In cybersecurity, deserialization is far more than a routine programming task—it’s often a hidden attack vector. While its primary purpose is to restore data into objects, without strict input validation and filtering, attackers can leverage carefully crafted payloads to perform remote code execution, bypass authorization, or even seize complete system control.
These risks are not only uncovered during traditional manual penetration testing but also appear frequently in automated scanning tools, vulnerability research platforms, and AI-powered threat analysis systems, making this process a high-priority concern for modern security teams.

Code Example – Insecure Deserialization
// ⚠️ Insecure Deserialization ExampleObjectInputStream in = new ObjectInputStream(new FileInputStream("payload.bin"));
Object obj = in.readObject();// This could execute malicious code from payload
in.close();
How Does Deserialization Operate in Systems?
Serialization converts complex objects into formats like JSON, XML, or binary streams for easy storage or transfer. Deserialization reverses the process, reconstructing data back into program-ready objects.
In distributed computing, API interaction, and data persistence, deserialization is ubiquitous. This ubiquity attracts attackers: when the data source is untrusted, malicious logic can be introduced during reconstruction, leading to severe security threats.
Why Do Deserialization Vulnerabilities Occur and How Are They Typically Created?
Such flaws usually result from multiple weaknesses combined. For instance, applications may directly deserialize binary streams from user input without validation; default language or framework mechanisms may allow unrestricted class loading; and security audits during development may fail to adequately assess serialization processes. Together, these weaknesses create openings attackers can use.
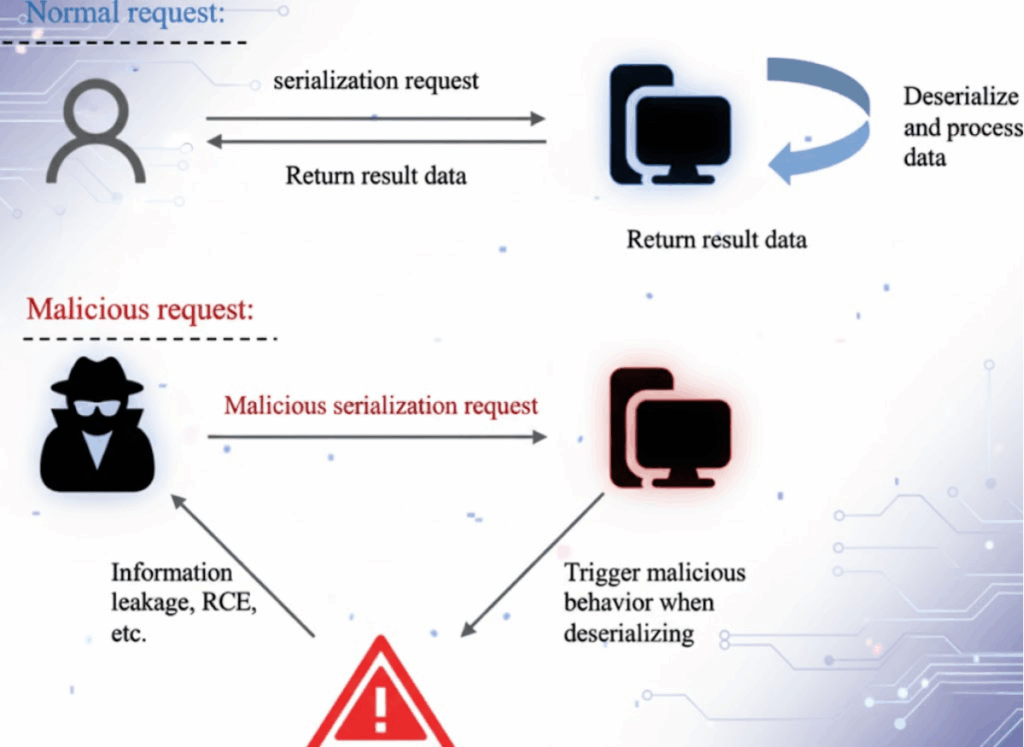
How Do Attackers Exploit Deserialization Vulnerabilities in Penetration Testing to Gain Control?
During penetration testing, attackers often craft malicious object payloads so that when the system deserializes them, embedded code is executed.
They may use tools like YSoSerial to generate these payloads, enabling remote code execution, or reconstruct high-privilege user objects, bypassing authentication mechanisms.
Command Example – Generating Malicious Payload
java -jar ysoserial.jar CommonsCollections1 "calc.exe" > payload.bin
Java Execution Example
ObjectInputStream in = new ObjectInputStream(new FileInputStream("payload.bin"));
Object obj = in.readObject();// Executes calc.exe
How Can Deserialization Vulnerabilities Be Identified and Verified In Security Testing?
Security professionals often combine manual testing, where they craft suspicious inputs and observe system behavior, with automated tools like Burp Suite plugins and YSoSerial to quickly locate potential weaknesses.
Advanced setups may employ AI-based models to analyze deserialization traffic patterns, detecting possible attack signatures.
Python Example – AI-Based Traffic Analysis
import joblib
import numpy as np
model = joblib.load("deserialize_detector.pkl")
sample_data = np.array([feature_vector])
prediction = model.predict(sample_data)
if prediction == 1:
print("⚠️ Suspicious Deserialization Detected")
What Measures Should Developers and Security Teams Take to Defend Against Deserialization Attacks?
To effectively defend against deserialization attacks, developers and security teams must first adopt the security mindset that every piece of input data could be untrusted, regardless of its apparent source or format. This awareness is critical because untrusted or insufficiently sanitized data can, during the deserialization process, be reconstructed into objects containing malicious logic, directly exposing the application to severe threats such as remote code execution or privilege escalation.
A robust defense strategy should start with rigorous input validation, ensuring that any data subject to deserialization undergoes complete checks for structural consistency, permissible value ranges, and compliance with expected formats. Development teams should avoid relying on native language or framework default deserialization mechanisms, as these are often overly permissive and lacking in robust safeguards; instead, secure serialization libraries or frameworks with explicit safety controls should be preferred. Furthermore, enforcing a strict class whitelist policy is highly advisable—by restricting the deserialization process to a predefined set of safe object types, the risk of unintentionally loading malicious or unknown classes can be greatly reduced.
Beyond protections implemented at the code level, deserialization security checks must be integrated into the broader DevSecOps workflow to ensure they form part of continuous integration and deployment cycles, rather than being introduced only as an afterthought before production release. This integration enables vulnerabilities to be detected and addressed early in the development lifecycle, minimizing remediation costs and impact. Additionally, detailed logging and anomaly detection should accompany all deserialization operations so that any irregular activity—such as attempts to instantiate disallowed classes or unexpected execution paths—can trigger immediate alerts and prompt security investigations.
When these measures are applied consistently and supported by ongoing developer training in secure coding practices, organizations can substantially reduce the risks associated with deserialization, turning what has historically been a frequent and high-impact attack vector into a controlled and manageable aspect of secure application design.
Java Example – Safe Deserialization
ObjectMapper mapper = new ObjectMapper();
Class<?> allowedType = MySafeClass.class;
FileInputStream fis = new FileInputStream("safeData.json");
Object obj = mapper.readValue(fis, allowedType);
fis.close();
How Will Deserialization Security Evolve in the Future, and What Role Will AI Play?
The future of deserialization security will increasingly revolve around intelligent agents capable of understanding, deciding, and executing security tasks.
Penligent is a prime example—it’s the world’s first Agentic AI Hacker, able to handle the entire penetration testing process for deserialization vulnerabilities from natural language prompts.
Leveraging over 200 integrated tools (such as Nmap, Burp, Nuclei, and YSoSerial), Penligent not only runs scans but thinks like a security professional: validating vulnerabilities, filtering false positives.


