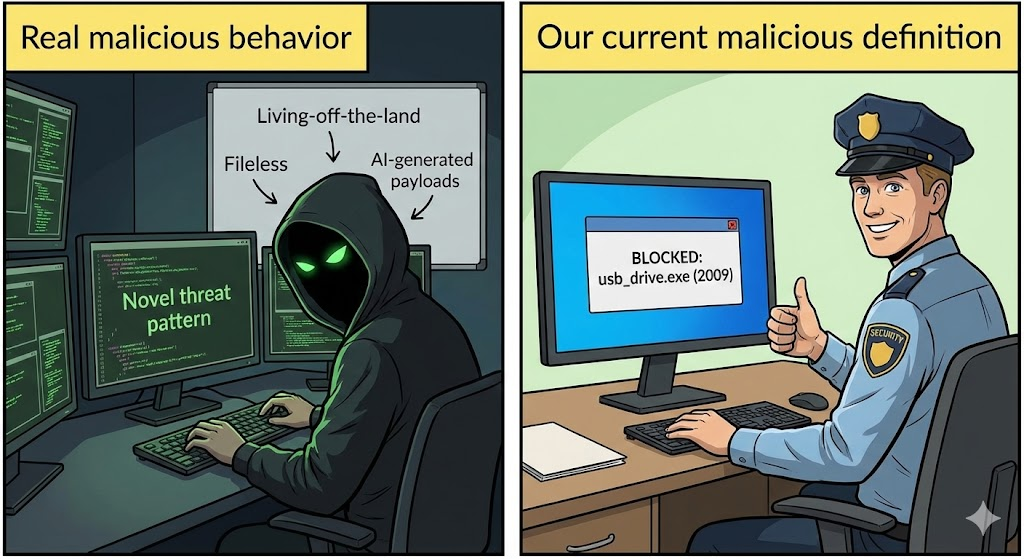
En la ciberseguridad moderna, definición maliciosa se refiere a cualquier comportamiento, código o intención diseñados para dañar sistemas, redes, datos o usuarios-Violación intencionada de la integridad, confidencialidad o disponibilidad. Esta definición es fundamental porque lo sustenta todo, desde el modelado de amenazas hasta la detección automatizada, la ingeniería de respuesta y los libros de jugadas de los adversarios en las pruebas de penetración. En términos sencillos, las acciones maliciosas no son fallos accidentales, sino operaciones intencionadas diseñadas para socavar los objetivos de seguridad. N2K CyberWire
Este artículo explora cómo se entiende "malicioso" en contextos técnicos, cómo se manifiesta en ataques reales, cómo los defensores pueden clasificar y mitigar los patrones maliciosos, y cómo las herramientas de seguridad basadas en IA, tales como Penligente puede ayudar a los ingenieros a detectar y responder a las actividades maliciosas a escala.
Qué significa realmente "malicioso" en ciberseguridad
La palabra "malicioso" en inglés sencillo denota intención malintencionada o dañinapero en ciberseguridad, se refiere específicamente a acciones que comprometer el funcionamiento esperado o el modelo de confianza de los sistemas. Según un glosario ampliamente aceptado en el sector, el comportamiento malicioso se refiere a acciones hostiles contra sistemas, datos o redes que causan daños, pérdidas o accesos no autorizados. N2K CyberWire
Esta definición separa la actividad maliciosa de los fallos accidentales o errores benignos. Por ejemplo, un fallo de software que borra accidentalmente registros es dañino pero no malicioso; malicioso significa que hay una estrategia deliberada para dañar o explotar. Esta distinción es fundamental para crear modelos de amenazas precisos y desplegar una automatización eficaz para detectar amenazas reales.
Fallos malintencionados y no malintencionados
| Categoría | Descripción | Ejemplo |
|---|---|---|
| Malicioso | Intención de dañar o explotar | Instalación de malware, filtración de datos |
| Error involuntario | Bug o error de configuración | Pérdida accidental de datos por error lógico |
| Anomalía desconocida | Comportamiento que requiere investigación | Pico inesperado en el uso de la CPU |
Al definir claramente el comportamiento malicioso, los equipos de seguridad pueden refinar las reglas de detección y reducir los falsos positivos.
Manifestaciones comunes de comportamiento malicioso
Una expresión primaria de intención maliciosa en el entorno digital es malwareEl malware es una contracción de "software malicioso", diseñado para perturbar los sistemas, robar datos o proporcionar acceso no autorizado. El malware funciona como una clase de amenazas que encarnan intenciones hostiles y van desde simples virus a amenazas persistentes avanzadas. eunetic.com
Tipos de software malicioso y ataques
| Tipo de amenaza | Función maliciosa | Ejemplo |
|---|---|---|
| Virus | Se autorreplica e infecta los archivos del anfitrión | Infector de archivos clásico |
| Gusano | Se propaga por las redes de forma autónoma | Conficker |
| Troyano | Se hace pasar por software benigno | Entrega de RAT |
| ransomware | Cifra los datos y pide un rescate | WannaCry |
| Spyware | Roba datos silenciosamente | Software espía de registro de pulsaciones de teclas |
| Agente de botnet | Permite el control remoto | Redes de bots DDoS |
El comportamiento malicioso también aparece en amenazas no informáticas como el phishing (ingeniería social para engañar a los usuarios), las URL maliciosas (diseñadas para alojar o distribuir programas maliciosos), el abuso de información privilegiada o los ataques distribuidos de denegación de servicio destinados a saturar los sistemas.
Cómo se desarrollan las acciones maliciosas: De la intención a la explotación
Entender la intención maliciosa es abstracto; ver cómo se desarrolla en ataques reales es concreto. Los actores de las amenazas diseñan operaciones maliciosas combinando diversas tácticas, como la explotación de vulnerabilidades, la ingeniería social y la persistencia encubierta. El malware moderno utiliza a menudo técnicas de ofuscación, polimorfismo y anti-sandbox para eludir la detección, lo que hace que las defensas tradicionales sean insuficientes por sí solas. techtarget.com
Estudio de caso CVE: CVE-2024-3670 (Ejemplo)
Una reciente vulnerabilidad de alta gravedad (CVE-2024-3670) en una importante aplicación web empresarial permitía a los atacantes desplegar la funcionalidad de carga de archivos arbitrarios sin la desinfección adecuada. Los atacantes podían cargar un shell web -un script malicioso- que conducía a la ejecución remota de código. Esta carga maliciosa permitía el movimiento lateral y el acceso persistente en el entorno de la víctima.
php
// Carga de archivos insegura (riesgo de exploit malicioso) if ($_FILES['upload']) {move_uploaded_file($_FILES['upload']['tmp_name'], "/var/www/html/" . $_FILES['upload']['name']); }
Mitigación defensiva: Valide siempre los tipos de archivo, aplique el escaneado de archivos y restrinja las rutas de carga.
Distinción entre patrones maliciosos y actividad normal
La mejor forma de captar las intenciones maliciosas no es mediante señales aisladas, sino mediante patrones. Los equipos de seguridad combinan varios indicadores -conexiones de red inesperadas, cambios de archivos no autorizados, procesos inusuales, etc.- para detectar verdaderas actividades maliciosas.
Indicadores de comportamiento
- Conexiones salientes inesperadas a dominios maliciosos conocidos
- Cambios inusuales en el sistema de archivos (archivos cifrados, ejecutables fraudulentos)
- Patrones de escalada de privilegios
- Mecanismos de persistencia (claves de ejecución del registro, cron jobs, instalación de servicios)
Las herramientas de análisis de comportamiento utilizan métodos estadísticos o basados en ML para separar las anomalías benignas de los patrones genuinamente maliciosos.
Muestras de código de ataque y defensa: Patrones maliciosos
A continuación se presentan ejemplos prácticos que ilustran la actividad maliciosa y la codificación defensiva segura.
- Inyección SQL
Patrón malicioso:
sql
SELECT * FROM usuarios WHERE nombredeusuario = '" + userInput + "';";
Esto permite a los atacantes vectores como OR '1'='1 para evitar la autenticación.
Defensa segura (consulta parametrizada):
python
cur.execute("SELECT * FROM usuarios WHERE nombredeusuario = %s", (userInput,) )
- Inyección de comandos
Patrón malicioso:
python
import os os.system("cat " + filename) # Dangerous if filename crafted by user
Patrón defensivo (lista blanca):
python
allowed_files = {"readme.txt", "config.json"}if filename in allowed_files: os.system(f "cat {filename}")
- Secuencias de comandos en sitios cruzados (XSS)
Malicioso:
html
<script>alert('xss')</script>
Defensa (huida):
javascript
res.send(escapeHtml(userInput));
- Escritura arbitraria de archivos
Intento malicioso:
javascript
fs.writeFileSync("/etc/passwd", userControlledContent);
Defensa:
javascript
const safePath = ruta.join("/data/safe", ruta.basename(nombrearchivo));
Estrategias de detección de actividades maliciosas
La detección moderna utiliza enfoques por capas:
- Basado en firmas detección: Reconoce patrones maliciosos conocidos.
- Comportamiento detección: Supervisa las anomalías en tiempo de ejecución.
- Análisis Sandbox: Ejecuta código sospechoso de forma aislada para observar comportamientos maliciosos.
- Integración de inteligencia sobre amenazas: Utiliza feeds actualizados para detectar COIs conocidos.
Estos métodos ayudan a detectar tanto las tácticas maliciosas conocidas como las nuevas.
El papel de la automatización y la IA en la detección de patrones maliciosos
A medida que las amenazas se han vuelto más adaptables, confiar únicamente en firmas estáticas ya no es viable. La IA y el aprendizaje automático ayudan a detectar patrones maliciosos ofuscados y de día cero correlacionando comportamientos inusuales entre fuentes de telemetría y aprendiendo perfiles típicos benignos frente a maliciosos.
Por ejemplo, las campañas avanzadas de malware como servicio ocultan cada vez más cargas útiles en canales cifrados y utilizan señuelos de phishing generados por inteligencia artificial para engañar a los usuarios, por lo que la detección proactiva resulta esencial.
Penligent: Detección y respuesta al malware basadas en IA
En entornos en los que las superficies de amenazas maliciosas son grandes y dinámicas, el análisis manual por sí solo no puede seguir el ritmo. Penligente aprovecha la IA para automatizar y ampliar los flujos de trabajo de detección y corrección de actividades maliciosas:
- Análisis automatizado de rutas de código en busca de patrones maliciosos incrustados.
- Perfiles de comportamiento para detectar desviaciones compatibles con intenciones maliciosas.
- Alertas priorizadas basadas en la puntuación del riesgo y el impacto potencial.
- Integración en procesos CI/CD y DevSecOps para detectar patrones maliciosos en una fase temprana.
Al combinar la experiencia en el dominio con la heurística basada en IA, Penligent ayuda a los equipos de seguridad a adelantarse a los actores de amenazas y a reducir el tiempo medio de detección y respuesta.
En la práctica, esto significa que un ingeniero de seguridad puede centrarse en investigaciones de alto valor mientras el sistema tamiza miles de millones de eventos para detectar verdaderas amenazas mediante análisis contextuales.
Construir una postura defensiva contra las amenazas maliciosas
La defensa frente a actividades maliciosas no se basa únicamente en herramientas específicas, sino también en la disciplina arquitectónica:
- Segmentación de la red limita el movimiento lateral.
- Menor privilegio reduce el radio de explosión de las brechas.
- Control continuo garantiza una detección precoz.
- Guías de respuesta a incidentes reducir el tiempo de recuperación.
Estas medidas se combinan con la detección automática para defenderse de las actividades maliciosas, tanto oportunistas como selectivas.
Conclusiones: Definición maliciosa como conocimiento básico de seguridad
Comprender la definición maliciosa en ciberseguridad no es sólo académica, sino práctica y práctica. Orienta el modelado de amenazas, la heurística de detección, la codificación defensiva y los flujos de trabajo de respuesta a incidentes. Diferenciar las intenciones maliciosas de los errores permite a los equipos asignar recursos de forma eficiente, priorizar las amenazas reales y crear estrategias de mitigación sólidas. Combinando esta base conceptual con modernas plataformas de automatización como Penligente arma a los ingenieros de seguridad con amplitud y profundidad en la defensa contra las amenazas maliciosas en evolución.