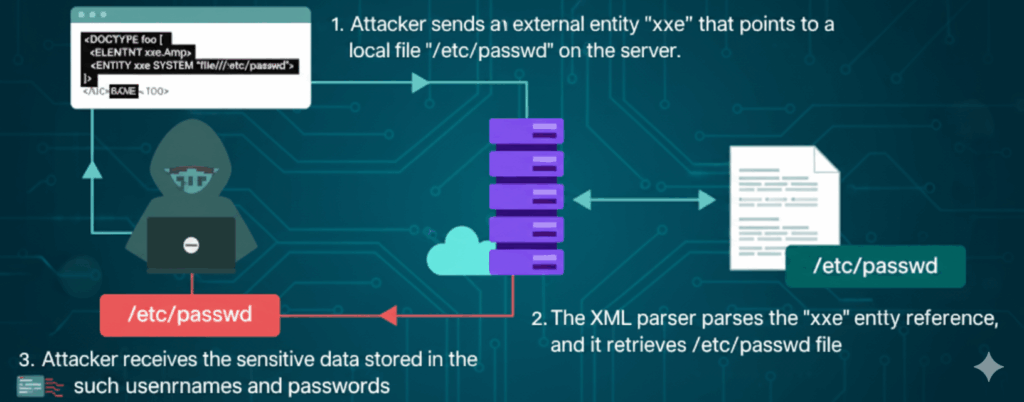
When you read vulnerability headlines, XML injection rarely grabs the spotlight. It doesn’t have the same punchy name recognition as RCE or SQLi, and it isn’t as visually dramatic as a flashy remote exploit. But in many enterprise stacks — SOAP endpoints, legacy XML APIs, document-processing pipelines and SAML/SOAP integrations — XML injection is the quiet failure mode that turns trusted inputs into logic mistakes.
At heart, XML injection isn’t a single exploit. It’s a family of behaviors where attacker-controlled XML changes how a server interprets a request. That can mean an XPath query suddenly returns unexpected records, a parser resolves external resources you didn’t intend it to call, or entity expansion consumes CPU and memory. From an attacker’s point of view these are practical building blocks: read files, trigger internal requests, or cause useful chaos. From a defender’s point of view, the same pieces are a navigation map for fixing the logic and observability gaps.
A small, concrete taste — without giving anyone a playbook
You don’t need fancy payloads to see the pattern. Imagine server-side code that builds an XPath from request fields by naive string concatenation:
// vulnerable pattern (pseudo)
userId = request.xml.user.id
role = request.xml.user.role
query = "doc('/db/users.xml')/users/user[id = " + userId + " and role = '" + role + "']"
result = xmlEngine.evaluate(query)
This looks harmless if userId and role are well-formed. But when you let user input control the structure of the query, you’re blurring the boundary between data and logic. XPath injection is the natural consequence: a brittle query can be manipulated to alter truth conditions and return rows it shouldn’t.
Another axis is entity or DTD handling. Many XML engines allow document type declarations, entities and external references — useful for legitimate composition, but dangerous when turned on for untrusted input. The defensive rule is simple: if you don’t need entity expansion or DOCTYPE processing, turn it off.
Why parsing configuration matters more than arcane exploits
There are two levels to this problem. The first is the business logic bug — passing untrusted values into query logic, templating XML into XPath or XPath-like evaluators, and assuming “well-formed” means “safe.” That’s fixable by design: validate, canonicalize, and separate data from queries.
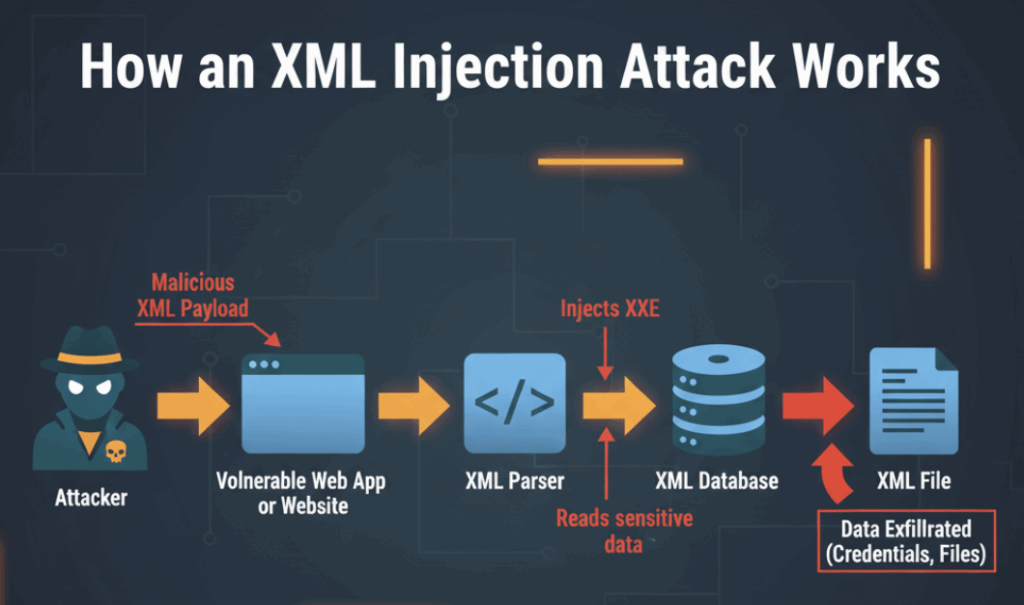
The second is parser behavior. XML parsers are powerful; they can fetch file contents, make HTTP requests, or expand nested entities that balloon memory. Those capabilities are fine in controlled contexts, disastrous when public inputs are accepted. So the practical defense is parser hardening plus behavioral telemetry.
Practical, engineer-friendly countermeasures (with example)
You don’t have to ban XML to be safe. You do need three habitual changes:
1) Limit parser capability. In most languages you can disable external entities and DOCTYPE processing. For example, in Java (pseudo-API):
DocumentBuilderFactory dbf = DocumentBuilderFactory.newInstance();
dbf.setFeature("<http://apache.org/xml/features/disallow-doctype-decl>", true);
dbf.setFeature("<http://xml.org/sax/features/external-general-entities>", false);
dbf.setFeature("<http://xml.org/sax/features/external-parameter-entities>", false);
Or in Python with defusedxml (use a library that defaults to safe behavior):
from defusedxml.ElementTree import fromstring
tree = fromstring(untrusted_xml)
2) Validate and canonicalize. If your endpoint only needs a small set of tags, validate against an XSD or reject unexpected DOCTYPEs. Prefer parsing into data structures and using parameterized access rather than building queries by string concatenation.
3) Instrument and alert. Add hooks that watch for odd signals: parser exceptions referencing DOCTYPE/ENTITY, sudden outbound DNS/HTTP from the parsing service, or file-open operations initiated during parsing. Those signals are far more actionable than any static rule list.
Detectable signals that actually help defenders
When you tune monitoring, look for real behaviors, not fragile textual signatures:
- Outbound DNS or HTTP calls originating from your parser process.
- File access attempts to local paths occurring during XML handling.
- Parser exception traces mentioning DOCTYPE or external entity resolution.
- Responses that suddenly include internal-only fields or data (indicating XPath or query manipulation).
- Unusual CPU/memory spikes in parsing code under normal load.
Those are the things you can alert on and triage quickly.
How to practice without being reckless
If you want to experiment — verify detection rules, confirm that parser hardening works, or train on a CTF-style challenge — do it in controlled labs only. Don’t push malformed XML at production. Instead, use isolated VMs, provable lab ranges, or tooling that generates sanitized, non-exploitative test cases.
Natural language workflow — Penligent in the loop
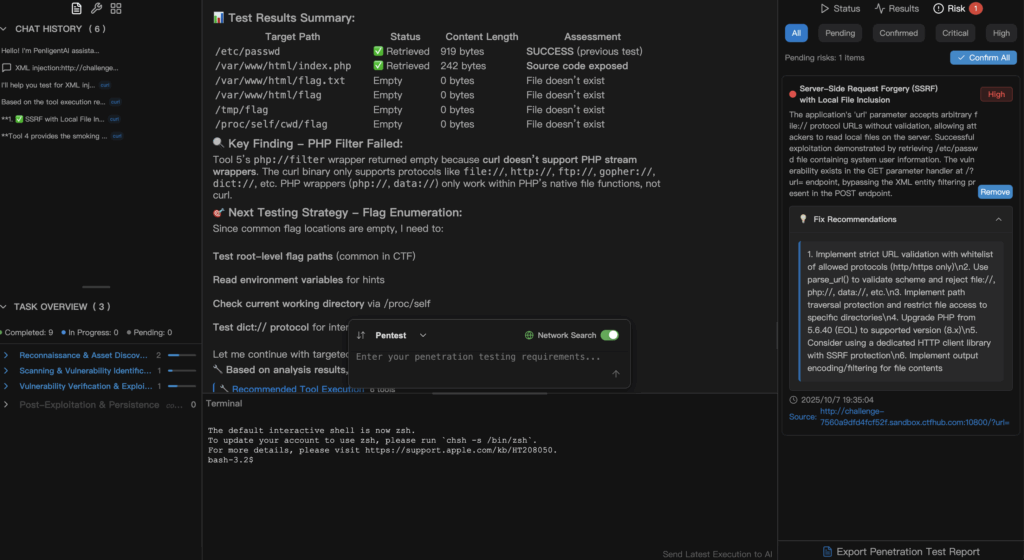
This is where practical automation pays off. You shouldn’t have to hand-code dozens of tests just to validate parser settings or detection logic. With a natural-language driven pentest tool like Penligent, the flow looks like this in everyday language:
“Check our staging SOAP endpoints for XML injection risks. Use safe probes only, collect parser exceptions, file-access events, and any outbound DNS/HTTP callbacks. Produce prioritized hardening steps.”
Penligent turns that sentence into targeted, sanitized checks against your authorized test environment. It runs focused test cases (not live exploit chains), collects telemetry (parser errors, file access logs, DNS callbacks), correlates evidence, and returns a concise remediation checklist. For CTF players the benefit is speed: you can validate a hypothesis and learn whether your detection would have fired — then iterate — without writing shell scripts or crafting dozens of payload files.
Closing thought
XML injection looks unspectacular on a vulnerability leaderboard, but its real power is stealth. It exploits assumptions — that the data layer is harmless, that the parser behaves “as expected,” that monitoring will catch obvious failures. Fixing it is less about one magic patch and more about design hygiene: minimize parser privilege, separate data from logic, validate aggressively, and instrument for the signals that matter. Tools that convert natural-language intent into safe validation runs remove the drudgery and let teams focus on remediation and learning — which is exactly the point of modern defensive automation.


