A CSRF token mismatch occurs when the anti-forgery token sent with an HTTP request does not match the token the server expects for the user’s session. In practice, this mismatch either signals that the request is not legitimately from the user (thereby thwarting a potential cross-site request forgery attack) or points to a serious implementation or configuration failure that jeopardizes both usability and security.
For the modern security engineer, understanding CSRF token mismatch is not just about preventing trivial form-post failures. It’s about recognizing a subtle but powerful indicator of session misconfiguration, caching anomalies, proxy layer interference, SPA/API token gaps, or even an active attack in progress.
If you build or secure web apps with authenticated sessions, APIs, or SPAs — or you run automated vulnerability scans / CI pipelines — mastering CSRF token mismatch as a category will sharpen both your detection and remediation posture.

Why CSRF Token Mismatch Matters to Security Engineers
Cross-Site Request Forgery (CSRF) remains one of the stealthiest web-attack vectors: a user logs into a web app, and an attacker tricks the browser into sending a request that the site trusts because it comes from the user’s session context. In the best-designed systems, that trust is broken by validating a server-generated, session-bound CSRF token; when that token fails to match, you get the “token mismatch” error.
But from a practitioner’s lens:
- A token mismatch may appear as a benign error (user complaints: “why can’t I submit the form?”) but it may expose deeper issues: broken session handling, incorrect cookie/SameSite flags, improper caching, or even unnoticed malicious requests.
- In penetration testing / automation, these errors are actionable signals — for example, they may show up as 403/419 responses, revealing that a state-changing endpoint is guarded, but perhaps only partially, or that the protection is mis-configured or bypassable.
- From a DevOps perspective, frequent mismatches in logs may point to regressions (e.g., reverse proxy changed, CDN caches stale pages, session driver altered) which reduce user trust or open doors for new attack vectors.
- In an AI-driven automation pipeline, capturing and classifying mismatch errors helps build models of normal vs anomalous flows, enabling proactive alerting of drift or potential exploitation.
Thus, CSRF token mismatch is more than a bug — it’s a visibility lever for both defenses and offense.
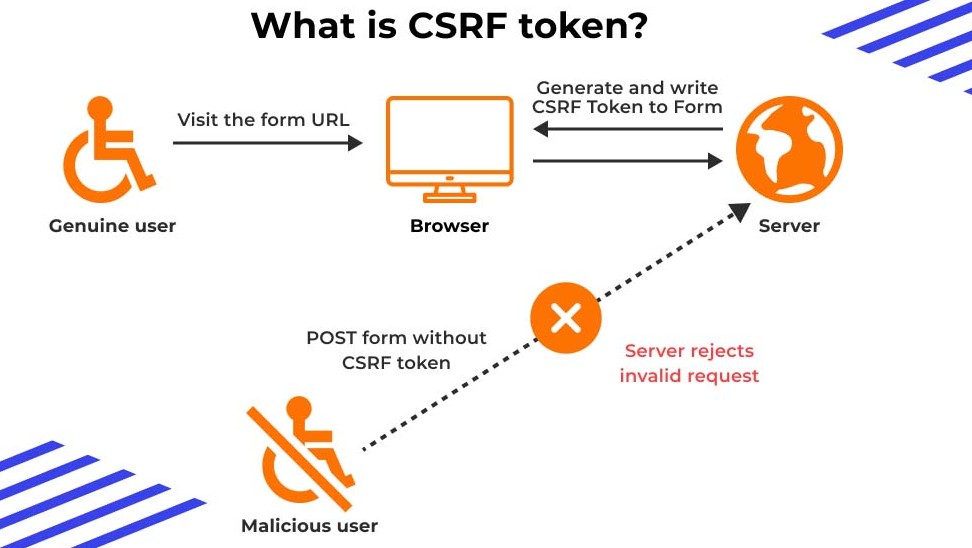
CSRF Protection Workflow
To diagnose mismatches effectively, you must map how CSRF is implemented end-to-end.
Token lifecycle
- When a user loads a page or initiates a session, the server generates a cryptographically random / unpredictable CSRF token.
- Server stores the token (session store, cookie store, or implicitly in stateless architectures).
- The token is embedded in the client payload: hidden <input> in forms, custom header (e.g.,
X-CSRF-TOKEN), or via double-submit cookie. - When a state-changing request (POST, PUT, DELETE) arrives, server verifies:
- that the token exists in the request, AND
- it matches the stored session or expected value.
- If verification fails → “CSRF token mismatch” → request rejected (403/419) or flagged.
In modern SPAs/APIs:
- Cookies with
SameSite=Strict/Lax,Secure,HttpOnlyflags help prevent credential theft. - Double-submit cookie model: token stored in cookie et sent in header/body, server compares both.
- Stateless JWT/CSRF token patterns embed HMAC signatures rather than session store. wiz.io+1
Understanding exactly where the token is generated, stored, and checked is critical in locating mismatch failures.
Root Causes of CSRF Token Mismatch Errors
Below is a table cataloging the most frequent causes of CSRF token mismatch and how to triage them:
| Root Cause | Diagnostic Signal | Quick Fix |
|---|---|---|
| Session expiration / regenerated token | User sees mismatch after inactivity | Increase session TTL or refresh token on login |
| Cached form/html includes stale token | Token value doesn’t match live session | Disable caching for forms; add Cache-Control headers |
| AJAX/SPA missing token header | Fetch/Axios requests succeed without header; mismatch only when header omitted | Ensure every request includes token header (e.g., X-CSRF-TOKEN) |
| Cookie domain/subdomain mis-config | Token cookie not sent, or session mismatch across subdomain | Align cookie domain, ensure same origin or SAN subdomain |
| SameSite / Secure / HttpOnly mis-config | CSRF cookie not sent in cross-site context, causing mismatch | Utilisation SameSite=Lax ou Strict, Secure if HTTPS; document cross-site flows |
| Reverse proxy, load balancer, CDN interference | Token mismatch only behind proxy layer | Ensure proxies forward headers, disable caching that strips tokens |
| Token regeneration at unexpected time | Multiple tokens generated in same session, browser uses old one | Do not regenerate CSRF token per form; only once per session unless needed |
| Browser extension / blocking cookies/scripts | Token cookie not created/read | Ask user to whitelist site or disable interfering extensions (e.g., adblockers) |
This table should serve as a diagnostic cheat-sheet when you see mismatch logs in your SIEM or pentest output.
Framework & Platform Deep Dive
Now let’s look at how popular frameworks implement CSRF and where CSRF token mismatch often surfaces.
Laravel (PHP)
Laravel attaches a TokenMismatchException when the token fails to verify. Bright Security+1 Typical issues: SESSION_DRIVER mis-configuration, cached views embedding outdated tokens, missing <meta name="csrf-token"> tag.
Snippet (AJAX setup):
// in Blade template header
<meta name="csrf-token" content="{{ csrf_token() }}">
<script>
$.ajaxSetup({
headers: {
'X-CSRF-TOKEN': $('meta[name="csrf-token"]').attr('content')
}
});
</script>
Django (Python)
Django uses the CsrfViewMiddleware et {% csrf_token %} template tag. Common pitfalls: views decorated incorrectly, AJAX not sending X-CSRFTOKEN header, CSRF_TRUSTED_ORIGINS mis-set.
Snippet:
<form method="post" action="/update-profile">
{% csrf_token %}
<!-- form fields -->
</form>
<script>
fetch('/update-profile', {
method: 'POST',
headers: {
'X-CSRFToken': getCookie('csrftoken'),
'Content-Type': 'application/json'
},
body: JSON.stringify({name: 'Alice'})
});
</script>
Node/Express (JavaScript)
Using csurf middleware with cookie-parser. Token mismatch often when cookie not forwarded or CSRF token header missing.
Snippet:
const express = require('express');
const csurf = require('csurf');
const cookieParser = require('cookie-parser');
const app = express();
app.use(cookieParser());
app.use(csurf({ cookie: true }));
app.get('/form', (req, res) => {
res.render('sendForm', { csrfToken: req.csrfToken() });
});
app.post('/process', (req, res) => {
// csurf verifies token automatically
res.send('Success');
});
SPAs / API Backends
In single-page apps or API-first architectures, common miss: not requesting initial token endpoint (e.g., /csrf-cookie), or using token from previous session.
“I eventually got it working… first you need to make a GET request to sanctum default csrf endpoint … then manually add header X-XSRF-TOKEN with cookie value.” Reddit
With this awareness, you can tailor your automation to verify the token lifecycle properly.
Penetration Testing & Hunting CSRF Token Mismatch
For a pentester or security engineer, CSRF token mismatch is not only a defensive mechanism: it’s an intel signal. Here’s how you turn it into a reconnaissance/attack vector.
- Scan endpoints that perform state-changing operations (POST, PUT, DELETE). Note responses: 403/419 often indicate CSRF protection triggered.
- Automated fuzzing: send requests without token, with invalid token, token from prior session. Compare response behaviours (200 vs 403) to map unprotected endpoints.
- Session hijack chaining: Suppose token mismatch occurs only when cookie domain differs or token recycled: you may exploit session fixation, proxy header override, or reverse-proxy mis-forwarding to bypass CSRF.
- Proxy cache poisoning vector: If cached HTML contains stale token and load-balanced users reuse it, you may reproduce a valid token for another user session.
- Exploit UI flows: Use a crafted link or iframe to force a token-less request; if it triggers mismatch, you know the token checking exists — next step: attempt missing/reflected token vulnerabilities or SameSite bypass.
Example script skeleton (Python):
import requests
session = requests.Session()
# Step A: get initial page with CSRF token
resp = session.get("<https://target.app/profile>")
token = parse_token(resp.text)
# Step B: send state-change without token
bad = session.post("<https://target.app/update>", json={'name':'Evil'})
print("Response code (no token):", bad.status_code) # expect 419/403
# Step C: send with token
good = session.post("<https://target.app/update>",
headers={'X-CSRF-TOKEN': token},
json={'name':'Evil'})
print("Response code (with token):", good.status_code) # expect 200
Logs showing responses switching between success and mismatch are high-signal for mis-config.
Automated Detection & Remediation with Penligent.ai
Modern security teams integrate automation and AI to detect regression, vulnerabilities and drift — this is where Penligent.ai enters the picture.
Platform integration
Penligent.ai’s intelligent pentest platform automates detection of CSRF-related flaws, including CSRF token mismatch. It crawls authentication flows, tracks token lifecycles, injects malformed or absent token variants, and correlates results to generate actionable findings. By combining machine-learning anomaly detection with rule-based validation, Penligent surfaces endpoints where token mismatches happen in-production or in CI-only environments. Security engineers can then filter by “frequent token mismatch” to prioritize fix-worthy flows.
Workflow example
Integrate Penligent.ai in your CI/CD pipeline so that each build triggers a scan of all state-changing endpoints. When a mismatch occurs, Penligent produces a finding: endpoint /api/v1/settings, response code 419, token missing header, same request with token returns 200. It attaches request/response dump, curl-replay, remediation suggestion (e.g., “Ensure X-CSRF-TOKEN header set and cookie domain aligns”). Over time you gain baseline metrics (mismatch frequency, new endpoints exposed) and can monitor drift via dashboard metrics. That means you move from reactive debugging of CSRF token mismatch errors to proactive prevention.
Engineering Best Practices & Hardening Checklist
Here is a checklist intended for both development and security teams to sweep for vulnerabilities around CSRF token mismatch.
- Token generation: one per session (or per mutable form), cryptographically random.
- Token validation: compare request token with session or double-submit cookie.
- Cookie policy: Set
Secure,HttpOnly,SameSite=Strict(orLaxwhen necessary). - Form / SPA integration: Ensure every state-changing request includes token (hidden field or header).
- Cache control: Do not cache HTML forms or pages that embed tokens.
- Proxy/Load Balancer: Maintain header forwarding, avoid stripping cookies, align subdomain routing.
- CI/Automated testing: Include token-absence, stale-token, and double-submit tests in build pipeline.
- Monitoring: Capture 403/419 logs labelled “CSRF token mismatch”; aggregate by endpoint and frequency.
- Regression alerts: If mismatch rate spikes after deployment, trigger investigation (could be config drift).
- Documentation & training: Ensure developers and front-end engineers know how tokens should be fetched/passed in SPAs.
Snippet (Nginx proxy header forwarding):
location / {
proxy_pass <http://backend>;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
# Ensure cookie header is forwarded
proxy_set_header Cookie $http_cookie;
proxy_pass_request_headers on;
}
Code Example Collection
Here are working examples across technologies to avoid and detect CSRF token mismatch.
Laravel AJAX example
<meta name="csrf-token" content="{{ csrf_token() }}">
<script>
axios.defaults.headers.common['X-CSRF-TOKEN'] = document.querySelector('meta[name="csrf-token"]').getAttribute('content');
axios.post('/update', { name: 'Bob' })
.then(r => console.log(r.data))
.catch(e => console.error('CSRF error', e.response.status));
</script>
Django fetch example
<body>
<script>
function getCookie(name) {
let v = document.cookie.match('(^|;)\\\\s*' + name + '\\\\s*=\\\\s*([^;]+)');
return v ? v.pop() : '';
}
fetch('/api/update-profile', {
method: 'POST',
headers: {
'X-CSRFToken': getCookie('csrftoken'),
'Content-Type': 'application/json'
},
body: JSON.stringify({ email: '[email protected]' })
}).then(res => {
if (res.status === 403) {
console.error('CSRF token mismatch or missing');
} else {
return res.json();
}
});
</script>
</body>
Node/Express snippet
app.use(cookieParser());
app.use(csurf({ cookie: true }));
app.get('/form', (req, res) => {
res.render('form', { csrfToken: req.csrfToken() });
});
app.post('/submit', (req, res) => {
res.send('Form submitted successfully');
});
Python log-parser for mismatch events
import re
pattern = re.compile(r'CSRF token mismatch error on endpoint (\\S+)')
with open('app.log') as f:
for line in f:
m = pattern.search(line)
if m:
print('Mismatch detected:', m.group(1))
CSRF in the Age of Zero Trust & AI-Driven Automation
As architectures evolve — microservices, decoupled SPAs, AI-driven scanning, zero-trust design — the paradigm for CSRF protection shifts too.
- Zero-trust networks suggest removing traditional session-cookie trust entirely; CSRF tokens must still be validated but often combined with finer‐grained identity assertions or OVF (One-Time Value) patterns.
- SameSite cookie adoption by browsers reduces some CSRF vectors, but you must still handle legacy flows, cross-origin API calls, and third-party auth flows (OAuth/OIDC).
- AI-driven vulnerability scanners enable continuous detection of token mismatches across hundreds of endpoints, flagging anomalies like mismatch rate spikes, token reuse patterns, or unusual endpoint behavior.
- Automatic remediation: metrics on mismatch frequency feed into ML models that detect drift — for example, “token-rate dropping below baseline” might indicate frontend code change removed token injection.
Conclusion
CSRF token mismatch is often dismissed as a mere “form submit error”, but for security engineers it is a strategic indicator — revealing session misconfiguration, proxy or caching faults, front-end token-handling mis-wiring, or even signs of live attacks. By understanding its lifecycle deeply, integrating checks into automation, and adopting robust engineering practices, you transform token mismatches from frustration logs into actionable defense telemetry.


