Einführung
In cybersecurity, brute force refers to a methodical, exhaustive attempt to guess credentials or cryptographic keys until successful. It is a cornerstone technique for red team operations, penetration testing, and password recovery exercises. Brute force is not about “hacking magic”; it is the operationalization of persistence and systematic search within defined boundaries. From dictionary attacks to hybrid approaches leveraging AI, brute force demonstrates how iterative computation can overcome human and system defenses.
Even in the age of automation and AI, brute force remains relevant. It teaches engineers about attack surface exposure, password policy effectiveness, and rate-limiting mechanisms. Moreover, modern AI-driven security platforms build upon these techniques, orchestrating attacks in a controlled, auditable, and reproducible fashion.
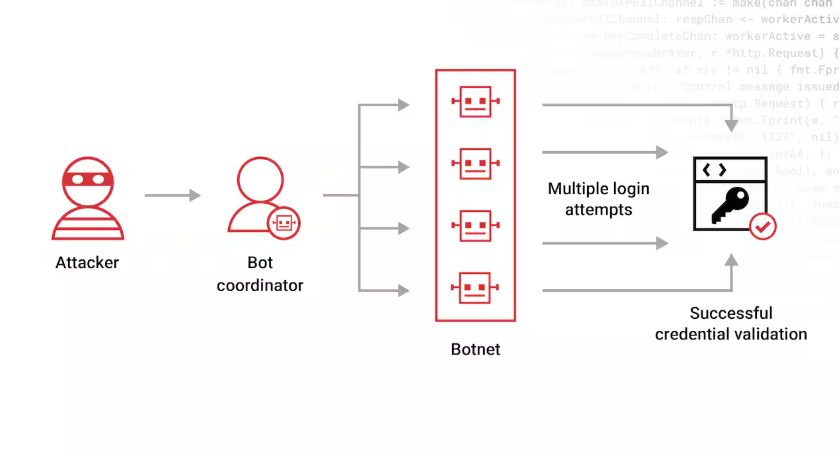
Why Brute Force Matters
Brute force serves as both a practical testing tool and a conceptual benchmark. It highlights weaknesses in authentication, measures entropy in password policies, and validates defensive controls like rate-limiting, MFA, and lockout mechanisms.
Key dimensions of relevance:
- Validation of Security Controls – Confirms whether defenses withstand exhaustive attack attempts.
- AI Training Ground – Provides empirical data for AI-driven penetration testing agents.
- Red-Blue Team Alignment – Bridges offensive technique understanding with defensive strategy implementation.
Classification and Capabilities of Brute Force Tools
Brute force operations can be categorized by target, strategy, and automation level.
| Kategorie | Core Function | Capability Traits | Example Tools |
|---|---|---|---|
| Password Guessing | Attempt user passwords against accounts | Dictionary & hybrid, parallel execution, retry management | Hydra, Medusa, Patator |
| Key Cracking | Recover cryptographic keys | GPU acceleration, rule-based mutation, distributed | John the Ripper, Hashcat, Cain & Abel |
| Web Form Attacks | Brute force login endpoints | Rate-limit awareness, session management, CAPTCHA handling | Burp Suite Intruder, OWASP ZAP, wfuzz |
| Protocol Attacks | Attack protocols like SSH, RDP, FTP | Connection pooling, auto-retry, stealth tuning | Ncrack, THC-Hydra, BruteSSH |
Engineering in Practice: Operationalizing Brute Force
Operationalization ensures reproducibility, auditability, and scalability of brute force tests.
Key practices:
- Output Contracts: structured outputs (JSON / SARIF / custom schema) including parameters, timestamps, results.
- Containerized Execution: run each tool in isolated environments.
- Microservices & Message Bus: wrap tools as remotely invokable jobs, chain via Kafka/RabbitMQ.
- CI/CD Integration: trigger attacks in controlled stages.
- Evidence & Audit Trail: capture command, stdout/stderr, exit code, host info.
Python example — parallel password attempts & unified JSON output:
import subprocess, json, concurrent.futures, os, time
TARGETS = ["10.0.0.5", "10.0.0.7"]
RESULT_DIR = "./out"
os.makedirs(RESULT_DIR, exist_ok=True)
def run_brute(tool_cmd):
meta = {"cmd": tool_cmd, "started_at": time.time()}
try:
proc = subprocess.run(tool_cmd, stdout=subprocess.PIPE, stderr=subprocess.PIPE, timeout=600, text=True)
meta.update({
"rc": proc.returncode,
"stdout": proc.stdout,
"stderr": proc.stderr,
"duration": time.time() - meta["started_at"]
})
except Exception as e:
meta.update({"rc": -1, "stdout": "", "stderr": str(e), "duration": time.time() - meta["started_at"]})
return meta
def brute_target(target):
hydra_cmd = ["hydra", "-L", "users.txt", "-P", "passwords.txt", f"ssh://{target}"]
hashcat_cmd = ["hashcat", "-m", "0", "hashes.txt", "wordlist.txt"]
res = {"target": target, "runs": {}}
res["runs"]["hydra"] = run_brute(hydra_cmd)
res["runs"]["hashcat"] = run_brute(hashcat_cmd)
return res
def main():
out = {"generated_at": time.time(), "results": {}}
with concurrent.futures.ThreadPoolExecutor(max_workers=4) as ex:
futures = {ex.submit(brute_target, t): t for t in TARGETS}
for fut in concurrent.futures.as_completed(futures):
t = futures[fut]
out["results"][t] = fut.result()
with open(f"{RESULT_DIR}/brute_results.json", "w") as fh:
json.dump(out, fh, indent=2)
if __name__ == "__main__":
main()
Penligent: Intelligent Pentesting with 200+ Hacking Tools
Penligent transforms brute force and broader pentesting workflows into AI-orchestrated, auditable processes. By parsing natural language instructions, the platform automatically selects appropriate tools (including brute force engines like Hydra/Hashcat), validates findings, prioritizes risks, and generates professional reports.
Example scenario:
Command: “Check subdomain X for weak passwords and SSH exposure”
Workflow: asset discovery → endpoint enumeration → dictionary/hybrid brute force → verification → report generation. All metadata, logs, and outputs are recorded for traceability.
In CI/CD pipelines, Penligent ensures continuous security feedback: any code or infrastructure change triggers targeted scans, high-priority findings generate tickets, and mitigation guidance is automatically attached. Brute force attacks are thus safely operationalized within corporate compliance standards.
Hardening playbook — prioritized engineering controls
Quick prioritized matrix
| Priorität | Kontrolle | Auswirkungen | Effort |
|---|---|---|---|
| P0 | Enforce MFA for all privileged accounts | Very High | Low–Medium |
| P0 | Block known leaked credentials (HIBP) at auth time | Very High | Mittel |
| P0 | Adaptive rate limiting + bot management on auth endpoints | Very High | Mittel |
| P1 | Strong password hashing (Argon2id with tuned params) | Hoch | Low |
| P1 | SIEM detections for multi-IP / velocity anomalies | Hoch | Mittel |
| P2 | Session & device risk scoring (SSO/risk engine) | Mittel | Medium–High |
| P2 | WAF rules + challenge pages for suspicious flows | Mittel | Mittel |
| P3 | Canary accounts / deception traps for credential stuffing | Mittel | Mittel |
| P3 | Harden SSH / RDP (jump hosts, conditional access) | Mittel | Low–Medium |
Enforce Multi-Factor Authentication (MFA) — practical policies
- Policy: Mandatory MFA for all privileged roles and for any staff accessing provisioning/infra/UI consoles. Gradually roll out to all users. Prefer phishing-resistant methods (FIDO2/WebAuthn, hardware keys) for admins.
- Implementation tips:
- For SSO (OIDC/SAML), require
acroderauthnContextClassRefthat denotes MFA. - Enforce step-up authentication for risky actions (password change, API key creation).
- For legacy apps that cannot support MFA natively, front them with an SSO or proxy that enforces MFA.
- For SSO (OIDC/SAML), require
- Monitoring: track % of privileged users with MFA enabled, failed MFA attempts, and step-up events. Alert if > X% of privileged logins lack MFA.
Block known leaked credentials — HaveIBeenPwned (HIBP) integration example
- Approach: At registration and at each login (or password change), check candidate password against a leaked-password feed. Use k-anonymity HIBP API to avoid sending full password. If password is observed in breach, block and force rotation.
- HIBP k-anonymity flow (sketch):
- Compute SHA-1(password) → prefix (first 5 hex chars) and suffix.
- Query
https://api.pwnedpasswords.com/range/{prefix}→ receive list of suffixes + counts. - Check whether your suffix is present — if yes, treat as breached.
- Policy: deny top N leaked passwords; optionally deny any password with leak count > threshold (e.g., > 100). Log occurrences and notify users.
Code (Python) sketch:
import hashlib, requests
def is_pwned(password):
s = hashlib.sha1(password.encode('utf-8')).hexdigest().upper()
prefix, suffix = s[:5], s[5:]
r = requests.get(f"<https://api.pwnedpasswords.com/range/{prefix}>")
return suffix in r.text
# Usage: on password set/change or periodically check stored creds (hashed), block if pwned
Adaptive rate limiting & bot management — concrete configs
- Principles: rate limit by (a) IP, (b) account, (c) IP+account, and (d) ASN/geolocation. Combine token bucket for burst tolerance with progressive backoff on repeated failures.
- Nginx example (basic rate limit by IP):
# nginx.conf snippet
limit_req_zone $binary_remote_addr zone=auth_zone:10m rate=5r/s;
server {
location /login {
limit_req zone=auth_zone burst=10 nodelay;
proxy_pass http://auth_service;
}
}
- Cloudflare / WAF: enable Bot Management, set challenge for suspicious scores; create custom WAF rule for auth POSTs with high request velocity.
- Progressive response: on first threshold → serve 429 or CAPTCHA; on higher severity → temporary block / require password reset.
Account lockout and password spraying mitigation — calibrated policies
- Problem: naive per-account lockout lets attackers test denial-of-service against accounts. Password spraying avoids per-account lockouts by trying few common passwords across many accounts.
- Recommended calibrated policy:
- Per-account: after N_failures = 10 fails within 10 minutes → increase challenge (CAPTCHA / MFA step-up) or temporary soft lock (e.g., 15 minutes).
- Spraying detection: if many different accounts show single failures from same IP / ASN → trigger IP throttle or require CAPTCHA on the originating IP.
- Progressive: implement an escalating policy rather than permanent lockout: challenge → MFA → temp lock → admin review.
- Example rule:
if failures(account) >= 10 && unique_ips(account) >= 5 -> require password reset & MFA.
Password storage & hashing — Argon2id recommended parameters
- Don’t use: plain SHA or unsalted MD5. Use modern KDFs. Argon2id is recommended for new systems; fallback to bcrypt if needed.
- Suggested baseline params (2025 guidance):
time_cost = 3,memory_cost = 64 * 1024KB (64 MB),parallelism = 2— tune upward as hardware allows.- Store salt (≥ 16 bytes) and KDF params with the hash.
- Rotation: provide a migration path — rehash on next login if params are stale. Cache/monitor average bcrypt/Argon2 timing to avoid DOS via expensive hashing.
SIEM / detection rules — Splunk & KQL examples
Detect many failed logins to different accounts from same IP (credential spraying indicator):
index=auth_logs action=failure | stats dc(user) as users, count as failures by src_ip | where users > 20 AND failures>50
Detect suspicious account with high unique IPs in 5 minutes:
index=auth_logs earliest=-5m | stats dc(src_ip) as uniq_ips, count as fails by user | where uniq_ips > 5 AND fails > 10
KQL (Azure) example
SigninLogs
| where ResultType != 0 and TimeGenerated > ago(10m)
| summarize failures = count(), distinctIPs = dcount(ClientIP) by UserPrincipalName
| where failures > 10 and distinctIPs > 4
Bot-management & WAF integration — playbook items
- Deploy a bot management solution (Cloudflare Bot Management, Akamai, PerimeterX). Tie bot score into decisioning — e.g., score > 80 → challenge, >95 → block.
- For critical auth endpoints: set WAF rules to inspect POST body patterns; block known credential stuffing signatures and throttle suspicious IPs.
- Ensure WAF logs feed SIEM with enough request context to perform replay/POC validation.
Deception & canary accounts — detection amplification
- Create monitored “canary” accounts with strong but realistic names; any failed attempts against them are high-confidence threats (because they are not in normal use).
- Instrument canaries to produce high-priority alerts and auto-block source IPs. Use decoy login endpoints that never receive legitimate traffic.
Testing, metrics & SLAs — how to measure success
Key metrics to track
- Mean Time to Detect (MTTD) for credential stuffing events.
- Mean Time to Respond (MTTR) for blocking source IPs / escalating to remediation.
- % privileged logins with MFA enabled.
- False-positive rate of brute-force detections (aim < 5% after tuning).
- Number of successful account takeovers (goal: 0); time between detection and containment.
Testing
- Schedule red-team simulations / agentic pentest runs to validate controls. Use staging environment for controlled credential spraying tests. Integrate the run with incident playbooks.
Schlussfolgerung
Brute force remains a foundational technique, both as a teaching tool and an operational necessity. Properly engineered, monitored, and AI-orchestrated, it evolves from a simple attack method to a reproducible, auditable security testing strategy. Platforms like Penligent illustrate how intelligent automation can safely operationalize brute force, integrate it with broader pentesting workflows, and continuously reinforce defenses.