OAST meaning are increasingly referenced in modern cybersecurity conversations as organizations adapt to vulnerabilities that evade traditional detection. In this article, we focus on OAST meaning as a core concept in modern application security—Out-of-Band Application Security Testing—and explain its relevance, how it works, common tools, threat use cases, defensive practices, and example attack and mitigation code that you can directly run or adapt. This level of detail is tailored for hardcore AI and security engineers building or defending complex systems.
What Is OAST Meaning in Security?
OAST (Out-of-Band Application Security Testing) is a testing methodology that identifies vulnerabilities by observing interactions that occur outside the normal request/response cycle of an application. Traditional Dynamic Application Security Testing (DAST) depends on responses directly returned to the tester, but many vulnerabilities—like Blind SQL injection, Blind SSRF, or Blind XSS—do not manifest visible in normal responses. OAST works by injecting a payload that triggers a callback to an external server controlled by the tester, which confirms vulnerability presence when that out-of-band interaction appears. Oast+1
In security scanning tools like ZAP and Burp Suite, OAST has become a core feature that significantly enhances blind vulnerability detection. Edgescan+1
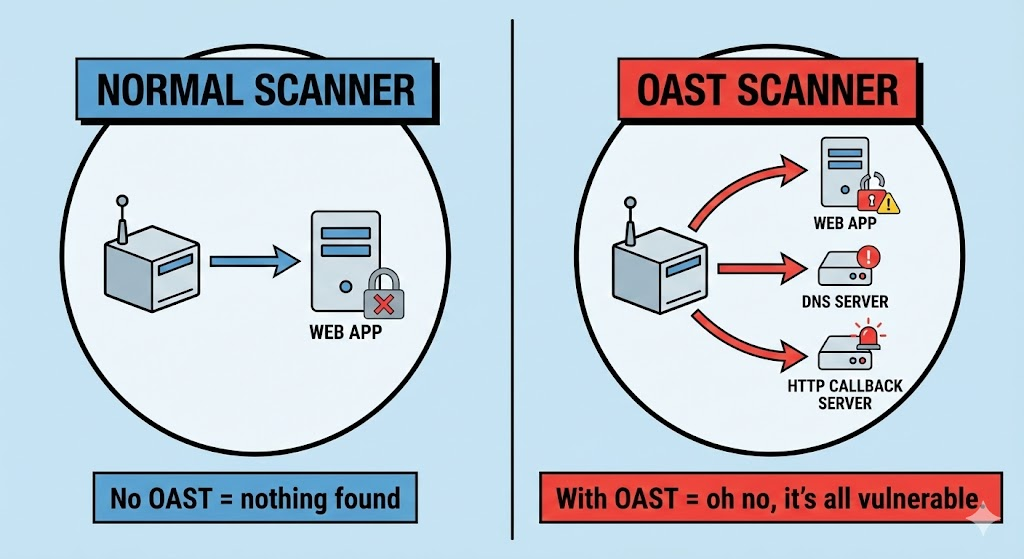
How OAST Works: Mechanics and Protocols
OAST testing typically involves these components:
- Unique Interaction Domain/Subdomain – A resolver domain uniquely associated with this testing cycle, often from an OAST service like Interactsh.
- Payload Injection – Malicious or test payload containing that unique domain.
- Monitoring Server – External system logs any incoming interaction (DNS query, HTTP request, SMTP event, etc.).
- Confirmation Logic – A callback or beacon proves the application processed the payload. HAHWUL
Common Reaction Channels in OAST Testing
| Channel | How It Works | Why It Matters |
|---|---|---|
| DNS | The target app causes a DNS query to the OAST server | Works even in restricted outbound environments |
| HTTP(S) | The target makes a web request to the OAST domain | Confirms deeper interaction |
| SMTP / LDAP / SMB / Others | Various protocols for richer interaction data | Detects diverse classes of vulnerabilities |
This enables OAST to uncover hidden flaws that traditional scanners cannot observe because they only examine the normal protocol path. Edgescan
Why OAST Is Critical in Modern Security
By combining OAST with DAST, testers can confirm vulnerabilities that do not produce visible application responses but do produce observable side-effects in external interaction channels.
PortSwigger highlights that OAST was revolutionary when introduced through Burp Collaborator, enabling Burp to detect new blind vulnerability classes like Blind SQLi or Blind OS command injection. PortSwigger
In 2025, security researchers also identified a sophisticated threat actor running a custom OAST infrastructure on Google Cloud to scan for and exploit 200+ different CVEs in large-scale campaigns, illustrating how OAST techniques can be abused when mass-automation meets vulnerability exploitation. IoT OT Security News

Tools and Platforms That Support OAST
Many modern security tools have integrated OAST support:
- ZAP OAST Support: Built-in listeners for DNS/HTTP(S) interactions and integration with BOAST, Interactsh, etc. ZAP+1
- Burp Suite Collaborator: Provides OAST callbacks to detect blind conditions. PortSwigger
- Interactsh: A powerful open platform for OAST interactions supporting many protocols (DNS, HTTP, SMTP, LDAP, SMB, FTP). HAHWUL
- BOAST: A server designed to collect and report OAST interaction events. ZAP
These platforms help security engineers capture callbacks and confirm vulnerabilities without relying solely on in-band evidence.
Practical OAST Scenarios and Threat Models
OAST is especially useful in identifying blind vulnerabilities, where an attacker can trigger an action on the server—and the only proof is that the server reached out to an external service.
Examples include:
- Blind SSRF – Server does not return data to the attacker but makes outbound HTTP/DNS requests.
- Blind Command Injection – Server runs code that triggers outbound traffic instead of showing output.
- Blind XSS – Persistent script triggers callback behavior when executed in victim contexts. Edgescan
An enterprise defender might see an AlphaSOC alert showing outbound traffic to a known OAST domain, indicating potential unauthorized exploitation or misconfiguration. AlphaSOC
Example Code: Simulating and Detecting OAST
Below are 5 direct attack/defense code examples that engineers can reference.
Example 1: Generating OAST DNS Trigger (Attack)
bash
#This payload will trigger a DNS query to the OAST servercurl <http://example.com?callback=uniqueid.oast.pro>
If the target processes this URL and makes a DNS lookup for uniqueid.oast.pro, the OAST server will log the query.
Example 2: Monitoring OAST Callback with Python
python
from flask import Flask, request
app = Flask(**name**)
@app.route("/callback", methods=["GET"])
def callback():
print("OAST Interaction:", request.remote_addr, request.args)
return "", 200
app.run(host="0.0.0.0", port=8080)
Deploy this simple server and register its domain with a DNS entry to act as an external OAST listener.
Example 3: Logging and Alerting OAST Traffic
python
import logging
def log_oast_event(event):
logging.basicConfig(level=logging.INFO)
logging.info(f"OAST callback from {event['ip']} with data {event['data']}")
Use this pattern to integrate callback alerts into SIEM pipelines.
Example 4: Filtering Outbound Traffic (Defense)
bash
#Block common OAST domains at firewall leveliptables -A OUTPUT -d oast.fun -j DROP iptables -A OUTPUT -d oast.pro -j DROP iptables -A OUTPUT -d oast.site -j DROP
This helps reduce unauthorized OAST callbacks from internal servers.
Example 5: Rejecting Untrusted Interaction Patterns
python
# Simplified request inspector
def is_untrusted_interaction(request):
if "oast" in request.host:
return True
return False
Integrate this function into WAF logic to flag and block suspicious callback endpoints.
Defensive Strategy Beyond Code
While code-level controls are essential, security engineers should adopt holistic defenses:
- Outbound Traffic Control – Apply default deny policies for outbound connections with allow-list rules.
- Block Known OAST Domains at perimeter firewalls.
- Monitor DNS and HTTP traffic for unusual callback domains that resemble OAST payloads.
- Integrate OAST into Testing Workflows (DAST + OAST scanning) to proactively find blind vulnerabilities.
Broad outbound blocking reduces the impact of blind exploitation methods when applications inadvertently process unsafe inputs. HAHWUL
OAST vs. Traditional DAST/SAST
| Testing Method | Detects Blind Flaws | Requires External Server | Typical Use Case |
|---|---|---|---|
| SAST | No | No | Code pattern analysis |
| DAST | Limited | No | Response-based scanning |
| OAST | Yes | Yes | Callback/side-effect based testing |
OAST enhances dynamic testing by revealing issues that only manifest through side-effects outside the HTTP response cycle.
Real-World Campaigns Using OAST-Style Techniques
Recent research uncovered a private OAST infrastructure hosted on Google Cloud used by threat actors to target over 200 CVEs with modified scanning tools and OAST callbacks. This demonstrates that attackers increasingly exploit blind vulnerabilities at scale and the need for defenders to detect such patterns. IoT OT Security News
This also means defenders may need to distinguish legitimate security testing traffic from malicious callback patterns, especially when attackers mimic cloud provider IPs.
Integrating AI-Driven Security Testing – Penligent
For modern engineering teams, traditional automated scanners may miss subtle blind vulnerabilities. Platforms like Penligent add value by:
- Generating AI-assisted OAST payloads with adaptive patterns
- Mapping application surfaces where blind interactions might occur
- Correlating callback evidence across protocols to prioritize real risks
- Integrating OAST tests into CI/CD pipelines for early detection
Penligent’s AI capabilities help uncover “weak signals” of blind vulnerabilities that static rules cannot easily capture, improving overall application security.
Conclusion
Understanding OAST meaning—Out-of-Band Application Security Testing—is crucial for engineers building secure applications. By leveraging OAST methods alongside DAST and SAST, security teams can find blind, asynchronous vulnerabilities that are invisible to traditional response-based scanning. With proper tooling, coding practices, and network controls, engineers can both detect and defend against exploitation techniques that rely on OAST callbacks, strengthening application resilience in the face of evolving threats.


