Why “java pdf exploit” keeps trending
“Java PDF exploit” is a catch-all search term people use when they’re worried about malicious PDFs that trigger vulnerabilities in PDF readers or abuse Java/JavaScript features in the document pipeline. PDFs can carry risk through multiple angles: embedded JavaScript, parser bugs in readers, or insecure PDF generators that ingest attacker-controlled input. Researchers have documented these issues for years—from JavaScript-based PDF attacks and exploit-kit delivery to recent rendering and generator abuses. Intigriti+4SentinelOne
In short: even though PDF wasn’t designed to run arbitrary code, implementation flaws in common readers and ecosystems have made it a reliable lure in real intrusions. Historic notes and threat write-ups from vendors and labs confirm this pattern.
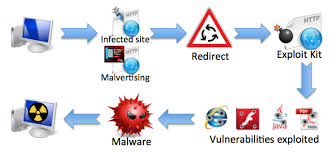
What attackers try vs. what defenders need
Attackers love PDFs because a single attachment can combine social engineering with client-side parsing bugs. They hide payloads with obfuscation/encoding, leverage JavaScript actions, or exploit parser discrepancies across apps and browsers. Defenders, however, don’t need exploit code; they need safe validation:
- recognize signals (unexpected Java process spawns, suspicious file-system access, odd network callbacks);
- reproduce behavior in a controlled way;
- ship prioritized fixes fast. (See recent and classic analyses on malicious PDFs and detection.) SentinelOne+1
A defensive demo: natural-language validation on Penligent
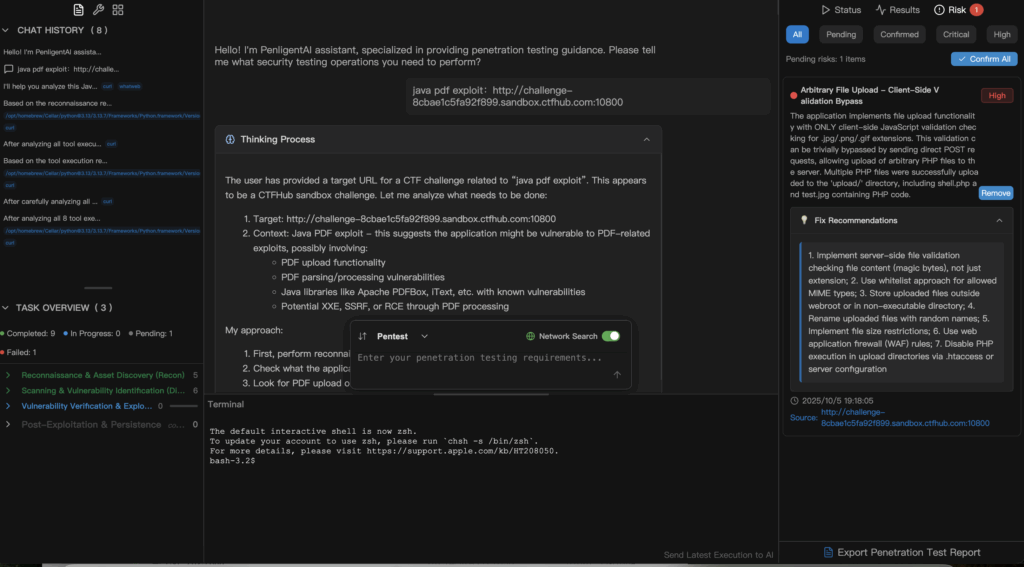
Here’s how teams can demonstrate the risk safely—with no command line and no scripting:
Step 1 — Prompt, in plain English
“Check my lab endpoint for java pdf exploit patterns. Use safe diagnostics only. Flag abnormal Java process activity, suspicious PDF actions, and any network callbacks.”
Step 2 — Penligent turns the prompt into a sanitized test
Penligent orchestrates controlled probes against a lab image, simulating PDF handling paths without running real exploit code. It watches for the same indicators researchers highlight (JS actions, parser anomalies, generator quirks) and correlates signals in real time. 2PortSwigger+2
Step 3 — Actionable outcome
You get clear, prioritized remediation guidance:
- patch and version targets (reader/OS hardening);
- disable risky PDF JavaScript where feasible;
- tighten ingress controls on PDF generators;
- add detections for process/file/network behaviors commonly seen in malicious PDFs. (Vendor and lab write-ups consistently recommend patching readers and disabling risky features.) Microsoft
This way, you transform a scary headline into repeatable validation—no risky live payloads, just defensible signals and fast fixes.
Practical hardening checklist
- Patch readers & OS (track CVEs for Acrobat/Reader and your PDF libraries). CVE
- Disable PDF JavaScript if business allows; audit “open/launch” actions. CISA
- Harden PDF generators (sanitize user-controlled inputs; test for SSRF/templating abuse). Intigriti
- Detect anomalies (Java processes spawned by readers, unexpected network egress, odd file writes). Medium+1
- Educate users (untrusted PDFs remain a top phishing vector; disable auto-open). Recent reporting shows PDF-based campaigns are still evolving. Thoughtworks
Try it yourself (natural-language prompts for Penligent)
- “Run a safe java pdf exploit validation on my test VM. No real payloads; collect process/file/network signals and propose fixes.”
- “Audit our PDF generator endpoints for injection/SSRF risks and produce a mitigation plan.” Intigriti
- “Check if Adobe Reader settings and versions across endpoints reduce exposure to known PDF JS issues.” CISA


