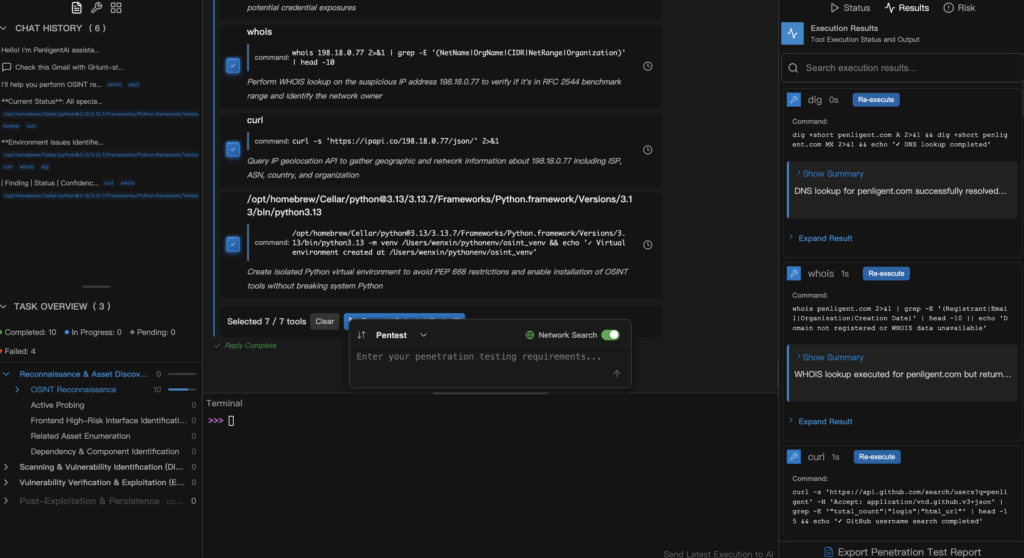
This is where AI pentest tools like Penligent enter the picture. GHunt demonstrates the power of targeted OSINT, but defenders and testers often need more: CVE detection, vulnerability validation, and full remediation workflows.
With Penligent, you don’t write scripts. You simply type a natural language prompt. For example:
- “Check this Gmail account with GHunt-like OSINT methods.”
- “Scan my iOS devices for CVE-2025-24085 and generate a remediation plan.”
- “Validate vulnerabilities in my web app and provide an audit-ready report.”
Penligent converts your request into safe Python code, runs checks across hundreds of integrated tools, and produces evidence bundles plus prioritized fixes.
Conclusion
GHunt shows how powerful OSINT can be when applied to a single ecosystem like Google. But to move from reconnaissance to full-scale pentesting, you need automation and scale. Penligent extends the logic of “one input, many insights” into an AI-powered pentest workflow: from natural language to CVE checks, from vulnerability validation to remediation reporting.


