For the uninitiated, a JSON Web Signature decode operation seems trivial—a simple Base64URL decoding exercise to view the claims inside a token. But for security engineers, penetration testers, and AI security researchers, “decoding” is merely the reconnaissance phase of a much more complex battleground.
While developers use decoding to debug authentication flows, attackers use it to reverse-engineer signing logic. The gap between decoding a token and verifying its integrity is where the most dangerous authentication bypass vulnerabilities in modern API history have lived.
This article dissects the anatomy of JWS, analyzes critical verification failures including high-impact CVEs, and explores how AI-driven security—like the engines powering Penligent—is changing how we audit these cryptographic mechanisms.
The Anatomy of a JWS: More Than Just Base64
Before analyzing exploits, we must align on the structure defined in RFC 7515. A JSON Web Signature (JWS) represents content secured with a digital signature or Message Authentication Code (MAC).
A compact JWS string consists of three parts separated by dots (.):
Header.Payload.Signature
The Decoding Logic
כאשר אתה מבצע פענוח חתימת אינטרנט json, you are essentially converting the first two segments from Base64URL format back into JSON.
Here is a raw Python implementation for security researchers who prefer CLI over web-based tools that might log sensitive tokens:
פייתון
`import sys import json import base64
def padding_fix(data): missing_padding = len(data) % 4 if missing_padding: data += ‘=’ * (4 – missing_padding) return data
def decode_jws(token): try: header_b64, payload_b64, signature_b64 = token.split(‘.’)
header = json.loads(base64.urlsafe_b64decode(padding_fix(header_b64)))
payload = json.loads(base64.urlsafe_b64decode(padding_fix(payload_b64)))
return header, payload
except ValueError:
print("[-] Invalid Token Format")
sys.exit(1)
Usage context
header, payload = decode_jws(sys.argv[1])
print(json.dumps(header, indent=2))`
The output of a decode operation typically reveals the metadata that dictates how the verification should happen. This metadata is the attacker’s primary target.
| Header Parameter | תיאור | Security Implication |
|---|---|---|
אלג | אלגוריתם (לדוגמה, HS256, RS256) | Dictates the crypto primitive. Primary target for downgrade attacks. |
typ | Token Type (e.g., JWT) | Often ignored, but can be used for type confusion. |
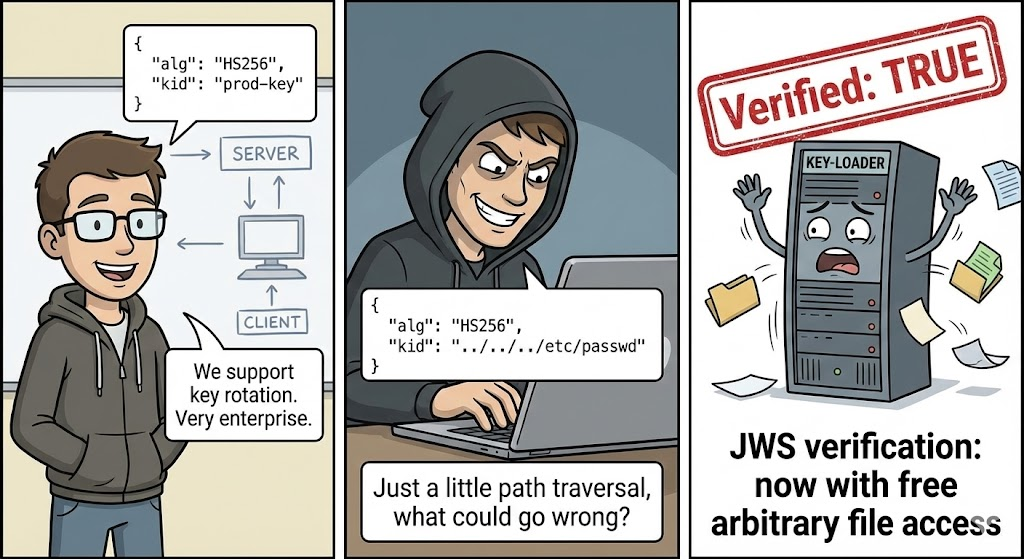
ילד | מזהה מפתח | Hints at which key to use. Can be manipulated for Directory Traversal או SQL Injection in rare cases. |
jku / x5u | JSON Web Key URL | Points to the public key URL. Target for SSRF or malicious key hosting. |
The “Decode-Verify” Gap: Where Vulnerabilities Live
The core problem is that many libraries and custom implementations decouple the decode step from the verify step. An application might decode the header to read the אלג field, and then use that user-controlled input to decide how to verify the signature.
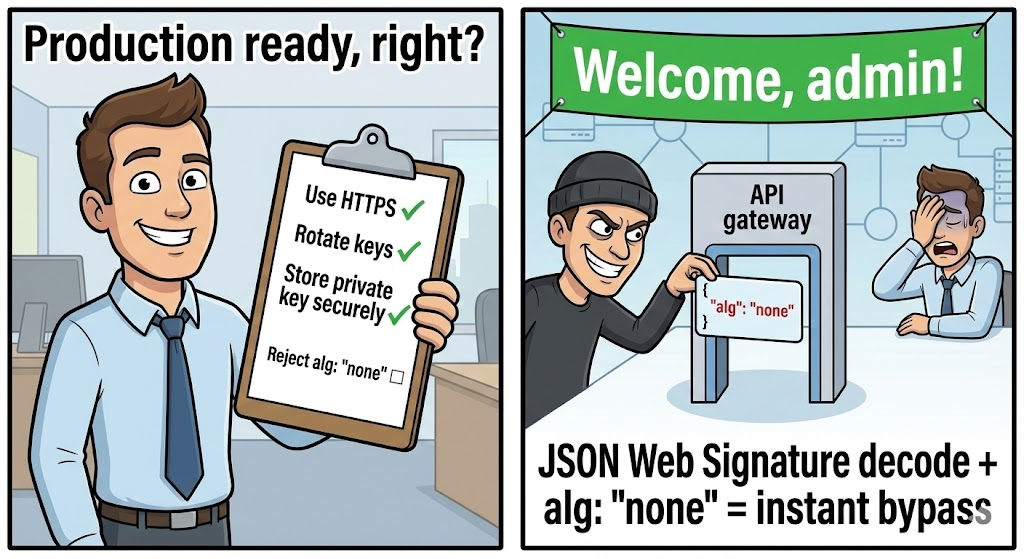
1. The “None” Algorithm Bypass
This is the “Hello World” of JWS exploits, yet it persists in legacy systems. If a backend implementation relies on the אלג header from the decoded token to determine verification logic, an attacker can modify the token:
- Decode the header.
- Change
אלגאלאף אחד(orאף אחד,NONE). - Strip the signature.
If the library supports אף אחד (intended for debugging) and doesn’t whitelist algorithms, the signature check is skipped entirely.
2. Algorithm Confusion (Key Confusion)
This is a more sophisticated attack. It occurs when a server supports both symmetric (HMAC) and asymmetric (RSA/ECDSA) signing but fails to validate which one is being used for a specific key.
- Scenario: The server expects an RS256 token (signed with a Private Key, verified with a Public Key).
- Attack: The attacker performs a פענוח חתימת אינטרנט json, changes
אלגאלHS256(HMAC), and signs the token using the server’s מפתח ציבורי כסוד HMAC. - תוצאה: Since the Public Key is often available to the client (or easily accessible), the attacker can forge a valid signature that the server verifies using its own Public Key (treating it as an HMAC secret).
Case Study: CVE-2022-21449 (“Psychic Paper”)
While algorithm confusion is a logic flaw, some vulnerabilities exist deep within the cryptographic implementation itself.
CVE-2022-21449 (CVSS 7.5), dubbed “Psychic Paper,” affected Java’s implementation of ECDSA signatures. It is a prime example of why simply validating that a “signature exists” is insufficient.
The Mechanism
In ECDSA, verification involves a mathematical equation: $v = R’$ (simplified). The vulnerability lay in Java’s ECDSA implementation where if the signature parts $r$ and $s$ were both set to 0, the verification logic would incorrectly return נכון עבור כלשהו payload.
An attacker could:
- Decode a legitimate JWS.
- Modify the payload (e.g.,
{"admin": true}). - Construct a signature where $r=0$ and $s=0$.
- Send it to a Java-based backend (running Java 15, 16, 17, or 18).
The server would verify the signature as valid, allowing a complete authentication bypass. This highlights that even standard, widely-used libraries are not immune to catastrophic failures.
AI-Driven JWS Auditing: The Penligent Approach
Manual analysis of JWS tokens is effective for individual exploits, but modern microservices architectures often employ hundreds of different keys, rotation policies, and algorithm configurations. A human engineer cannot manually פענוח חתימת אינטרנט json and test every permutation of header injection, key confusion, and library-specific bypasses across an entire attack surface.
This is where AI-driven automated penetration testing becomes essential.
Penligent leverages advanced Large Language Models (LLMs) and reinforcement learning to automate this depth of testing. Unlike traditional scanners that use static regex to look for known bad strings, Penligent’s engine:
- Contextual Decoding: It intercepts traffic, decodes JWS tokens, and understands the context (e.g., “This token is used for the payment gateway, not just login”).
- יצירת מטען אדפטיבי: It doesn’t just try
alg: none. It analyzes the server’s error responses to infer the backend library. If it detects a Java environment, it might attempt variations of CVE-2022-21449. If it seesילדparameters, it probes for SQL injection or command injection via Key ID. - Logic Flow Analysis: Penligent can identify if a token is correctly verified in one endpoint but simply פוענח and trusted without verification in a secondary microservice—a common architectural flaw.
By integrating intelligent JWS analysis, Penligent moves beyond simple vulnerability scanning into the realm of autonomous red teaming, ensuring that cryptographic implementations are robust against both known CVEs and zero-day logic flaws.
Hardening Guidelines for Engineers
To secure applications against JWS attacks, we must move from “implicit trust” to “explicit verification.”
1. Enforce Algorithm Whitelisting
Never rely on the אלג header from the decoded token to determine the verification method. Hardcode the expected algorithm in your verifier.
JavaScript
// Secure approach (Node.js jose library) const verified = await jose.jwtVerify(token, secretKey, { algorithms: ['RS256'], // Explicitly whitelist ONLY RS256 });
2. Validate the ילד (Key ID) STRICTLY
If your setup uses multiple keys (JWKS), ensure the ילד header matches a key in your whitelist. Do not pass the ילד value directly to a database query or filesystem call.
3. Use Modern Libraries
Avoid writing your own crypto wrappers. Use battle-tested libraries like jose (Node.js), PyJWT (Python), or jjwt (Java). However, ensure you are subscribed to security bulletins for these libraries.
4. Separate Decode from Verify (Logically)
Understand that פענוח חתימת אינטרנט json is for display purposes (UI, logging). Verify is for הרשאה. Never use decoded data for business logic before the verification step returns נכון.
סיכום
The ability to פענוח חתימת אינטרנט json is a fundamental skill, but it is merely the scratching of the surface. For the security engineer, the raw JSON is a map of potential misconfigurations. From the classic “None” algorithm to mathematical bypasses like CVE-2022-21449, the integrity of the web relies on rigorous verification, not just successful decoding.
As application complexity grows, leveraging AI-powered tools like Penligent to automate the detection of these subtle cryptographic flaws is becoming a necessity for robust enterprise security posture.
References:


