Directory attacks have become a persistent and evolving threat in today’s interconnected digital landscape. By exploiting weaknesses in how web applications handle file paths and directory access, malicious actors can bypass traditional defenses and expose sensitive data. Understanding what a directory attack is, how it works, and how it can be stopped is essential for both security professionals and organizations determined to safeguard their infrastructure. The sections below break down this threat from its core mechanics to practical prevention strategies, providing a comprehensive view of the risks and the countermeasures available.

What is Directory Attack?
Within the realm of cybersecurity, a directory attack describes a category of techniques in which an attacker intentionally manipulates the path of a file request or engages in systematic probing of hidden folders, all in an effort to gain unauthorized access to vital resources residing on a server. These attacks often take the form of a directory traversal, where malicious input such as ../ is used to climb upwards through the file structure beyond the intended scope of a web application, or a directory enumeration, where different directory names are methodically guessed and tested to reveal concealed administrative panels, backup archives, or configuration files. In some scenarios, attackers may directly exploit unsecured directory endpoints, bypassing any authentication measures and extracting sensitive data with little resistance.
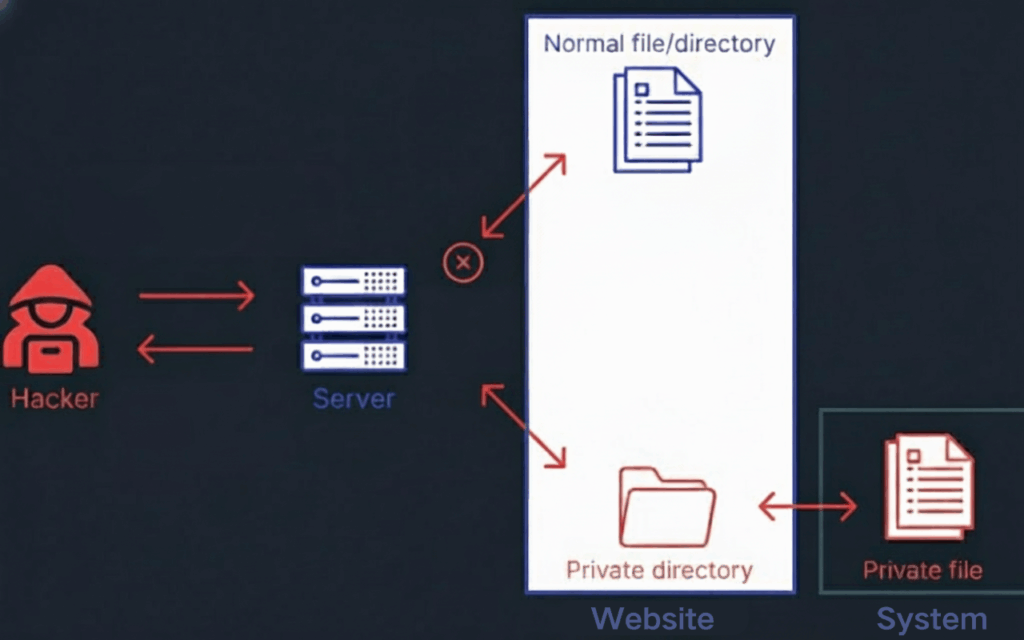
An Example of Directory Attack
Consider a web application that serves user profile images through a standard request format such as:
<https://example.com/profile.php?img=avatar.png>
If the application fails to properly cleanse the incoming request parameter, a malicious actor might submit an altered URL that looks like:
<https://example.com/profile.php?img=../../../../etc/passwd>
In a vulnerable environment, the server could interpret this adjusted path not as an image file but instead as a call to the system’s /etc/passwd file. This classic example of path traversal not only reveals usernames but also provides valuable information about the system’s configuration, which in turn could be leveraged for deeper, more damaging exploitation.
Directory Attack Risks and Their Impact on Systems
The seriousness of directory attacks lies not merely in the ability to read an unintended file; rather, it is in the chain of consequences that can follow such unauthorized access. If an attacker is able to obtain credentials, API tokens, or database connection strings from exposed files, these assets can rapidly become stepping stones towards compromising the entire system. Once proprietary source code is retrieved, an organization’s competitive edge and intellectual property may be exposed, leaving it vulnerable to replication or exploitation. Beyond technical damages, gaining access to certain types of files may trigger violations of data protection regulations such as GDPR, HIPAA, or CCPA, leading to potential legal consequences and reputational harm. Furthermore, in a significant number of red-team operations, directory attacks serve as an initial reconnaissance step that paves the way for privilege escalation, lateral movement through the network, or chaining into more sophisticated, multi-stage attacks.
What Tools Do Security Testers Use for Directory Attacks?
| Tool | Primary Use | Key Features |
|---|---|---|
| Penligent | AI-powered pentesting & directory attack defense | An integration station supporting over 200+ security tools, featuring natural language operation, automatic vulnerability verification and one-click report generation. |
| Gobuster | Dir & file brute-forcing | Fast CLI tool; custom wordlists; DNS subdomain scanning. |
| DirBuster | HTTP dir enumeration | GUI, recursive scans, multi-threading. |
| FFUF | High-speed fuzzing | Regex filtering; recursion; content matching. |
| Burp Suite | Manual+automated testing | Crawling; parameter fuzzing; reporting. |
| WFuzz | HTTP fuzzing | Payload injection across parameters. |
Penligent integrates the above tools, enabling seamless use of Gobuster, DirBuster, FFUF, Burp Suite, and WFuzz within its AI-powered security framework.
How to Prevent a Directory Attack?
Preventing directory attacks requires more than plugging holes; it involves designing systems that inherently resist such exploitation. Web applications should process user input through strict validation routines that reject any path segments or encoded characters suggestive of traversal attempts. Access to files should operate on a whitelist principle, meaning only predefined and verified directories may be reached by public requests. Servers should normalize every request path to an absolute form and ensure it remains confined to secure zones, while operating under the principle of least privilege so that even if a flaw is exploited, the attacker’s reach is severely limited. Finally, error messages and debugging information must be crafted carefully to avoid inadvertent disclosure of directory structures, and regular penetration testing should be scheduled to uncover new weaknesses before adversaries do.