In the modern cybersecurity landscape, where threats evolve at unprecedented speed, automated penetration testing has emerged as one of the most effective ways to ensure that vulnerabilities are identified and addressed before they can be exploited. Organizations are under intense pressure to maintain a constant awareness of their security posture, and traditional penetration testing often requires days or even weeks of manual effort from highly specialized professionals. This reliance on expert skills, coupled with the need for significant time and resources, makes frequent and comprehensive testing difficult to sustain.
By contrast, automated penetration testing delivers a combination of speed, repeatability, and scalability that changes the security assessment paradigm. Solutions such as Penligent push this transformation further by embedding intelligence into every stage—from understanding natural language commands and orchestrating complex toolchains, to validating findings in real time and producing actionable insights.
What is Automated Penetration Testing?
Automated penetration testing refers to the practice of using specialized software systems to emulate the activities of a malicious intruder and to probe for security weaknesses across networks, systems, and web applications. Unlike conventional vulnerability scanning, which merely identifies potential issues without assessing their actual impact, automated penetration testing takes the additional step of attempting to exploit these weaknesses under controlled conditions.
This provides security teams with not only a clearer picture of the potential threat landscape but also concrete evidence of the feasibility and severity of each vulnerability.
Practical Advantages of Automated Penetration Testing
The most compelling advantage of automated penetration testing lies in its ability to compress the testing timeline from multiple days to a matter of hours without sacrificing accuracy. By maintaining consistent methodology across runs, it eliminates the variability that often arises when different testers conduct assessments manually.
Moreover, its scalability allows organizations to extend security evaluations across hundreds or even thousands of assets without a proportional increase in human effort. When embedded into a continuous integration and deployment pipeline, it creates a living layer of defense that responds to code changes and infrastructure updates in near real time.
With Penligent, these benefits are strengthened further, as its natural language interface acts as a command center for orchestrating over 200 industry-standard tools, while its built-in intelligence ensures that results are not just collected but understood, validated, and prioritized so resources can be focused on addressing the most urgent risks.
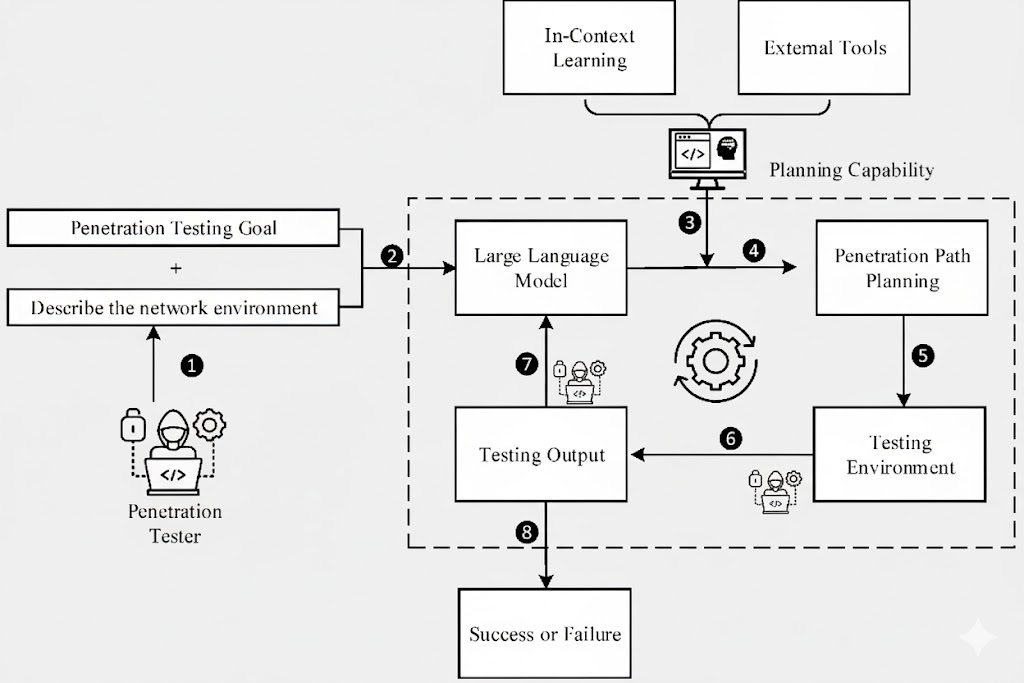
Workflow of Automated Penetration Testing
In practice, automated penetration testing follows a logical sequence designed to mimic the progressive stages of a real-world attack while remaining within a controlled and ethical framework. The process typically begins with asset discovery, whereby the system identifies all accessible endpoints, services, and network components that could form part of the attack surface.
The next step involves comprehensive vulnerability scanning, which leverages multiple scanning engines to detect known flaws ranging from misconfigurations to outdated software versions. Following detection, the testing platform transitions into exploitation and validation, where it attempts to confirm the existence of vulnerabilities by simulating exploitation scenarios. This ensures that results are trustworthy and not merely speculative.
Finally, the process culminates in reporting and remediation guidance, generating a detailed document that outlines confirmed issues, their risk levels, and explicit recommendations for corrective action.
Platforms like Penligent refine this workflow by eliminating the need for manual orchestration between steps. With Penligent, an operator can simply express a goal in natural language—such as “Scan this application for SQL injection risks”—and the AI Agent interprets the request, runs targeted asset discovery, selects appropriate tools (e.g., SQLmap, Nmap, Nuclei), validates all findings in real time, assigns priority rankings, and produces a collaborative report that the security team can act upon immediately. This integrated approach not only speeds up the cycle but also ensures that high-priority vulnerabilities move to the front of the remediation queue without manual triage.
Automated Penetration Testing Workflow Demonstrated in Java
To illustrate the workflow, below is a conceptual Java program that represents the stages of automated penetration testing. Although simplified, it mirrors the key steps—asset discovery, vulnerability scanning, validation, and reporting—and can be extended to integrate actual security tools via command-line or API calls.